WINRM
Remote Access to WinRM and Remote Management Users Group
Check the standard permissions of the PoSh session:
(Get-PSSessionConfiguration -Name Microsoft.PowerShell).Permission
As you can see, the access is allowed for the following built-in groups:
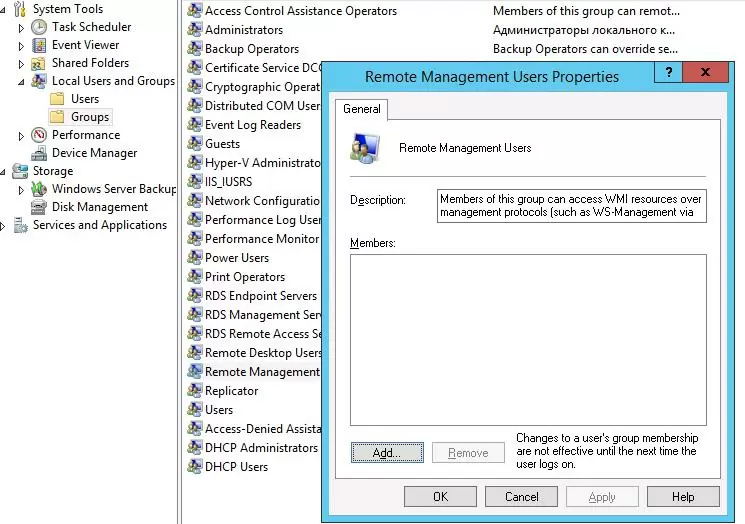
- BUILTIN\Administrators — AccessAllowed,
- BUILTIN\Remote Management Users — AccessAllowed
So, to let a user connect to a remote machine through WinRM, it’s enough to be a member of the built-in local group of administrators or Remote Management Users security group (this group is created by default starting from PowerShell 4.0). This group also has access to WMI resources via management protocols (e.g., WS-Management)
A user can be added to the group using Computer Management snap-in:
or using the command:
net localgroup "Remote Management Users" /add jsmith
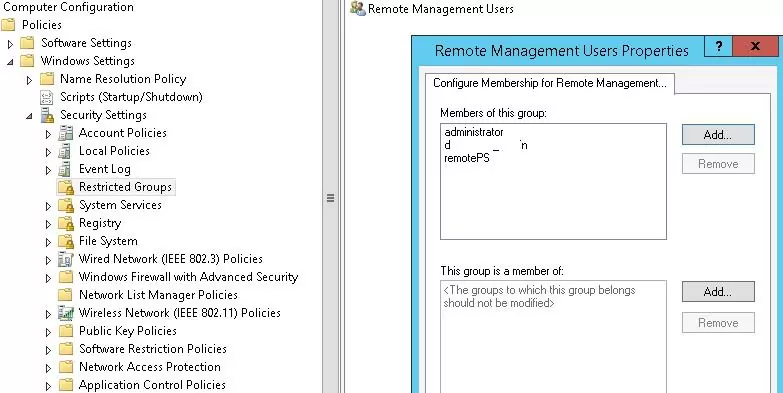
If you need to provide such permissions on multiple computers, you can use Group Policy. To do this, assign the GPO to the computers you need, and add the new Remote Management Users group to the Computer Configuration -> Windows Settings -> Security Settings -> Restricted Groups policy. Add to the policy users or groups that need to be granted access to WinRM.
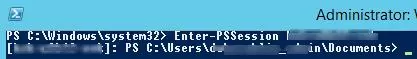
After a user becomes a member of the Remote Management Users group, he can create a remote PowerShell session using Enter-PSSession or run commands using the Invoke-Command cmdlet.
User privileges in this session will be limited to user rights on this machine.
Make sure if the remote connection is established.
┌──(puck㉿kali)-[~/vulnlab/bruno]
└─$ evil-winrm -i bruno.vl -u 'svc_scan' -p 'Sunshine1'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_scan\Documents>
.
notes…
note : thus you can powerview to the machine WITHOUT being a member of “Remote Management Users” or “Administrators” group.
┌──(puck㉿kali)-[~/vulnlab/bruno] └─$ powerview bruno.vl/svc_scan:'Sunshine1'@bruno.vl /home/puck/.local/share/pipx/venvs/powerview/lib/python3.13/site-packages/impacket/version.py:12: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81. import pkg_resources Logging directory is set to /home/puck/.powerview/logs/bruno-svc_scan-bruno.vl ╭─LDAPS─[brunodc.bruno.vl]─[BRUNO\svc_scan]-[NS:<auto>] ╰─PV ❯
.